Ce contenu n'est pas disponible dans la langue sélectionnée.
2.7. Firewall Configuration
The Firewall Configuration window is similar to the screen in the installation program and the Security Level Configuration Tool.
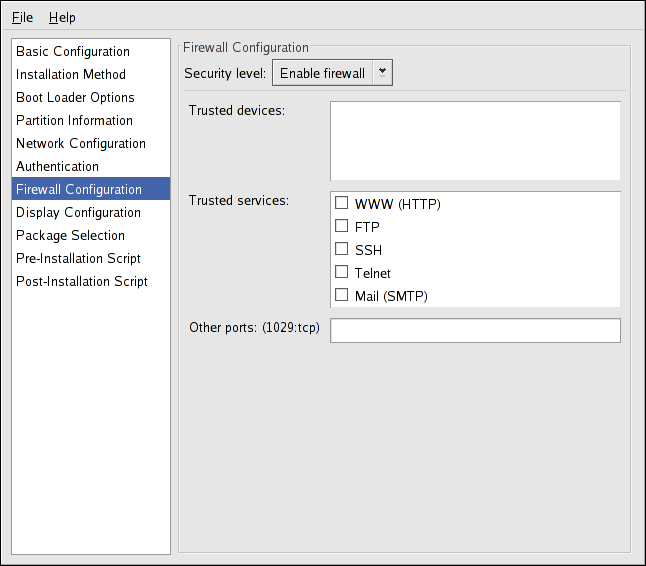
Figure 2.10. Firewall Configuration
If Disable firewall is selected, the system allows complete access to any active services and ports. No connections to the system are refused or denied.
Selecting Enable firewall configures the system to reject incoming connections that are not in response to outbound requests, such as DNS replies or DHCP requests. If access to services running on this machine is required, you can choose to allow specific services through the firewall.
Only devices configured in the Network Configuration section are listed as available Trusted devices. Connections from any devices selected in the list are accepted by the system. For example, if eth1 only receives connections from internal system, you might want to allow connections from it.
If a service is selected in the Trusted services list, connections for the service are accepted and processed by the system.
In the Other ports text field, list any additional ports that should be opened for remote access. Use the following format:
port:protocol. For example, to allow IMAP access through the firewall, specify imap:tcp. Specify numeric ports can also be specified; to allow UDP packets on port 1234 through the firewall, enter 1234:udp. To specify multiple ports, separate them with commas.
2.7.1. SELinux Configuration
Copier lienLien copié sur presse-papiers!
Although configuration for SELinux is not specified in the Kickstart Configurator, kickstart enables SELinux in
enforcing mode by default if the selinux parameter is omitted from the kickstart file.