Este contenido no está disponible en el idioma seleccionado.
Chapter 1. Getting Started
This chapter covers the basic tasks that you might need to perform just after you have installed Red Hat Enterprise Linux 7.
Note that these items may include tasks that are usually done already during the installation process, but they do not have to be done necessarily, such as the registration of the system. The subchapters dealing with such tasks provide a brief summary of how this can be achieved during the installation and links to related documentation in a special section.
For detailed information on Red Hat Enterprise Linux 7 installation, consult Red Hat Enterprise Linux 7 Installation Guide.
This chapter mentions some commands to be performed. The commands that need to be entered by the root user have # in the prompt, while the commands that can be performed by a regular user, have $ in their prompt.
For further information on common post-installation tasks, you can see also Red Hat Enterprise Linux 7 Installation Guide.
Although all post-installation tasks can be achieved through the command line, you can also use the web console tool to perform some of them.
What web console Is and Which Tasks It Can Be Used For
web console is a system administration tool that provides a user interface for monitoring and administering servers through a web browser.
web console enables to perform these tasks:
- Monitoring basic system features, such as hardware, internet connection, or performance characteristics
- Analyzing the content of the system log files
- Configuring basic networking features, such as interfaces, network logs, packet sizes
- Managing user accounts
- Monitoring and configuring system services
- Creating diagnostic reports
- Setting kernel dump configuration
- Configuring SELinux
- Managing system subscriptions
- Accessing the terminal
For more information on installing and using web console, see Managing systems using the RHEL 7 web console.
1.1. Basic Configuration of the Environment
Basic configuration of the environment includes:
- Date and Time
- System Locales
- Keyboard Layout
Setting of these items is normally a part of the installation process.
For more information, see the appropriate source according to the installation method:
When installing with the Anaconda installer, see:
Date&Time, Language Support and Keyboard Configuration in Red Hat Enterprise Linux 7 Installation Guide
When installing with the Kickstart file, consult:
Kickstart Commands and Options in Red Hat Enterprise Linux 7 Installation Guide.
If you need to reconfigure the basic characteristics of the environment after the installation, follow the instructions in this section.
1.1.1. Introduction to Configuring the Date and Time
Accurate time keeping is important for a number of reasons. In Red Hat Enterprise Linux 7, time keeping is ensured by the NTP protocol, which is implemented by a daemon running in user space. The user space daemon updates the system clock running in the kernel. The system clock can keep time by using various clock sources.
Red Hat Enterprise Linux 7 uses the following daemons to implement NTP:
chronydThe
chronyddaemon is used by default. It is available from the chrony package. For more information on configuring and usingNTPwithchronyd, see Chapter 18, Configuring NTP Using the chrony Suite.ntpdThe
ntpddaemon is available from the ntp package. For more information on configuring and usingNTPwithntpd, see Chapter 19, Configuring NTP Using ntpd.
If you want to use ntpd instead of default chronyd, you need to disable chronyd, install, enable and configure ntpd as shown in Chapter 19, Configuring NTP Using ntpd.
Displaying the Current Date and Time
To display the current date and time, use one of the following commands:
date
~]$ datetimedatectl
~]$ timedatectl
Note that the timedatectl command provides more verbose output, including universal time, currently used time zone, the status of the Network Time Protocol (NTP) configuration, and some additional information.
For more information on configuring the date and time, see Chapter 3, Configuring the Date and Time.
1.1.2. Introduction to Configuring the System Locale
System-wide locale settings are stored in the /etc/locale.conf file, which is read at early boot by the systemd daemon. The locale settings configured in /etc/locale.conf are inherited by every service or user, unless individual programs or individual users override them.
Basic tasks to handle the system locales:
Listing available system locale settings:
localectl list-locales
~]$ localectl list-localesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Displaying current status of the system locales settings:
localectl status
~]$ localectl statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow Setting or changing the default system locale settings:
localectl set-locale LANG=locale
~]# localectl set-locale LANG=localeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information on configuring the system locale, see Chapter 2, System Locale and Keyboard Configuration.
1.1.3. Introduction to Configuring the Keyboard Layout
The keyboard layout settings control the layout used on the text console and graphical user interfaces.
Basic tasks to handle the keyboard layout include:
Listing available keymaps:
localectl list-keymaps
~]$ localectl list-keymapsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Displaying current status of keymap settings:
localectl status
~]$ localectl statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow Setting or changing the default system keymap:
localectl set-keymap
~]# localectl set-keymapCopy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information on configuring the keyboard layout, see Chapter 2, System Locale and Keyboard Configuration.
1.2. Configuring and Inspecting Network Access
The network access is usually configured during the installation process. However, the installation process does not prompt you to configure network interfaces on some common installation paths. Consequently, it is possible that the network access is not configured after the installation. If this happens, you can configure network access after installation.
For a quickstart to configuring network access during the installation, see Section 1.2.1, “Configuring Network Access During the Installation Process”. To configure network access after the installation, you can use either the nmcli command-line utility, described in Red Hat Enterprise Linux 7 Networking Guide or the nmtui text user interface utility, described in Red Hat Enterprise Linux 7 Networking Guide.
The nmcli and nmtui utilities also enable you to add one or more new network connections, as well as modify and inspect the existing connections. If you want to create and manage network connections with nmcli, see Section 1.2.2, “Managing Network Connections After the Installation Process Using nmcli”. If you want to create and manage network connections with nmtui, see Section 1.2.3, “Managing Network Connections After the Installation Process Using nmtui”.
1.2.1. Configuring Network Access During the Installation Process
Ways to configure network access during the installation proces:
- The menu at the Installation Summary screen in the graphical user interface of the Anaconda installation program
- The option in the text mode of the Anaconda installation program
- The Kickstart file
When the system boots for the first time after the installation has finished, any network interfaces which you configured during the installation are automatically activated.
For detailed information on configuration of network access during installation process, see Red Hat Enterprise Linux 7 Installation Guide.
1.2.2. Managing Network Connections After the Installation Process Using nmcli
Run the following commands as the root user to manage network connections using the nmcli utility.
To create a new connection:
nmcli con add type type of the connection "con-name" connection name ifname ifname interface-name the name of the interface ipv4 address ipv4 address gw4 address gateway address
~]# nmcli con add type type of the connection "con-name" connection name ifname ifname interface-name the name of the interface ipv4 address ipv4 address gw4 address gateway addressTo modify the existing connection:
nmcli con mod "con-name"
~]# nmcli con mod "con-name"To display all connections:
nmcli con show
~]# nmcli con showTo display the active connection:
nmcli con show --active
~]# nmcli con show --activeTo display all configuration settings of a particular connection:
nmcli con show "con-name"
~]# nmcli con show "con-name"For more information on the nmcli command-line utility, see Red Hat Enterprise Linux 7 Networking Guide.
1.2.3. Managing Network Connections After the Installation Process Using nmtui
The NetworkManager text user interface (TUI) utility, nmtui, provides a text interface to configure networking by controlling NetworkManager.
For more information about installing and using the nmtui text interface tool, see Red Hat Enterprise Linux 7 Networking Guide.
1.2.4. Managing Networking in web console
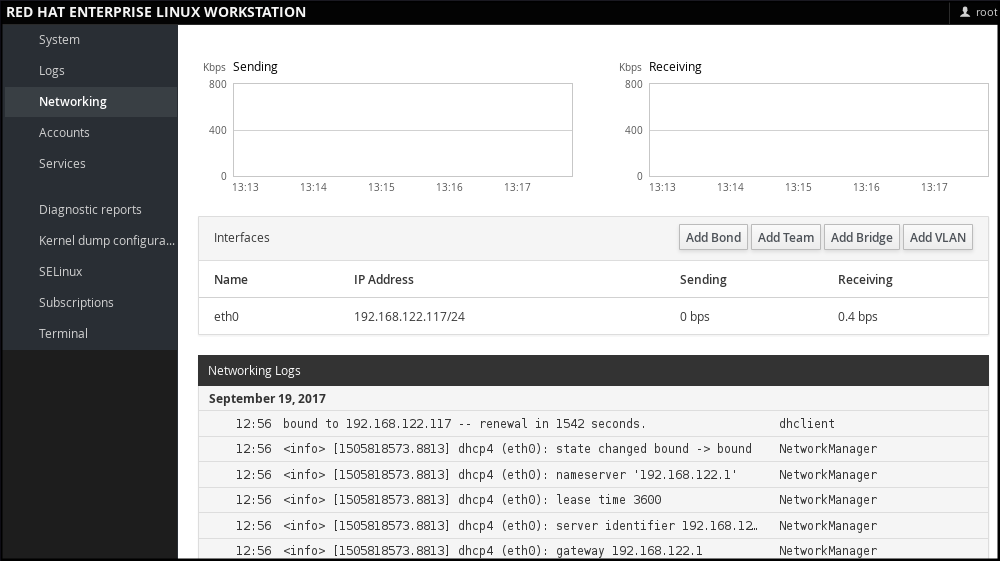
In web console, the menu enables you:
- To display currently received and sent packets
- To display the most important characteristics of available network interfaces
- To display content of the networking logs.
- To add various types of network interfaces (bond, team, bridge, VLAN)
Figure 1.1. Managing Networking in web console
1.3. The Basics of Registering the System and Managing Subscriptions
1.3.1. What Red Hat Subscriptions Are and Which Tasks They Can Be Used For
The products installed on Red Hat Enterprise Linux 7, including the operating system itself, are covered by subscriptions.
A subscription to Red Hat Content Delivery Network is used to track:
- Registered systems
- Products installed on those system
- Subscriptions attached to those product
1.3.2. Registering the System During the Installation
This section provides a brief summary of registering Red Hat Enterprise Linux 7 during the installation process. If your operating system is not registered after the installation, you can find what might have been missed during the installation by reading through this section. For detailed information, consult Red Hat Enterprise Linux 7 Installation Guide.
Basically, there are two ways to register the system during the installation:
- Normally, registration is a part of the Initial Setup configuration process. For more information, see Red Hat Enterprise Linux 7 Installation Guide.
- Another option is to run Subscription manager as a post-installation script, which performs the automatic registration at the moment when the installation is complete and before the system is rebooted for the first time. To ensure this, modify the %post section of the Kickstart file. For more detailed information on running Subscription manager as a post-installation script, see Red Hat Enterprise Linux 7 Installation Guide.
1.3.3. Registering the System after the Installation
If you have not registered your system during installation process, you can do it afterwards by applying the following procedure. Note that all commands in this procedure need to be performed as the root user.
Registering and Subscribing Your System
Register your system:
subscription-manager register
~]# subscription-manager registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command will prompt you to enter your Red Hat Customer Portal user name and password.
Determine the pool ID of a subscription that you require:
subscription-manager list --available
~]# subscription-manager list --availableCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command displays all available subscriptions for your Red Hat account. For every subscription, various characteristics are displayed, including the pool ID.
Attach the appropriate subscription to your system by replacing pool_id with the pool ID determined in the previous step:
subscription-manager attach --pool=pool_id
~]# subscription-manager attach --pool=pool_idCopy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information on registration of your system and attachment of the Red Hat Content Delivery Network subscriptions, see Chapter 7, Registering the System and Managing Subscriptions.
1.3.4. Registering a System to EUS Content
To access the Extended Update Support (EUS) content, register your system as follows:
Verify that EUS entitlements are available:
subscription-manager list --available --matches="*Extended Update Support"
~]# subscription-manager list --available --matches="*Extended Update Support"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow Attach the applicable subscription using the Pool identifier:
subscription-manager attach --pool 8a99f9ac7238188b01723d9c8a8a06a9
~]# subscription-manager attach --pool 8a99f9ac7238188b01723d9c8a8a06a9Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace the default repositories enabled for the system with the EUS variants:
subscription-manager repos --disable \*
~]# subscription-manager repos --disable \*Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the repositories which represent the EUS content set for the RHEL revision in use:
subscription-manager repos --enable rhel-7-server-eus-rpms
~]# subscription-manager repos --enable rhel-7-server-eus-rpmsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Select the required and supported release for the end system:
subscription-manager release --set 7.6
~]# subscription-manager release --set 7.6Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For currently supported EUS releases, see Extended Update Support Add-on.
1.3.5. Registering a System to E4S Content
The following procedure describes how to register a system and utilize the E4S content.
Register your system using the following command:
subscription-manager register
~]# subscription-manager registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that E4S entitlements are available:
subscription-manager list --available --matches="*Update Services for SAP Solutions*"
~]# subscription-manager list --available --matches="*Update Services for SAP Solutions*"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow Attach the applicable subscription using the Pool identifier:
subscription-manager attach --pool=#################
~]# subscription-manager attach --pool=#################Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace the default repositories enabled for the system with the EUS variants:
subscription-manager repos --disable="*"
~]# subscription-manager repos --disable="*"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the repositories which represent the E4S content set for the RHEL revision in use:
subscription-manager --enable=rhel-7-server-e4s-rpms
~]# subscription-manager --enable=rhel-7-server-e4s-rpmsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Clear the repository cache and release lock the system to a valid release for E4S which supports your SAP application:
yum clean all && subscription-manager release --set=7.7
~]# yum clean all && subscription-manager release --set=7.7Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.4. Installing Software
This section provides information to guide you through the basics of software installation on a Red Hat Enterprise Linux 7 system. It mentions the prerequisites that you need to fulfil to be able to install software in Section 1.4.1, “Prerequisites for Software Installation”, provides the basic information on software packaging and software repositories in Section 1.4.2, “Introduction to the System of Software Packaging and Software Repositories”, and references the ways to perform basic tasks related to software installation in Section 1.4.3, “Managing Basic Software Installation Tasks with Subscription Manager and Yum”.
1.4.1. Prerequisites for Software Installation
The Red Hat Content Delivery Network subscription service provides a mechanism to handle Red Hat software inventory and enables you to install additional software or update already installed packages. You can start installing software once you have registered your system and attached a subscription, as described in Section 1.3, “The Basics of Registering the System and Managing Subscriptions”.
1.4.2. Introduction to the System of Software Packaging and Software Repositories
All software on a Red Hat Enterprise Linux system is divided into RPM packages, which are stored in particular repositories. When a system is subscribed to the Red Hat Content Delivery Network, a repository file is created in the /etc/yum.repos.d/ directory.
Use the yum utility to manage package operations:
- Searching information about packages
- Installing packages
- Updating packages
- Removing packages
- Checking the list of currently available repositories
- Adding or removing a repository
- Enabling or disabling a repository
For information on basic tasks related to the installation of software, see Section 1.4.3, “Managing Basic Software Installation Tasks with Subscription Manager and Yum”. For further information on managing software repositories, see Section 7.2, “Managing Software Repositories”. For detailed information on using the yum utility, see Chapter 9, Yum.
1.4.3. Managing Basic Software Installation Tasks with Subscription Manager and Yum
The most basic software-installation tasks that you might need after the operating system has been installed include:
Listing all available repositories:
subscription-manager repos --list
~]# subscription-manager repos --listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Listing all currently enabled repositories:
yum repolist
~]$ yum repolistCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enabling or disabling a repository:
subscription-manager repos --enable repository
~]# subscription-manager repos --enable repositoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow subscription-manager repos --disable repository
~]# subscription-manager repos --disable repositoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Searching for packages matching a specific string:
yum search string
~]$ yum search stringCopy to Clipboard Copied! Toggle word wrap Toggle overflow Installing a package:
yum install package_name
~]# yum install package_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Updating all packages and their dependencies:
yum update
~]# yum updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow Updating a package:
yum update package_name
~]# yum update package_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Uninstalling a package and any packages that depend on it:
yum remove package_name
~]# yum remove package_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Listing information on all installed and available packages:
yum list all
~]$ yum list allCopy to Clipboard Copied! Toggle word wrap Toggle overflow Listing information on all installed packages:
yum list installed
~]$ yum list installedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
1.5. Making systemd Services Start at Boot Time
Systemd is a system and service manager for Linux operating systems that introduces the concept of systemd units. For more information on systemd, see Section 10.1, “Introduction to systemd”.
This section provides the information on how to ensure that a service is enabled or disabled at boot time. It also explains how to manage the services through web console.
1.5.1. Enabling or Disabling the Services
You can determine services that are enabled or disabled at boot time already during the installation process, or you can enable or disable a service on an installed operating system.
To create the list of services enabled or disabled at boot time during the installation process, use the services option in the Kickstart file:
services [--disabled=list] [--enabled=list]
services [--disabled=list] [--enabled=list]The list of disabled services is processed before the list of enabled services. Therefore, if a service appears on both lists, it will be enabled. The list of the services should be given in the comma separated format. Do not include spaces in the list of services. For detailed information, refer to Red Hat Enterprise Linux 7 Installation Guide.
To enable or disable a service on an already installed operating system:
systemctl enableservice_name
~]# systemctl enableservice_namesystemctl disableservice_name
~]# systemctl disableservice_nameFor further details, see Section 10.2, “Managing System Services”.
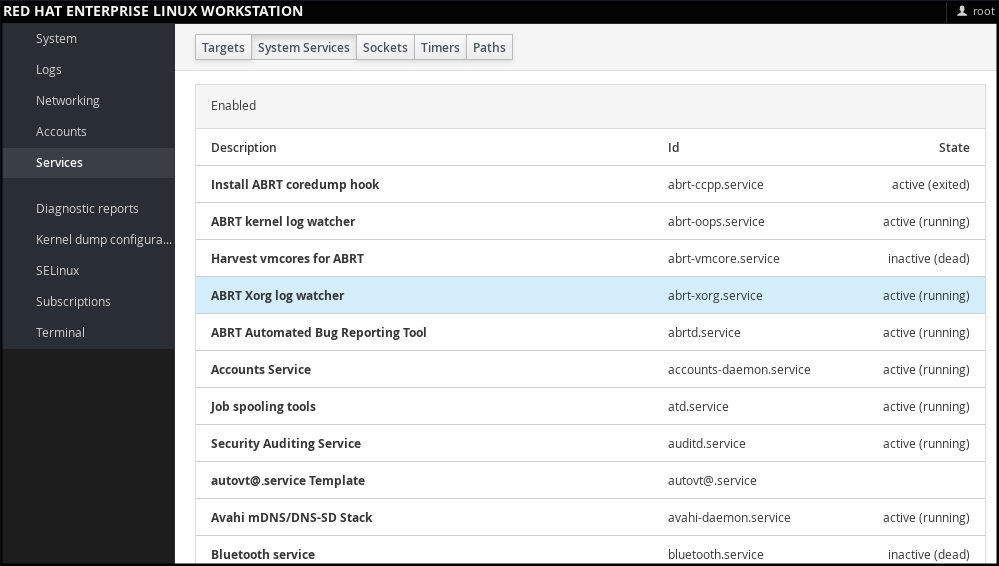
1.5.2. Managing Services in web console
In web console, select to manage systemd targets, services, sockets, timers and paths. There you can check their status, start or stop them, enable or disable them.
Figure 1.2. Managing Services in web console
1.5.3. Additional Resources on systemd Services
For more information on systemd, see Chapter 10, Managing Services with systemd.
1.6. Enhancing System Security with a Firewall, SELinux and SSH Logings
Computer security is the protection of computer systems from the theft or damage to their hardware, software, or information, as well as from disruption or misdirection of the services they provide. Ensuring computer security is therefore an essential task not only in the enterprises processing sensitive data or handling some business transactions.
Computer security includes a wide variety of features and tools. This section covers only the basic security features that you need to configure after you have installed the operating system. For detailed information on securing Red Hat Enterprise Linux 7, see Red Hat Enterprise Linux 7 Security Guide.
1.6.1. Ensuring the Firewall Is Enabled and Running
1.6.1.1. What a Firewall Is and How It Enhances System Security
A firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network.
On Red Hat Enterprise Linux 7, the firewall is provided by the firewalld service, which is automatically enabled during the installation of Red Hat Enterprise Linux. However, if you explicitly disabled the service, for example in the kickstart configuration, you can re-enable it, as described in Section 1.6.1.2, “Re-enabling the firewalld Service”. For overview of firewall setting options in the Kickstart file, see Red Hat Enterprise Linux 7 Installation Guide.
1.6.1.2. Re-enabling the firewalld Service
In case that the firewalld service is disabled after the installation, Red Hat recommends to consider re-enabling it.
You can display the current status of firewalld even as a regular user:
systemctl status firewalld
~]$ systemctl status firewalld
If firewalld is not enabled and running, switch to the root user, and change its status:
systemctl start firewalld
~]# systemctl start firewalldsystemctl enable firewalld
~]# systemctl enable firewalld
For further information on post-installation procedures related to firewalld, see Red Hat Enterprise Linux 7 Security Guide. For detailed information on configuring and using firewall, see Red Hat Enterprise Linux 7 Security Guide
1.6.2. Ensuring the Appropriate State of SELinux
1.6.2.1. What SELinux Is and How It Enhances System Security
Security Enhanced Linux (SELinux) is an additional layer of system security that determines which process can access which files, directories, and ports.
SELinux States
SELinux has two possible states:
- Enabled
- Disabled
When SELinux is disabled, only Discretionary Access Control (DAC) rules are used.
SELinux Modes
When SELinux is enabled, it can run in one of the following modes:
- Enforcing
- Permissive
Enforcing mode means that SELinux policies is enforced. SELinux denies access based on SELinux policy rules, and enables only the interactions that are particularly allowed. Enforcing mode is the default mode after the installation and it is also the safest SELinux mode.
Permissive mode means that SELinux policies is not enforced. SELinux does not deny access, but denials are logged for actions that would have been denied if running in enforcing mode. Permissive mode is the default mode during the installation. Operating in permissive mode is also useful in some specific cases, for example if you require access to the Access Vector Cache (AVC) denials when troubleshooting problems.
For further information on SELinux in Red Hat Enterprise Linux 7, see Red Hat Enterprise Linux 7 SELinux User’s and Administrator’s Guide.
1.6.2.2. Ensuring the Required State of SELinux
By default, SELinux operates in permissive mode during the installation and in enforcing mode when the installation has finished.
However, in some specific situations, SELinux might be explicitly set to permissive mode or it might even be disabled on the installed operating system. This can be set for example in the kickstart configuration. For overview of SELinux setting options in the Kickstart file, see Red Hat Enterprise Linux 7 Installation Guide.
Red Hat recommends to keep your system in enforcing mode.
To display the current SELinux mode, and to set the mode as needed:
Ensuring the Required State of SELinux
Display the current SELinux mode in effect:
getenforce
~]$ getenforceCopy to Clipboard Copied! Toggle word wrap Toggle overflow If needed, switch between the SELinux modes.
The switch can be either temporary or permanent. A temporary switch is not persistent across reboots, while permanent switch is.
To temporary switch to either enforcing or permissive mode:
setenforce Enforcing
~]# setenforce EnforcingCopy to Clipboard Copied! Toggle word wrap Toggle overflow setenforce Permissive
~]# setenforce PermissiveCopy to Clipboard Copied! Toggle word wrap Toggle overflow To permanently set the SELinux mode, modify the SELINUX variable in the
/etc/selinux/configconfiguration file.For example, to switch SELinux to enforcing mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.6.2.3. Managing SELinux in web console
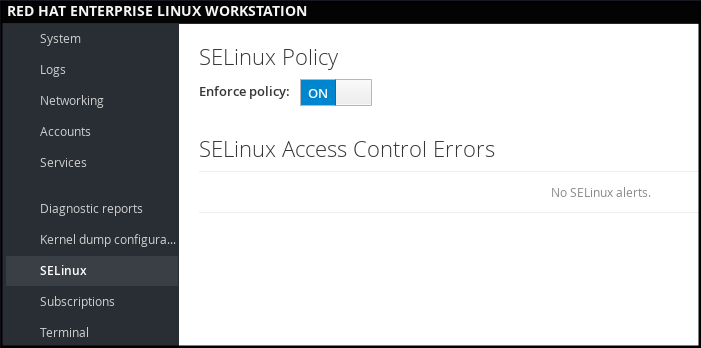
In web console, use the option to turn SELinux enforcing policy on or off.
By default, SELinux enforcing policy in web console is on, and SELinux operates in enforcing mode. By turning it off, you can switch SELinux into permissive mode. Note that such deviation from the default configuration in the /etc/sysconfig/selinux file is automatically reverted on the next boot.
Figure 1.3. Managing SELinux in web console
1.6.3. Using SSH-based Authentication
1.6.3.1. What SSH-based Authentication Is and How It Enhances System Security
If you want to secure your communication with another computer, you can use SSH-based authentication.
Secure Shell (SSH) is a protocol which facilitates client-server communication and allows users to log in to any host system running SSH remotely. SSH encrypts the connection. The client transmits its authentication information to the server using encryption, and all data sent and received during a session are transferred under the encryption.
SSH enables its users to authenticate without a password. To do so, SSH uses a private-public key scheme.
For further information about SSH safeguards, see Section 12.1.2, “Main Features”.
1.6.3.2. Establishing an SSH Connection
To be able to use SSH connection, create a pair of two keys consisting of a public and a private key.
Creating the Key Files and Copying Them to the Server
Generate a public and a private key:
ssh-keygen
~]$ ssh-keygenCopy to Clipboard Copied! Toggle word wrap Toggle overflow Both keys are stored in the
~/.ssh/directory:-
~/.ssh/id_rsa.pub- public key ~/.ssh/id_rsa- private keyThe public key does not need to be secret. It is used to verify the private key. The private key is secret. You can choose to protect the private key with the passphrase that you specify during the key generation process. With the passphrase, authentication is even more secure, but is no longer password-less. You can avoid this using the
ssh-agentcommand. In this case, you will enter the passphrase only once - at the beginning of a session. For more information onssh-agentconfiguration, see Section 12.2.4, “Using Key-based Authentication”.
-
Copy the most recently modified public key to a remote machine you want to log into:
ssh-copy-id USER@hostname
~]# ssh-copy-id USER@hostnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow As a result, you are now able to enter the system in a secure way, but without entering a password.
1.6.3.3. Disabling SSH Root Login
To increase system security, you can disable SSH access for the root user, which is enabled by default.
For more information on this topic, see Red Hat Enterprise Linux 7 Security Guide.
Disabling SSH Root Login
Access the
/etc/ssh/sshd_configfile:vi /etc/ssh/sshd_config
~]# vi /etc/ssh/sshd_configCopy to Clipboard Copied! Toggle word wrap Toggle overflow Change the line that reads
#PermitRootLogin yesto:PermitRootLogin no
PermitRootLogin noCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
sshdservice:systemctl restart sshd
~]# systemctl restart sshdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
1.7. The Basics of Managing User Accounts
Red Hat Enterprise Linux 7 is a multi-user operating system, which enables multiple users on different computers to access a single system installed on one machine. Every user operates under its own account, and managing user accounts thus represents a core element of Red Hat Enterprise Linux system administration.
Normal and System Accounts
Normal accounts are created for users of a particular system. Such accounts can be added, removed, and modified during normal system administration.
System accounts represent a particular applications identifier on a system. Such accounts are generally added or manipulated only at software installation time, and they are not modified later.
System accounts are presumed to be available locally on a system. If these accounts are configured and provided remotely, such as in the instance of an LDAP configuration, system breakage and service start failures can occur.
For system accounts, user IDs below 1000 are reserved. For normal accounts, you can use IDs starting at 1000. However, the recommended practice is to assign IDs starting at 5000. See Section 4.1, “Introduction to Users and Groups” for more information. The guidelines for assigning IDs can be found in the /etc/login.defs file.
What Groups Are and Which Purposes They Can Be Used For
A group is an entity which ties together multiple user accounts for a common purpose, such as granting access to particular files.
1.7.1. The Most Basic Command-Line Tools to Manage User Accounts and Groups
The most basic tasks to manage user accounts and groups, and the appropriate command-line tools, include:
Displaying user and group IDs:
id
~]$ idCopy to Clipboard Copied! Toggle word wrap Toggle overflow Creating a new user account:
useradd [options] user_name
~]# useradd [options] user_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Assigning a new password to a user account belonging to username:
passwd user_name
~]# passwd user_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Adding a user to a group:
usermod -a -G group_name user_name
~]# usermod -a -G group_name user_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow
For detailed information on managing users and groups, see Chapter 4, Managing Users and Groups.
If you want to use graphical user interface to manage users and groups, see Section 4.2, “Managing Users in a Graphical Environment”.
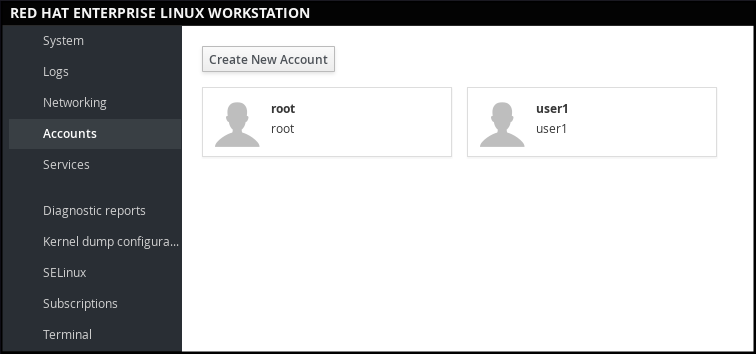
1.7.2. Managing User Accounts in web console
To manage accounts in web console, select the menu.
Figure 1.4. Managing User Accounts in web console
1.8. Dumping the Crashed Kernel Using the kdump Mechanism
This section provides an introduction to the Kernel crash dump mechanism, also called kdump, and briefly explains what kdump is used for in Section 1.8.1, “What kdump Is and Which Tasks It Can Be Used For”.
Activation of the kdump service is a part of the installation process, and by default, kdump was enabled during the installation. This section summarizes how to activate kdump during the installation in Section 1.8.2, “Enabling and Activating kdump During the Installation Process”, and how to manually enable the kdump service if it is disabled after the installation in Section 1.8.3, “Ensuring That kdump Is Installed and Enabled after the Installation Process”.
You can also use web console to configure kdump. See Section 1.8.4, “Configuring kdump in web console” for more information.
1.8.1. What kdump Is and Which Tasks It Can Be Used For
In case of a system crash, you can use the Kernel crash dump mechanism called kdump that enables you to save the content of the system’s memory for later analysis. The kdump mechanism relies on the kexec system call, which can be used to boot a Linux kernel from the context of another kernel, bypass BIOS, and preserve the contents of the first kernel’s memory that would otherwise be lost.
When kernel crash occurs, kdump uses kexec to boot into a second kernel (a capture kernel), which resides in a reserved part of the system memory that is inaccessible to the first kernel. The second kernel captures the contents of the crashed kernel’s memory (a crash dump) and saves it.
1.8.2. Enabling and Activating kdump During the Installation Process
During the installation, enablement and activation of kdump can be done either in the Anaconda installer or using the %addon com_redhat_kdump command in the Kickstart file.
For more information, see the appropriate source according to the installation method:
When installing with the Anaconda installer, see:
Installing Using Anaconda in Red Hat Enterprise Linux 7 Installation Guide.
When installing with the Kickstart file, see:
Kickstart Commands and Options in Red Hat Enterprise Linux 7 Installation Guide.
1.8.3. Ensuring That kdump Is Installed and Enabled after the Installation Process
To ensure that kdump is installed and to configure it:
Checking Whether kdump Is Installed and Configuring kdump
To check whether kdump is installed on your system:
rpm -q kexec-tools
~]$ rpm -q kexec-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow If not installed, to install kdump, enter as the
rootuser:yum install kexec-tools
~]# yum install kexec-toolsCopy to Clipboard Copied! Toggle word wrap Toggle overflow To configure kdump:
Use either the command line or graphical user interface.
Both options are described in detail in Red Hat Enterprise Linux 7 Kernel Crash Dump Guide.
If you need to install the graphical configuration tool:
yum install system-config-kdump
~]# yum install system-config-kdumpCopy to Clipboard Copied! Toggle word wrap Toggle overflow
1.8.4. Configuring kdump in web console
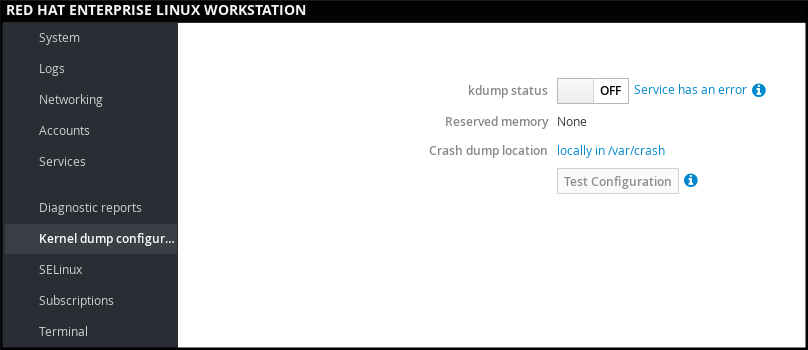
In web console, select to verify:
- the kdump status
- the amount of memory reserved for kdump
- the location of the crash dump files
Figure 1.5. Configuring kdump in web console
1.8.5. Additional Resources on kdump
For more information on kdump, see Red Hat Enterprise Linux 7 Kernel Crash Dump Guide.
1.9. Performing System Rescue and Creating System Backup with ReaR
When a software or hardware failure breaks the operating system, you need a mechanism to rescue the system. It is also useful to have the system backup saved. Red Hat recommends using the Relax-and-Recover (ReaR) tool to fulfil both these needs.
1.9.1. What ReaR Is and Which Tasks It Can Be Used For
ReaR is a disaster recovery and system migration utility which enables you to create the complete rescue system. By default, this rescue system restores only the storage layout and the boot loader, but not the actual user and system files.
Additionally, certain backup software enables you to integrate ReaR for disaster recovery.
ReaR enables to perform the following tasks:
- Booting a rescue system on the new hardware
- Replicating the original storage layout
- Restoring user and system files
1.9.2. Quickstart to Installation and Configuration of ReaR
To install ReaR, enter as the root user:
yum install rear
~]# yum install rear
Use the settings in the /etc/rear/local.conf file to configure ReaR.
For further information see, Section 27.1, “Basic ReaR Usage”.
1.9.3. Quickstart to Creation of the Rescue System with ReaR
- To create the rescue system, perform the following command as the
rootuser
rear mkrescue
~]# rear mkrescueFor further information on creating the rescue system with ReaR, see Section 27.1.3, “Creating a Rescue System”.
1.9.4. Quickstart to Configuration of ReaR with the Backup Software
ReaR contains a fully-integrated built-in, or internal, backup method called NETFS.
To make ReaR use its internal backup method, add these lines to the /etc/rear/local.conf file:
BACKUP=NETFS BACKUP_URL=backup location
BACKUP=NETFS
BACKUP_URL=backup location
You can also configure ReaR to keep the previous backup archives when the new ones are created by adding the following line to /etc/rear/local.conf:
NETFS_KEEP_OLD_BACKUP_COPY=y
NETFS_KEEP_OLD_BACKUP_COPY=y
To make the backups incremental, meaning that only the changed files are backed up on each run, add this line to /etc/rear/local.conf:
BACKUP_TYPE=incremental
BACKUP_TYPE=incrementalFor detailed information about using the ReaR NETFS internal backup method, see Section 27.2.1, “The Built-in Backup Method”.
For information on supported external backup methods and unsupported backup methods, see Section 27.2.2, “Supported Backup Methods” and Section 27.2.3, “Unsupported Backup Methods”.
1.10. Using the Log Files to Troubleshoot Problems
When troubleshooting a problem, you may appreciate the log files that contain different information and messages about the operating system. The logging system in Red Hat Enterprise Linux 7 is based on the built-in syslog protocol. Particular programs use this system to record events and organize them into log files, which are useful when auditing the operating system and troubleshooting various problems.
For more information on log files, see Chapter 23, Viewing and Managing Log Files.
1.10.1. Services Handling the syslog Messages
The syslog messages are handled by two services:
-
the
systemd-journalddaemon - Collects messages from the kernel, the early stages of the boot process, standard output and error of daemons as they start up and run, and syslog, and forwards the messages to thersyslogservice for further processing. -
the
rsyslogservice - Sorts the syslog messages by type and priority, and writes them to the files in the/var/logdirectory, where the logs are persistently stored.
1.10.2. Subdirectories Storing the syslog Messages
The syslog messages are stored in various subdirectories under the /var/log directory according to what kind of messages and logs they contain:
-
var/log/messages- all syslog messages except those mentioned below -
var/log/secure- security and authentication-related messages and errors -
var/log/maillog- mail server-related messages and errors -
var/log/cron- log files related to periodically executed tasks -
var/log/boot.log- log files related to system startup
1.11. Accessing Red Hat Support
To obtain support from Red Hat, use the Red Hat Customer Portal, which provides access to everything available with your subscription.
This section describes:
- Obtaining Red Hat support, see Section 1.11.1, “Obtaining Red Hat Support Through Red Hat Customer Portal”
- Using the SOS report to troubleshoot problems, see Section 1.11.2, “Using the SOS Report to Troubleshoot Problems”
1.11.1. Obtaining Red Hat Support Through Red Hat Customer Portal
By using the Red Hat Customer Portal you can:
- Open a new support case
- Initiate a live chat with a Red Hat expert
- Contact a Red Hat expert by making a call or sending an email
To access the Red Hat Customer Portal, go to https://access.redhat.com..
To work with Red Hat Customer Portal services related to Red Hat support, you can use:
- Web browser
- Red Hat Support Tool
1.11.1.1. What the Red Hat Support Tool Is and Which Tasks It Can Be Used For
The Red Hat Support Tool is a command-line based tool which provides a text console interface to the subscription-based Red Hat access services. This tool is contained in the redhat-support-tool package.
The Red Hat Support Tool enables you to perform support-related tasks, such as:
- Opening or updating support cases
- Searching in the Red Hat knowledge base solutions
- Analyzing Python and Java errors
To start the tool in interactive mode:
redhat-support-tool Welcome to the Red Hat Support Tool. Command (? for help):
~]$ redhat-support-tool
Welcome to the Red Hat Support Tool.
Command (? for help):In interactive mode, enter to display the available commands:
Command (? for help): ?
Command (? for help): ?For more information about the installation and use of the Red Hat Support Tool, see Chapter 8, Accessing Support Using the Red Hat Support Tool, and the Red Hat Knowledgebase article Red Hat Access: Red Hat Support Tool.
1.11.2. Using the SOS Report to Troubleshoot Problems
The SOS report collects configuration details, system information and diagnostic information from a Red Hat Enterprise Linux system. Attach the report when you open a support case.
Note that the SOS report is provided in the sos package, which is not installed with the default minimal installation of Red Hat Enterprise Linux 7.
To install the sos package:
yum install sos
~]# yum install sosTo generate an SOS report:
sosreport
~]# sosreportTo attach the sos report to your support case, see the Red Hat Knowledgebase article How can I attach a file to a Red Hat support case?. Note that you will be prompted to enter the number of the support case, when attaching the sos report.
For more information on SOS report, see the Red Hat Knowledgebase article What is a sosreport and how to create one in Red Hat Enterprise Linux 4.6 and later?.