Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 9. Tutorial: Configuring Microsoft Entra ID (formerly Azure Active Directory) as an identity provider
You can configure Microsoft Entra ID (formerly Azure Active Directory) as the cluster identity provider in Red Hat OpenShift Service on AWS.
This tutorial guides you to complete the following tasks:
- Register a new application in Entra ID for authentication.
- Configure the application registration in Entra ID to include optional and group claims in tokens.
- Configure the Red Hat OpenShift Service on AWS cluster to use Entra ID as the identity provider.
- Grant additional permissions to individual groups.
9.1. Prerequisites
- You created a set of security groups and assigned users by following the Microsoft documentation.
9.2. Registering a new application in Entra ID for authentication
To register your application in Entra ID, first create the OAuth callback URL, then register your application.
Procedure
Create the cluster’s OAuth callback URL by changing the specified variables and running the following command:
NoteRemember to save this callback URL; it will be required later in the process.
domain=$(rosa describe cluster -c <cluster_name> | grep "DNS" | grep -oE '\S+.openshiftapps.com') echo "OAuth callback URL: https://oauth.${domain}/oauth2callback/AAD"$ domain=$(rosa describe cluster -c <cluster_name> | grep "DNS" | grep -oE '\S+.openshiftapps.com') echo "OAuth callback URL: https://oauth.${domain}/oauth2callback/AAD"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The "AAD" directory at the end of the OAuth callback URL must match the OAuth identity provider name that you will set up later in this process.
Create the Entra ID application by logging in to the Azure portal, and select the App registrations blade. Then, select New registration to create a new application.
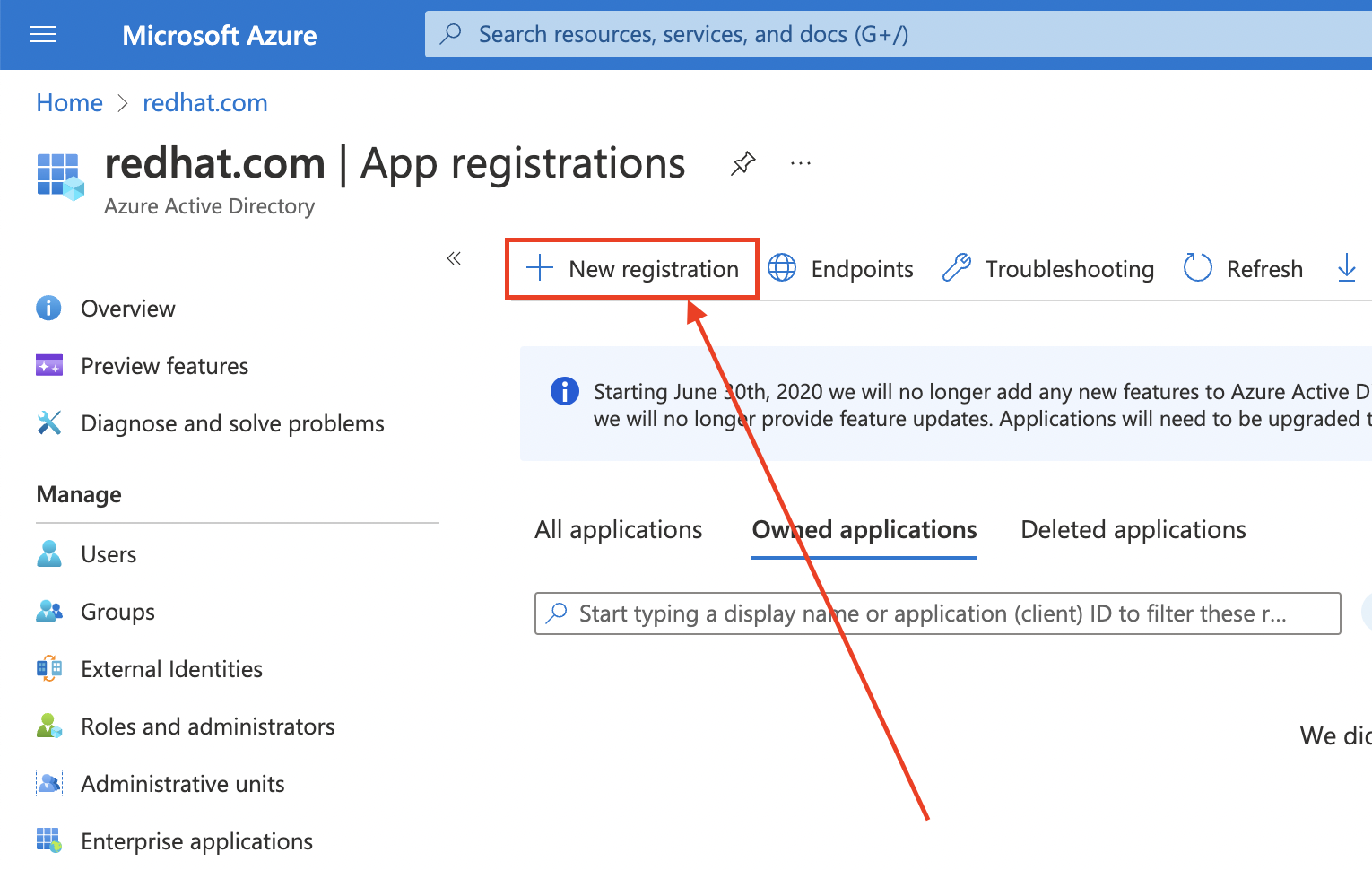
-
Name the application, for example
openshift-auth. - Select Web from the Redirect URI dropdown and enter the value of the OAuth callback URL you retrieved in the previous step.
After providing the required information, click Register to create the application.
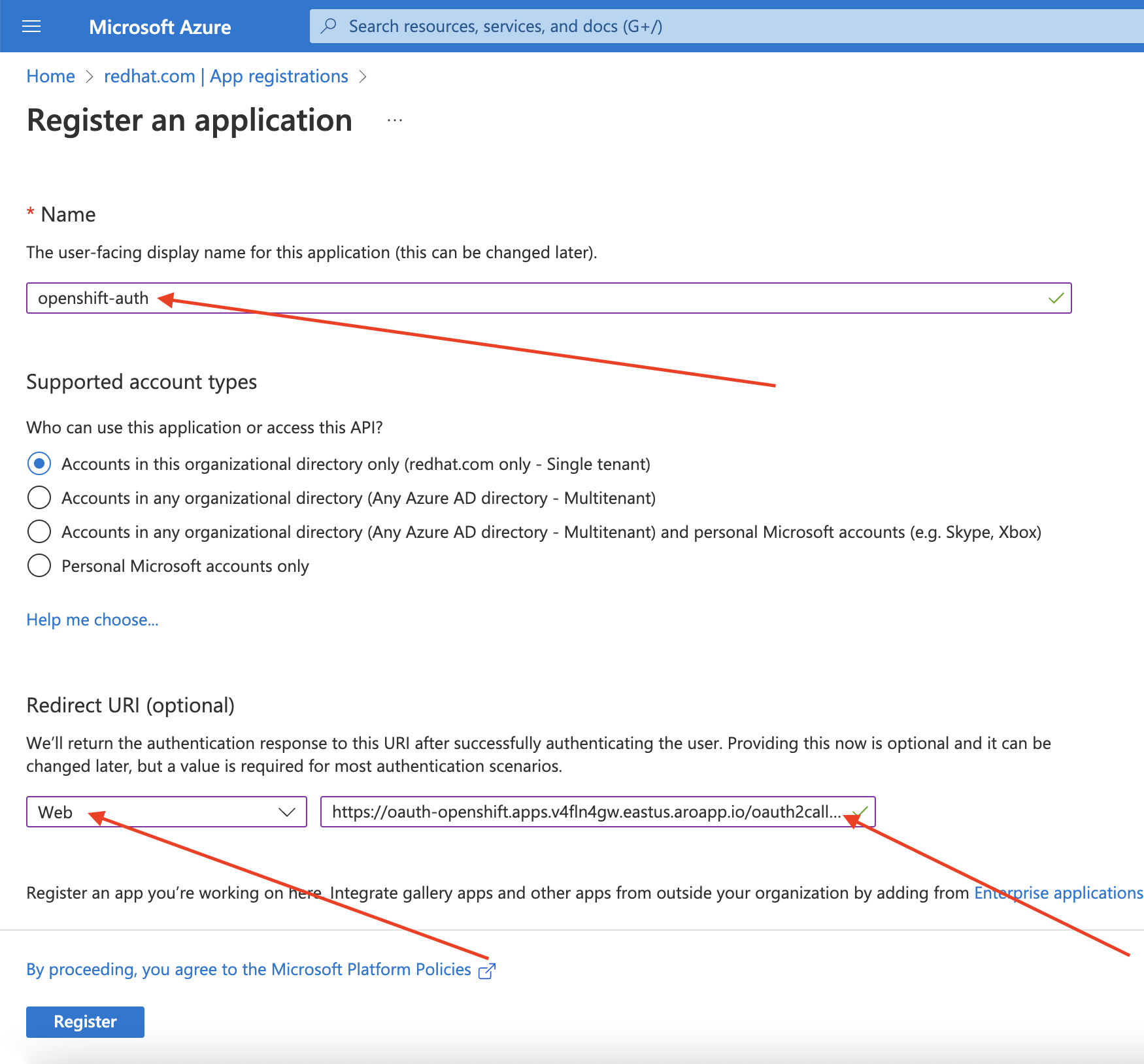
Select the Certificates & secrets sub-blade and select New client secret.
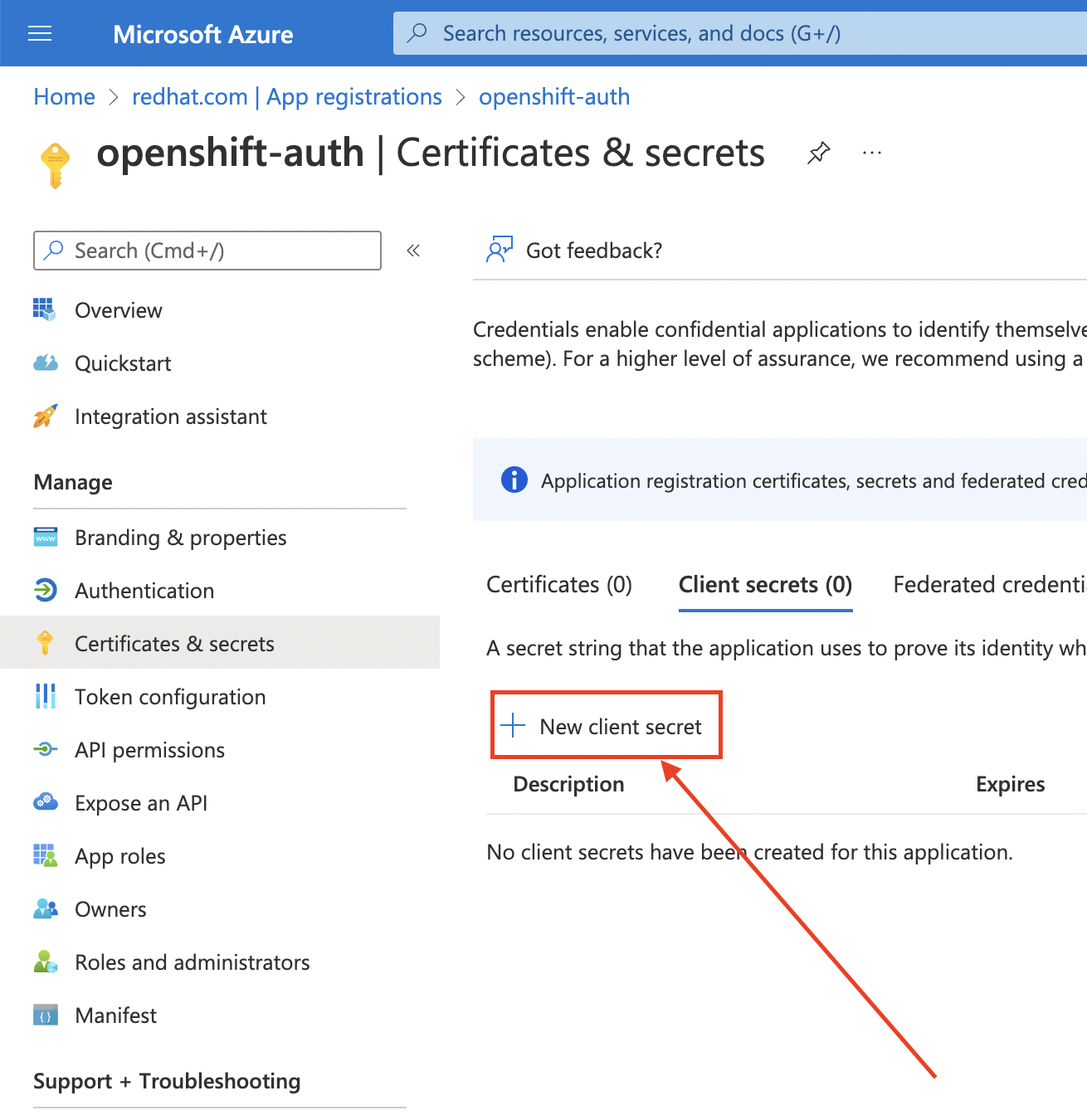
Complete the requested details and store the generated client secret value. This secret is required later in this process.
ImportantAfter initial setup, you cannot see the client secret. If you did not record the client secret, you must generate a new one.
Select the Overview sub-blade and note the
Application (client) IDandDirectory (tenant) ID. You will need these values in a future step.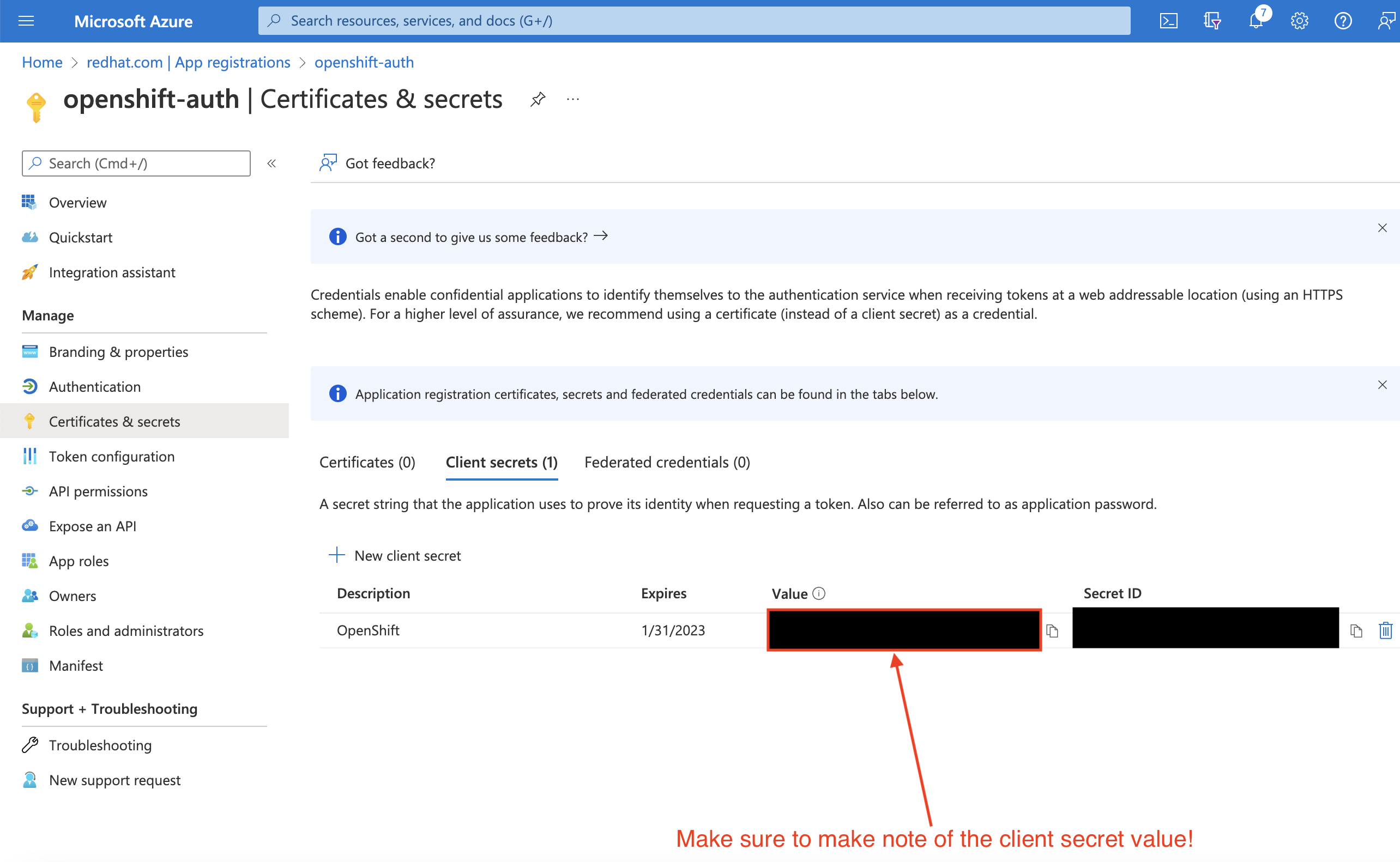
9.3. Configuring the application registration in Entra ID to include optional and group claims
To ensure that Red Hat OpenShift Service on AWS has enough information to create the user’s account, you must configure Entra ID to give two optional claims: email and preferred_username. For more information about optional claims in Entra ID, see the Microsoft documentation.
In addition to individual user authentication, Red Hat OpenShift Service on AWS provides group claim functionality. This functionality allows an OpenID Connect (OIDC) identity provider, such as Entra ID, to offer a user’s group membership for use within Red Hat OpenShift Service on AWS.
9.3.1. Configuring optional claims
You can configure the optional claims in Entra ID.
Procedure
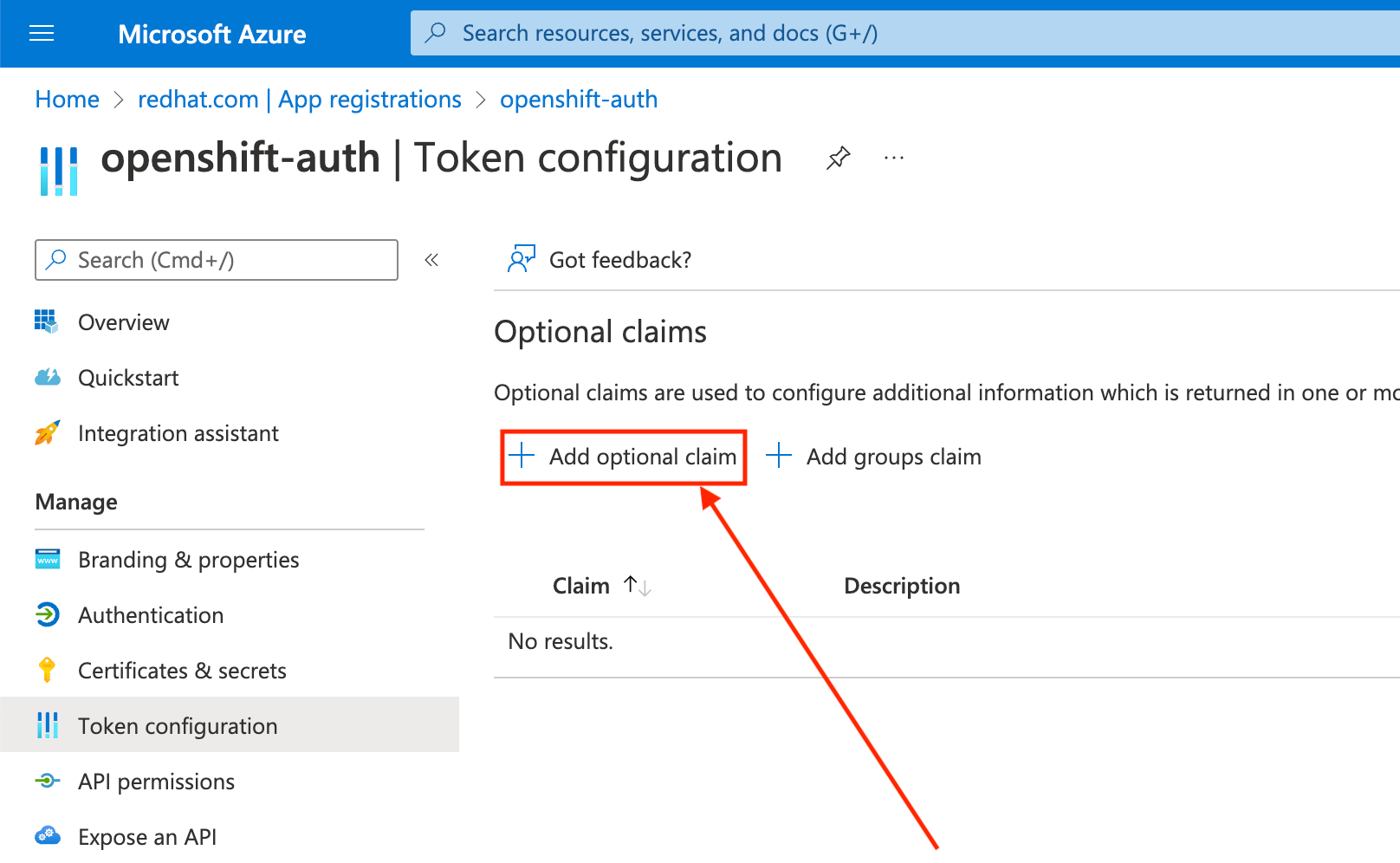
Click the Token configuration sub-blade and select the Add optional claim button.
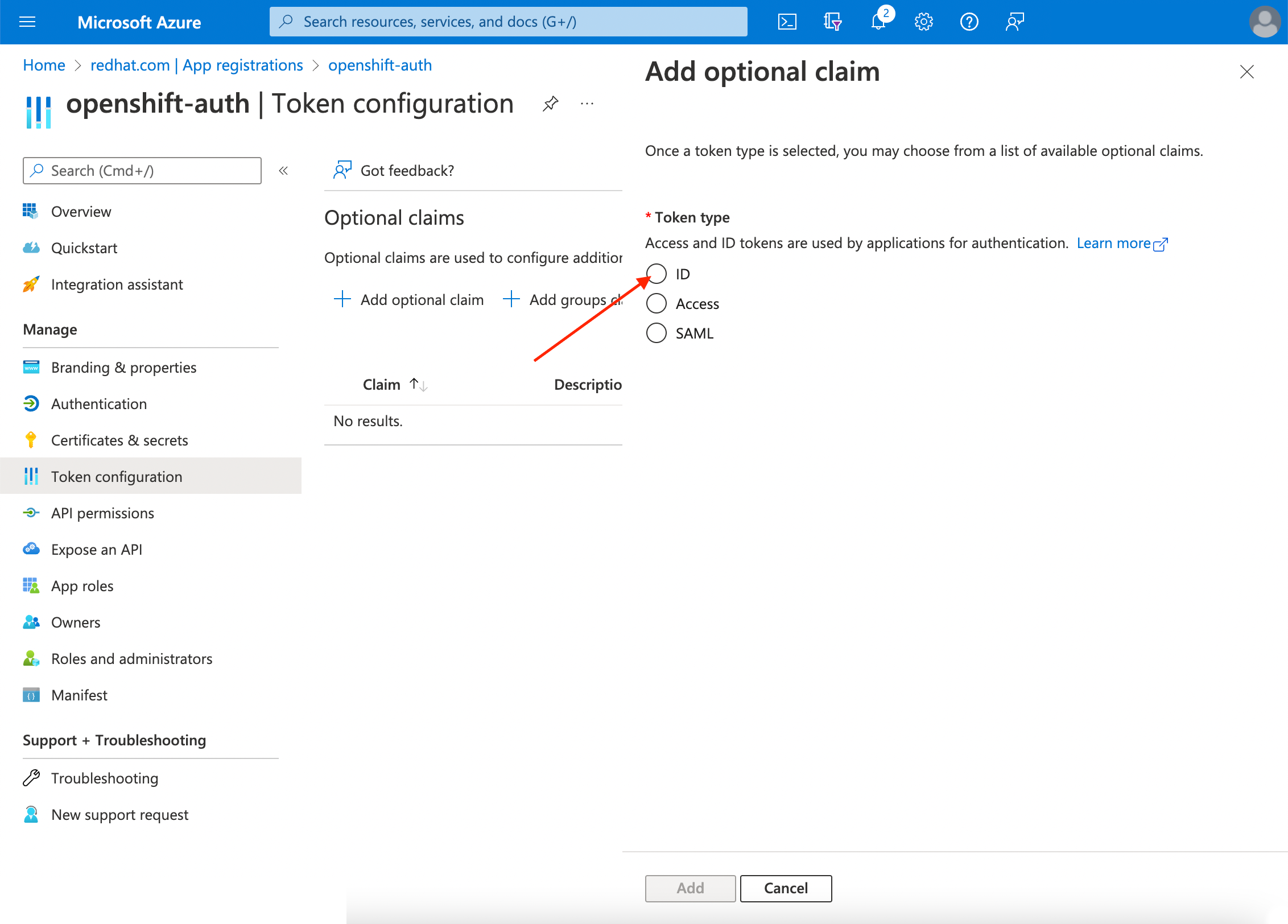
Select the ID radio button.
Select the email claim checkbox.
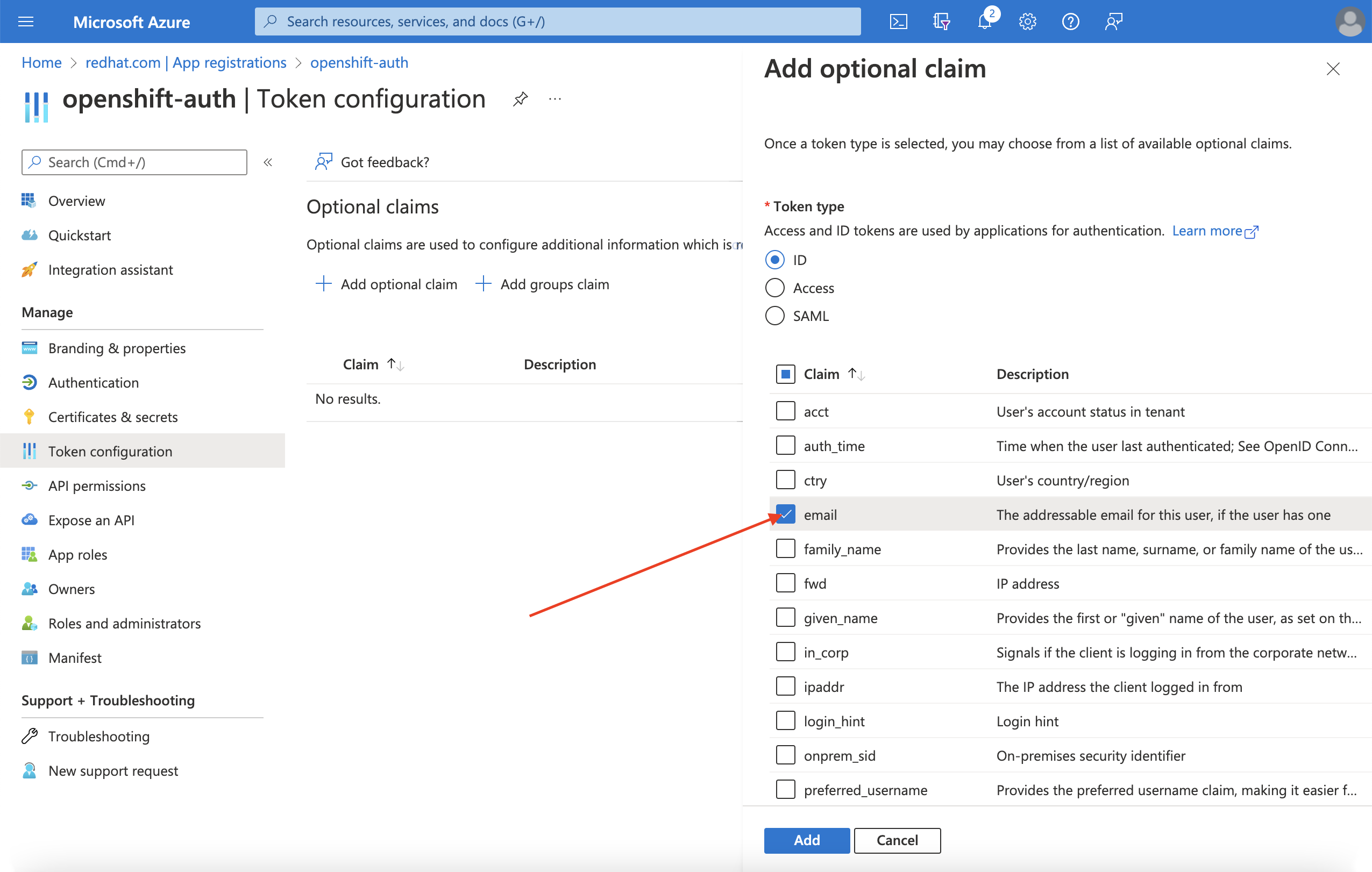
Select the
preferred_usernameclaim checkbox. Then, click Add to configure the email and preferred_username claims your Entra ID application.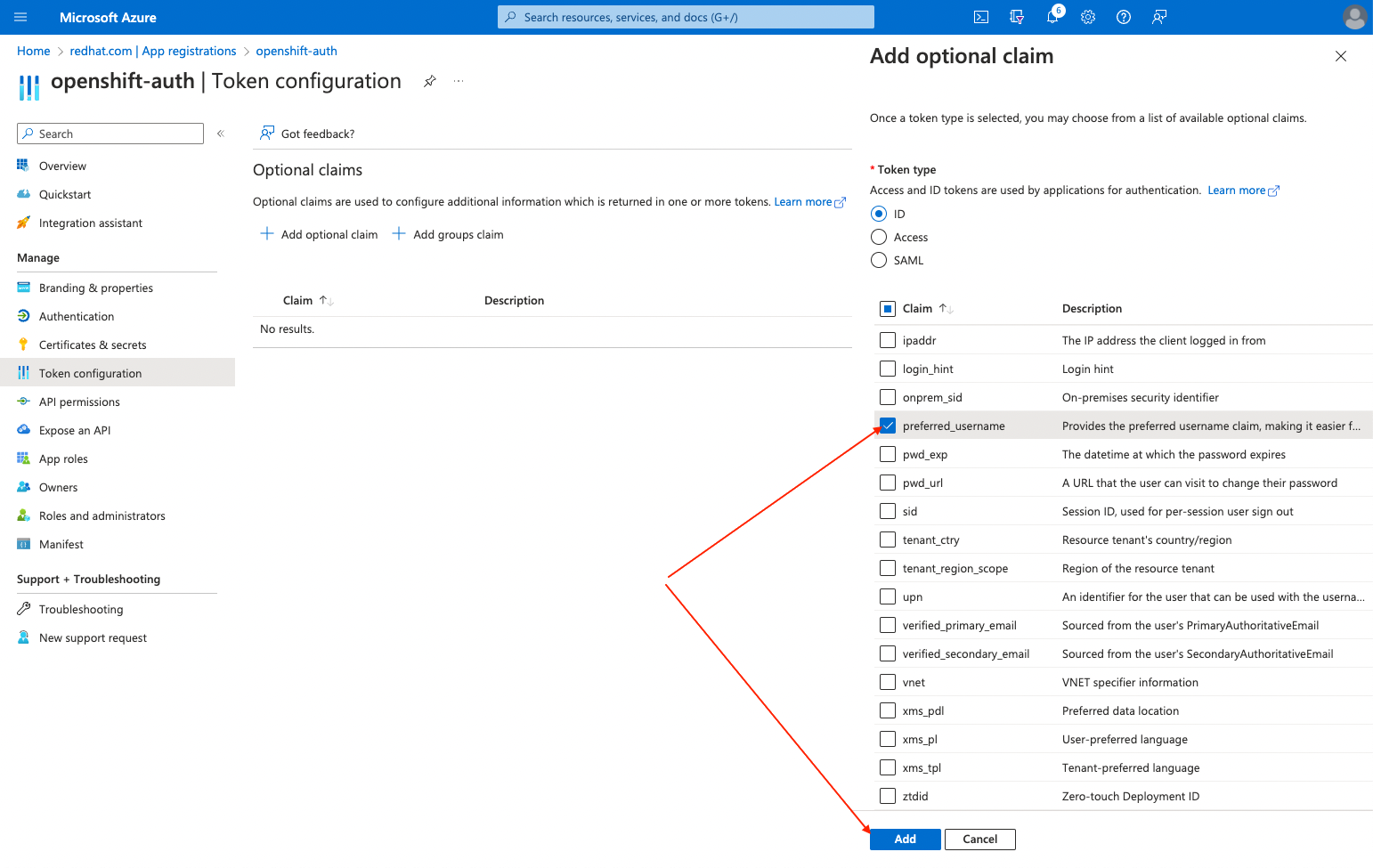
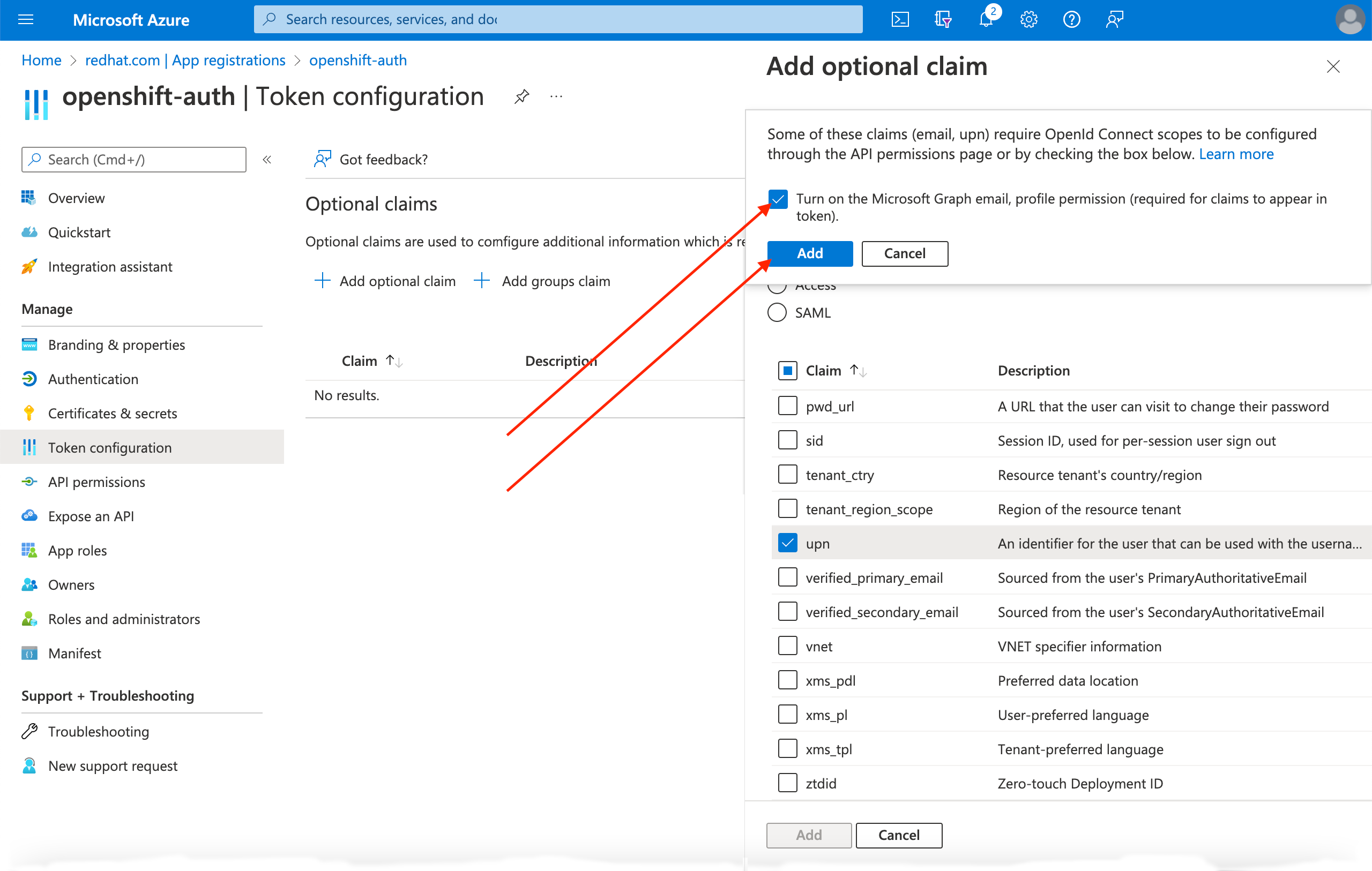
A dialog box appears at the top of the page. Follow the prompt to enable the necessary Microsoft Graph permissions.
9.3.2. Configuring group claims (optional)
Configure Entra ID to offer a groups claim.
Procedure
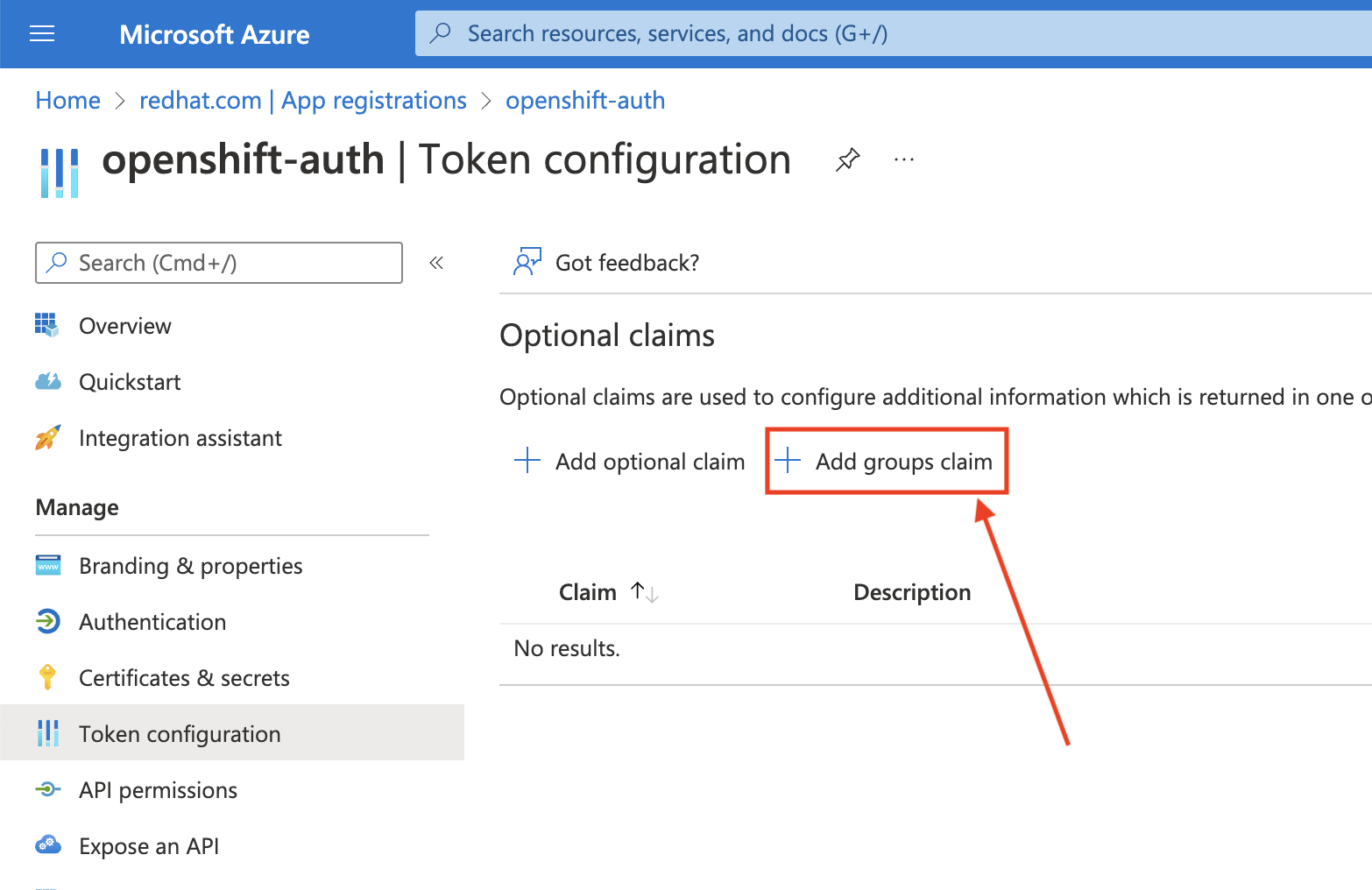
From the Token configuration sub-blade, click Add groups claim.
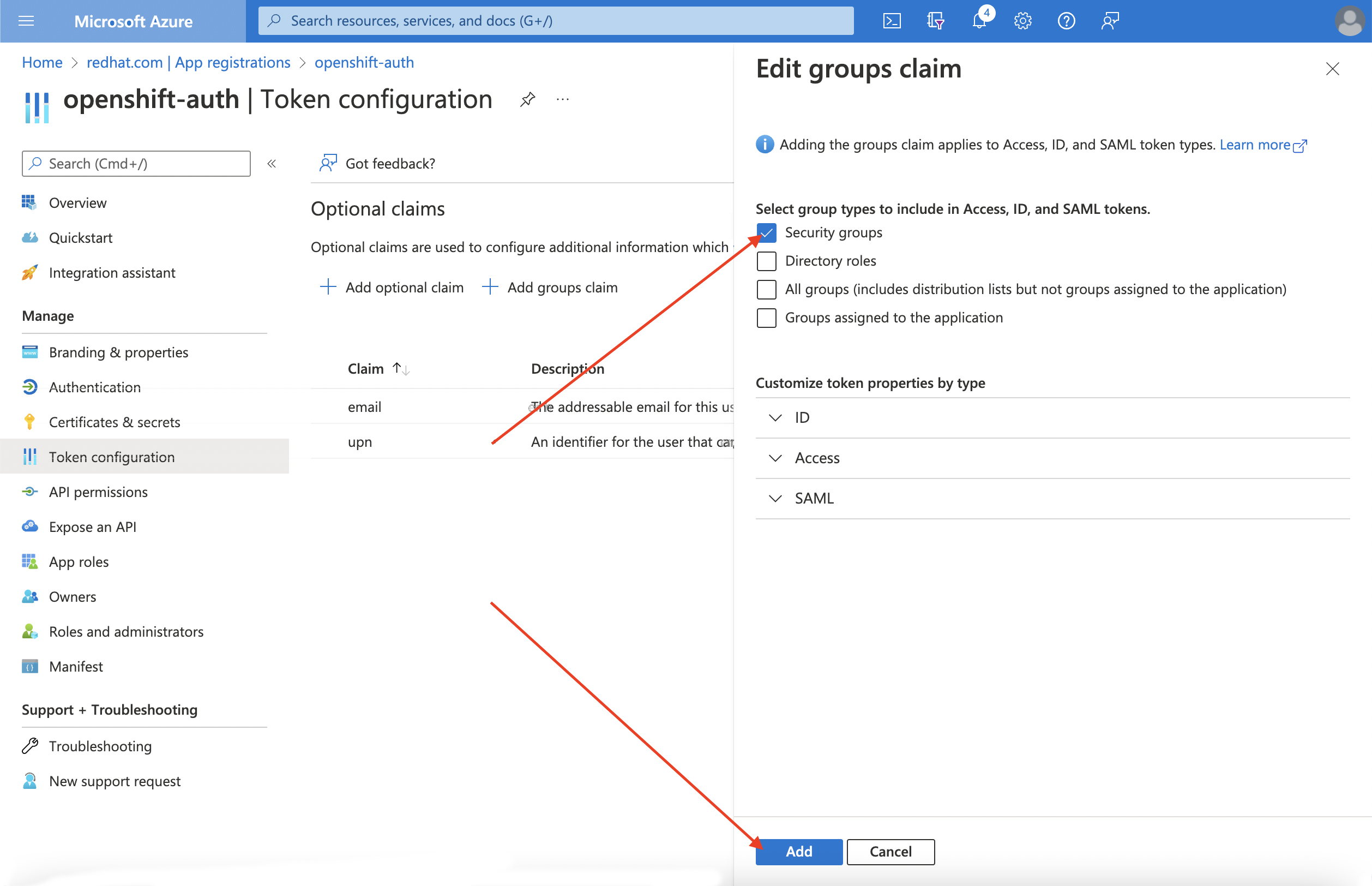
To configure group claims for your Entra ID application, select Security groups and then click the Add.
NoteIn this example, the group claim includes all of the security groups that a user is a member of. In a real production environment, ensure that the groups that the group claim only includes groups that apply to Red Hat OpenShift Service on AWS.
9.4. Configuring the Red Hat OpenShift Service on AWS cluster to use Entra ID as the identity provider
You must configure Red Hat OpenShift Service on AWS to use Entra ID as its identity provider. Although Red Hat OpenShift Service on AWS offers the ability to configure identity providers by using OpenShift Cluster Manager, use the ROSA CLI to configure the cluster’s OAuth provider to use Entra ID as its identity provider. Before configuring the identity provider, set the necessary variables for the identity provider configuration.
Procedure
Create the variables by running the following command:
CLUSTER_NAME=example-cluster IDP_NAME=AAD APP_ID=yyyyyyyy-yyyy-yyyy-yyyy-yyyyyyyyyyyy CLIENT_SECRET=xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx TENANT_ID=zzzzzzzz-zzzz-zzzz-zzzz-zzzzzzzzzzzz
$ CLUSTER_NAME=example-cluster $ IDP_NAME=AAD $ APP_ID=yyyyyyyy-yyyy-yyyy-yyyy-yyyyyyyyyyyy $ CLIENT_SECRET=xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx $ TENANT_ID=zzzzzzzz-zzzz-zzzz-zzzz-zzzzzzzzzzzzCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
example-cluster- Replace this with the name of your cluster.
AAD- Replace this value with the name you used in the OAuth callback URL that you generated earlier in this process.
yyyyyyyy-yyyy-yyyy-yyyy-yyyyyyyyyyyy- Replace this with the Application (client) ID.
xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx- Replace this with the Client Secret.
zzzzzzzz-zzzz-zzzz-zzzz-zzzzzzzzzzzz- Replace this with the Directory (tenant) ID.
Configure the cluster’s OAuth provider by running the following command. If you enabled group claims, ensure that you use the
--group-claims groupsargument.If you enabled group claims, run the following command:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you did not enable group claims, run the following command:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow After a few minutes, the cluster authentication Operator reconciles your changes, and you can log in to the cluster by using Entra ID.
9.5. Granting additional permissions to individual users and groups
When your first log in, you might notice that you have very limited permissions. By default, Red Hat OpenShift Service on AWS only grants you the ability to create new projects, or namespaces, in the cluster. Other projects are restricted from view.
You must grant these additional abilities to individual users and groups.
9.6. Granting additional permissions to individual users
Red Hat OpenShift Service on AWS includes a significant number of preconfigured roles, including the cluster-admin role that grants full access and control over the cluster.
Procedure
Grant a user access to the
cluster-adminrole by running the following command:rosa grant user cluster-admin --user=<USERNAME> --cluster=${CLUSTER_NAME}$ rosa grant user cluster-admin --user=<USERNAME> --cluster=${CLUSTER_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<USERNAME>- Provide the Entra ID username that you want to have cluster admin permissions.
9.7. Granting additional permissions to individual groups
If you opted to enable group claims, the cluster OAuth provider automatically creates or updates the user’s group memberships by using the group ID. The cluster OAuth provider does not automatically create RoleBindings and ClusterRoleBindings for the groups that are created; you are responsible for creating those bindings by using your own processes.
To grant an automatically generated group access to the cluster-admin role, you must create a ClusterRoleBinding to the group ID.
Procedure
Create the
ClusterRoleBindingby running the following command:oc create clusterrolebinding cluster-admin-group --clusterrole=cluster-admin --group=<GROUP_ID>
$ oc create clusterrolebinding cluster-admin-group --clusterrole=cluster-admin --group=<GROUP_ID>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<GROUP-ID>- Provide the Entra ID group ID that you want to have cluster admin permissions.
Now, any user in the specified group automatically receives
cluster-adminaccess.