Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 4. Deploying the RHEL bootable images
You can deploy the rhel-bootc container image by using the following different mechanisms.
- Anaconda
-
bootc-image-builder -
bootc install
The following bootable image types are available:
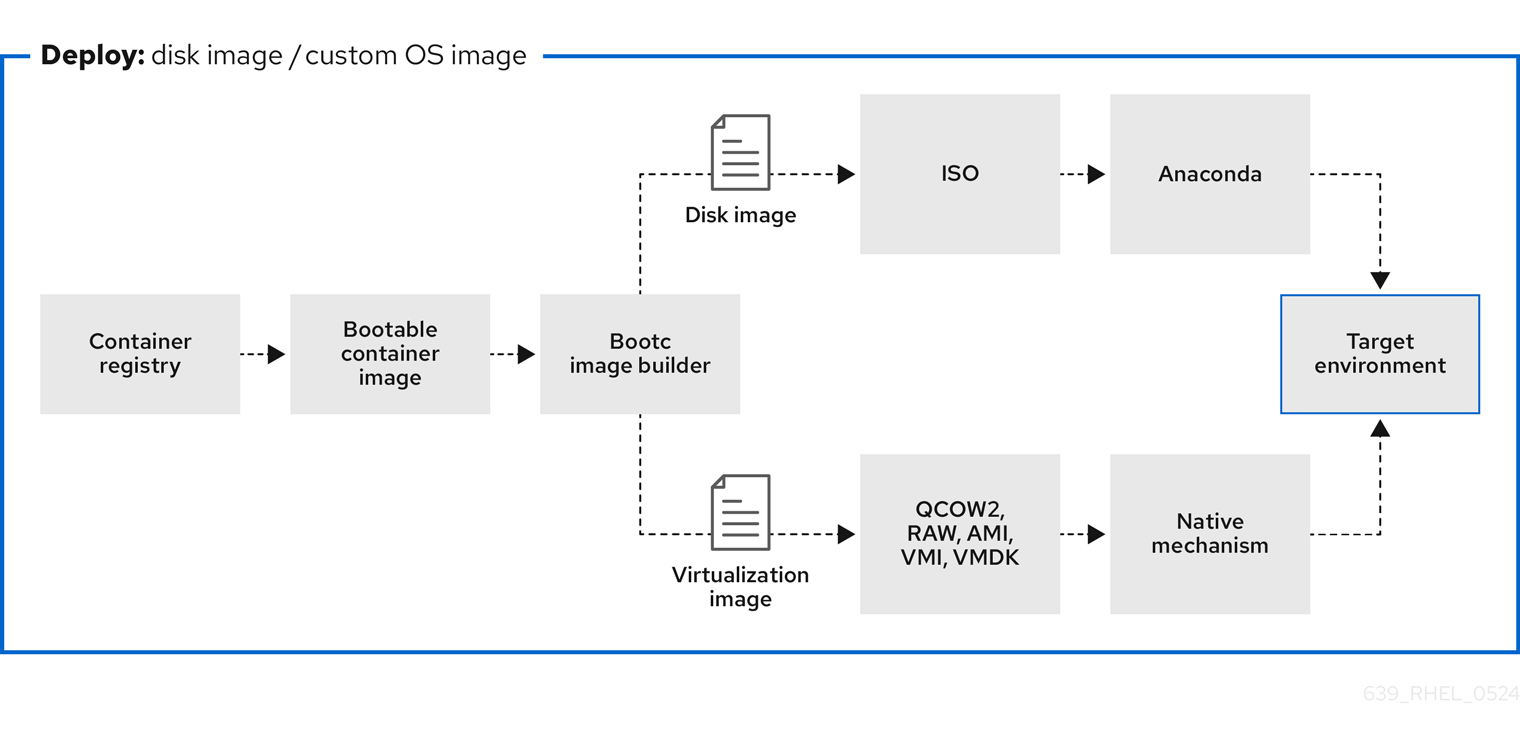
Disk images that you generated by using the
bootc image-buildersuch as:- QCOW2 (QEMU copy-on-write, virtual disk)
- Raw (Mac Format)
- AMI (Amazon Cloud)
- ISO: Unattended installation method, by using an USB Sticks or Install-on-boot.
After you have created a layered image that you can deploy, there are several ways that the image can be installed to a host:
You can use RHEL installer and Kickstart to install the layered image to a bare metal system, by using the following mechanisms:
- Deploy by using USB
- PXE
-
You can also use
bootc-image-builderto convert the container image to a bootable image and deploy it to a bare metal or to a cloud environment.
The installation method happens only one time. After you deploy your image, any future updates will apply directly from the container registry as the updates are published.
Figure 4.1. Deploying a bootable container image by using a basic build installer bootc install, or deploying a container image by using Anaconda and Kickstart
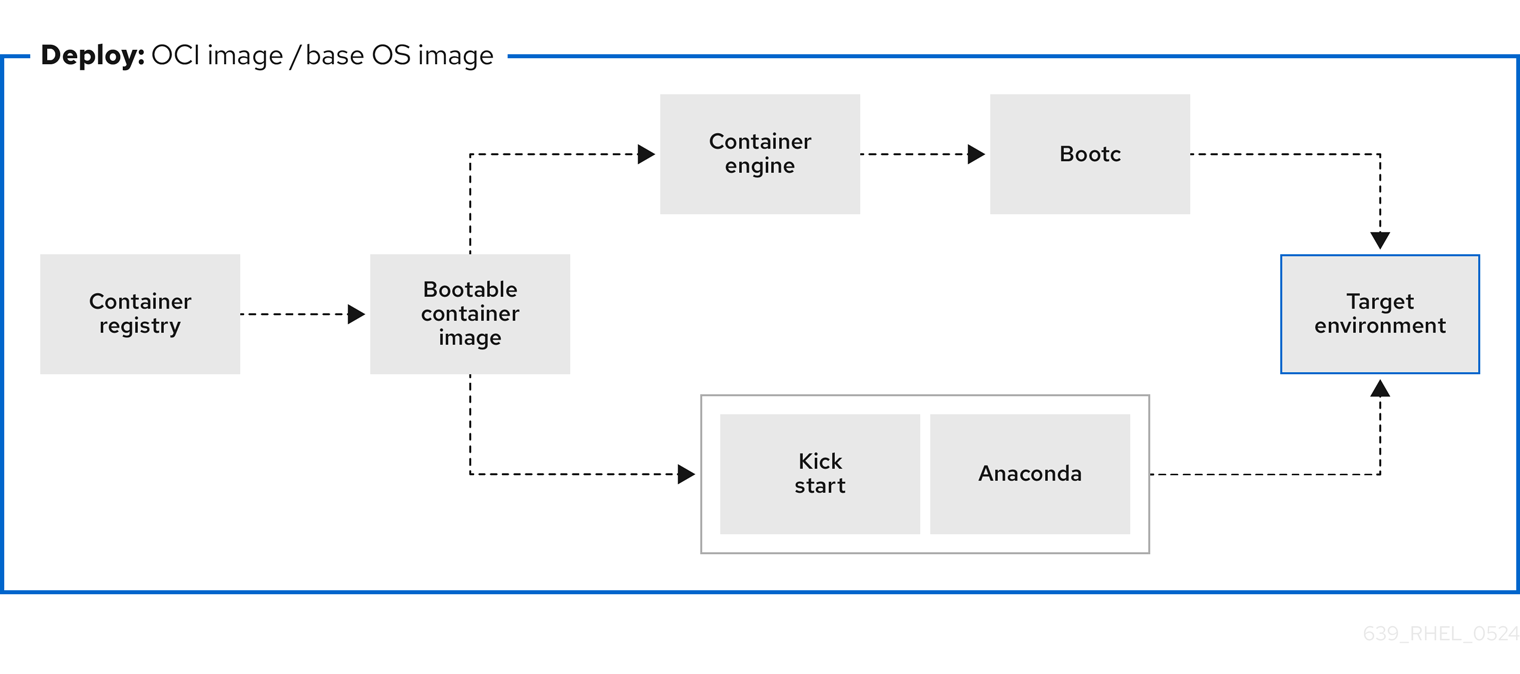
Figure 4.2. Using bootc-image-builder to create disk images from bootable container images and deploying disk images in different environments, such as the edge, servers, and clouds by using Anaconda, bootc-image-builder or bootc install
4.1. Deploying a container image by using KVM with a QCOW2 disk image
After creating a QEMU disk image from a RHEL bootable container image by using the bootc-image-builder tool, you can use a virtualization software to boot it.
Prerequisites
- You created a container image. See Creating QCOW2 images by using bootc-image-builder.
- You pushed the container image to an accessible repository.
Procedure
Run the container image that you create by using either
libvirt. See Creating virtual machines by using the command-line interface for more details.The following example uses
libvirt:$ sudo virt-install \ --name bootc \ --memory 4096 \ --vcpus 2 \ --disk qcow2/disk.qcow2 \ --import \ --os-variant rhel9-unknown
Verification
- Connect to the VM in which you are running the container image. See Connecting to virtual machines for more details.
Next steps
- You can make updates to the image and push the changes to a registry. See Managing RHEL bootable images.
Additional resources
4.2. Deploying a container image to AWS with an AMI disk image
After using the bootc-image-builder tool to create an AMI from a bootable container image, and uploading it to a AWS s3 bucket, you can deploy a container image to AWS with the AMI disk image.
Prerequisites
- You created an Amazon Machine Image (AMI) from a bootable container image. See Creating AMI images by using bootc-image-builder and uploading it to AWS.
-
cloud-initis available in the Containerfile that you previously created so that you can create a layered image for your use case.
Procedure
- In a browser, access Service→EC2 and log in.
- On the AWS console dashboard menu, choose the correct region. The image must have the Available status, to indicate that it was correctly uploaded.
- On the AWS dashboard, select your image and click .
- In the new window that opens, choose an instance type according to the resources you need to start your image. Click .
- Review your instance details. You can edit each section if you need to make any changes. Click .
- Before you start the instance, select a public key to access it. You can either use the key pair you already have or you can create a new key pair.
Click to start your instance. You can check the status of the instance, which displays as Initializing.
After the instance status is Running, the button becomes available.
- Click . A window appears with instructions on how to connect by using SSH.
Run the following command to set the permissions of your private key file so that only you can read it. See Connect to your Linux instance.
$ chmod 400 <your-instance-name.pem>Connect to your instance by using its Public DNS:
$ ssh -i <your-instance-name.pem>ec2-user@<your-instance-IP-address>
Your instance continues to run unless you stop it.
Verification
After launching your image, you can:
- Try to connect to http://<your_instance_ip_address> in a browser.
- Check if you are able to perform any action while connected to your instance by using SSH.
Next steps
- After you deploy your image, you can make updates to the image and push the changes to a registry. See Managing RHEL bootable images.
Additional resources
4.3. Deploying a container image by using Anaconda and Kickstart
After you convert your bootable container image to an ISO image by using bootc-image-builder, you can deploy the ISO image by using Anaconda and Kickstart to install your container image. The installable boot ISO already contains the ostreecontainer Kickstart file configured that you can use to provision your custom container image.
The use of rpm-ostree to make changes, or install content, is not supported.
Prerequisites
- You have downloaded the 9.4 Boot ISO for your architecture from Red Hat. See Downloading RH boot images.
Procedure
Create an
ostreecontainerKickstart file. For example:# Basic setup text network --bootproto=dhcp --device=link --activate # Basic partitioning clearpart --all --initlabel --disklabel=gpt reqpart --add-boot part / --grow --fstype xfs # Reference the container image to install - The kickstart # has no
%packagessection. A container image is being installed. ostreecontainer --url registry.redhat.io/rhel9/bootc-image-builder:latest firewall --disabled services --enabled=sshd # Only inject a SSH key for root rootpw --iscrypted locked sshkey --username root "<your key here>" rebootBoot a system by using the 9.4 Boot ISO installation media.
Append the Kickstart file with the following to the kernel argument:
inst.ks=http://<path_to_your_kickstart>
- Press CTRL+X to boot the system.
Next steps
- After you deploy your container image, you can make updates to the image and push the changes to a registry. See Managing RHEL bootable images.
Additional resources
- ostreecontainer documentation
- bootc upgrade fails when using local rpm-ostree modifications solution
4.4. Deploying a custom ISO container image
Convert a bootable container image to an ISO image by using bootc-image-builder. This creates a system similar to the RHEL ISOs available for download, except that your container image content is embedded in the ISO disk image. You do not need to have access to the network during installation. Then, you install the ISO disk image that you created from bootc-image-builder to a bare metal system.
Prerequisites
- You have created a customized container image.
Procedure
-
Create a custom installer ISO disk image with
bootc-image-builder. See Creating ISO images by using bootc-image-builder. - Copy the ISO disk image to a USB flash drive.
- Perform a bare metal installation by using the content in the USB stick into a disconnected environment.
Next steps
- After you deploy your container image, you can make updates to the image and push the changes to a registry. See Managing RHEL bootable images.
4.5. Deploying an ISO bootable container over PXE boot
You can use a network installation to deploy the RHEL ISO image over PXE boot to run your ISO bootable container image.
Prerequisites
- You have downloaded the 9.4 Boot ISO for your architecture from Red Hat. See Downloading RH boot images.
You have configured the server for the PXE boot. Choose one of the following options:
- For HTTP clients, see Configuring the DHCPv4 server for HTTP and PXE boot.
- For UEFI-based clients, see Configuring a TFTP server for UEFI-based clients.
- For BIOS-based clients, see Configuring a TFTP server for BIOS-based clients.
- You have a client, also known as the system to which you are installing your ISO image.
Procedure
- Export the RHEL installation ISO image to the HTTP server. The PXE boot server is now ready to serve PXE clients.
- Boot the client and start the installation.
- Select PXE Boot when prompted to specify a boot source. If the boot options are not displayed, press the Enter key on your keyboard or wait until the boot window opens.
- From the Red Hat Enterprise Linux boot window, select the boot option that you want, and press Enter.
- Start the network installation.
Next steps
- You can make updates to the image and push the changes to a registry. See Managing RHEL bootable images.
4.6. Building, configuring, and launching disk images with bootc-image-builder
You can inject configuration into a custom image by using a Containerfile.
Procedure
Create a disk image. The following example shows how to add a user to the disk image.
[[blueprint.customizations.user]] name = "user" password = "pass" key = "ssh-rsa AAA ... user@email.com" groups = ["wheel"]
-
name- User name. Mandatory -
password- Nonencrypted password. Not mandatory -
key- Public SSH key contents. Not mandatory -
groups- An array of groups to add the user into. Not mandatory
-
Run
bootc-image-builderand pass the following arguments:$ sudo podman run \ --rm \ -it \ --privileged \ --pull=newer \ --security-opt label=type:unconfined_t \ -v $(pwd)/config.toml:/config.toml \ -v $(pwd)/output:/output \ registry.redhat.io/rhel9/bootc-image-builder:latest \ --type qcow2 \ --config config.toml \ quay.io/<namespace>/<image>:<tag>
Launch a VM, for example, by using
virt-install:$ sudo virt-install \ --name bootc \ --memory 4096 \ --vcpus 2 \ --disk qcow2/disk.qcow2 \ --import \ --os-variant rhel9
Verification
Access the system with SSH:
# ssh -i /<path_to_private_ssh-key> <user1>@<ip-address>
Next steps
- After you deploy your container image, you can make updates to the image and push the changes to a registry. See Managing RHEL bootable images.
4.7. Deploying a container image by using bootc
With bootc, you have a container that is the source of truth. It contains a basic build installer and it is available as bootc install to-disk or bootc install to-filesystem. By using the bootc install methods you do not need to perform any additional steps to deploy the container image, because the container images include a basic installer.
With image mode for RHEL, you can install unconfigured images, for example, images that do not have a default password or SSH key.
Perform a bare metal installation to a device by using a RHEL ISO image.
Prerequisites
- You have downloaded the 9.4 Boot ISO for your architecture from Red Hat. See Downloading RH boot images.
- You have created a configuration file.
Procedure
inject a configuration into the running ISO image, for example:
$ podman run --rm --privileged --pid=host -v /var/lib/containers:/var/lib/containers --security-opt label=type:unconfined_t <image> bootc install to-disk <path-to-disk>
Next steps
- After you deploy your container image, you can make updates to the image and push the changes to a registry. See Managing RHEL bootable images.
4.8. Advanced installation with to-filesystem
The bootc install contains two subcommands: bootc install to-disk and bootc install to-filesystem.
-
The
bootc-install-to-filesystemperforms installation to the target filesystem. The
bootc install to-disksubcommand consists of a set of opinionated lower level tools that you can also call independently. The command consist of the following tools:-
mkfs.$fs /dev/disk -
mount /dev/disk /mnt -
bootc install to-filesystem --karg=root=UUID=<uuid of /mnt> --imgref $self /mnt
-
4.8.1. Using bootc install to-existing-root
The bootc install to-existing-root is a variant of install to-filesystem. You can use it to convert an existing system into the target container image.
This conversion eliminates the /boot and /boot/efi partitions and can delete the existing Linux installation. The conversion process reuses the filesystem, and even though the user data is preserved, the system no longer boots in package mode.
Prerequisites
- You must have root permissions to complete the procedure.
-
You must match the host environment and the target container version, for example, if your host is a RHEL 9 host, then you must have a RHEL 9 container. Installing a RHEL container on a Fedora host by using
btrfsas the RHEL kernel will not support that filesystem.
Procedure
Run the following command to convert an existing system into the target container image. Pass the target
rootfsby using the-v /:/targetoption.# podman run --rm --privileged -v /dev:/dev -v /var/lib/containers:/var/lib/containers -v /:/target \ --pid=host --security-opt label=type:unconfined_t \ <image> \ bootc install to-existing-root
This command deletes the data in
/boot, but everything else in the existing operating system is not automatically deleted. This can be useful because the new image can automatically import data from the previous host system. Consequently, container images, database, the user home directory data, configuration files in/etcare all available after the subsequent reboot in/sysroot.You can also use the
--root-ssh-authorized-keysflag to inherit the root user SSH keys, by adding--root-ssh-authorized-keys /target/root/.ssh/authorized_keys. For example:# podman run --rm --privileged -v /dev:/dev -v /var/lib/containers:/var/lib/containers -v /:/target \ --pid=host --security-opt label=type:unconfined_t \ <image> \ bootc install to-existing-root --root-ssh-authorized-keys /target/root/.ssh/authorized_keys