4. Configuring SSL Connections for Server-Agent Communication
By default, the JBoss ON server and JBoss ON agents talk to each other in the clear, meaning all communications traffic is unencrypted and no authentication is performed on either end.
Running servers in the clear, particularly since JBoss ON can perform configuration changes on some types of resources, can have security considerations for your network. JBoss ON should only be run without encryption or authentication if JBoss ON is being tested or if all JBoss ON servers and agents are deployed on a fully secured network, with access limited by a firewall or VPN and restricted to trusted personnel.
JBoss ON uses SSL/TLS to secure connections between agents and servers in two separate ways:
- Encryption specially encodes the data sent between agents and servers during a session.
- Authentication uses SSL server and client certificates to verify the identity of an agent before it connects to a server, and vice versa.
Note
There is a basic authentication mechanism employed by the server in which it assigns security tokens to its agents which are used to identify and "authenticate" registered agents. This token mechanism should not, however, be considered a strong authentication scheme for the purposes of protecting your JBoss ON network from infiltration.
Setting up encryption is very simple; it only requires enabling the proper transport mechanism between servers and agents. This prevents an attacker from intercepting communications or data between a legitimate JBoss ON server and a legitimate JBoss ON agent, by sniffing data or setting up a man-in-the-middle attack.
Authentication adds another layer of protection by preventing an attacker from installing a "rogue" JBoss ON agent and letting it register itself on the JBoss ON system, so that the rogue agent has access to the network. Although setting up authentication is more complicated than using encryption alone, it is worth the effort to implement for the additional protection, especially if there are vulnerabilities in the network setup.
4.1. Setting up Encryption
Copy linkLink copied to clipboard!
All that need to be done to set up encryption is to enable the SSL transport connectors in the JBoss ON server and agent configuration files. There are two transport options for SSL,
sslservlet and sslsocket.
The JBoss ON server has a default certificate that it can use for encryption and the agent can generate a self-signed certificate, so it's not necessary to generate or install additional SSL certificates for encryption alone.
- First, enable SSL encryption on the JBoss ON server.
- Shut down the JBoss ON server.
serverRoot/jon-server-3.2.GA/bin/rhqctl.sh stop
serverRoot/jon-server-3.2.GA/bin/rhqctl.sh stopCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the
serverRoot/jon-server-3.2.GA/bin/rhq-server.propertiesfile for the JBoss ON server. - Edit the
rhq.communications.connector.*settings to use SSL. To use thesslsockettransport method, which is recommended for authentication, update therhq.communications.connector.transportmethod, set the port number to use for the socket, and remove the servlet specified in the transport parameters setting.rhq.communications.connector.transport=sslsocket rhq.communications.connector.bind-address= rhq.communications.connector.bind-port=55555 rhq.communications.connector.transport-params=
rhq.communications.connector.transport=sslsocket rhq.communications.connector.bind-address= rhq.communications.connector.bind-port=55555 rhq.communications.connector.transport-params=Copy to Clipboard Copied! Toggle word wrap Toggle overflow To use thesslservlettransport method, all that's necessary is to change therhq.communications.connector.transportmethod.rhq.communications.connector.transport=sslservlet rhq.communications.connector.bind-address= rhq.communications.connector.bind-port= rhq.communications.connector.transport-params=/jboss-remoting-servlet-invoker/ServerInvokerServlet
rhq.communications.connector.transport=sslservlet rhq.communications.connector.bind-address= rhq.communications.connector.bind-port= rhq.communications.connector.transport-params=/jboss-remoting-servlet-invoker/ServerInvokerServletCopy to Clipboard Copied! Toggle word wrap Toggle overflow - For setting encryption alone, make sure that certificate-based authentication is disabled:
rhq.server.tomcat.security.client-auth-mode=false rhq.server.client.security.server-auth-mode-enabled=false
rhq.server.tomcat.security.client-auth-mode=false rhq.server.client.security.server-auth-mode-enabled=falseCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, define the secure protocol to use. The default is TLS (which is usually fine), but you can set it to SSL.
rhq.server.tomcat.security.secure-socket-protocol=TLS rhq.server.client.security.secure-socket-protocol=TLS
rhq.server.tomcat.security.secure-socket-protocol=TLS rhq.server.client.security.secure-socket-protocol=TLSCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes, and restart the JBoss ON server.
serverRoot/jon-server-3.2.GA/bin/rhqctl start
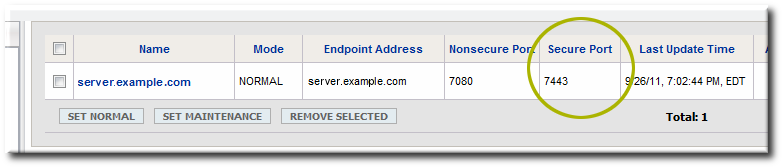
serverRoot/jon-server-3.2.GA/bin/rhqctl startCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Verify that the end point address and port number given in the configuration are actually the settings set for the server in JBoss ON.
- Click the Administration tab in the top menu.
- In the Topology box on the left, select the Servers item.
- Check the port number in the Secure Port column.
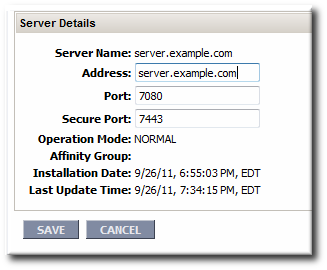
- If the value is wrong, click the name of the server to open the edit page.
- Click the under the server information, and reset the end point address or port as necessary.
- Then, enable SSL encryption in the agent.
Note
This shows how to edit the agent configuration by editing the agent configuration file. The agent configuration can also be edited by going through the advanced setup mode in the agent start script:agentRoot/rhq-agent/bin/rhq-agent.sh --cleanconfig --setup --advanced
agentRoot/rhq-agent/bin/rhq-agent.sh --cleanconfig --setup --advancedCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the agent configuration file:
vim agentRoot/rhq-agent/conf/agent-configuration.xml
vim agentRoot/rhq-agent/conf/agent-configuration.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the transport protocol to
sslsocket.<entry key="rhq.communications.connector.transport" value="sslsocket" />
<entry key="rhq.communications.connector.transport" value="sslsocket" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the server connection information so that it matches the configuration for the server. The bind address for the server is commented out by default, and the other parameters are set to the JBoss ON server defaults, including using
sslservletfor the server's transport protocol.<entry key="rhq.communications.connector.transport" value="sslsocket" /> <entry key="rhq.agent.server.transport" value="sslservlet" /> <entry key="rhq.agent.server.bind-port" value="55555" /> <entry key="rhq.agent.server.bind-address" value="server.example.com" /> <entry key="rhq.agent.server.transport-params" value="" />
<entry key="rhq.communications.connector.transport" value="sslsocket" /> <entry key="rhq.agent.server.transport" value="sslservlet" /> <entry key="rhq.agent.server.bind-port" value="55555" /> <entry key="rhq.agent.server.bind-address" value="server.example.com" /> <entry key="rhq.agent.server.transport-params" value="" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow - For setting encryption alone, make sure that certificate-based authentication is disabled. These parameters can be left commented out or can be explicitly set to turn off authentication.
<entry key="rhq.communications.connector.security.client-auth-mode" value="none" /> <entry key="rhq.agent.client.security.server-auth-mode-enabled" value="false" />
<entry key="rhq.communications.connector.security.client-auth-mode" value="none" /> <entry key="rhq.agent.client.security.server-auth-mode-enabled" value="false" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, define additional protocol settings for the agent. This is necessary if the server is configured to use transport protocols other than TLS.
<entry key="rhq.communications.connector.security.secure-socket-protocol" value="TLS" /> <entry key="rhq.agent.client.security.secure-socket-protocol" value="TLS" />
<entry key="rhq.communications.connector.security.secure-socket-protocol" value="TLS" /> <entry key="rhq.agent.client.security.secure-socket-protocol" value="TLS" />Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Exit the agent and restart it, using the
--cleanconfigoption to load the new configuration.agentRoot/rhq-agent/bin/rhq-agent.sh --cleanconfig
agentRoot/rhq-agent/bin/rhq-agent.sh --cleanconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow