23.3. Authenticating to an Identity Management Client with a Smart Card
As an Identity Management user with multiple role accounts in the Identity Management server, you can authenticate with your smart card to a desktop client system joined to the Identity Management domain. This enables you to use the client system as the selected role.
For a basic overview of the supported options, see:
For information on configuring the environment to enable the authentication, see:
For information on how to authenticate, see:
23.3.1. Smart Card-based Authentication Options Supported on Identity Management Clients
Copy linkLink copied to clipboard!
Users in Identity Management can use the following options when authenticating using a smart card on Identity Management clients.
- Local authentication
- Local authentication includes authentication using:
- the text console
- the graphical console, such as the Gnome Display Manager (GDM)
- local authentication services, such as
suorsudo
- Remote authentication with
ssh - Certificates on a smart card are stored together with the PIN-protected SSH private key.
Smart card-based authentication using other services, such as FTP, is not supported.
23.3.2. Preparing the Identity Management Client for Smart-card Authentication
Copy linkLink copied to clipboard!
As the Identity Management administrator, perform these steps:
- On the server, create a shell script to configure the client.
- Use the ipa-advise config-client-for-smart-card-auth command, and save its output to a file:
ipa-advise config-client-for-smart-card-auth > client_smart_card_script.sh
# ipa-advise config-client-for-smart-card-auth > client_smart_card_script.shCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the script file, and review its contents.
- Add execute permissions to the file using the
chmodutility:chmod +x client_smart_card_script.sh
# chmod +x client_smart_card_script.shCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Copy the script to the client, and run it. Add the path to the PEM file with the certificate authority (CA) that signed the smart card certificate:
./client_smart_card_script.sh CA_cert.pem
# ./client_smart_card_script.sh CA_cert.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Additionally, if an external certificate authority (CA) signed the certificate on the smart card, add the smart card CA as a trusted CA:
- On the Identity Management server, install the CA certificate:
ipa-cacert-manage -n "SmartCard CA" -t CT,C,C install ca.pem ipa-certupdate
# ipa-cacert-manage -n "SmartCard CA" -t CT,C,C install ca.pem # ipa-certupdateCopy to Clipboard Copied! Toggle word wrap Toggle overflow Repeatipa-certupdatealso on all replicas and clients. - Restart the HTTP server:
systemctl restart httpd
# systemctl restart httpdCopy to Clipboard Copied! Toggle word wrap Toggle overflow Repeat systemctl restart httpd also on all replicas.
Note
SSSD enables administrators to tune the certificate verification process with the
certificate_verification parameter, for example if the Online Certificate Status Protocol (OCSP) servers defined in the certificate are not reachable from the client. For more information, see the sssd.conf(5) man page.
23.3.3. Authenticating on an Identity Management Client with a Smart Card Using the Console Login
Copy linkLink copied to clipboard!
To authenticate as an Identity Management user, enter the user name and PIN.
- When logging in from the command line:
client login: idm_user PIN for PIV Card Holder pin (PIV_II) for user idm_user@idm.example.com:
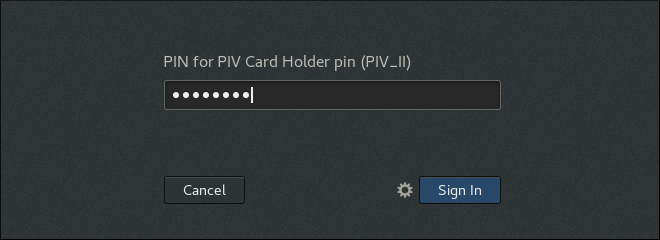
client login: idm_user PIN for PIV Card Holder pin (PIV_II) for user idm_user@idm.example.com:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - When logging in using the Gnome Desktop Manager (GDM), GDM prompts you for the smart card PIN after you select the required user:
Figure 23.13. Entering the smart card PIN in the Gnome Desktop Manager
To authenticate as an Active Directory user, enter the user name in a format that uses the NetBIOS domain name:
AD.EXAMPLE.COM\ad_user or ad_user@AD.EXAMPLE.COM.
If the authentication fails, see Section A.4, “Investigating Smart Card Authentication Failures”.
23.3.4. Authenticating to the Remote System from the Local System
Copy linkLink copied to clipboard!
On the local system, perform these steps:
- Insert the smart card.
- Launch
ssh, and specify the PKCS#11 library with the-Ioption:- As an Identity Management user:
ssh -I /usr/lib64/opensc-pkcs11.so -l idm_user server.idm.example.com
$ ssh -I /usr/lib64/opensc-pkcs11.so -l idm_user server.idm.example.com Enter PIN for 'PIV_II (PIV Card Holder pin)': Last login: Thu Apr 6 12:49:32 2017 from 10.36.116.42Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As an Active Directory user:
ssh -I /usr/lib64/opensc-pkcs11.so -l ad_user@ad.example.com server.idm.example.com
$ ssh -I /usr/lib64/opensc-pkcs11.so -l ad_user@ad.example.com server.idm.example.com Enter PIN for 'PIV_II (PIV Card Holder pin)': Last login: Thu Apr 6 12:49:32 2017 from 10.36.116.42Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Optional. Use the
idutility to check that you are logged in as the intended user.- As an Identity Management user:
id
$ id uid=1928200001(idm_user) gid=1928200001(idm_user) groups=1928200001(idm_user) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023Copy to Clipboard Copied! Toggle word wrap Toggle overflow - As an Active Directory user:
id
$ id uid=1171201116(ad_user@ad.example.com) gid=1171201116(ad_user@ad.example.com) groups=1171201116(ad_user@ad.example.com),1171200513(domain users@ad.example.com) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If the authentication fails, see Section A.4, “Investigating Smart Card Authentication Failures”.
23.3.5. Additional Resources
Copy linkLink copied to clipboard!
- Authentication using
sshwith a smart card does not obtain a ticket-granting ticket (TGT) on the remote system. To obtain a TGT on the remote system, the administrator must configure Kerberos on the local system and enable Kerberos delegation. For an example of the required configuration, see this Kerberos knowledge base entry. - For details on smart-card authentication with OpenSSH, see Using Smart Cards to Supply Credentials to OpenSSH in the Security Guide.