Este contenido no está disponible en el idioma seleccionado.
15.3. Managing Users and Groups for a CA, OCSP, KRA, or TKS
Many of the operations that users can perform are dictated by the groups that they belong to; for instance, agents for the CA manage certificates and profiles, while administrators manage CA server configuration.
Four subsystems — the CA, OCSP, KRA, and TKS — use the Java administrative console to manage groups and users. The TPS has web-based admin services, and users and groups are configured through its web service page.
15.3.1. Managing Groups
Note
pkiconsole is being deprecated.
15.3.1.1. Creating a New Group
- Log into the administrative console.
pkiconsole https://server.example.com:8443/subsystem_type
- Select Users and Groups from the navigation menu on the left.
- Select the Groups tab.
- Click , and fill in the group information.
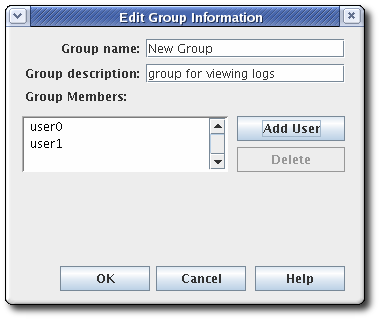 It is only possible to add users who already exist in the internal database.
It is only possible to add users who already exist in the internal database. - Edit the ACLs to grant the group privileges. See Section 15.5.4, “Editing ACLs” for more information. If no ACIs are added to the ACLs for the group, the group will have no access permissions to any part of Certificate System.
15.3.1.2. Changing Members in a Group
Members can be added or deleted from all groups. The group for administrators must have at least one user entry.
- Log into the administrative console.
- Select Users and Groups from the navigation tree on the left.
- Click the Groups tab.
- Select the group from the list of names, and click .
- Make the appropriate changes.
- To change the group description, type a new description in the Group description field.
- To remove a user from the group, select the user, and click .
- To add users, click . Select the users to add from the dialog box, and click .
15.3.2. Managing Users (Administrators, Agents, and Auditors)
The users for each subsystem are maintained separately. Just because a person is an administrator in one subsystem does not mean that person has any rights (or even a user entry) for another subsystem. Users can be configured and, with their user certificates, trusted as agents, administrators, or auditors for a subsystem.
15.3.2.1. Creating Users
After you installed Certificate System, only the user created during the setup exists. This section describes how to create additional users.
Note
For security reasons, create individual accounts for Certificate System users.
15.3.2.1.1. Creating Users Using the Command Line
To create a user using the command line:
- Add a user account. For example, to add the
exampleuser to the CA:# pki -d ~/.dogtag/pki-instance_name/ca/alias/ -c password -n caadmin \ ca-user-add example --fullName "Example User" --------------------- Added user "example" --------------------- User ID: example Full name: Example UserThis command uses thecaadminuser to add a new account. - Optionally, add a user to a group. For example, to add the
exampleuser to theCertificate Manager Agentsgroup:# pki -d ~/.dogtag/pki-instance_name/ -p password -n "caadmin" \ user-add-membership example Certificate Manager Agents - Create a certificate request:
- If a Key Recovery Authority (KRA) exists in your Certificate System environment:
# CRMFPopClient -d ~/.dogtag/pki-instance_name/ -p password \ -n "user_name" -q POP_SUCCESS -b kra.transport -w "AES/CBC/PKCS5Padding" \ -v -o ~/user_name.reqThis command stores the Certificate Signing Request (CSR) in theCRMFformat in the~/user_name.reqfile. - If no Key Recovery Authority (KRA) exists in your Certificate System environment:
- Create a NSS database directory:
#export pkiinstance=ca1#echo ${pkiinstance}#export agentdir=~/.dogtag/${pkiinstance}/agent1.dir#echo ${agentdir}#pki -d ${agentdir}/ -C ${somepwdfile} client-init - Store the CSR in a PKCS-#10 formatted file specified by the
-ooption,-dfor the path to an initialized NSS database directory,-Poption for a password file,-pfor a password, and-nfor a subject DN:#PKCS10Client -d ${agentdir}/ -P ${somepwdfile} -n "cn=agent1,uid=agent1" -o ${agentdir}/agent1.csrPKCS10Client: Certificate request written into /.dogtag/ca1/agent1.dir/agent1.csr PKCS10Client: PKCS#10 request key id written into /.dogtag/ca1/agent1.dir/agent1.csr.keyId
- Create an enrollment request:
- Create the
~/cmc.role_crmf.cfgfile with the following content:#numRequests: Total number of PKCS10 requests or CRMF requests. numRequests=1 #input: full path for the PKCS10 request or CRMF request, #the content must be in Base-64 encoded format #Multiple files are supported. They must be separated by space. input=~/user_name.req #output: full path for the CMC request in binary format output=~/cmc.role_crmf.req #tokenname: name of token where agent signing cert can be found (default is internal) tokenname=internal #nickname: nickname for agent certificate which will be used #to sign the CMC full request. nickname=PKI Administrator for Example.com #dbdir: directory for cert9.db, key4.db and pkcs11.txt dbdir=~/.dogtag/pki-instance_name/ #password: password for cert9.db which stores the agent #certificate password=password #format: request format, either pkcs10 or crmf format=crmf
Set the parameters based on your environment and the CSR format used in the previous step. - Pass the previously created configuration file to the
CMCRequestutility to create the CMC request:# CMCRequest ~/cmc.role_crmf.cfg
- Submit a Certificate Management over CMS (CMC) request:
- Create the
~/HttpClient_role_crmf.cfgfile with the following content:# #host: host name for the http server host=server.example.com #port: port number port=8443 #secure: true for secure connection, false for nonsecure connection secure=true #input: full path for the enrollment request, the content must be in binary format input=~/cmc.role_crmf.req #output: full path for the response in binary format output=~/cmc.role_crmf.resp #tokenname: name of token where SSL client authentication cert can be found (default is internal) #This parameter will be ignored if secure=false tokenname=internal #dbdir: directory for cert9.db, key4.db and pkcs11.txt #This parameter will be ignored if secure=false dbdir=~/.dogtag/pki-instance_name/ #clientmode: true for client authentication, false for no client authentication #This parameter will be ignored if secure=false clientmode=true #password: password for cert9.db #This parameter will be ignored if secure=false and clientauth=false password=password #nickname: nickname for client certificate #This parameter will be ignored if clientmode=false nickname=PKI Administrator for Example.com #servlet: servlet name servlet=/ca/ee/ca/profileSubmitCMCFull
Set the parameters based on your environment. - Submit the request to the CA:
# HttpClient ~/HttpClient_role_crmf.cfg Total number of bytes read = 3776 after SSLSocket created, thread token is Internal Key Storage Token client cert is not null handshake happened writing to socket Total number of bytes read = 2523 MIIJ1wYJKoZIhvcNAQcCoIIJyDCCCcQCAQMxDzANBglghkgBZQMEAgEFADAxBggr ... The response in data format is stored in ~/cmc.role_crmf.resp
- Verify the result:
# CMCResponse ~/cmc.role_crmf.resp Certificates: Certificate: Data: Version: v3 Serial Number: 0xE Signature Algorithm: SHA256withRSA - 1.2.840.113549.1.1.11 Issuer: CN=CA Signing Certificate,OU=pki-instance_name Security Domain Validity: Not Before: Friday, July 21, 2017 12:06:50 PM PDT America/Los_Angeles Not After: Wednesday, January 17, 2018 12:06:50 PM PST America/Los_Angeles Subject: CN=user_name ... Number of controls is 1 Control #0: CMCStatusInfoV2 OID: {1 3 6 1 5 5 7 7 25} BodyList: 1 Status: SUCCESS
- Optionally, to import the certificate as the user to its own
~/.dogtag/pki-instance_name/database:# certutil -d ~/.dogtag/pki-instance_name/ -A -t "u,u,u" -n "user_name certificate" -i ~/cmc.role_crmf.resp
- Add the certificate to the user record:
- List certificates issued for the user to discover the certificate's serial number. For example, to list certificates that contain the
exampleuser name in the certificate's subject:pki -d ~/.dogtag/pki-instance_name/ -c password -n caadmin ca-user-cert-find example ----------------- 1 entries matched ----------------- Cert ID: 2;6;CN=CA Signing Certificate,O=EXAMPLE;CN=PKI Administrator,E=example@example.com,O=EXAMPLE Version: 2 Serial Number: 0x6 Issuer: CN=CA Signing Certificate,O=EXAMPLE Subject: CN=PKI Administrator,E=example@example.com,O=EXAMPLE ---------------------------- Number of entries returned 1The serial number of the certificate is required in the next step. - Add the certificate using its serial number from the certificate repository to the user account in the Certificate System database. For example, for a CA user:
pki -c password -n caadmin ca-user-cert-add example --serial 0x6
15.3.2.1.2. Creating Users Using the Console
Note
pkiconsole is being deprecated.
To create a user using the PKI Console:
- Log into the administrative console.
pkiconsole https://server.example.com:8443/subsystem_type
- In the Configuration tab, select Users and Groups. Click .
- Fill in the information in the Edit User Information dialog.
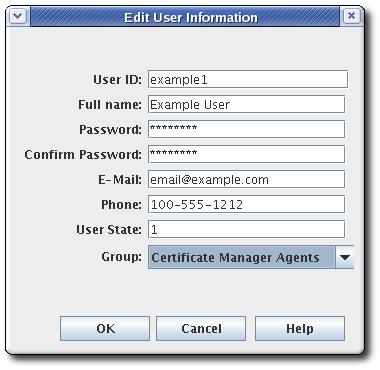 Most of the information is standard user information, such as the user's name, email address, and password. This window also contains a field called User State, which can contain any string, which is used to add additional information about the user; most basically, this field can show whether this is an active user.
Most of the information is standard user information, such as the user's name, email address, and password. This window also contains a field called User State, which can contain any string, which is used to add additional information about the user; most basically, this field can show whether this is an active user. - Select the group to which the user will belong. The user's group membership determines what privileges the user has. Assign agents, administrators, and auditors to the appropriate subsystem group.
- Store the user's certificate.
- Request a user certificate through the CA end-entities service page.
- If auto-enrollment is not configured for the user profile, then approve the certificate request.
- Retrieve the certificate using the URL provided in the notification email, and copy the base-64 encoded certificate to a local file or to the clipboard.
- Select the new user entry, and click .
- Click , and paste in the base-64 encoded certificate.
15.3.2.2. Changing a Certificate System User's Certificate
- Log into the administrative console.
- Select Users and Groups.
- Select the user to edit from the list of user IDs, and click .
- Click to add the new certificate.
- In the Import Certificate window, paste the new certificate in the text area. Include the
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----marker lines.
15.3.2.3. Renewing Administrator, Agent, and Auditor User Certificates
There are two methods of renewing a certificate. Regenerating the certificate takes its original key and its original profile and request, and recreates an identical key with a new validity period and expiration date. Re-keying a certificate resubmits the initial certificate request to the original profile, but generates a new key pair. Administrator certificates can be renewed by being re-keyed.
Each subsystem has a bootstrap user that was created at the time the subsystem was created. A new certificate can be requested for this user before their original one expires, using one of the default renewal profiles.
Certificates for administrative users can be renewed directly in the end user enrollment forms, using the serial number of the original certificate.
- Renew the admin user certificates in the CA's end users forms, as described in Section 5.4.1.1.2, “Certificate-Based Renewal”. This must be the same CA as first issued the certificate (or a clone of it).Agent certificates can be renewed by using the certificate-based renewal form in the end entities page. Self-renew user SSL client certificate. This form recognizes and updates the certificate stored in the browser's certificate store directly.
Note
It is also possible to renew the certificate usingcertutil, as described in Section 17.3.3, “Renewing Certificates Using certutil”. Rather than using the certificate stored in a browser to initiate renewal,certutiluses an input file with the original key. - Add the renewed user certificate to the user entry in the internal LDAP database.
- Open the console for the subsystem.
pkiconsole https://server.example.com:admin_port/subsystem_type
- Configuration | Users and Groups | Users | admin | Certificates | Import
- In the Configuration tab, select Users and Groups.
- In the Users tab, double-click the user entry with the renewed certificate, and click .
- Click , and paste in the base-64 encoded certificate.
Note
pkiconsoleis being deprecated.This can also be done by usingldapmodifyto add the renewed certification directly to the user entry in the internal LDAP database, by replacing theuserCertificateattribute in the user entry, such asuid=admin,ou=people,dc=subsystem-base-DN.
15.3.2.4. Renewing an Expired Administrator, Agent, and Auditor User Certificate
When a valid user certificate has already expired, you can no longer use the web service page nor the
pki command-line tool requiring authentication. In such a scenario, you can use the pki-server cert-fix command to renew an expired certificate.
Before you proceed, make sure:
- You have a valid CA certificate.
- You have root privileges.
Procedure 15.1. Renewing an Expired Administrator, Agent, and Auditor User Certificate
- Disable self test.
- Either run the following command:
#pki-server selftest-disable -i PKI_instance - Or remove the following line from CA's
CS.cfgfile and restart the CA subsystem:selftests.container.order.startup=CAPresence:critical, SystemCertsVerification:critical
- Check the expired certificates in the client's NSS database and find the certificate’s serial number (certificate ID).
- List the user certificates:
#certutil -L -d /root/nssdb/ - Get the expired certificate serial number, which you want to renew:
#certutil -L -d /root/nssdb/ -n Expired_cert | grep SerialSerial Number: 16 (0x10)
- Renew the certificate. The local LDAP server requires the LDAP Directory Manager’s password.
#pki-server cert-fix --ldap-url ldap://host389 --agent-uid caadmin -i PKI_instance -p PKI_https_port --extra-cert 16 - Re-eanable self test.
- Either run the following command:
#pki-server selftest-enable -i PKI_instance - Or add the following line to CA's
CS.cfgfile and restart the CA subsystem:selftests.container.order.startup=CAPresence:critical, SystemCertsVerification:critical
To verify that you have succeeded in the certificate renewal, you can display sufficient information about the certificate by running:
#pki ca-cert-find
To see full details of the specific certificate including attributes, extensions, public key modulus, hashes, and more, you can also run:
#pki ca-cert-show 16 --pretty
15.3.2.5. Deleting a Certificate System User
Users can be deleted from the internal database. Deleting a user from the internal database deletes that user from all groups to which the user belongs. To remove the user from specific groups, modify the group membership.
Delete a privileged user from the internal database by doing the following:
- Log into the administrative console.
- Select Users and Groups from the navigation menu on the left.
- Select the user from the list of user IDs, and click .
- Confirm the delete when prompted.