18.3. The USB Filter Editor
18.3.1. Installing the USB Filter Editor
The USB Filter Editor is a Windows tool used to configure the usbfilter.txt policy file. The policy rules defined in this file allow or deny automatic pass-through of specific USB devices from client machines to virtual machines managed using the Red Hat Virtualization Manager. The policy file resides on the Red Hat Virtualization Manager in the following location: /etc/ovirt-engine/usbfilter.txt Changes to USB filter policies do not take effect unless the ovirt-engine service on the Red Hat Virtualization Manager server is restarted.
Download the USB Filter Editor installer from "Installers and Images for Red Hat Virtualization Manager".
Installing the USB Filter Editor
- On a Windows machine, run the .msi file you downloaded for the USB Filter Editor.
- Follow the steps of the installation wizard. Unless otherwise specified, the USB Filter Editor will be installed by default in either C:\Program Files\RedHat\USB Filter Editor or C:\Program Files(x86)\RedHat\USB Filter Editor depending on your version of Windows.
- A USB Filter Editor shortcut icon is created on your desktop.
Use a Secure Copy (SCP) client to import and export filter policies from the Red Hat Virtualization Manager. A Secure Copy tool for Windows machines is WinSCP (http://winscp.net).
The default USB device policy provides virtual machines with basic access to USB devices; update the policy to allow the use of additional USB devices.
18.3.2. The USB Filter Editor Interface
Double-click the USB Filter Editor shortcut icon on your desktop.
The Red Hat USB Filter Editor interface displays the Class, Vendor, Product, Revision, and Action for each USB device. Permitted USB devices are set to Allow in the Action column; prohibited devices are set to Block.
| Name | Description |
|---|---|
| Class | Type of USB device; for example, printers, mass storage controllers. |
| Vendor | The manufacturer of the selected type of device. |
| Product | The specific USB device model. |
| Revision | The revision of the product. |
| Action | Allow or block the specified device. |
The USB device policy rules are processed in their listed order. Use the Up and Down buttons to move rules higher or lower in the list. The universal Block rule needs to remain as the lowest entry to ensure all USB devices are denied unless explicitly allowed in the USB Filter Editor.
18.3.3. Adding a USB Policy
Double-click the USB Filter Editor shortcut icon on your desktop to open the editor.
Adding a USB Policy
- Click Add.
Use the USB Class, Vendor ID, Product ID, and Revision check boxes and lists to specify the device.
Click the Allow button to permit virtual machines use of the USB device; click the Block button to prohibit the USB device from virtual machines.
Click OK to add the selected filter rule to the list and close the window.
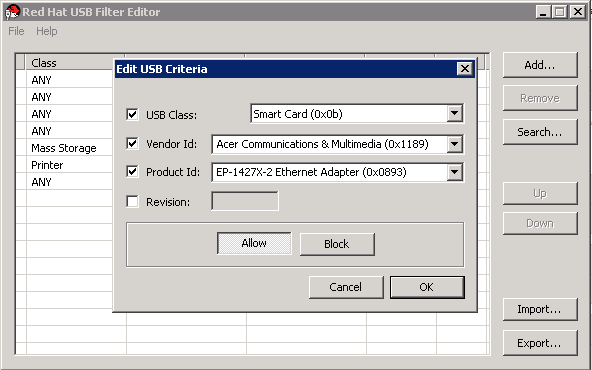
Example 18.1. Adding a Device
The following is an example of how to add USB Class
Smartcard, deviceEP-1427X-2 Ethernet Adapter, from manufacturerAcer Communications & Multimediato the list of allowed devices.-
Click
to save the changes.
You have added a USB policy to the USB Filter Editor. USB filter policies must be exported to the Red Hat Virtualization Manager to take effect.
18.3.4. Removing a USB Policy
Double-click the USB Filter Editor shortcut icon on your desktop to open the editor.
Removing a USB Policy
- Select the policy to be removed.
- Click Remove. A message displays prompting you to confirm that you want to remove the policy.
- Click Yes to confirm that you want to remove the policy.
-
Click
to save the changes.
You have removed a USB policy from the USB Filter Editor. USB filter policies must be exported to the Red Hat Virtualization Manager to take effect.
18.3.5. Searching for USB Device Policies
Search for attached USB devices to either allow or block them in the USB Filter Editor.
Double-click the USB Filter Editor shortcut icon on your desktop to open the editor.
Searching for USB Device Policies
- Click Search. The Attached USB Devices window displays a list of all the attached devices.
- Select the device and click Allow or Block as appropriate. Double-click the selected device to close the window. A policy rule for the device is added to the list.
- Use the Up and Down buttons to change the position of the new policy rule in the list.
-
Click
to save the changes.
You have searched the attached USB devices. USB filter policies need to be exported to the Red Hat Virtualization Manager to take effect.
18.3.6. Exporting a USB Policy
USB device policy changes need to be exported and uploaded to the Red Hat Virtualization Manager for the updated policy to take effect. Upload the policy and restart the ovirt-engine service.
Double-click the USB Filter Editor shortcut icon on your desktop to open the editor.
Exporting a USB Policy
- Click Export; the Save As window opens.
- Save the file with a file name of usbfilter.txt.
- Using a Secure Copy client, such as WinSCP, upload the usbfilter.txt file to the server running Red Hat Virtualization Manager. The file must be placed in the following directory on the server: /etc/ovirt-engine/
As the root user on the server running Red Hat Virtualization Manager, restart the ovirt-engine service.
systemctl restart ovirt-engine.service
# systemctl restart ovirt-engine.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
18.3.7. Importing a USB Policy
An existing USB device policy must be downloaded and imported into the USB Filter Editor before you can edit it.
Importing a USB Policy
- Using a Secure Copy client, such as WinSCP, download the usbfilter.txt file from the server running Red Hat Virtualization Manager. The file can be found in the following directory on the server: /etc/ovirt-engine/
- Double-click the USB Filter Editor shortcut icon on your desktop to open the editor.
- Click Import to open the Open window.
- Open the usbfilter.txt file that was downloaded from the server.