1.2. System Permissions
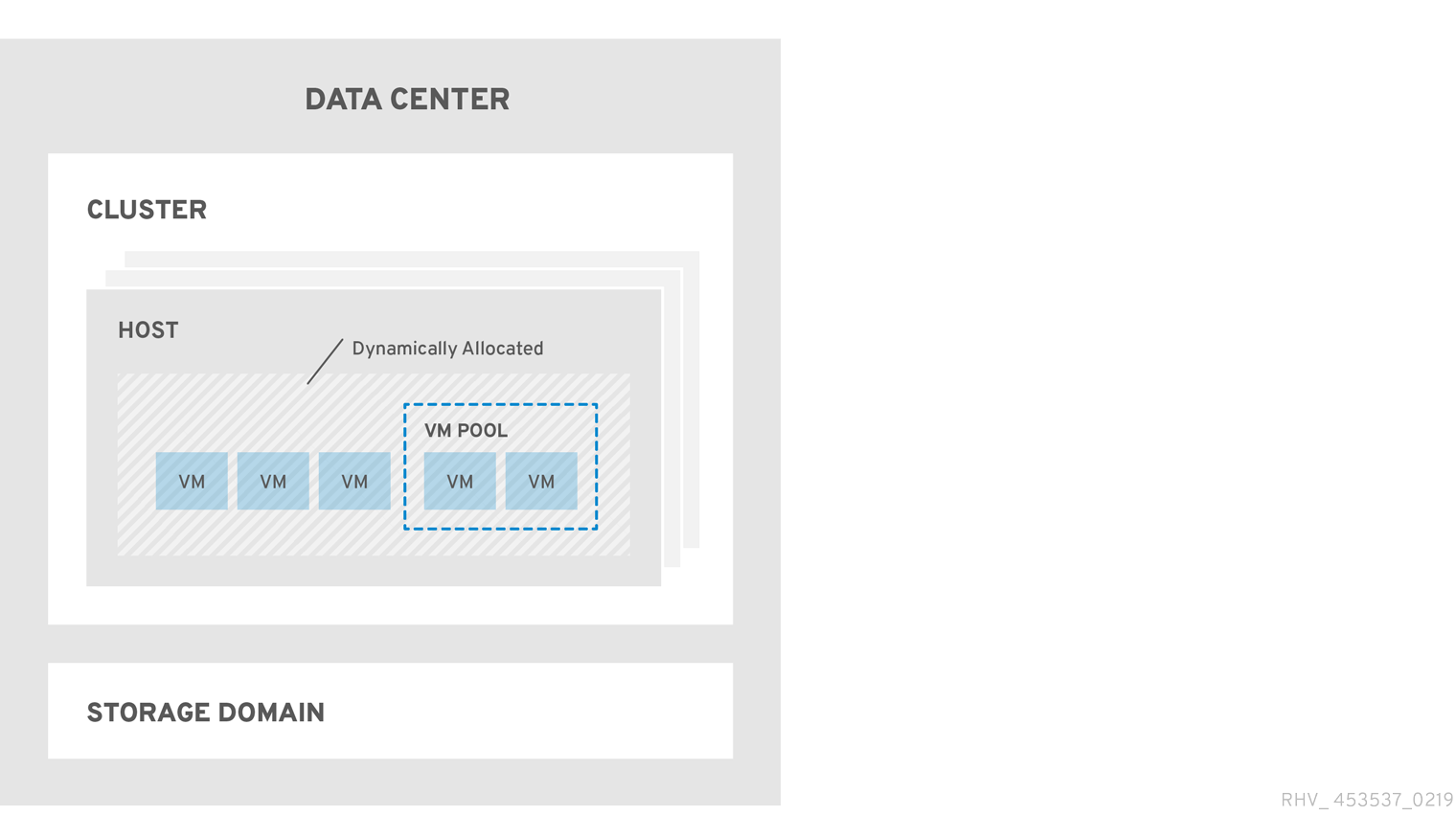
Permissions enable users to perform actions on objects, where objects are either individual objects or container objects. Any permissions that apply to a container object also apply to all members of that container.
Figure 1.2. Permissions & Roles
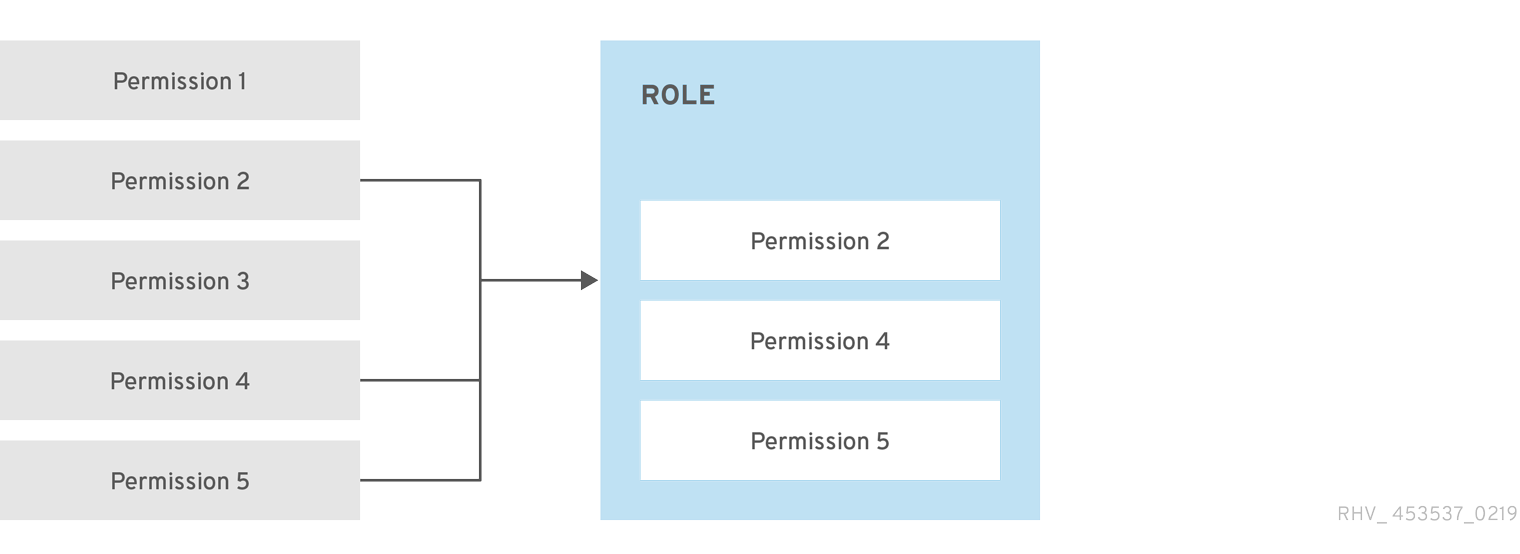
Figure 1.3. Red Hat Virtualization Object Hierarchy
1.2.1. User Properties
Roles and permissions are the properties of the user. Roles are predefined sets of privileges that permit access to different levels of physical and virtual resources. Multilevel administration provides a finely grained hierarchy of permissions. For example, a data center administrator has permissions to manage all objects in the data center, while a host administrator has system administrator permissions to a single physical host. A user can have permissions to use a single virtual machine but not make any changes to the virtual machine configurations, while another user can be assigned system permissions to a virtual machine.
1.2.2. User and Administrator Roles
Red Hat Virtualization provides a range of pre-configured roles, from an administrator with system-wide permissions to an end user with access to a single virtual machine. While you cannot change or remove the default roles, you can clone and customize them, or create new roles according to your requirements. There are two types of roles:
- Administrator Role: Allows access to the Administration Portal for managing physical and virtual resources. An administrator role confers permissions for actions to be performed in the VM Portal; however, it has no bearing on what a user can see in the VM Portal.
- User Role: Allows access to the VM Portal for managing and accessing virtual machines and templates. A user role determines what a user can see in the VM Portal. Permissions granted to a user with an administrator role are reflected in the actions available to that user in the VM Portal.
1.2.3. User Roles Explained
The table below describes basic user roles which confer permissions to access and configure virtual machines in the VM Portal.
| Role | Privileges | Notes |
|---|---|---|
| UserRole | Can access and use virtual machines and pools. | Can log in to the VM Portal, use assigned virtual machines and pools, view virtual machine state and details. |
| PowerUserRole | Can create and manage virtual machines and templates. | Apply this role to a user for the whole environment with the Configure window, or for specific data centers or clusters. For example, if a PowerUserRole is applied on a data center level, the PowerUser can create virtual machines and templates in the data center. |
| UserVmManager | System administrator of a virtual machine. | Can manage virtual machines and create and use snapshots. A user who creates a virtual machine in the VM Portal is automatically assigned the UserVmManager role on the machine. |
The table below describes advanced user roles which allow you to do more fine tuning of permissions for resources in the VM Portal.
| Role | Privileges | Notes |
|---|---|---|
| UserTemplateBasedVm | Limited privileges to only use Templates. | Can use templates to create virtual machines. |
| DiskOperator | Virtual disk user. | Can use, view and edit virtual disks. Inherits permissions to use the virtual machine to which the virtual disk is attached. |
| VmCreator | Can create virtual machines in the VM Portal. | This role is not applied to a specific virtual machine; apply this role to a user for the whole environment with the Configure window. Alternatively apply this role for specific data centers or clusters. When applying this role to a cluster, you must also apply the DiskCreator role on an entire data center, or on specific storage domains. |
| TemplateCreator | Can create, edit, manage and remove virtual machine templates within assigned resources. | This role is not applied to a specific template; apply this role to a user for the whole environment with the Configure window. Alternatively apply this role for specific data centers, clusters, or storage domains. |
| DiskCreator | Can create, edit, manage and remove virtual disks within assigned clusters or data centers. | This role is not applied to a specific virtual disk; apply this role to a user for the whole environment with the Configure window. Alternatively apply this role for specific data centers or storage domains. |
| TemplateOwner | Can edit and delete the template, assign and manage user permissions for the template. | This role is automatically assigned to the user who creates a template. Other users who do not have TemplateOwner permissions on a template cannot view or use the template. |
| VnicProfileUser | Logical network and network interface user for virtual machine and template. | Can attach or detach network interfaces from specific logical networks. |
1.2.4. Administrator Roles Explained
The table below describes basic administrator roles which confer permissions to access and configure resources in the Administration Portal.
| Role | Privileges | Notes |
|---|---|---|
| SuperUser | System Administrator of the Red Hat Virtualization environment. | Has full permissions across all objects and levels, can manage all objects across all data centers. |
| ClusterAdmin | Cluster Administrator. | Possesses administrative permissions for all objects underneath a specific cluster. |
| DataCenterAdmin | Data Center Administrator. | Possesses administrative permissions for all objects underneath a specific data center except for storage. |
Do not use the administrative user for the directory server as the Red Hat Virtualization administrative user. Create a user in the directory server specifically for use as the Red Hat Virtualization administrative user.
The table below describes advanced administrator roles which allow you to do more fine tuning of permissions for resources in the Administration Portal.
| Role | Privileges | Notes |
|---|---|---|
| TemplateAdmin | Administrator of a virtual machine template. | Can create, delete, and configure the storage domains and network details of templates, and move templates between domains. |
| StorageAdmin | Storage Administrator. | Can create, delete, configure, and manage an assigned storage domain. |
| HostAdmin | Host Administrator. | Can attach, remove, configure, and manage a specific host. |
| NetworkAdmin | Network Administrator. | Can configure and manage the network of a particular data center or cluster. A network administrator of a data center or cluster inherits network permissions for virtual pools within the cluster. |
| VmPoolAdmin | System Administrator of a virtual pool. | Can create, delete, and configure a virtual pool; assign and remove virtual pool users; and perform basic operations on a virtual machine in the pool. |
| GlusterAdmin | Gluster Storage Administrator. | Can create, delete, configure, and manage Gluster storage volumes. |
| VmImporterExporter | Import and export Administrator of a virtual machine. | Can import and export virtual machines. Able to view all virtual machines and templates exported by other users. |
1.2.5. Assigning an Administrator or User Role to a Resource
Assign administrator or user roles to resources to allow users to access or manage that resource.
Assigning a Role to a Resource
- Find and click the resource’s name to open the details view.
- Click the Permissions tab to list the assigned users, the user’s role, and the inherited permissions for the selected resource.
- Click Add.
- Enter the name or user name of an existing user into the Search text box and click Go. Select a user from the resulting list of possible matches.
- Select a role from the Role to Assign drop-down list.
- Click OK.
The user now has the inherited permissions of that role enabled for that resource.
1.2.6. Removing an Administrator or User Role from a Resource
Remove an administrator or user role from a resource; the user loses the inherited permissions associated with the role for that resource.
Removing a Role from a Resource
- Find and click the resource’s name to open the details view.
- Click the Permissions tab to list the assigned users, the user’s role, and the inherited permissions for the selected resource.
- Select the user to remove from the resource.
- Click Remove.
- Click OK.
1.2.7. Managing System Permissions for a Data Center
As the SuperUser, the system administrator manages all aspects of the Administration Portal. More specific administrative roles can be assigned to other users. These restricted administrator roles are useful for granting a user administrative privileges that limit them to a specific resource. For example, a DataCenterAdmin role has administrator privileges only for the assigned data center with the exception of the storage for that data center, and a ClusterAdmin has administrator privileges only for the assigned cluster.
A data center administrator is a system administration role for a specific data center only. This is useful in virtualization environments with multiple data centers where each data center requires an administrator. The DataCenterAdmin role is a hierarchical model; a user assigned the data center administrator role for a data center can manage all objects in the data center with the exception of storage for that data center. Use the Configure button in the header bar to assign a data center administrator for all data centers in the environment.
The data center administrator role permits the following actions:
- Create and remove clusters associated with the data center.
- Add and remove hosts, virtual machines, and pools associated with the data center.
- Edit user permissions for virtual machines associated with the data center.
You can only assign roles and permissions to existing users.
You can change the system administrator of a data center by removing the existing system administrator and adding the new system administrator.
1.2.8. Data Center Administrator Roles Explained
Data Center Permission Roles
The table below describes the administrator roles and privileges applicable to data center administration.
| Role | Privileges | Notes |
|---|---|---|
| DataCenterAdmin | Data Center Administrator | Can use, create, delete, manage all physical and virtual resources within a specific data center except for storage, including clusters, hosts, templates and virtual machines. |
| NetworkAdmin | Network Administrator | Can configure and manage the network of a particular data center. A network administrator of a data center inherits network permissions for virtual machines within the data center as well. |
1.2.9. Managing System Permissions for a Cluster
As the SuperUser, the system administrator manages all aspects of the Administration Portal. More specific administrative roles can be assigned to other users. These restricted administrator roles are useful for granting a user administrative privileges that limit them to a specific resource. For example, a DataCenterAdmin role has administrator privileges only for the assigned data center with the exception of the storage for that data center, and a ClusterAdmin has administrator privileges only for the assigned cluster.
A cluster administrator is a system administration role for a specific cluster only. This is useful in data centers with multiple clusters, where each cluster requires a system administrator. The ClusterAdmin role is a hierarchical model: a user assigned the cluster administrator role for a cluster can manage all objects in the cluster. Use the Configure button in the header bar to assign a cluster administrator for all clusters in the environment.
The cluster administrator role permits the following actions:
- Create and remove associated clusters.
- Add and remove hosts, virtual machines, and pools associated with the cluster.
- Edit user permissions for virtual machines associated with the cluster.
You can only assign roles and permissions to existing users.
You can also change the system administrator of a cluster by removing the existing system administrator and adding the new system administrator.
1.2.10. Cluster Administrator Roles Explained
Cluster Permission Roles
The table below describes the administrator roles and privileges applicable to cluster administration.
| Role | Privileges | Notes |
|---|---|---|
| ClusterAdmin | Cluster Administrator | Can use, create, delete, manage all physical and virtual resources in a specific cluster, including hosts, templates and virtual machines. Can configure network properties within the cluster such as designating display networks, or marking a network as required or non-required. However, a ClusterAdmin does not have permissions to attach or detach networks from a cluster, to do so NetworkAdmin permissions are required. |
| NetworkAdmin | Network Administrator | Can configure and manage the network of a particular cluster. A network administrator of a cluster inherits network permissions for virtual machines within the cluster as well. |
1.2.11. Managing System Permissions for a Network
As the SuperUser, the system administrator manages all aspects of the Administration Portal. More specific administrative roles can be assigned to other users. These restricted administrator roles are useful for granting a user administrative privileges that limit them to a specific resource. For example, a DataCenterAdmin role has administrator privileges only for the assigned data center with the exception of the storage for that data center, and a ClusterAdmin has administrator privileges only for the assigned cluster.
A network administrator is a system administration role that can be applied for a specific network, or for all networks on a data center, cluster, host, virtual machine, or template. A network user can perform limited administration roles, such as viewing and attaching networks on a specific virtual machine or template. You can use the Configure button in the header bar to assign a network administrator for all networks in the environment.
The network administrator role permits the following actions:
- Create, edit and remove networks.
- Edit the configuration of the network, including configuring port mirroring.
- Attach and detach networks from resources including clusters and virtual machines.
The user who creates a network is automatically assigned NetworkAdmin permissions on the created network. You can also change the administrator of a network by removing the existing administrator and adding the new administrator.
1.2.12. Network Administrator and User Roles Explained
Network Permission Roles
The table below describes the administrator and user roles and privileges applicable to network administration.
| Role | Privileges | Notes |
|---|---|---|
| NetworkAdmin | Network Administrator for data center, cluster, host, virtual machine, or template. The user who creates a network is automatically assigned NetworkAdmin permissions on the created network. | Can configure and manage the network of a particular data center, cluster, host, virtual machine, or template. A network administrator of a data center or cluster inherits network permissions for virtual pools within the cluster. To configure port mirroring on a virtual machine network, apply the NetworkAdmin role on the network and the UserVmManager role on the virtual machine. |
| VnicProfileUser | Logical network and network interface user for virtual machine and template. | Can attach or detach network interfaces from specific logical networks. |
1.2.13. Managing System Permissions for a Host
As the SuperUser, the system administrator manages all aspects of the Administration Portal. More specific administrative roles can be assigned to other users. These restricted administrator roles are useful for granting a user administrative privileges that limit them to a specific resource. For example, a DataCenterAdmin role has administrator privileges only for the assigned data center with the exception of the storage for that data center, and a ClusterAdmin has administrator privileges only for the assigned cluster.
A host administrator is a system administration role for a specific host only. This is useful in clusters with multiple hosts, where each host requires a system administrator. You can use the Configure button in the header bar to assign a host administrator for all hosts in the environment.
The host administrator role permits the following actions:
- Edit the configuration of the host.
- Set up the logical networks.
- Remove the host.
You can also change the system administrator of a host by removing the existing system administrator and adding the new system administrator.
1.2.14. Host Administrator Roles Explained
Host Permission Roles
The table below describes the administrator roles and privileges applicable to host administration.
| Role | Privileges | Notes |
|---|---|---|
| HostAdmin | Host Administrator | Can configure, manage, and remove a specific host. Can also perform network-related operations on a specific host. |
1.2.15. Managing System Permissions for a Storage Domain
As the SuperUser, the system administrator manages all aspects of the Administration Portal. More specific administrative roles can be assigned to other users. These restricted administrator roles are useful for granting a user administrative privileges that limit them to a specific resource. For example, a DataCenterAdmin role has administrator privileges only for the assigned data center with the exception of the storage for that data center, and a ClusterAdmin has administrator privileges only for the assigned cluster.
A storage administrator is a system administration role for a specific storage domain only. This is useful in data centers with multiple storage domains, where each storage domain requires a system administrator. Use the Configure button in the header bar to assign a storage administrator for all storage domains in the environment.
The storage domain administrator role permits the following actions:
- Edit the configuration of the storage domain.
- Move the storage domain into maintenance mode.
- Remove the storage domain.
You can only assign roles and permissions to existing users.
You can also change the system administrator of a storage domain by removing the existing system administrator and adding the new system administrator.
1.2.16. Storage Administrator Roles Explained
Storage Domain Permission Roles
The table below describes the administrator roles and privileges applicable to storage domain administration.
| Role | Privileges | Notes |
|---|---|---|
| StorageAdmin | Storage Administrator | Can create, delete, configure and manage a specific storage domain. |
| GlusterAdmin | Gluster Storage Administrator | Can create, delete, configure and manage Gluster storage volumes. |
1.2.17. Managing System Permissions for a Virtual Machine Pool
As the SuperUser, the system administrator manages all aspects of the Administration Portal. More specific administrative roles can be assigned to other users. These restricted administrator roles are useful for granting a user administrative privileges that limit them to a specific resource. For example, a DataCenterAdmin role has administrator privileges only for the assigned data center with the exception of the storage for that data center, and a ClusterAdmin has administrator privileges only for the assigned cluster.
A virtual machine pool administrator is a system administration role for virtual machine pools in a data center. This role can be applied to specific virtual machine pools, to a data center, or to the whole virtualized environment; this is useful to allow different users to manage certain virtual machine pool resources.
The virtual machine pool administrator role permits the following actions:
- Create, edit, and remove pools.
- Add and detach virtual machines from the pool.
You can only assign roles and permissions to existing users.
1.2.18. Virtual Machine Pool Administrator Roles Explained
Pool Permission Roles
The table below describes the administrator roles and privileges applicable to pool administration.
| Role | Privileges | Notes |
|---|---|---|
| VmPoolAdmin | System Administrator role of a virtual pool. | Can create, delete, and configure a virtual pool, assign and remove virtual pool users, and perform basic operations on a virtual machine. |
| ClusterAdmin | Cluster Administrator | Can use, create, delete, manage all virtual machine pools in a specific cluster. |
1.2.19. Managing System Permissions for a Virtual Disk
As the SuperUser, the system administrator manages all aspects of the Administration Portal. More specific administrative roles can be assigned to other users. These restricted administrator roles are useful for granting a user administrative privileges that limit them to a specific resource. For example, a DataCenterAdmin role has administrator privileges only for the assigned data center with the exception of the storage for that data center, and a ClusterAdmin has administrator privileges only for the assigned cluster.
Red Hat Virtualization Manager provides two default virtual disk user roles, but no default virtual disk administrator roles. One of these user roles, the DiskCreator role, enables the administration of virtual disks from the VM Portal. This role can be applied to specific virtual machines, to a data center, to a specific storage domain, or to the whole virtualized environment; this is useful to allow different users to manage different virtual resources.
The virtual disk creator role permits the following actions:
- Create, edit, and remove virtual disks associated with a virtual machine or other resources.
- Edit user permissions for virtual disks.
You can only assign roles and permissions to existing users.
1.2.20. Virtual Disk User Roles Explained
Virtual Disk User Permission Roles
The table below describes the user roles and privileges applicable to using and administrating virtual disks in the VM Portal.
| Role | Privileges | Notes |
|---|---|---|
| DiskOperator | Virtual disk user. | Can use, view and edit virtual disks. Inherits permissions to use the virtual machine to which the virtual disk is attached. |
| DiskCreator | Can create, edit, manage and remove virtual disks within assigned clusters or data centers. | This role is not applied to a specific virtual disk; apply this role to a user for the whole environment with the Configure window. Alternatively apply this role for specific data centers, clusters, or storage domains. |
1.2.21. Setting a Legacy SPICE Cipher
SPICE consoles use FIPS-compliant encryption by default, with a cipher string. The default SPICE cipher string is: kECDHE+FIPS:kDHE+FIPS:kRSA+FIPS:!eNULL:!aNULL
This string is generally sufficient. However, if you have a virtual machine with an older operating system or SPICE client, where either one or the other does not support FIPS-compliant encryption, you must use a weaker cipher string. Otherwise, a connection security error may occur if you install a new cluster or a new host in an existing cluster and try to connect to that virtual machine.
You can change the cipher string by using an Ansible playbook.
Changing the cipher string
On the Manager machine, create a file in the directory
/usr/share/ovirt-engine/playbooks. For example:vim /usr/share/ovirt-engine/playbooks/change-spice-cipher.yml
# vim /usr/share/ovirt-engine/playbooks/change-spice-cipher.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following in the file and save it:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the file you just created:
ansible-playbook -l hostname /usr/share/ovirt-engine/playbooks/change-spice-cipher.yml
# ansible-playbook -l hostname /usr/share/ovirt-engine/playbooks/change-spice-cipher.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can reconfigure the host with the Ansible playbook ovirt-host-deploy using the --extra-vars option with the variable host_deploy_spice_cipher_string, as follows:
ansible-playbook -l hostname \ --extra-vars host_deploy_spice_cipher_string=”DEFAULT:-RC4:-3DES:-DES” \ /usr/share/ovirt-engine/playbooks/ovirt-host-deploy.yml
# ansible-playbook -l hostname \
--extra-vars host_deploy_spice_cipher_string=”DEFAULT:-RC4:-3DES:-DES” \
/usr/share/ovirt-engine/playbooks/ovirt-host-deploy.yml