Este contenido no está disponible en el idioma seleccionado.
9.5. Creating Rules
Rules determine what certificate object is published in what location. Rules work independently, not in tandem. A certificate or CRL that is being published is matched against every rule. Any rule which it matches is activated. In this way, the same certificate or CRL can be published to a file, to an Online Certificate Status Manager, and to an LDAP directory by matching a file-based rule, an OCSP rule, and matching a directory-based rule.
Rules can be set for each object type: CA certificates, CRLs, user certificates, and cross-pair certificates. The rules can be more detailed for different kinds of certificates or different kinds of CRLs.
The rule first determines if the object matches by matching the type and predicate set up in the rule with the object. Where matching objects are published is determined by the publisher and mapper associated with the rule.
Rules are created for each type of certificate the Certificate Manager issues.
Modify publishing rules by doing the following:
- Log into the Certificate Manager Console.
pkiconsole https://server.example.com:8443/ca
- In the Configuration tab, select Certificate Manager from the navigation tree on the left. Select Publishing, and then Rules.The Rules Management tab, which lists configured rules, opens on the right.
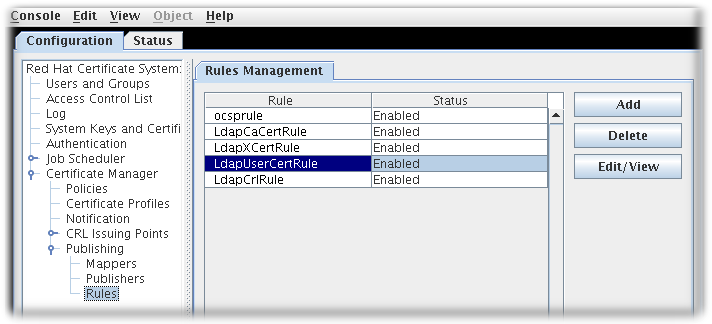
- To edit an existing rule, select that rule from the list, and click . This opens the Rule Editor window.
- To create a rule, click . This opens the Select Rule Plug-in Implementation window.
 Select the
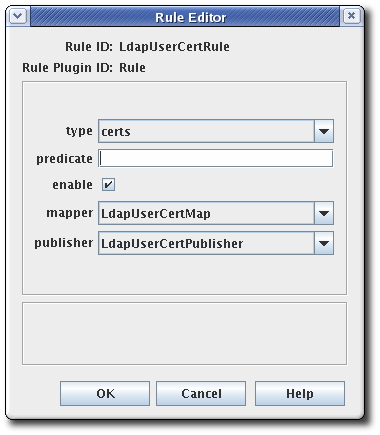
Select theRulemodule. This is the only default module. If any custom modules have been been registered, they are also available. - Edit the rule.

- type. This is the type of certificate for which the rule applies. For a CA signing certificate, the value is
cacert. For a cross-signed certificate, the value isxcert. For all other types of certificates, the value iscerts. For CRLs, specifycrl. - predicate. This sets the predicate value for the type of certificate or CRL issuing point to which this rule applies. The predicate values for CRL issuing points, delta CRLs, and certificates are listed in Table 9.3, “Predicate Expressions”.
- enable.
- mapper. Mappers are not necessary when publishing to a file; they are only needed for LDAP publishing. If this rule is associated with a publisher that publishes to an LDAP directory, select an appropriate mapper here. Leave blank for all other forms of publishing.
- publisher. Sets the publisher to associate with the rule.
Table 9.3, “Predicate Expressions” lists the predicates that can be used to identify CRL issuing points and delta CRLs and certificate profiles.
| Predicate Type | Predicate |
|---|---|
| CRL Issuing Point | issuingPointId==Issuing_Point_Instance_ID && isDeltaCRL==[true|false]
To publish only the master CRL, set
isDeltaCRL==false. To publish only the delta CRL, set isDeltaCRL==true. To publish both, set a rule for the master CRL and another rule for the delta CRL.
|
| Certificate Profile | profileId==profile_name
To publish certificates based on the profile used to issue them, set
profileId== to a profile name, such as caServerCert.
|
Note
pkiconsole is being deprecated.