5.4. The IdM Web UI
ipa command-line utility. Therefore, the users can choose whether they want to manage IdM from the UI or from the command line.
admin user and other users with administrative privileges, all management tasks are available. For regular users, only a limited set of operations related to their own user account is available.
5.4.1. Supported Web Browsers
- Mozilla Firefox 38 and later
- Google Chrome 46 and later
5.4.2. Accessing the Web UI and Authenticating
5.4.2.1. Accessing the Web UI
https://server.example.com
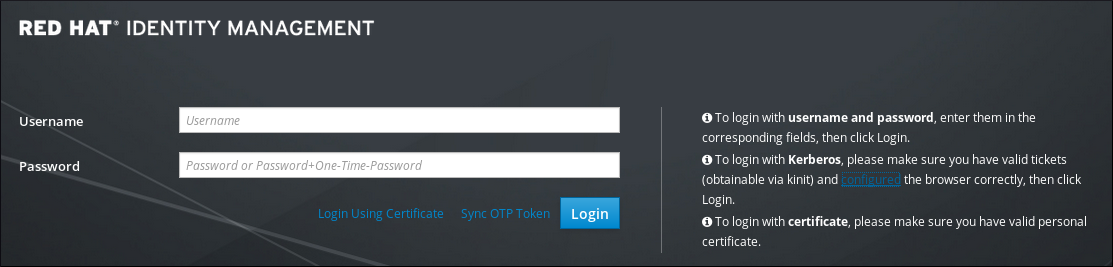
https://server.example.comFigure 5.1. Web UI Login Screen
5.4.2.2. Available Login Methods
- With an active Kerberos ticket
- If the user has a valid TGT obtained with the
kinitutility, clicking automatically authenticates the user. Note that the browser must be configured properly to support Kerberos authentication.For information on obtaining a Kerberos TGT, see Section 5.2, “Logging into IdM Using Kerberos”. For information on configuring the browser, see Section 5.4.3, “Configuring the Browser for Kerberos Authentication”. - By providing user name and password
- To authenticate using a user name and password, enter the user name and password on the web UI login screen.IdM also supports one-time password (OTP) authentication. For more information, see Section 22.3, “One-Time Passwords”.
- With a smart card
- For more information, see Section 23.6, “Authenticating to the Identity Management Web UI with a Smart Card”.
Figure 5.2. The IdM Web UI Layout
5.4.2.3. Web UI Session Length
5.4.2.4. Authenticating to the IdM Web UI as an AD User
ipa idoverrideuser-add 'Default Trust View' ad_user@ad.example.com
[admin@server ~]$ ipa idoverrideuser-add 'Default Trust View' ad_user@ad.example.com5.4.3. Configuring the Browser for Kerberos Authentication
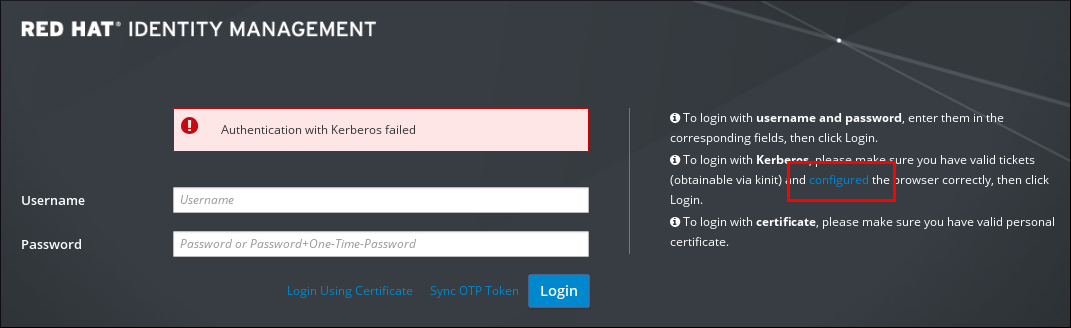
Figure 5.3. Kerberos Authentication Error
- Automatically from the IdM web UI. This option is only available for Firefox. See the section called “Automatic Firefox Configuration in the Web UI” for details.
- Automatically from the command line during the IdM client installation. This option is only available for Firefox. See the section called “Automatic Firefox Configuration from the Command Line” for details.
- Manually in the Firefox configuration settings. This option is available for all supported browsers. See the section called “Manual Browser Configuration” for details.
Automatic Firefox Configuration in the Web UI
- Click the link for browser configuration on the web UI login screen.
Figure 5.4. Link to Configuring the Browser in the Web UI
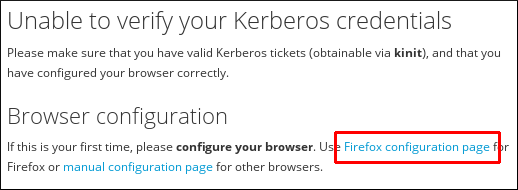
- Choose the link for Firefox configuration to open the Firefox configuration page.
Figure 5.5. Link to the Firefox Configuration Page
- Follow the steps on the Firefox configuration page.
Automatic Firefox Configuration from the Command Line
--configure-firefox option when installing the IdM client with the ipa-client-install utility:
ipa-client-install --configure-firefox
# ipa-client-install --configure-firefox--configure-firefox option creates a global configuration file with default Firefox settings that enable Kerberos for single sign-on (SSO).
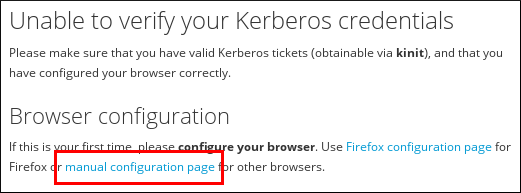
Manual Browser Configuration
- Click the link for browser configuration on the web UI login screen.
Figure 5.6. Link to Configuring the Browser in the Web UI
- Choose the link for manual browser configuration.
Figure 5.7. Link to the Manual Configuration Page
- Look for the instructions to configure your browser and follow the steps.
5.4.4. Configuring an External System for Kerberos Authentication to the Web UI
- Copy the
/etc/krb5.conffile from the IdM server to the external machine. For example:scp /etc/krb5.conf root@externalmachine.example.com:/etc/krb5_ipa.conf
# scp /etc/krb5.conf root@externalmachine.example.com:/etc/krb5_ipa.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow WarningDo not overwrite the existingkrb5.conffile on the external machine. - On the external machine, set the terminal session to use the copied IdM Kerberos configuration file:
export KRB5_CONFIG=/etc/krb5_ipa.conf
$ export KRB5_CONFIG=/etc/krb5_ipa.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the browser on the external machine as described in Section 5.4.3, “Configuring the Browser for Kerberos Authentication”.
kinit utility to authenticate against the IdM server domain.
5.4.5. Proxy Servers and Port Forwarding in the Web UI
-D option of the ssh utility; for more information on using -D, see the ssh(1) man page.