Este contenido no está disponible en el idioma seleccionado.
2.4. Web Interface
2.4.1. Browser Initialization
This section explains browser initialization for Firefox to access PKI services.
Importing a CA Certificate
- Click
. 
- Select the Authorities tab and click the button.

- Select the
ca.crtfile and click .
Importing a Client Certificate
- Click
. - Select the Your Certificates tab.

- Click on and select the client p12 file, such as
ca_admin_cert.p12. - Enter the password for the client certificate on the prompt.
- Click .
- Verify that an entry is added under Your Certificates.
Accessing the Web Console
You can access the PKI services by opening
https://host_name:port in your browser.
2.4.2. The Administrative Interfaces
The all subsystems use HTML-based administrative interface. It is accessed by entering the host name and secure port as the URL, authenticating with the administrator's certificate, and clicking the appropriate Administrators link.
Note
There is a single TLS port for all subsystems which is used for both administrator and agent services. Access to those services is restricted by certificate-based authentication.
The HTML admin interface is much more limited than the Java console; the primary administrative function is managing the subsystem users.
The TPS only allows operations to manage users for the TPS subsystem. However, the TPS admin page can also list tokens and display all activities (including normally-hidden administrative actions) performed on the TPS.
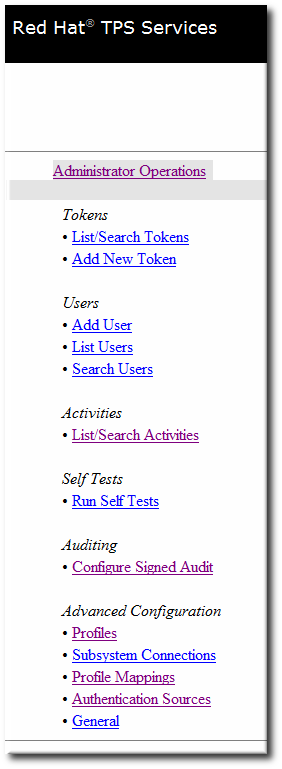
Figure 2.2. TPS Admin Page
2.4.3. Agent Interfaces
The agent services pages are where almost all of the certificate and token management tasks are performed. These services are HTML-based, and agents authenticate to the site using a special agent certificate.
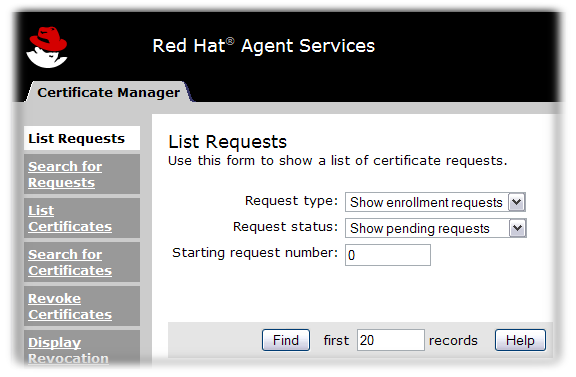
Figure 2.3. Certificate Manager's Agent Services Page
The operations vary depending on the subsystem:
- The Certificate Manager agent services include approving certificate requests (which issues the certificates), revoking certificates, and publishing certificates and CRLs. All certificates issued by the CA can be managed through its agent services page.
- The TPS agent services, like the CA agent services, manages all of the tokens which have been formatted and have had certificates issued to them through the TPS. Tokens can be enrolled, suspended, and deleted by agents. Two other roles (operator and admin) can view tokens in web services pages, but cannot perform any actions on the tokens.
- KRA agent services pages process key recovery requests, which set whether to allow a certificate to be issued reusing an existing key pair if the certificate is lost.
- The OCSP agent services page allows agents to configure CAs which publish CRLs to the OCSP, to load CRLs to the OCSP manually, and to view the state of client OCSP requests.
The TKS is the only subsystem without an agent services page.
2.4.4. End User Pages
The CA and TPS both process direct user requests in some way. That means that end users have to have a way to connect with those subsystems. The CA has end-user, or end-entities, HTML services. The TPS uses the Enterprise Security Client.
The end-user services are accessed over standard HTTP using the server's host name and the standard port number; they can also be accessed over HTTPS using the server's host name and the specific end-entities TLS port.
For CAs, each type of TLS certificate is processed through a specific online submission form, called a profile. There are about two dozen certificate profiles for the CA, covering all sorts of certificates — user TLS certificates, server TLS certificates, log and file signing certificates, email certificates, and every kind of subsystem certificate. There can also be custom profiles.
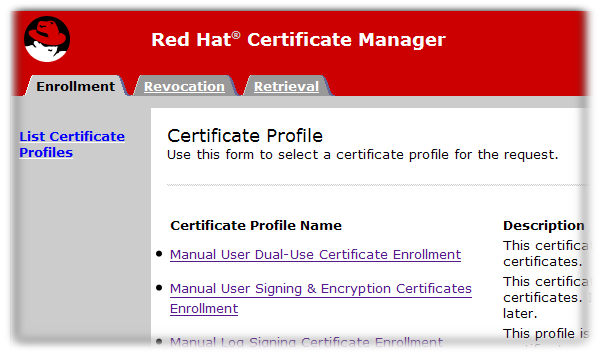
Figure 2.4. Certificate Manager's End-Entities Page
End users retrieve their certificates through the CA pages when the certificates are issued. They can also download CA chains and CRLs and can revoke or renew their certificates through those pages.