Chapter 8. Organizing and Grouping Entries
8.1. Using Groups
nsRoleDN attribute in the user object. If you use groups, then the DN of the users who are members of this group are stored in member attributes in the group object. If you enabled the memberOf plug-in, then the groups the user is a member of, are additionally stored in memberOf attribute in the user object. With this plug-in enabled, groups additionally have the benefit of roles, that you can list the group memberships of a user, similar as when using roles. Additionally, groups are faster than roles.
8.1.1. The Different Types of Groups
groupOfNames(recommended) is a simple group, that allows any entry to be added. The attribute used to determine members for this ismember.groupOfUniqueNames, likegroupOfNames, simply lists user DNs as members, but the members must be unique. This prevents users being added more than once as a group member, which is one way of preventing self-referential group memberships. The attribute used to determine members for this isuniqueMember.groupOfURLsuses a list of LDAP URLs to filter and generate its membership list. This object class is required for any dynamic group and can be used in conjunction withgroupOfNamesandgroupOfUniqueNames.groupOfCertificatesis similar togroupOfURLsin that it uses an LDAP filter to search for and identify certificates (or, really, certificate names) to identify group members. This is useful for group-based access control, since the group can be given special access permissions. The attribute used to determine members for this ismemberCertificate.
| Type of Group | Group Object Classes | Member Attributes |
|---|---|---|
| Static | groupOfNames [a] | member |
groupOfUniqueNames [a] | uniqueMember | |
| Dynamic | groupOfURLs | memberURL |
groupOfCertificates | memberCertificate | |
[a]
If this object class is used together with one of the dynamic object classes, the group becomes dynamic.
| ||
Example 8.1. A Static Group Entry
Example 8.2. A Dynamic Group Entry
groupOfUniqueNames, can explicitly list some group members along with the dynamic LDAP URL. For example:
Note
memberURL attribute instead of listing the group members in an attribute, the memberOf plug-in does not add the memberOf attribute to the user objects that match the filter.
8.1.2. Creating a Static Group
8.1.2.1. Creating a Static Group Using the Command Line
Creating a Static Group with the groupOfNames Object Class
dsidm utility creates static groups in the cn=Groups entry in the specified base DN.
example_group group with the groupOfNames object class in the cn=Groups,dc=example,dc=com entry
dsidm -D "cn=Directory Manager" ldap://server.example.com -b "dc=example,dc=com" group create --cn "example_group"
# dsidm -D "cn=Directory Manager" ldap://server.example.com -b "dc=example,dc=com" group create --cn "example_group"Creating a Static Group with the groupOfUniqueNames Object Class
groupOfUniqueNames object class, use the ldapmodify utility to add the entry.
example_group group with the groupOfUniqueNames object class in the cn=Groups,dc=example,dc=com entry:
8.1.3. Creating a Dynamic Group
8.1.3.1. Creating a Dynamic Group Using the Command Line
Creating a Dynamic Group with the groupOfURLs Object Class
example_group group with the groupOfURLs object class in the cn=Groups,dc=example,dc=com entry:
Creating a Dynamic Group with the groupOfCertificates Object Class
example_group group with the groupOfCertificates object class in the cn=Groups,dc=example,dc=com entry:
8.1.4. Listing Group Membership in User Entries
memberOf attribute in the member's entry. (By default, this checks the member attribute, but multiple attribute instances can be used to support multiple different group types.)
memberOf attributes on the user entries. The MemberOf Plug-in provides a way to view the groups to which a user belongs simply by looking at the entry, including nested group membership. It can be very difficult to backtrack memberships through nested groups, but the MemberOf Plug-in shows memberships for all groups, direct and indirect.
8.1.4.1. Considerations When Using the memberOf Plug-in
memberOf plug-in.
- Using the
memberOfPlug-in in a Replication Topology - There are two approaches to manage the
memberOfattribute in a replication topology:- Enable the
memberOfplug-in on all supplier and read-only replica servers in the topology. In this case, you must exclude thememberOfattribute from replication in all replication agreements. For details about about excluding attributes, see Section 15.1.7, “Replicating a Subset of Attributes with Fractional Replication”. - Enable the
memberOfplug-in only on all supplier servers in the topology. For this:- You must disable replication of the
memberOfattribute to all write-enabled suppliers in the replication agreement. For details about about excluding attributes, see Section 15.1.7, “Replicating a Subset of Attributes with Fractional Replication”. - You must Enable replication of the
memberOfattribute to all read-only replicas in their replication agreement. - You must not enable the
memberOfplug-in on read-only replicas.
- Using the
memberOfplug-in With Distributed Databases - As described in Section 2.2.1, “Creating Databases”, you can store sub-trees of your directory in individual databases. By default, the
memberOfplug-in only updates user entries which are stored within the same database as the group. To enable the plug-in to also update users in different databases as the group, you must set thememberOfAllBackendsparameter toon. See Section 8.1.4.5.2, “Configuring the MemberOf Plug-in on Each Server Using the Web Console”.
8.1.4.2. Required Object Classes by the memberOf Plug-In
memberOf plug-in By default, the memberOf plug-in will add the MemberOf object class to objects to provide the memberOf attribute. This object class is safe to add to any object for this purpose, and no further action is required to enable this plug-in to operate correctly. Alternatively, you can create user objects that contain the inetUser or inetAdmin, object class. Both object classes support the memberOf attribute as well.
extensibleObject object class.
Note
LDAP: error code 65 - Object Class Violation
LDAP: error code 65 - Object Class Violation8.1.4.3. The MemberOf Plug-in Syntax
memberOfGroupAttr) and the other for the attribute to create and manage in the member's user entry (memberOfAttr).
memberOfGroupAttr attribute is multi-valued. Because different types of groups use different member attributes, using multiple memberOfGroupAttr attributes allows the plug-in to manage multiple types of groups.
Example 8.3. Default MemberOf Plug-in Entry
Note
member), it may be necessary to include the member group attribute or whatever previous member attribute was used, in addition any new member attributes used in the plug-in configuration.
memberOfGroupAttr: member memberOfGroupAttr: uniqueMember
memberOfGroupAttr: member
memberOfGroupAttr: uniqueMember
8.1.4.4. Enabling the MemberOf Plug-in
8.1.4.4.1. Enabling the MemberOf Plug-in Using the Command Line
- Use the
dsconfutility to enable the plug-in:dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof enable
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof enableCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the instance:
dsctl instance_name restart
# dsctl instance_name restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.1.4.4.2. Enabling the MemberOf Plug-in Using the Web Console
- Open the Directory Server user interface in the web console. See Section 1.4, “Logging Into Directory Server Using the Web Console”.
- Select the instance.
- Select the menu.
- Select the MemberOf plug-in.
- Change the status to
ONto enable the plug-in. - Restart the instance. See Section 1.5.2, “Starting and Stopping a Directory Server Instance Using the Web Console”.
8.1.4.5. Configuring the MemberOf Plug-in on Each Server
8.1.4.5.1. Configuring the MemberOf Plug-in on Each Server Using the Command Line
- Enable the plug-in. See Section 8.1.4.4.1, “Enabling the MemberOf Plug-in Using the Command Line”.
- To retrieve members of a group from a different attribute than
member, which is the default, set thememberOfGroupAttrparameter to the respective attribute name.For example, to read group members fromuniqueMemberattributes, replace the current value ofmemberOfGroupAttr:- Optionally, display the attribute that is currently configured:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof show ... memberofgroupattr: member ...
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof show ... memberofgroupattr: member ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command displays that currently only thememberattribute is configured to retrieve members of a group. - Remove all attributes from the configuration that currently set:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --groupattr delete Successfully changed the cn=MemberOf Plugin,cn=plugins,cn=config
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --groupattr delete Successfully changed the cn=MemberOf Plugin,cn=plugins,cn=configCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
It is not possible to remove a specific group attribute. - Add the
uniqueMemberattribute to the configuration:dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --groupattr uniqueMember successfully added memberOfGroupAttr value "uniqueMember"
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --groupattr uniqueMember successfully added memberOfGroupAttr value "uniqueMember"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set multiple attributes, pass them all to the--groupattrparameter. For example:dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --groupattr member uniqueMember ...
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --groupattr member uniqueMember ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- By default, the MemberOf plug-in adds the
memberOfattribute to user entries. To use a different attribute, set the name of the attribute in thememberOfAttrparameter.For example, to add thecustomMemberOfattribute to user records, replace the current value ofmemberOfAttr:- Optionally, display the attribute that is currently configured:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof show ... memberofattr: memberOf ...
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof show ... memberofattr: memberOf ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the MemberOf plug-in to add the
customMemberOfattribute to user entries:dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --attr customMemberOf memberOfAttr set to "customMemberOf"
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --attr customMemberOf memberOfAttr set to "customMemberOf"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
You can only set this parameter to an attribute that supports DN syntax.
- In an environment that uses distributed databases, you can configure the plug-in to search user entries in all databases instead of only the local database:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --allbackends on memberOfAllBackends enabled successfully
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --allbackends on memberOfAllBackends enabled successfullyCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the instance:
dsctl instance_name restart
# dsctl instance_name restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.1.4.5.2. Configuring the MemberOf Plug-in on Each Server Using the Web Console
- Open the Directory Server user interface in the web console. See Section 1.4, “Logging Into Directory Server Using the Web Console”.
- Select the instance.
- Open the menu.
- Select the memberOf plug-in.
- Change the status to
ONto enable the plug-in. - Fill the fields to configure the plug-in. For example, to configure that the plug-in adds the
customMemberOfattribute to user entries if theuniqueMemberattribute is added to a group:
- Click .
- Restart the instance. See Section 1.5.2, “Starting and Stopping a Directory Server Instance Using the Web Console”.
8.1.4.7. Setting the Scope of the MemberOf Plug-in
memberOfEntryScope and memberOfEntryScopeExcludeSubtree parameters to set what suffixes the MemberOf plug-in works on.
MemberOf plug-in only adds the memberOf attribute to the group if both the user and the group are in the plug-in's scope. For example, to configure the MemberOf plug-in to work on all entries in dc=example,dc=com, but to exclude entries in ou=private,dc=example,dc=com:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --scope "dc=example,com" dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --exclude "dc=group,dc=example,com"
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --scope "dc=example,com"
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof set --exclude "dc=group,dc=example,com"--scope DN parameter:
- The membership attribute, such as
member, is updated in the group entry to remove the user DN value. - The
memberOfattribute is updated in the user entry to remove the group DN value.
Note
--exclude parameter has a higher priority than values set in --scope. If the scopes set in both parameters overlap, the MemberOf plug-in only works on the non-overlapping directory entries.
8.1.4.8. Regenerating memberOf Values
memberOf attributes on group member entries, based on the configuration in the group entry itself. However, the memberOf attribute can be manually edited in a user entry or new entries can be imported or replicated to the server that have a memberOf attribute already set. These situations create inconsistencies between the memberOf configuration managed by the server plug-in and the actual memberships defined in an entry.
memberOf values in dc=example,dc=com entry and subentries:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof fixup -f "(|(objectclass=inetuser)(objectclass=inetadmin)(objectclass=nsmemberof))" "dc=example,dc=com" Attempting to add task entry... Successfully added task entry
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin memberof fixup -f "(|(objectclass=inetuser)(objectclass=inetadmin)(objectclass=nsmemberof))" "dc=example,dc=com"
Attempting to add task entry...
Successfully added task entry-f filter option is optional. Use the filter to regenerate the memberOf attributes in user entries matching the filter. If you do not specify a filter, the tasks regenerates the attributes in all entries containing the inetUser, inetAdmin, or nsMemberOf object class.
Note
memberOf attributes for entries on other servers are not updated until the updated entry is replicated.
8.1.5. Automatically Adding Entries to Specified Groups
Note
autoMemberProcessModifyOps parameter in the cn=Auto Membership Plugin,cn=plugins,cn=config entry is set to on. With this setting, the Automembership plug-in also updates group memberships when an administrator moves a user to a different group by editing a user entry.
autoMemberProcessModifyOps to off, Directory Server invokes the plug-in only when you add a group entry to the user, and you must manually run a fix-up task to update the group membership.
Note
8.1.5.1. Looking at the Structure of an Automembership Rule
cn=plugins,cn=config. Group assignments are defined through child entries.
8.1.5.1.1. The Automembership Configuration Entry
- An LDAP search to identify entries, including both a search scope and a search filter (
autoMemberScopeandautoMemberFilter) - A default group to which to add the member entries (
autoMemberDefaultGroup) - The member entry format, which is the attribute in the group entry, such as
member, and the attribute value, such asdn(autoMemberGroupingAttr)
ntUser to the cn=windows-users group:
cn=Auto Membership Plugin,cn=plugins,cn=config entry description in the Red Hat Directory Server Configuration, Command, and File Reference.
8.1.5.1.2. Additional Regular Expression Entries
Example 8.4. Automember Definition for a Host Group
Example 8.5. Regular Expression Condition for a Web Server Group
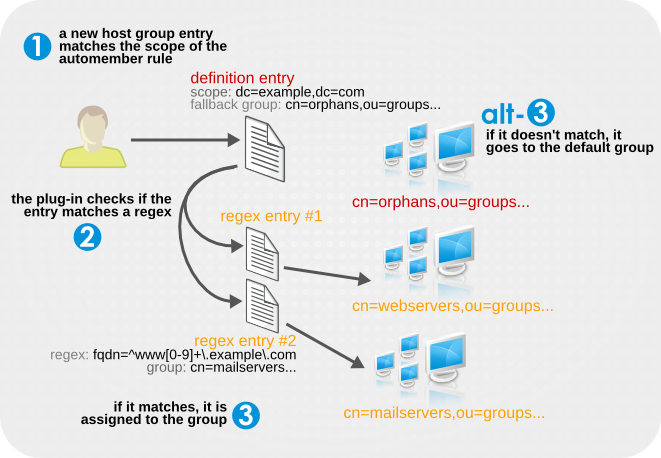
^www\.web[0-9]+\.example\.com, such as www.web1.example.com, is added to the cn=webservers group, defined for that exact regular expression. Any other machine entry, which matches the LDAP filter objectclass=ipHost but with a different type of fully-qualified domain name, is added to the general host group, cn=systems, defined in the main definition entry.
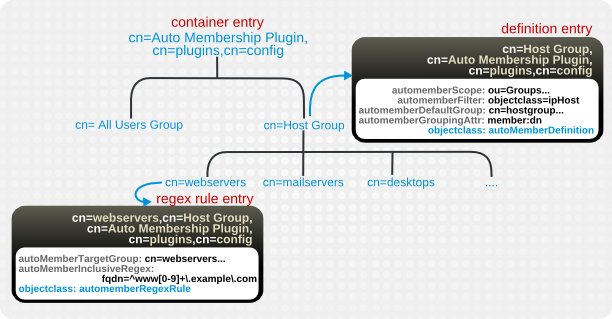
Figure 8.1. Regular Expression Conditions
| Attribute | Description |
|---|---|
| autoMemberRegexRule (required object class) | Identifies the entry as a regular expression rule. This entry must be a child of an automember definition (objectclass: autoMemberDefinition). |
| autoMemberInclusiveRegex | Sets a regular expression to use to identify entries to include. Only matching entries are added to the group. Multiple regular expressions could be used, and if an entry matches any one of those expressions, it is included in the group.
The format of the expression is a Perl-compatible regular expression (PCRE). For more information on PCRE patterns, see the
pcresyntax(3) man page.
This is a multi-valued attribute.
|
| autoMemberExclusiveRegex | Sets a regular expression to use to identify entries to exclude. If an entry matches the exclusion condition, then it is not included in the group. Multiple regular expressions could be used, and if an entry matches any one of those expressions, it is excluded in the group.
The format of the expression is a Perl-compatible regular expression (PCRE). For more information on PCRE patterns, see the
pcresyntax(3) man page.
This is a multi-valued attribute.
Note
Exclude conditions are evaluated first and take precedence over include conditions.
|
| autoMemberTargetGroup | Sets which group to add the entry to as a member, if it meets the regular expression conditions. |
8.1.5.2. Configuring Auto Membership Definitions
8.1.5.2.1. Configuring Auto Membership Definitions Using the Command Line
- Enable the Auto Membership plug-in:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin automember enable Enabled Auto Membership Plugin
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin automember enable Enabled Auto Membership PluginCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create a Auto Membership definition. For example:
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin automember definition definition_name add --default-group "cn=windows-group,cn=groups,dc=example,dc=com" --scope "ou=People,dc=example,dc=com" --filter "objectclass=ntUser" --grouping-attr "member:dn" Automember definition created successfully!
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin automember definition definition_name add --default-group "cn=windows-group,cn=groups,dc=example,dc=com" --scope "ou=People,dc=example,dc=com" --filter "objectclass=ntUser" --grouping-attr "member:dn" Automember definition created successfully!Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, you can set further parameters in an Auto Membership definition, for example, to use regular expressions to identify entries to include.Use the
ldapmodifyutility to add or update these parameters in thecn=definition_name,cn=Auto Membership Plugin,cn=plugins,cn=configentry. For parameters you can set, seecn=Auto Membership Plugin,cn=plugins,cn=configentry description in the Red Hat Directory Server Configuration, Command, and File Reference. - Restart the instance:
dsctl instance_name restart
# dsctl instance_name restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.1.5.2.2. Configuring Auto Membership Definitions Using the Web Console
- Open the Directory Server user interface in the web console. See Section 1.4, “Logging Into Directory Server Using the Web Console”.
- Select the instance.
- Open the menu.
- Select the Auto Membership plug-in.
- Change the status to
ONto enable the plug-in. - Click .
- Fill the fields. For example:

- Optionally, add a regular expression filter.
- Click .
- Restart the instance. See Section 1.5.2, “Starting and Stopping a Directory Server Instance Using the Web Console”.
8.1.5.3. Updating Existing Entries to apply Auto Membership Definitions
autoMemberProcessModifyOps parameter in the cn=Auto Membership Plugin,cn=plugins,cn=config entry is enabled. With this setting, the Automembership plug-in also updates group memberships when an administrator moves a user to a different group by editing a user entry. However, if you set autoMemberProcessModifyOps to off, you must manually run a fix-up task when you added new entries to the directory or changed existing entries.
dsconf -D "cn=Directory Manager" ldap://server.example.com plugin automember fixup -f "filter" -s scope
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin automember fixup -f "filter" -s scope8.1.5.4. Examples of Automembership Rules
- Different host groups based on IP address
- Windows user groups
- Different user groups based on employee ID
Example 8.6. Host Groups by IP Address
Example 8.7. Windows User Group
posixAccount attribute to identify all new users. All new users created within Directory Server are created with the posixAccount attribute, so that is a safe catch-all for new Directory Server users. However, when user accounts are synchronized over from the Windows domain to the Directory Server, the Windows user accounts are created without the posixAccount attribute.
ntUser attribute. The basic, all-users group rule can be modified to target Windows users specifically, which can then be added to the default all-users group or to a Windows-specific group.
Example 8.8. User Groups by Employee Type
employeeType attribute.
8.1.5.5. Testing Automembership Definitions
cn=automember export updates runs against existing entries in the directory and exports the results of what users would have been added to what groups, based on the rules. This is useful for testing existing rules against existing users to see how your real deployment are performing.
cn=automember rebuild membership task — the base DN to search, search filter, and search scope — and has an additional parameter to specify an export LDIF file to record the proposed entry updates.
cn=automember map updates takes an import LDIF of new users and then runs the new users against the current automembership rules. This can be very useful for testing a new rule, before applying it to (real) new or existing user entries.
ldapmodify:
8.1.5.6. Canceling the Auto Membership Plug-in Task
Procedure
- To cancel the Auto Membership plug-in task enter:
dsconf server.example.com plugin automember abort-fixup
# dsconf server.example.com plugin automember abort-fixupCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
- To see the list of all Auto Membership plug-in tasks, including canceled tasks, enter:
dsconf server.example.com plugin automember fixup-status
# dsconf server.example.com plugin automember fixup-statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow