Questo contenuto non è disponibile nella lingua selezionata.
31.2. Configuring Host-based Access Control in an IdM Domain
- ImportantDo not disable the
allow_allrule before creating custom HBAC rules. If you do this, no users will be able to access any hosts.
31.2.1. Creating HBAC Rules
- the IdM web UI (see the section called “Web UI: Creating an HBAC Rule”)
- the command line (see the section called “Command Line: Creating HBAC Rules”)
gidNumber attribute instead of a link to an IdM group object. For this reason, an HBAC rule can only reference a user's supplementary groups and not its primary group.
Web UI: Creating an HBAC Rule
- Select
. - Click to start adding a new rule.
- Enter a name for the rule, and click to go directly to the HBAC rule configuration page.
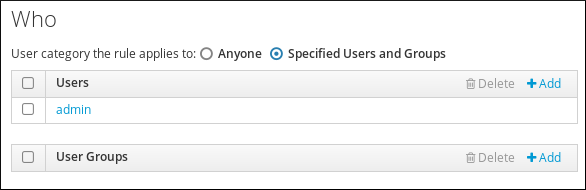
- In the Who area, specify the target users.
- To apply the HBAC rule to specified users or groups only, select Specified Users and Groups. Then click to add the users or groups.
- To apply the HBAC rule to all users, select Anyone.
Figure 31.2. Specifying a Target User for an HBAC Rule
- In the Accessing area, specify the target hosts:
- To apply the HBAC rule to specified hosts or groups only, select Specified Hosts and Groups. Then click to add the hosts or groups.
- To apply the HBAC rule to all hosts, select Any Host.
- In the Via Service area, specify the target HBAC services:
- To apply the HBAC rule to specified services or groups only, select Specified Services and Groups. Then click to add the services or groups.
- To apply the HBAC rule to all services, select Any Service.
NoteOnly the most common services and service groups are configured for HBAC rules by default.- To display the list of services that are currently available, select
. - To display the list of service groups that are currently available, select
.
To add more services and service groups, see Section 31.3, “Adding HBAC Service Entries for Custom HBAC Services” and Section 31.4, “Adding HBAC Service Groups”. - Changing certain settings on the HBAC rule configuration page highlights the button at the top of the page. If this happens, click the button to confirm the changes.
Command Line: Creating HBAC Rules
- Use the ipa hbacrule-add command to add the rule.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Specify the target users.
- To apply the HBAC rule to specified users or groups only, use the ipa hbacrule-add-user command.For example, to add a group:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To add multiple users or groups, use the--usersand--groupsoptions:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To apply the HBAC rule to all users, use the ipa hbacrule-mod command and specify the
alluser category:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the HBAC rule is associated with individual users or groups, ipa hbacrule-mod --usercat=all fails. In this situation, remove the users and groups using the ipa hbacrule-remove-user command.For details, run ipa hbacrule-remove-user with the--helpoption.
- Specify the target hosts.
- To apply the HBAC rule to specified hosts or groups only, use the ipa hbacrule-add-host command.For example, to add a single host:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To add multiple hosts or groups, use the--hostsand--hostgroupsoptions:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - To apply the HBAC rule to all hosts, use the ipa hbacrule-mod command and specify the
allhost category:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the HBAC rule is associated with individual hosts or groups, ipa hbacrule-mod --hostcat=all fails. In this situation, remove the hosts and groups using the ipa hbacrule-remove-host command.For details, run ipa hbacrule-remove-host with the--helpoption.
- Specify the target HBAC services.
- To apply the HBAC rule to specified services or groups only, use the ipa hbacrule-add-service command.For example, to add a single service:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To add multiple services or groups, you can use the--hbacsvcsand--hbacsvcgroupsoptions:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteOnly the most common services and service groups are configured for HBAC rules. To add more, see Section 31.3, “Adding HBAC Service Entries for Custom HBAC Services” and Section 31.4, “Adding HBAC Service Groups”. - To apply the HBAC rule to all services, use the ipa hbacrule-mod command and specify the
allservice category:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the HBAC rule is associated with individual services or groups, ipa hbacrule-mod --servicecat=all fails. In this situation, remove the services and groups using the ipa hbacrule-remove-service command.For details, run ipa hbacrule-remove-service with the--helpoption.
- Optional. Verify that the HBAC rule has been added correctly.
- Use the ipa hbacrule-find command to verify that the HBAC rule has been added to IdM.
- Use the ipa hbacrule-show command to verify the properties of the HBAC rule.
For details, run the commands with the--helpoption.
Examples of HBAC Rules
Example 31.1. Granting a Single User Access to All Hosts Using Any Service
admin user to access all systems in the domain using any service, create a new HBAC rule and set:
- the user to
admin - the host to Any host (in the web UI), or use
--hostcat=allwith ipa hbacrule-add (when adding the rule) or ipa hbacrule-mod - the service to Any service (in the web UI), or use
--servicecat=allwith ipa hbacrule-add (when adding the rule) or ipa hbacrule-mod
Example 31.2. Ensuring That Only Specific Services Can Be Used to Access a Host
sudo-related services to access the host named host.example.com, create a new HBAC rule and set:
- the user to Anyone (in the web UI), or use
--usercat=allwith ipa hbacrule-add (when adding the rule) or ipa hbacrule-mod - the host to
host.example.com - the HBAC service group to
Sudo, which is a default group forsudoand related services
31.2.2. Testing HBAC Rules
- the IdM web UI (see the section called “Web UI: Testing an HBAC Rule”)
- the command line (see the section called “Command Line: Testing an HBAC Rule”)
Web UI: Testing an HBAC Rule
- Select
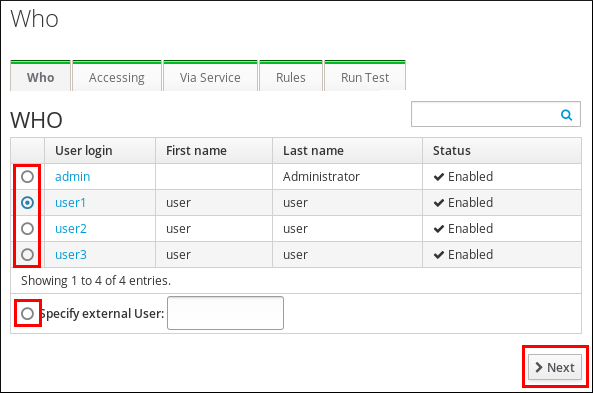
. - On the Who screen: Specify the user under whose identity you want to perform the test, and click .
Figure 31.3. Specifying the Target User for an HBAC Test
- On the Accessing screen: Specify the host that the user will attempt to access, and click .
- On the Via Service screen: Specify the service that the user will attempt to use, and click .
- On the Rules screen: Select the HBAC rules you want to test, and click . If you do not select any rule, all rules will be tested.Select Include Enabled to run the test on all rules whose status is
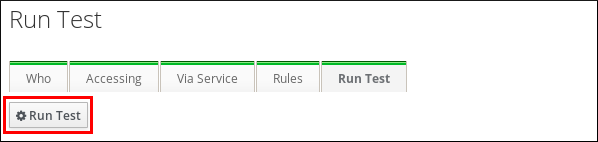
Enabled. Select Include Disabled to run the test on all rules whose status isDisabled. To view and change the status of HBAC rules, select. ImportantIf the test runs on multiple rules, it will pass successfully if at least one of the selected rules allows access. - On the Run Test screen: Click .
Figure 31.4. Running an HBAC Test
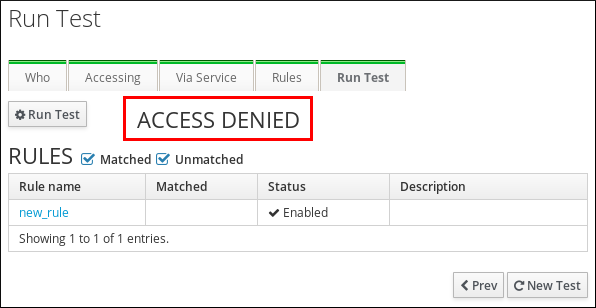
- Review the test results:
- If you see
ACCESS DENIED, the user was not granted access in the test. - If you see
ACCESS GRANTED, the user was able to access the host successfully.
Figure 31.5. Reviewing HBAC Test Results
By default, IdM lists all the tested HBAC rules when displaying the test results.- Select Matched to display the rules that allowed successful access.
- Select Unmatched to display the rules that prevented access.
Command Line: Testing an HBAC Rule
- the user under whose identity you want to perform the test
- the host that the user will attempt to access
- the service that the user will attempt to use
enabled. To specify different HBAC rules:
- Use the
--rulesoption to define one or more HBAC rules. - Use the
--disabledoption to test all HBAC rules whose status isdisabled.
Example 31.3. Testing an HBAC Rule from the Command Line
rule2 prevented user1 from accessing example.com using the sudo service:
ipa hbactest --user=user1 --host=example.com --service=sudo --rules=rule1
$ ipa hbactest --user=user1 --host=example.com --service=sudo --rules=rule1
---------------------
Access granted: False
---------------------
Not matched rules: rule1Example 31.4. Testing Multiple HBAC Rules from the Command Line
Matched ruleslist the rules that allowed successful access.Not matched ruleslist the rules that prevented access.
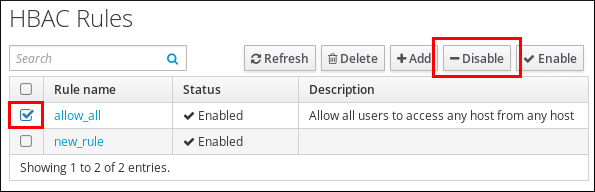
31.2.3. Disabling HBAC Rules
allow_all HBAC rule, you must disable allow_all.
- the IdM web UI (see the section called “Web UI: Disabling an HBAC Rule”)
- the command line (see the section called “Command Line: Disabling an HBAC Rule”)
Web UI: Disabling an HBAC Rule
- Select
. - Select the HBAC rule you want to disable, and click .
Figure 31.6. Disabling the allow_all HBAC Rule
Command Line: Disabling an HBAC Rule
allow_all rule:
ipa hbacrule-disable allow_all
$ ipa hbacrule-disable allow_all
------------------------------
Disabled HBAC rule "allow_all"
------------------------------