7. Integrating LDAP Services for Authentication and Authorization
Important
7.1. Supported Directory Services
- Red Hat Directory Server 8.1 and 8.2
- Microsoft Active Directory 2003 and 2008
7.2. How JBoss ON Uses LDAP for Authentication
Warning
Note
JONUser=true, which can make it easier and more precise to locate entries.
Note
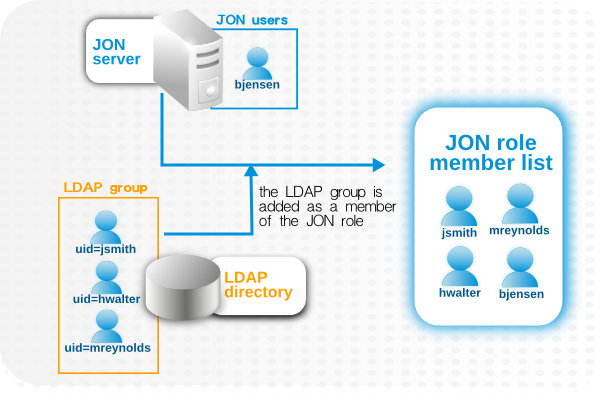
Integrating LDAP directories introduces another area where users can be created and managed and where the membership of roles can be changed. On the one hand, this can make managing users much easier, especially by allowing existing users to register themselves seamlessly and by automatically updating role membership. However, because users can still be created in JBoss ON and added manually to JBoss ON, user and role management can become messy.
jsmith) and password, but is improperly assigned the JBoss ON role membership of LDAP user John Smith (LDAP UID jsmith) because her JBoss ON user ID was the same as his LDAP user ID, and her account was incorrectly mapped to his LDAP account and, therefore, his LDAP group membership.
Figure 33. LDAP Groups, JBoss ON Roles, and Role Members
- Only create regular user accounts in one place. If LDAP should be used for authentication, then only add or delete user accounts in the LDAP directory.
- Ideally, limit JBoss ON user accounts to special, administrative users and rely on the LDAP directory for regular accounts.
- Try to design roles around LDAP groups, meaning that JBoss ON user accounts in those roles should be limited to admin accounts or avoided altogether.
7.3. Configuring LDAP User Authentication
- In the top menu, click the Administration tab.
- In the menu table on the left, select the item.
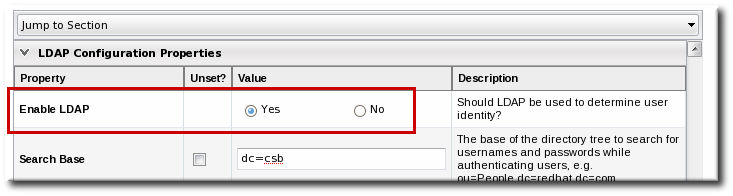
- Jump to the LDAP Configuration Properties area.
- Check the Use LDAP Authentication checkbox so that JBoss ON will use the LDAP user directory as its identity store.
- Configure the connection settings to connect to the specific LDAP directory.
- Give the LDAP URL of the LDAP server. This has the format
ldap://hostname[:port]. For example:ldap://server.example.com:389
ldap://server.example.com:389Copy to Clipboard Copied! Toggle word wrap Toggle overflow By default, this connects to the localhost over port 389 (standard LDAP port) or 636 (secure LDAP port, if SSL is selected). - To use a secure connection, check the Use SSL checkbox. When using SSL, make sure that the LDAP directory is actually running over SSL, and make sure that the connection URL points to the appropriate SSL port and protocol:
ldaps://server.example.com:636
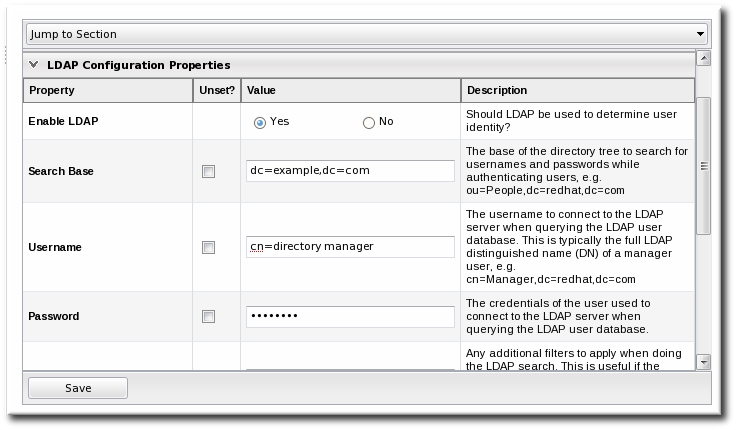
ldaps://server.example.com:636Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Give the bind credentials to use to connect to the server. The username is the full LDAP distinguished name of the user as whom JBoss ON binds to the directory.
Note
The user must exist in the LDAP directory before configuring the LDAP settings in JBoss ON. Otherwise, login attempts to the JBoss ON server will fail.Also, make sure that the JBoss ON user has appropriate read and search access to the user and group subtrees in the LDAP directory.
- Set the search parameters that JBoss ON uses when searching the LDAP directory for matching user entries.
- The search base is the point in the directory tree where the server begins looking for entries. If this is used only for user authentication or if all JBoss ON-related entries are in the same subtree, then this can reference a specific subtree:
ou=user,ou=JON,dc=example,dc=com
ou=user,ou=JON,dc=example,dc=comCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the users or groups are spread across the directory, then select the base DN:dc=example,dc=com
dc=example,dc=comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, set a search filter to use to search for a specific subset of entries. This can improve search performance and results, particularly when all JBoss ON-related entries share a common LDAP attribute, like a custom
JonUserattribute. The filter can use wild cards (objectclass=*) or specific values (JonUser=true). - Set the LDAP naming attribute; this is the element on the farthest left of the full distinguished name. For example, in
uid=jsmith,ou=people,dc=example,dc=com, the far left element isuid=jsmith, and the naming attribute isuid.The default naming attribute in Active Directory iscn. In Red Hat Directory Server, the default naming attribute isuid.
- Save the LDAP settings.
Note
The Group Filter and Member Property fields aren't required for user authentication. They're used for configuring LDAP groups to be assigned to roles, as in Section 7.5, “Associating LDAP User Groups to Roles in JBoss ON”.
7.4. How JBoss ON Roles Work with LDAP User Groups
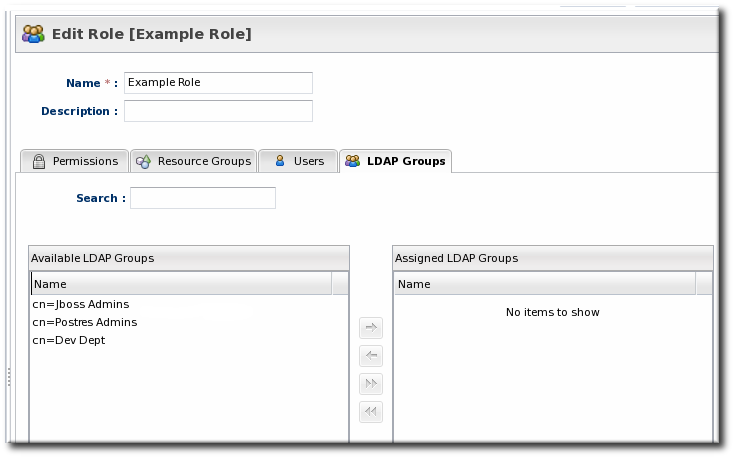
Figure 34. Groups Assigned to a Role
- An LDAP directory server connection has to be configured.
- There has to be an LDAP attribute given to search for group entries.For Active Directory, this is generally the
groupobject class. For Red Hat Directory Server, this is generallygroupOfUniqueNames. Other standard object classes are available, and it is also possible to use a custom, even JBoss ON-specific, object class. - There has to be an LDAP attribute given to identify members in the group.Common member attributes are
memberanduniqueMember.
(&(group_filter)(member_attribute=user_DN))
(&(group_filter)(member_attribute=user_DN))member attribute on an Active Directory group:
ldapsearch -h server.example.com -x -D "cn=Administrator,cn=Users,dc=example,dc=com" -W -b "dc=example,dc=com" -x '(&(objectclass=group)(member=CN=John Smith,CN=Users,DC=example,DC=com))'
ldapsearch -h server.example.com -x -D "cn=Administrator,cn=Users,dc=example,dc=com" -W -b "dc=example,dc=com" -x '(&(objectclass=group)(member=CN=John Smith,CN=Users,DC=example,DC=com))'uniqueMember attribute on groupOfUniqueNames groups more commonly than member and group. For example:
/usr/lib64/mozldap6/ldapsearch -D "cn=directory manager" -w secret -p 389 -h server.example.com -b "ou=People,dc=example,dc=com" -s sub "(&(objectclass=groupOfUniqueNames)(uniqueMember=uid=jsmith,ou=People,dc=example,dc=com))"
/usr/lib64/mozldap6/ldapsearch -D "cn=directory manager" -w secret -p 389 -h server.example.com -b "ou=People,dc=example,dc=com" -s sub "(&(objectclass=groupOfUniqueNames)(uniqueMember=uid=jsmith,ou=People,dc=example,dc=com))"Note
7.5. Associating LDAP User Groups to Roles in JBoss ON
- In the top menu, click the Administration tab.
- In the menu table on the left, select the item.
- Jump to the LDAP Configuration Properties area.
- Set up the LDAP connections, as described in Section 7.3, “Configuring LDAP User Authentication”. It is not required that the LDAP directory be used as the identity store in order to configure LDAP authorization, but it is recommended.
- Set the parameters to use for the server to use to search for LDAP groups and their members.The search filter that JBoss ON constructs looks like this:
(&(group_filter)(member_attribute=user_DN))
(&(group_filter)(member_attribute=user_DN))Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The Group Search Filter field sets how to search for the group entry. This is usually done by specifying the type of group to search for through its object class:
(objectclass=groupOfUniqueNames)
(objectclass=groupOfUniqueNames)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The Group Member Filter field gives the attribute that the specified group type uses to store member distinguished names. For example:
uniqueMember
uniqueMemberCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The user_DN is dynamically supplied by JBoss ON when a user logs into the UI. - Save the LDAP settings.