Chapter 27. Load balancing with MetalLB
27.1. Configuring MetalLB address pools
To allocate and manage the IP addresses assigned to load balancer services, configure MetalLB address pool custom resources. Defining these pools ensures that application workloads remain reachable through designated network ranges for consistent external access.
The namespaces used in the examples show metallb-system as the namespace.
For more information about how to install the MetalLB Operator, see About MetalLB and the MetalLB Operator.
27.1.1. About the IPAddressPool custom resource
To define the IP address ranges available for load balancer services, configure the properties of the MetalLB IPAddressPool custom resource (CR). Establishing these parameters allows your cluster to automatically allocate specific external addresses to your application workloads.
The following table details the parameters for the IPAddressPool CR:
| Parameter | Type | Description |
|---|---|---|
|
|
|
Specifies the name for the address pool. When you add a service, you can specify this pool name in the |
|
|
| Specifies the namespace for the address pool. Specify the same namespace that the MetalLB Operator uses. |
|
|
|
Optional: Specifies the key-value pair assigned to the |
|
|
| Specifies a list of IP addresses for the MetalLB Operator to assign to services. You can specify multiple ranges in a single pool, where these ranges all share the same settings. Specify each range in Classless Inter-Domain Routing (CIDR) notation or as starting and ending IP addresses separated with a hyphen. |
|
|
|
Optional: Specifies whether the MetalLB Operator automatically assigns IP addresses from this pool. Specify Note
For IP address pool configurations, ensure the addresses parameter specifies only IP addresses that are available and not in use by other network devices, especially gateway addresses, to prevent conflicts when |
|
|
|
Optional: When you set the parameter to enabled, the IP addresses ending |
You can assign IP addresses from an IPAddressPool to services and namespaces by configuring the spec.serviceAllocation specification.
| Parameter | Type | Description |
|---|---|---|
|
|
| Optional: Defines the priority between IP address pools when more than one IP address pool matches a service or namespace. A lower number indicates a higher priority. |
|
|
| Optional: Specifies a list of namespaces that you can assign to IP addresses in an IP address pool. |
|
|
| Optional: Specifies namespace labels that you can assign to IP addresses from an IP address pool by using label selectors in a list format. |
|
|
| Optional: Specifies service labels that you can assign to IP addresses from an address pool by using label selectors in a list format. |
27.1.2. Configuring an address pool
To precisely manage external access to application workloads, configure MetalLB address pools for your cluster. By defining these pools, you can control the specific IP address ranges assigned to load balancer services for consistent network routing.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create a file, such as
ipaddresspool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
labels-
The label assigned to the
IPAddressPoolcan be referenced by theipAddressPoolSelectorsin theBGPAdvertisementCRD to associate theIPAddressPoolwith the advertisement.
Apply the configuration for the IP address pool by entering the following command:
oc apply -f ipaddresspool.yaml
$ oc apply -f ipaddresspool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
View the address pool by entering the following command:
oc describe -n metallb-system IPAddressPool doc-example
$ oc describe -n metallb-system IPAddressPool doc-exampleCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Confirm that the address pool name, such as
doc-example, and the IP address ranges exist in the output.
27.1.3. Configure MetalLB address pool for VLAN
To precisely manage external access across a specific VLAN, configure MetalLB address pools for your cluster. Defining these pools ensures that load balancer services receive authorized IP addresses from designated network ranges for secure and consistent routing.
Prerequisites
-
Install the OpenShift CLI (
oc). - Configure a separate VLAN.
-
Log in as a user with
cluster-adminprivileges.
Procedure
Create a file, such as
ipaddresspool-vlan.yaml, that is similar to the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
labels.zone-
This label assigned to the
IPAddressPoolcan be referenced by theipAddressPoolSelectorsin theBGPAdvertisementCRD to associate theIPAddressPoolwith the advertisement. spec.addresses- This IP range must match the subnet assigned to the VLAN on your network. To support layer 2 (L2) mode, the IP address range must be within the same subnet as the cluster nodes.
Apply the configuration for the IP address pool:
oc apply -f ipaddresspool-vlan.yaml
$ oc apply -f ipaddresspool-vlan.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow To ensure this configuration applies to the VLAN, you need to set the
specgatewayConfig.ipForwardingtoGlobal.Run the following command to edit the network configuration custom resource (CR):
oc edit network.operator.openshift/cluster
$ oc edit network.operator.openshift/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update the
spec.defaultNetwork.ovnKubernetesConfigsection to include thegatewayConfig.ipForwardingset toGlobal. The following example demonstrates this configuration:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
27.1.4. Example address pool configurations
To precisely allocate IP address ranges for cluster services, configure MetalLB address pools by using Classless Inter-Domain Routing (CIDR) notation or hyphenated bounds. Defining these specific ranges ensures that application workloads receive valid IP assignments that align with your existing network infrastructure requirements.
- Example of IPv4 and CIDR ranges
- You can specify a range of IP addresses in classless inter-domain routing (CIDR) notation. You can combine CIDR notation with the notation that uses a hyphen to separate lower and upper bounds.
- Example of assigning IP addresses
-
You can set the
autoAssignparameter tofalseto prevent MetalLB from automatically assigning IP addresses from the address pool. You can then assign a single IP address or multiple IP addresses from an IP address pool. To assign an IP address, append the/32CIDR notation to the target IP address in thespec.addressesparameter. This setting ensures that only the specific IP address is available for assignment, leaving non-reserved IP addresses for application use.
Example IPAddressPool CR that assigns multiple IP addresses
When you add a service, you can request a specific IP address from the address pool or you can specify the pool name in an annotation to request any IP address from the pool.
- Example of IPv4 and IPv6 addresses
-
You can add address pools that use IPv4 and IPv6. You can specify multiple ranges in the
addresseslist, just like several IPv4 examples.
How the service is assigned to a single IPv4 address, a single IPv6 address, or both is determined by how you add the service. The spec.ipFamilies and spec.ipFamilyPolicy parameters control how IP addresses are assigned to the service.
spec.addresses: Where 10.0.100.0/28 is the local network IP address followed by the /28 network prefix.
- Example of assigning IP address pools to services or namespaces
-
You can assign IP addresses from an
IPAddressPoolto services and namespaces that you specify.
If you assign a service or namespace to more than one IP address pool, MetalLB uses an available IP address from the higher-priority IP address pool. If no IP addresses are available from the assigned IP address pools with a high priority, MetalLB uses available IP addresses from an IP address pool with lower priority or no priority.
You can use the matchLabels label selector, the matchExpressions label selector, or both, for the namespaceSelectors and serviceSelectors specifications. This example demonstrates one label selector for each specification.
where:
serviceAllocation.priority- Assign a priority to the address pool. A lower number indicates a higher priority.
serviceAllocation.namespaces- Assign one or more namespaces to the IP address pool in a list format.
serviceAllocation.namespaceSelectors- Assign one or more namespace labels to the IP address pool by using label selectors in a list format.
serviceAllocation.serviceSelectors- Assign one or more service labels to the IP address pool by using label selectors in a list format.
27.2. About advertising for the IP address pools
To provide fault-tolerant external IP addresses and load balancing for cluster services, configure MetalLB to advertise addresses by using Layer 2 protocols, the Border Gateway Protocol (BGP), or both. Selecting the appropriate protocol ensures reliable traffic routing and high availability for your application workloads.
MetalLB supports advertising by using Layer 2 and BGP for the same set of IP addresses.
MetalLB provides the flexibility to assign address pools to specific BGP peers, effectively limiting advertising to a subset of nodes on the network. This allows for more complex configurations, such as facilitating the isolation of nodes or the segmentation of the network.
27.2.1. About the BGPAdvertisement custom resource
To configure how the cluster announces IP addresses to external peers, define the properties of the BGPAdvertisement custom resource (CR). Specifying these parameters ensures that MetalLB correctly manages routing advertisements for your application services within the network.
The following table describes the parameters for the BGPAdvertisements CR:
| Parameter | Type | Description |
|---|---|---|
|
|
| Specifies the name for the BGP advertisement. |
|
|
| Specifies the namespace for the BGP advertisement. Specify the same namespace that the MetalLB Operator uses. |
|
|
|
Optional: Specifies the number of bits to include in a 32-bit CIDR mask. To aggregate the routes that the speaker advertises to BGP peers, the mask is applied to the routes for several service IP addresses and the speaker advertises the aggregated route. For example, with an aggregation length of |
|
|
|
Optional: Specifies the number of bits to include in a 128-bit CIDR mask. For example, with an aggregation length of |
|
|
| Optional: Specifies one or more BGP communities. Each community is specified as two 16-bit values separated by the colon character. Well-known communities must be specified as 16-bit values:
|
|
|
| Optional: Specifies the local preference for this advertisement. This BGP attribute applies to BGP sessions within the Autonomous System. |
|
|
|
Optional: The list of |
|
|
|
Optional: A selector for the |
|
|
|
Optional: By setting the |
|
|
|
Optional: Use a list to specify the |
27.2.2. Configure MetalLB with a BGP advertisement and a basic use case
To advertise specific IPv4 and IPv6 routes to peer BGP routers for assigned load-balancer IP addresses, configure MetalLB by using default preference and community settings. Establishing these routes ensures reliable external traffic delivery and consistent network propagation for your application services.
Ensure that you can configure MetalLB so that the peer BGP routers receive one 203.0.113.200/32 route and one fc00:f853:ccd:e799::1/128 route for each load-balancer IP address that MetalLB assigns to a service. If you do not specify the localPref and communities parameters, MetalLB advertises the routes with localPref set to `0 and no BGP communities.
27.2.2.1. Advertising a basic address pool configuration with BGP
To ensure application services are reachable from external network peers, configure MetalLB to advertise an IPAddressPool by using the BGP advertisement. Establishing this advertisement allows the external network to correctly route traffic to the load balancer IP addresses of your cluster services.
The procedure demonstrates how to configure MetalLB to advertise the IPAddressPool by using BGP.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create an IP address pool.
Create a file, such as
ipaddresspool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool:
oc apply -f ipaddresspool.yaml
$ oc apply -f ipaddresspool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a BGP advertisement.
Create a file, such as
bgpadvertisement.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration:
oc apply -f bgpadvertisement.yaml
$ oc apply -f bgpadvertisement.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.2.3. Configuring MetalLB with a BGP advertisement and an advanced use case
To assign application services specific IP addresses from designated IPv4 and IPv6 ranges, configure MetalLB for advanced address allocation. Establishing these ranges and BGP advertisements ensures that your load-balancer services remain reachable through predictable network paths.
Configure MetalLB so that MetalLB assigns IP addresses to load-balancer services in the ranges between 203.0.113.200 and 203.0.113.203 and between fc00:f853:ccd:e799::0 and fc00:f853:ccd:e799::f.
To explain the two BGP advertisements, consider an instance when MetalLB assigns the IP address of 203.0.113.200 to a service. With that IP address as an example, the speaker advertises the following two routes to BGP peers:
-
203.0.113.200/32, withlocalPrefset to100and the community set to the numeric value of theNO_ADVERTISEcommunity. This specification indicates to the peer routers that they can use this route but they should not propagate information about this route to BGP peers. -
203.0.113.200/30, aggregates the load-balancer IP addresses assigned by MetalLB into a single route. MetalLB advertises the aggregated route to BGP peers with the community attribute set to8000:800. BGP peers propagate the203.0.113.200/30route to other BGP peers. When traffic is routed to a node with a speaker, the203.0.113.200/32route is used to forward the traffic into the cluster and to a pod that is associated with the service.
As you add more services and MetalLB assigns more load-balancer IP addresses from the pool, peer routers receive one local route, 203.0.113.20x/32, for each service, and the 203.0.113.200/30 aggregate route. Each service that you add generates the /30 route, but MetalLB deduplicates the routes to one BGP advertisement before communicating with peer routers.
27.2.3.1. Advertising an advanced address pool configuration with BGP
To ensure application services are reachable from external network peers through specific routing paths, configure MetalLB to advertise an advanced address pool by using the BGP. Establishing this advertisement allows your cluster to precisely communicate routing information to the external infrastructure.
The procedure demonstrates how to configure MetalLB to advertise an advanced address pool by using the BGP.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create an IP address pool.
Create a file, such as
ipaddresspool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool:
oc apply -f ipaddresspool.yaml
$ oc apply -f ipaddresspool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a BGP advertisement.
Create a file, such as
bgpadvertisement1.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration:
oc apply -f bgpadvertisement1.yaml
$ oc apply -f bgpadvertisement1.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a file, such as
bgpadvertisement2.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration:
oc apply -f bgpadvertisement2.yaml
$ oc apply -f bgpadvertisement2.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.2.4. Advertising an IP address pool from a subset of nodes
To restrict IP address advertisements to a specific set of nodes, such as a public-facing subnet, configure the nodeSelector parameter in the BGPAdvertisement custom resource (CR). When you configure these selectors, OpenShift Container Platform routes external traffic only through designated network interfaces for improved security and isolation.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create an IP address pool by using a CR:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Control which cluster nodes advertise the IP address from
pool1by setting the.spec.nodeSelectorvalue in theBGPAdvertisementCR. The following example advertises the IP address frompool1only fromNodeAandNodeB.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
27.2.5. About the L2Advertisement custom resource
To configure how application services are announced over a Layer 2 network, define the properties in the L2Advertisement custom resource (CR). Establishing these parameters ensures that MetalLB correctly manages routing for your load-balancer IP addresses within the local network infrastructure
The following table details parameters for the l2Advertisements CR:
| Parameter | Type | Description |
|---|---|---|
|
|
| Specifies the name for the L2 advertisement. |
|
|
| Specifies the namespace for the L2 advertisement. Specify the same namespace that the MetalLB Operator uses. |
|
|
|
Optional: The list of |
|
|
|
Optional: A selector for the |
|
|
|
Optional: Important Limiting the nodes to announce as next hops is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process. For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope. |
|
|
|
Optional: The list of |
27.2.6. Configuring MetalLB with an L2 advertisement
To provide fault-tolerant external IP addresses for cluster services, configure MetalLB to advertise an IPAddressPool by using the Layer 2 protocol. Establishing this advertisement ensures that application workloads remain reachable within the local network through standard address discovery protocols.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create an IP address pool.
Create a file, such as
ipaddresspool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool:
oc apply -f ipaddresspool.yaml
$ oc apply -f ipaddresspool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an L2 advertisement.
Create a file, such as
l2advertisement.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration:
oc apply -f l2advertisement.yaml
$ oc apply -f l2advertisement.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.2.7. Configuring MetalLB with an L2 advertisement and labels
To dynamically associate IP address pools with advertisements by using labels instead of specific names, configure the ipAddressPoolSelectors parameter in the MetalLB custom resource (CR). By using selectors, you can manage network routing more efficiently by automatically grouping address pools as your cluster scales.
The example in the procedure shows how to configure MetalLB so that the IPAddressPool is advertised with the L2 protocol by configuring the ipAddressPoolSelectors field.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create an IP address pool.
Create a file, such as
ipaddresspool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool:
oc apply -f ipaddresspool.yaml
$ oc apply -f ipaddresspool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an L2 advertisement that advertises the IP address by using
ipAddressPoolSelectors.Create a file, such as
l2advertisement.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration:
oc apply -f l2advertisement.yaml
$ oc apply -f l2advertisement.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.2.8. Configuring MetalLB with an L2 advertisement for selected interfaces
To restrict which network interfaces advertise assigned service IP addresses, configure the interfaces parameter in the MetalLB L2Advertisement custom resource (CR). Defining specific interfaces ensures that cluster services are reachable only through designated network paths for improved traffic management and isolation.
The example in the procedure shows how to configure MetalLB so that the IP address pool is advertised only from the network interfaces listed in the interfaces parameter of all nodes.
Prerequisites
-
You have installed the OpenShift CLI (
oc). -
You are logged in as a user with
cluster-adminprivileges.
Procedure
Create an IP address pool.
Create a file, such as
ipaddresspool.yaml, and enter the configuration details as shown in the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool as shown in the following example:
oc apply -f ipaddresspool.yaml
$ oc apply -f ipaddresspool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an L2 advertisement with the
interfacesselector to advertise the IP address.Create a YAML file, such as
l2advertisement.yaml, and enter the configuration details as shown the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the advertisement as shown in the following example:
oc apply -f l2advertisement.yaml
$ oc apply -f l2advertisement.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThe interface selector does not affect how MetalLB chooses the node to announce a given IP by using L2. The chosen node does not announce the service if the node does not have the selected interface.
27.2.9. Configuring MetalLB with secondary networks
To enable traffic forwarding for MetalLB on a secondary network interface, add a machine configuration that allows IP packet forwarding between interfaces. Implementing this configuration ensures that application services remain reachable when they use nondefault network paths.
From OpenShift Container Platform 4.14 the default network behavior does not allow forwarding of IP packets between network interfaces.
OpenShift Container Platform clusters upgraded from 4.13 are not affected because a global parameter is set during an upgrade to enable global IP forwarding.
To enable IP forwarding for the secondary interface, you have two options:
- Enable IP forwarding for all interfaces.
Enable IP forwarding for a specific interface.
NoteEnabling IP forwarding for a specific interface provides more granular control, while enabling it for all interfaces applies a global setting.
Procedure
Enable forwarding for a specific secondary interface, such as
bridge-netby creating and applying aMachineConfigCR.-
Create the
MachineConfigCR to enable IP forwarding for the specified secondary interface namedbridge-net. Save the following YAML in the
enable-ip-forward.yamlfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<node_role>-
Node role where you want to enable IP forwarding, for example,
worker.
Apply the configuration by running the following command:
oc apply -f enable-ip-forward.yaml
$ oc apply -f enable-ip-forward.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
Create the
Optional: Enable IP forwarding globally by running the following command:
oc patch network.operator cluster -p '{"spec":{"defaultNetwork":{"ovnKubernetesConfig":{"gatewayConfig":{"ipForwarding": "Global"}}}}}' --type=merge$ oc patch network.operator cluster -p '{"spec":{"defaultNetwork":{"ovnKubernetesConfig":{"gatewayConfig":{"ipForwarding": "Global"}}}}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.3. Configuring MetalLB BGP peers
To establish BGP sessions and advertise routes for load balancer services, configure MetalLB Border Gateway Protocol (BGP) peer custom resources (CRs). Defining these peers ensures that your network infrastructure receives accurate routing information to reach cluster application workloads.
You can add, modify, and delete BGP peers. The MetalLB Operator uses the BGP peer custom resources to identify the peers that MetalLB speaker pods contact to start BGP sessions. The peers receive the route advertisements for the load-balancer IP addresses that MetalLB assigns to services.
27.3.1. About the BGP peer custom resource
To establish network connectivity and advertise routes for load-balancer services, configure the properties of the MetalLB Border Gateway Protocol (BGP) peer custom resource (CR). Establishing these parameters ensures that your cluster authorizes specific routing peers to direct external traffic correctly to your application workloads.
The following table describes the parameters for the BGP peer CR:
| Parameter | Type | Description |
|---|---|---|
|
|
| Specifies the name for the BGP peer CR. |
|
|
| Specifies the namespace for the BGP peer CR. |
|
|
|
Specifies the Autonomous System Number (ASN) for the local end of the BGP session. In all BGP peer CRs that you add, specify the same value. The range is |
|
|
|
Specifies the ASN for the remote end of the BGP session. The range is |
|
|
|
Detects the ASN to use for the remote end of the session without explicitly setting it. Specify |
|
|
| Specifies the IP address of the peer to contact for establishing the BGP session. |
|
|
| Optional: Specifies the IP address to use when establishing the BGP session. The value must be an IPv4 address. |
|
|
|
Optional: Specifies the network port of the peer to contact for establishing the BGP session. The range is |
|
|
|
Optional: Specifies the duration for the hold time to propose to the BGP peer. The minimum value is 3 seconds ( |
|
|
|
Optional: Specifies the maximum interval between sending keep-alive messages to the BGP peer. If you specify this parameter, you must also specify a value for the |
|
|
| Optional: Specifies the router ID to advertise to the BGP peer. If you specify this parameter, you must specify the same value in every BGP peer custom resource that you add. |
|
|
| Optional: Specifies the MD5 password to send to the peer for routers that enforce TCP MD5 authenticated BGP sessions. |
|
|
|
Optional: Specifies name of the authentication secret for the BGP peer. The secret must live in the |
|
|
| Optional: Specifies the name of a BFD profile. |
|
|
| Optional: Specifies a selector, using match expressions and match labels, to control which nodes can connect to the BGP peer. |
|
|
|
Optional: Specifies that the BGP peer is multiple network hops away. If the BGP peer is not directly connected to the same network, the speaker cannot establish a BGP session unless this parameter is set to |
The passwordSecret parameter is mutually exclusive with the password parameter, and contains a reference to a secret containing the password to use. Setting both parameters results in a failure of the parsing.
27.3.2. Configuring a BGP peer
To exchange routing information and advertise IP addresses for load balancer services, configure MetalLB BGP peer CRs. Establishing these peers ensures that your network infrastructure can reach and correctly route traffic to cluster application workloads.
You can add a BGP peer custom resource to exchange routing information with network routers and advertise the IP addresses for services.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges. - Configure MetalLB with a BGP advertisement.
Procedure
Create a file, such as
bgppeer.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the BGP peer configuration by entering the following command:
oc apply -f bgppeer.yaml
$ oc apply -f bgppeer.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.3.3. Configure a specific set of BGP peers for a given address pool
To assign specific IP address pools to designated BGP peers, configure MetalLB BGP advertisements. Establishing these mappings ensures that your cluster advertises designated network ranges only to authorized routing peers for precise external traffic control.
This procedure demonstrates the following tasks:
-
Configure a set of address pools:
pool1andpool2. -
Configure a set of BGP peers:
peer1andpeer2. -
Configure BGP advertisement to assign
pool1topeer1andpool2topeer2.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create address pool
pool1.Create a file, such as
ipaddresspool1.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool
pool1:oc apply -f ipaddresspool1.yaml
$ oc apply -f ipaddresspool1.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create address pool
pool2.Create a file, such as
ipaddresspool2.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool
pool2:oc apply -f ipaddresspool2.yaml
$ oc apply -f ipaddresspool2.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create BGP
peer1.Create a file, such as
bgppeer1.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the BGP
peer1:oc apply -f bgppeer1.yaml
$ oc apply -f bgppeer1.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create BGP
peer2.Create a file, such as
bgppeer2.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the BGP
peer2:oc apply -f bgppeer2.yaml
$ oc apply -f bgppeer2.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create BGP advertisement 1.
Create a file, such as
bgpadvertisement1.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration:
oc apply -f bgpadvertisement1.yaml
$ oc apply -f bgpadvertisement1.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create BGP advertisement 2.
Create a file, such as
bgpadvertisement2.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration:
oc apply -f bgpadvertisement2.yaml
$ oc apply -f bgpadvertisement2.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.3.4. Exposing a service through a network VRF
To isolate network traffic and manage multiple routing tables, expose a service through a virtual routing and forwarding (VRF) instance. Associating a VRF with a MetalLB BGP peer ensures that external traffic is segmented and correctly routed to the intended application workloads.
Exposing a service through a VRF on a BGP peer is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
By using a VRF on a network interface to expose a service through a BGP peer, you can segregate traffic to the service, configure independent routing decisions, and enable multi-tenancy support on a network interface.
By establishing a BGP session through an interface belonging to a network VRF, MetalLB can advertise services through that interface and enable external traffic to reach the service through this interface. However, the network VRF routing table is different from the default VRF routing table used by OVN-Kubernetes. Therefore, the traffic cannot reach the OVN-Kubernetes network infrastructure.
To enable the traffic directed to the service to reach the OVN-Kubernetes network infrastructure, you must configure routing rules to define the next hops for network traffic. See the NodeNetworkConfigurationPolicy resource in "Managing symmetric routing with MetalLB" in the Additional resources section for more information.
The following high-level steps demonstrate how to expose a service through a network VRF with a BGP peer:
- Define a BGP peer and add a network VRF instance.
- Specify an IP address pool for MetalLB.
- Configure a BGP route advertisement for MetalLB to advertise a route by using the specified IP address pool and the BGP peer associated with the VRF instance.
- Deploy a service to test the configuration.
Prerequisites
-
You installed the OpenShift CLI (
oc). -
You logged in as a user with
cluster-adminprivileges. -
You defined a
NodeNetworkConfigurationPolicy(NNCP) to associate a Virtual Routing and Forwarding (VRF) instance with a network interface. For more information about completing this prerequisite, see the Additional resources section. - You installed MetalLB on your cluster.
Procedure
Create a
BGPPeercustom resource (CR):Create a file, such as
frrviavrf.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow spec.vrf: Specifies the network VRF instance to associate with the BGP peer. MetalLB can advertise services and make routing decisions based on the routing information in the VRF.NoteYou must configure this network VRF instance in a
NodeNetworkConfigurationPolicyCR. See the Additional resources for more information.Apply the configuration for the BGP peer by running the following command:
oc apply -f frrviavrf.yaml
$ oc apply -f frrviavrf.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an
IPAddressPoolCR:Create a file, such as
first-pool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool by running the following command:
oc apply -f first-pool.yaml
$ oc apply -f first-pool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
BGPAdvertisementCR:Create a file, such as
first-adv.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow peers.frrviavrf: In this example, MetalLB advertises a range of IP addresses from thefirst-poolIP address pool to thefrrviavrfBGP peer.Apply the configuration for the BGP advertisement by running the following command:
oc apply -f first-adv.yaml
$ oc apply -f first-adv.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
Namespace,Deployment, andServiceCR:Create a file, such as
deploy-service.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the namespace, deployment, and service by running the following command:
oc apply -f deploy-service.yaml
$ oc apply -f deploy-service.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Identify a MetalLB speaker pod by running the following command:
oc get -n metallb-system pods -l component=speaker
$ oc get -n metallb-system pods -l component=speakerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME READY STATUS RESTARTS AGE speaker-c6c5f 6/6 Running 0 69m
NAME READY STATUS RESTARTS AGE speaker-c6c5f 6/6 Running 0 69mCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the state of the BGP session is
Establishedin the speaker pod by running the following command, replacing the variables to match your configuration:oc exec -n metallb-system <speaker_pod> -c frr -- vtysh -c "show bgp vrf <vrf_name> neigh"
$ oc exec -n metallb-system <speaker_pod> -c frr -- vtysh -c "show bgp vrf <vrf_name> neigh"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
BGP neighbor is 192.168.30.1, remote AS 200, local AS 100, external link BGP version 4, remote router ID 192.168.30.1, local router ID 192.168.30.71 BGP state = Established, up for 04:20:09 ...
BGP neighbor is 192.168.30.1, remote AS 200, local AS 100, external link BGP version 4, remote router ID 192.168.30.1, local router ID 192.168.30.71 BGP state = Established, up for 04:20:09 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the service is advertised correctly by running the following command:
oc exec -n metallb-system <speaker_pod> -c frr -- vtysh -c "show bgp vrf <vrf_name> ipv4"
$ oc exec -n metallb-system <speaker_pod> -c frr -- vtysh -c "show bgp vrf <vrf_name> ipv4"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
27.3.6. Example BGP peer configurations
To precisely manage network topology and improve routing resilience, configure MetalLB BGP peer settings that limit node connectivity and incorporate BFD profiles. Defining these parameters ensures that your cluster maintains secure peer relationships and rapidly detects path failures for high service availability.
- Example of limiting which nodes connect to a BGP peer
-
You can specify the
nodeSelectorsparameter to control which nodes can connect to a BGP peer.
- Example of specifying a BFD profile for a BGP peer
- You can specify a BFD profile to associate with BGP peers. BFD complements BGP by providing faster detection of communication failures between peers than BGP alone.
Deleting the bidirectional forwarding detection (BFD) profile and removing the bfdProfile added to the border gateway protocol (BGP) peer resource does not disable the BFD. Instead, the BGP peer starts using the default BFD profile. To disable BFD from a BGP peer resource, delete the BGP peer configuration and recreate it without a BFD profile. For more information, see BZ#2050824.
- Example of specifying BGP peers for dual-stack networking
- To support dual-stack networking, add one BGP peer custom resource for IPv4 and one BGP peer custom resource for IPv6.
27.4. Configuring community alias
As a cluster administrator, you can configure a community alias and use it across different advertisements.
27.4.1. About the community custom resource
To simplify BGP configuration, define named aliases for community values by using the community custom resource. You can reference these aliases when advertising ipAddressPools with the BGPAdvertisement resource.
The fields for the community custom resource are described in the following table.
The community CRD applies only to BGPAdvertisement.
| Field | Type | Description |
|---|---|---|
|
|
|
Specifies the name for the |
|
|
|
Specifies the namespace for the |
|
|
|
Specifies a list of BGP community aliases that can be used in BGPAdvertisements. A community alias consists of a pair of name (alias) and value (number:number). Link the BGPAdvertisement to a community alias by referring to the alias name in its |
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the alias for the |
|
|
|
The BGP |
27.4.2. Configuring MetalLB with a BGP advertisement and community alias
To advertise an IPAddressPool by using the BGP protocol, configure MetalLB with a community alias. This configuration sets the alias to the numeric value of the NO_ADVERTISE community.
In the following example, the peer BGP router doc-example-peer-community receives one 203.0.113.200/32 route and one fc00:f853:ccd:e799::1/128 route for each load-balancer IP address that MetalLB assigns to a service. A community alias is configured with the NO_ADVERTISE community.
Prerequisites
-
Install the OpenShift CLI (
oc) -
Log in as a user with
cluster-adminprivileges.
Procedure
Create an IP address pool.
Create a file, such as
ipaddresspool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool:
oc apply -f ipaddresspool.yaml
$ oc apply -f ipaddresspool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a community alias named
community1.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a BGP peer named
doc-example-bgp-peer.Create a file, such as
bgppeer.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the BGP peer:
oc apply -f bgppeer.yaml
$ oc apply -f bgppeer.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a BGP advertisement with the community alias.
Create a file, such as
bgpadvertisement.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
NO_ADVERTISE: Specifies theCommunityAlias.namehere and not the community custom resource (CR) name.Apply the configuration:
oc apply -f bgpadvertisement.yaml
$ oc apply -f bgpadvertisement.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.5. Configuring MetalLB BFD profiles
To achieve faster path failure detection for BGP sessions, configure MetalLB Bidirectional Forwarding Detection (BFD) profiles. Establishing these profiles ensures that your network routing remains highly available and responsive by identifying connectivity issues more quickly than standard protocols.
You can add, modify, and delete BFD profiles. The MetalLB Operator uses the BFD profile custom resources (CRs) to identify the BGP sessions that use BFD.
27.5.1. About the BFD profile custom resource
To enable rapid detection of communication failures between routing peers, configure the properties of the MetalLB BFD profile custom resource (CR). Defining these parameters ensures that network traffic is quickly rerouted if a path becomes unavailable, maintaining high cluster reachability and stability.
The following table describes parameters for the BFD profile CR:
| Parameter | Type | Description |
|---|---|---|
|
|
| Specifies the name for the BFD profile custom resource. |
|
|
| Specifies the namespace for the BFD profile custom resource. |
|
|
| Specifies the detection multiplier to determine packet loss. The remote transmission interval is multiplied by this value to determine the connection loss detection timer.
For example, when the local system has the detect multiplier set to |
|
|
|
Specifies the echo transmission mode. If you are not using distributed BFD, echo transmission mode works only when the peer is also FRR. The default value is
When echo transmission mode is enabled, consider increasing the transmission interval of control packets to reduce bandwidth usage. For example, consider increasing the transmit interval to |
|
|
|
Specifies the minimum transmission interval, less jitter, that this system uses to send and receive echo packets. The range is |
|
|
| Specifies the minimum expected TTL for an incoming control packet. This field applies to multi-hop sessions only.
The purpose of setting a minimum TTL is to make the packet validation requirements more stringent and avoid receiving control packets from other sessions. The default value is |
|
|
| Specifies whether a session is marked as active or passive. A passive session does not attempt to start the connection. Instead, a passive session waits for control packets from a peer before it begins to reply.
Marking a session as passive is useful when you have a router that acts as the central node of a star network and you want to avoid sending control packets that you do not need the system to send. The default value is |
|
|
|
Specifies the minimum interval that this system is capable of receiving control packets. The range is |
|
|
|
Specifies the minimum transmission interval, less jitter, that this system uses to send control packets. The range is |
27.5.2. Configuring a BFD profile
To achieve faster path failure detection for BGP sessions, configure a MetalLB BFD profile and associate it with a BGP peer. Establishing these profiles ensures that your network routing remains highly available and responsive by identifying connectivity issues more rapidly than standard protocols.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create a file, such as
bfdprofile.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the BFD profile:
oc apply -f bfdprofile.yaml
$ oc apply -f bfdprofile.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
27.6. Configuring services to use MetalLB
To ensure predictable network endpoints, control how MetalLB assigns IP addresses to services of type LoadBalancer. Requesting specific addresses or pools ensures that your applications receive valid IP assignments that align with your specific network addressing plan.
27.6.1. Request a specific IP address
To assign a specific, static IP address to a service, configure the spec.loadBalancerIP parameter in the service specification.
MetalLB attempts to assign the requested address from the configured address pools, ensuring that your service is reachable at a designated, static network endpoint. If the requested IP address is not within any range, MetalLB reports a warning.
Example service YAML for a specific IP address
If MetalLB cannot assign the requested IP address, the EXTERNAL-IP for the service reports <pending> and running oc describe service <service_name> includes an event like the following example:
Example event when MetalLB cannot assign a requested IP address
... Events: Type Reason Age From Message ---- ------ ---- ---- ------- Warning AllocationFailed 3m16s metallb-controller Failed to allocate IP for "default/invalid-request": "4.3.2.1" is not allowed in config
...
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Warning AllocationFailed 3m16s metallb-controller Failed to allocate IP for "default/invalid-request": "4.3.2.1" is not allowed in config27.6.2. Request an IP address from a specific pool
To ensure predictable network endpoints, control how MetalLB assigns IP addresses to services of type LoadBalancer. Requesting specific addresses or pools ensures that your applications receive valid IP assignments that align with your specific network addressing plan.
Example service YAML for an IP address from a specific pool
If the address pool that you specify for <address_pool_name> does not exist, MetalLB attempts to assign an IP address from any pool that permits automatic assignment.
27.6.3. Accept any IP address
To automatically allocate IP addresses to services without manual specification, configure MetalLB address pools to permit automatic assignment. MetalLB dynamically assigns available addresses from these pools, ensuring seamless service deployment and network connectivity.
Example service YAML for accepting any IP address
27.6.5. Configuring a service with MetalLB
To expose an application to external network traffic, configure a load-balancing service. MetalLB assigns an external IP address from a configured address pool, ensuring that your application is reachable from outside the cluster.
Prerequisites
-
Install the OpenShift CLI (
oc). - Install the MetalLB Operator and start MetalLB.
- Configure at least one address pool.
- Configure your network to route traffic from the clients to the host network for the cluster.
Procedure
Create a
<service_name>.yamlfile. In the file, set thespec.typeparameter toLoadBalancer.Refer to the examples for information about how to request the external IP address that MetalLB assigns to the service.
Create the service:
oc apply -f <service_name>.yaml
$ oc apply -f <service_name>.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
service/<service_name> created
service/<service_name> createdCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Describe the service:
oc describe service <service_name>
$ oc describe service <service_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
Annotations- Specifies the annotation that is present if you request an IP address from a specific pool.
Type-
Specifies the service type that must indicate
LoadBalancer. LoadBalancer Ingress- Specifies the indicates the external IP address if the service is assigned correctly.
Events- Specifies the events parameter that indicates the node name that is assigned to announce the external IP address. If you experience an error, the events parameter indicates the reason for the error.
27.7. Managing symmetric routing with MetalLB
As a cluster administrator, you can effectively manage traffic for pods behind a MetalLB load-balancer service with multiple host interfaces by implementing features from MetalLB, NMState, and OVN-Kubernetes. By combining these features in this context, you can provide symmetric routing, traffic segregation, and support clients on different networks with overlapping CIDR addresses.
To achieve this functionality, learn how to implement virtual routing and forwarding (VRF) instances with MetalLB, and configure egress services.
Configuring symmetric traffic by using a VRF instance with MetalLB and an egress service is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
27.7.1. Challenges of managing symmetric routing with MetalLB
To resolve network isolation and asymmetric routing challenges on multiple host interfaces, implement a configuration combining MetalLB, NMState, and OVN-Kubernetes. This solution ensures symmetric routing and prevents overlapping CIDR addresses without requiring manual static route maintenance.
One option to ensure that return traffic reaches the correct client is to use static routes. However, with this solution, MetalLB cannot isolate the services and then announce each service through a different interface. Additionally, static routing requires manual configuration and requires maintenance if remote sites are added.
A further challenge of symmetric routing when implementing a MetalLB service is scenarios where external systems expect the source and destination IP address for an application to be the same. The default behavior for OpenShift Container Platform is to assign the IP address of the host network interface as the source IP address for traffic originating from pods. This is problematic with multiple host interfaces.
You can overcome these challenges by implementing a configuration that combines features from MetalLB, NMState, and OVN-Kubernetes.
27.7.2. Overview of managing symmetric routing by using VRFs with MetalLB
You can overcome the challenges of implementing symmetric routing by using NMState to configure a VRF instance on a host, associating the VRF instance with a MetalLB BGPPeer resource, and configuring an egress service for egress traffic with OVN-Kubernetes.
Figure 27.1. Network overview of managing symmetric routing by using VRFs with MetalLB
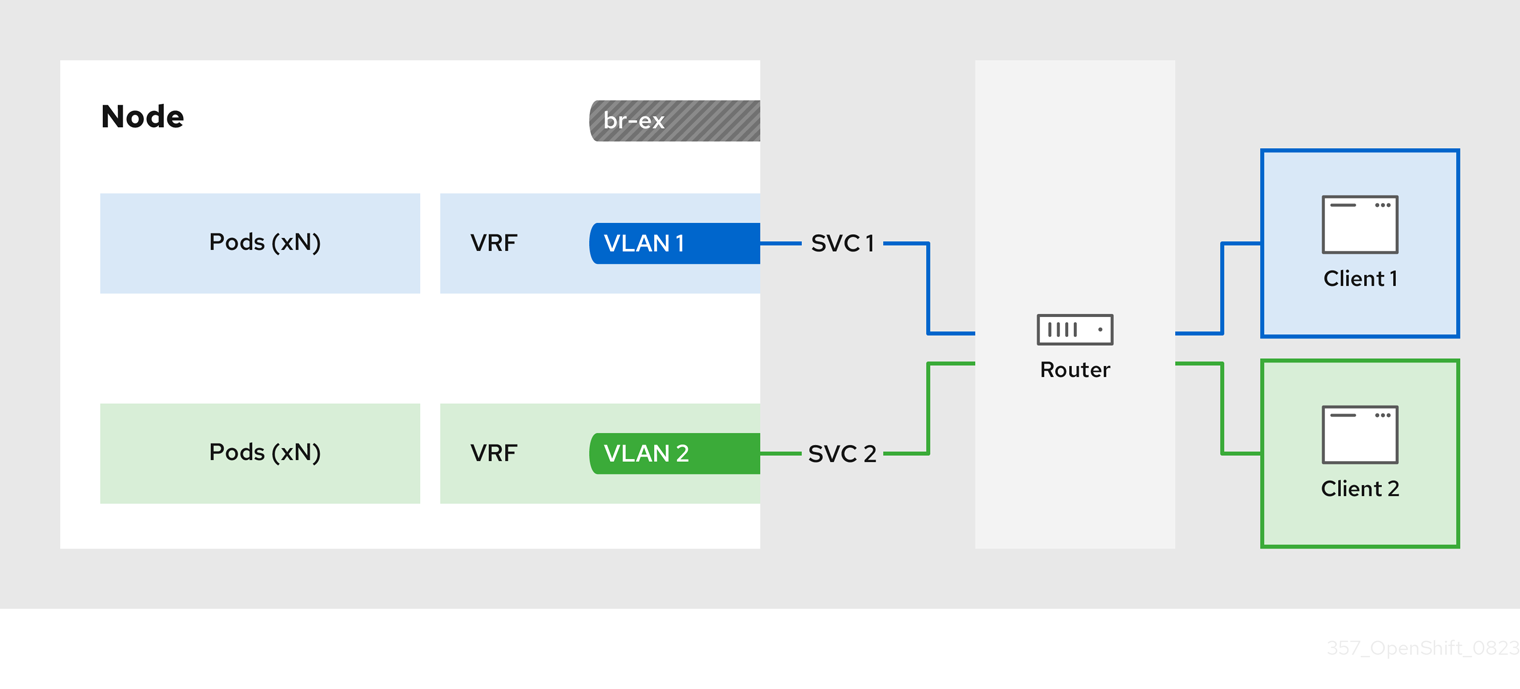
The configuration process involves three stages:
- 1: Define a VRF and routing rules
-
Configure a
NodeNetworkConfigurationPolicycustom resource (CR) to associate a VRF instance with a network interface. - Use the VRF routing table to direct ingress and egress traffic.
-
Configure a
- 2: Link the VRF to a MetalLB
BGPPeer -
Configure a MetalLB
BGPPeerresource to use the VRF instance on a network interface. -
By associating the
BGPPeerresource with the VRF instance, the designated network interface becomes the primary interface for the BGP session, and MetalLB advertises the services through this interface.
-
Configure a MetalLB
- 3: Configure an egress service
- Configure an egress service to choose the network associated with the VRF instance for egress traffic.
- Optional: Configure an egress service to use the IP address of the MetalLB load-balancer service as the source IP for egress traffic.
27.7.3. Configuring symmetric routing by using VRFs with MetalLB
To ensure that applications behind a MetalLB service use the same network path for both ingress and egress, configure symmetric routing by using Virtual Routing and Forwarding (VRF).
The example in the procedure associates a VRF routing table with MetalLB and an egress service to enable symmetric routing for ingress and egress traffic for pods behind a LoadBalancer service.
-
If you use the
sourceIPBy: "LoadBalancerIP"setting in theEgressServiceCR, you must specify the load-balancer node in theBGPAdvertisementcustom resource (CR). -
You can use the
sourceIPBy: "Network"setting on clusters that use OVN-Kubernetes configured with thegatewayConfig.routingViaHostspecification set totrueonly. Additionally, if you use thesourceIPBy: "Network"setting, you must schedule the application workload on nodes configured with the network VRF instance.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges. - Install the Kubernetes NMState Operator.
- Install the MetalLB Operator.
Procedure
Create a
NodeNetworkConfigurationPolicyCR to define the VRF instance:Create a file, such as
node-network-vrf.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
metadata.name- Specifies the name of the policy.
nodeSelector.vrf-
Specifies the policy for all nodes with the label
vrf:true. interfaces.name.ens4vrf- Specifies the name of the interface.
interfaces.type- Specifies the type of interface. This example creates a VRF instance.
vrf.port- Specifies the node interface that the VRF attaches to.
vrf.route-table-id- Specifies the name of the route table ID for the VRF.
- `interfaces.name.ens4 `
- Specifies the IPv4 address of the interface associated with the VRF.
routes-
Specifies the configuration for network routes. The
next-hop-addressfield defines the IP address of the next hop for the route. Thenext-hop-interfacefield defines the outgoing interface for the route. In this example, the VRF routing table is2, which references the ID that you define in theEgressServiceCR. route-rules-
Specifies additional route rules. The
ip-tofields must match theCluster NetworkCIDR,Service NetworkCIDR, andInternal Masqueradesubnet CIDR. You can view the values for these CIDR address specifications by running the following command:oc describe network.operator/cluster. route-rules.route-table-
Specifies the main routing table that the Linux kernel uses when calculating routes has the ID
254.
Apply the policy by running the following command:
oc apply -f node-network-vrf.yaml
$ oc apply -f node-network-vrf.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
BGPPeercustom resource (CR):Create a file, such as
frr-via-vrf.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
spec.vrf- Specifies the VRF instance to associate with the BGP peer. MetalLB can advertise services and make routing decisions based on the routing information in the VRF.
Apply the configuration for the BGP peer by running the following command:
oc apply -f frr-via-vrf.yaml
$ oc apply -f frr-via-vrf.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an
IPAddressPoolCR:Create a file, such as
first-pool.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration for the IP address pool by running the following command:
oc apply -f first-pool.yaml
$ oc apply -f first-pool.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
BGPAdvertisementCR:Create a file, such as
first-adv.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
peers-
In this example, MetalLB advertises a range of IP addresses from the
first-poolIP address pool to thefrrviavrfBGP peer. nodeSelectors-
In this example, the
EgressServiceCR configures the source IP address for egress traffic to use the load-balancer service IP address. Therefore, you must specify the load-balancer node for return traffic to use the same return path for the traffic originating from the pod.
Apply the configuration for the BGP advertisement by running the following command:
oc apply -f first-adv.yaml
$ oc apply -f first-adv.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an
EgressServiceCR:Create a file, such as
egress-service.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
metadata.name-
Specifies the name for the egress service. The name of the
EgressServiceresource must match the name of the load-balancer service that you want to modify. metadata.namespace-
Specifies the namespace for the egress service. The namespace for the
EgressServicemust match the namespace of the load-balancer service that you want to modify. The egress service is namespace-scoped. spec.sourceIPBy-
Specifies the
LoadBalancerservice ingress IP address as the source IP address for egress traffic. matchLabels.vrf-
If you specify
LoadBalancerfor thesourceIPByspecification, a single node handles theLoadBalancerservice traffic. In this example, only a node with the labelvrf: "true"can handle the service traffic. If you do not specify a node, OVN-Kubernetes selects a worker node to handle the service traffic. When a node is selected, OVN-Kubernetes labels the node in the following format:egress-service.k8s.ovn.org/<svc_namespace>-<svc_name>: "". network-
Specifyies the routing table ID for egress traffic. Ensure that the value matches the
route-table-idID defined in theNodeNetworkConfigurationPolicyresource, for example,route-table-id: 2.
Apply the configuration for the egress service by running the following command:
oc apply -f egress-service.yaml
$ oc apply -f egress-service.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that you can access the application endpoint of the pods running behind the MetalLB service by running the following command:
curl <external_ip_address>:<port_number>
$ curl <external_ip_address>:<port_number>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
<external_ip_address>:<port_number>: Specifies the external IP address and port number to suit your application endpoint.
-
-
Optional: If you assigned the
LoadBalancerservice ingress IP address as the source IP address for egress traffic, verify this configuration by using tools such astcpdumpto analyze packets received at the external client.
27.8. Configuring the integration of MetalLB and FRR-K8s
To access advanced routing services not natively provided by MetalLB, configure the FRRConfiguration custom resource (CR). Defining the CR exposes specific FRRouting (FRR) capabilities and extends the routing functionality of your cluster beyond standard MetalLB advertisements.
The FRRConfiguration custom resource is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
FRRouting (FRR) is a free, open-source internet routing protocol suite for Linux and UNIX platforms. FRR-K8s is a Kubernetes-based DaemonSet that exposes a subset of the FRR API in a Kubernetes-compliant manner. MetalLB generates the FRR-K8s configuration corresponding to the MetalLB configuration applied.

When configuring Virtual Route Forwarding (VRF), you must change the VRFs to a table ID lower than 1000 as higher than 1000 is reserved for OpenShift Container Platform.
27.8.1. Activating the integration of MetalLB and FRR-K8s
The following procedure shows you how to activate FRR-K8s as the backend for MetalLB.
Prerequisites
- You have a cluster installed on bare-metal hardware.
-
You have installed the OpenShift CLI (
oc). -
You have logged in as a user with
cluster-adminprivileges.
Procedure
Set the
bgpBackendfield of theMetalLBCR tofrr-k8sas in the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
27.8.2. FRR configurations
You can create multiple FRRConfiguration CRs to use FRR services in MetalLB.
MetalLB generates an FRRConfiguration object which FRR-K8s merges with all other configurations that all users have created. For example, you can configure FRR-K8s to receive all of the prefixes advertised by a given neighbor. The following example configures FRR-K8s to receive all of the prefixes advertised by a BGPPeer with host 172.18.0.5:
Example FRRConfiguration CR
You can also configure FRR-K8s to always block a set of prefixes, regardless of the configuration applied. This can be useful to avoid routes going to pods or ClusterIPs CIDRs that might result in cluster malfunctions. The following example blocks the set of prefixes 192.168.1.0/24:
Example MetalLB CR
You can set FRR-K8s to block the clusterNetwork CIDR and serviceNetwork CIDR. You can view the values for these CIDR address specifications by running the following command:
oc describe network.config/cluster
$ oc describe network.config/cluster27.8.3. Configuring the FRRConfiguration CRD
To customize routing behavior beyond standard MetalLB capabilities, configure the FRRConfiguration custom resource (CR).
The following reference examples demonstrate how to define specific FRRouting (FRR) parameters to enable advanced services, such as receiving routes:
- The
routersparameter -
You can use the
routersparameter to configure multiple routers, one for each Virtual Routing and Forwarding (VRF) resource. For each router, you must define the Autonomous System Number (ASN).
You can also define a list of Border Gateway Protocol (BGP) neighbors to connect to, as in the following example:
Example FRRConfiguration CR
- The
toAdvertiseparameter -
By default,
FRR-K8sdoes not advertise the prefixes configured as part of a router configuration. To advertise the prefixes, you use thetoAdvertiseparameter.
You can advertise a subset of the prefixes, as in the following example:
Example FRRConfiguration CR
-
allowed.prefixes: Advertises a subset of prefixes.
The following example shows you how to advertise all of the prefixes:
Example FRRConfiguration CR
allowed.mode: Advertises all prefixes.- The
toReceiveparameter -
By default,
FRR-K8sdoes not process any prefixes advertised by a neighbor. You can use thetoReceiveparameter to process such addresses.
- The
You can configure for a subset of the prefixes, as in this example:
Example FRRConfiguration CR
-
prefixes: The prefix is applied if the prefix length is less than or equal to theleprefix length and greater than or equal to thegeprefix length.
The following example configures FRR to handle all the prefixes announced:
Example FRRConfiguration CR
- The
bgpparameter -
You can use the
bgpparameter to define variousBFDprofiles and associate them with a neighbor. In the following example,BFDbacks up theBGPsession andFRRcan detect link failures:
Example FRRConfiguration CR
- The
nodeSelectorparameter -
By default,
FRR-K8sapplies the configuration to all nodes where the daemon is running. You can use thenodeSelectorparameter to specify the nodes to which you want to apply the configuration. For example:
Example FRRConfiguration CR
The fields for the FRRConfiguration custom resource are described in the following table:
| Parameter | Type | Description |
|---|---|---|
|
|
| Specifies the routers that FRR is to configure (one per VRF). |
|
|
| The Autonomous System Number (ASN) to use for the local end of the session. |
|
|
|
Specifies the ID of the |
|
|
| Specifies the host VRF used to establish sessions from this router. |
|
|
| Specifies the neighbors to establish BGP sessions with. |
|
|
| Specifies the ASN to use for the remote end of the session. |
|
|
| Specifies the IP address to establish the session with. |
|
|
|
Specifies the port to dial when establishing the session. Defaults to |
|
|
|
Specifies the password to use for establishing the BGP session. |
|
|
|
Specifies the name of the authentication secret for the neighbor. The secret must be of type "kubernetes.io/basic-auth", and in the same namespace as the FRR-K8s daemon. The key "password" stores the password in the secret. |
|
|
| Specifies the requested BGP hold time, per RFC4271. Defaults to 180s. |
|
|
|
Specifies the requested BGP keepalive time, per RFC4271. Defaults to |
|
|
| Specifies how long BGP waits between connection attempts to a neighbor. |
|
|
| Indicates if the BGPPeer is a multi-hop away. |
|
|
| Specifies the name of the BFD Profile to use for the BFD session associated with the BGP session. If not set, the BFD session is not set up. |
|
|
| Represents the list of prefixes to advertise to a neighbor, and the associated properties. |
|
|
| Specifies the list of prefixes to advertise to a neighbor. This list must match the prefixes that you define in the router. |
|
|
|
Specifies the mode to use when handling the prefixes. You can set to |
|
|
| Specifies the prefixes associated with an advertised local preference. You must specify the prefixes associated with a local preference in the prefixes allowed to be advertised. |
|
|
| Specifies the prefixes associated with the local preference. |
|
|
| Specifies the local preference associated with the prefixes. |
|
|
| Specifies the prefixes associated with an advertised BGP community. You must include the prefixes associated with a local preference in the list of prefixes that you want to advertise. |
|
|
| Specifies the prefixes associated with the community. |
|
|
| Specifies the community associated with the prefixes. |
|
|
| Specifies the prefixes to receive from a neighbor. |
|
|
| Specifies the information that you want to receive from a neighbor. |
|
|
| Specifies the prefixes allowed from a neighbor. |
|
|
|
Specifies the mode to use when handling the prefixes. When set to |
|
|
| Disables MP BGP to prevent it from separating IPv4 and IPv6 route exchanges into distinct BGP sessions. |
|
|
| Specifies all prefixes to advertise from this router instance. |
|
|
| Specifies the list of BFD profiles to use when configuring the neighbors. |
|
|
| The name of the BFD Profile to be referenced in other parts of the configuration. |
|
|
|
Specifies the minimum interval at which this system can receive control packets, in milliseconds. Defaults to |
|
|
|
Specifies the minimum transmission interval, excluding jitter, that this system wants to use to send BFD control packets, in milliseconds. Defaults to |
|
|
| Configures the detection multiplier to determine packet loss. To determine the connection loss-detection timer, multiply the remote transmission interval by this value. |
|
|
|
Configures the minimal echo receive transmission-interval that this system can handle, in milliseconds. Defaults to |
|
|
| Enables or disables the echo transmission mode. This mode is disabled by default, and not supported on multihop setups. |
|
|
| Mark session as passive. A passive session does not attempt to start the connection and waits for control packets from peers before it begins replying. |
|
|
| For multihop sessions only. Configures the minimum expected TTL for an incoming BFD control packet. |
|
|
| Limits the nodes that attempt to apply this configuration. If specified, only those nodes whose labels match the specified selectors attempt to apply the configuration. If it is not specified, all nodes attempt to apply this configuration. |
|
|
| Defines the observed state of FRRConfiguration. |
27.8.4. How FRR-K8s merges multiple configurations
FRR-K8s uses an additive merge strategy when multiple users configure the same node. By using FRR-K8s, you can extend existing configurations, such as adding neighbors or prefixes, but prevent the removal of components defined by other sources.
- Configuration conflicts
Certain configurations can cause conflicts, leading to errors, for example:
- different ASN for the same router (in the same VRF)
- different ASN for the same neighbor (with the same IP / port)
- multiple BFD profiles with the same name but different values
When the daemon finds an invalid configuration for a node, it reports the configuration as invalid and reverts to the previous valid FRR configuration.
- Merging
When merging, iyou can complete the following actions:
- Extend the set of IP addresses that you want to advertise to a neighbor.
- Add an extra neighbor with its set of IP addresses.
- Extend the set of IP addresses to which you want to associate a community.
- Allow incoming routes for a neighbor.
Each configuration must be self contained. This means, for example, that you cannot allow prefixes that are not defined in the router section by leveraging prefixes coming from another configuration.
If the configurations to be applied are compatible, merging works as follows:
-
FRR-K8scombines all the routers. -
FRR-K8smerges all prefixes and neighbors for each router. -
FRR-K8smerges all filters for each neighbor.
A less restrictive filter has precedence over a stricter one. For example, a filter accepting some prefixes has precedence over a filter not accepting any, and a filter accepting all prefixes has precedence over one that accepts some.
27.9. MetalLB logging, troubleshooting, and support
To diagnose and resolve MetalLB configuration issues, refer to this list of commonly used commands. By using these commands, you can verify network connectivity and inspect service states to ensure efficient error recovery.
27.9.1. Setting the MetalLB logging levels
To manage log verbosity for the FRRouting (FRR) container, configure the logLevel specification. By adjusting this setting, you can reduce log volume from the default info level or increase detail for troubleshooting MetalLB configuration issues.
Gain a deeper insight into MetalLB by setting the logLevel to debug.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole. -
You have installed the OpenShift CLI (
oc).
Procedure
Create a file, such as
setdebugloglevel.yaml, with content like the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration by entering the following command:
oc replace -f setdebugloglevel.yaml
$ oc replace -f setdebugloglevel.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteUse the
oc replacecommand because themetallbCR was already created and you need to change only the log level.Display the names of the
speakerpods:oc get -n metallb-system pods -l component=speaker
$ oc get -n metallb-system pods -l component=speakerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME READY STATUS RESTARTS AGE speaker-2m9pm 4/4 Running 0 9m19s speaker-7m4qw 3/4 Running 0 19s speaker-szlmx 4/4 Running 0 9m19s
NAME READY STATUS RESTARTS AGE speaker-2m9pm 4/4 Running 0 9m19s speaker-7m4qw 3/4 Running 0 19s speaker-szlmx 4/4 Running 0 9m19sCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSpeaker and controller pods are recreated to ensure the updated logging level is applied. The logging level is modified for all the components of MetalLB.
View the
speakerlogs:oc logs -n metallb-system speaker-7m4qw -c speaker
$ oc logs -n metallb-system speaker-7m4qw -c speakerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the FRR logs:
oc logs -n metallb-system speaker-7m4qw -c frr
$ oc logs -n metallb-system speaker-7m4qw -c frrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
27.9.1.1. FRRouting (FRR) log levels
To control the verbosity of network logs for troubleshooting or monitoring, refer to the FRRouting (FRR) logging levels.
The following values define the severity of recorded events, so that you can use them to filter output based on operational requirements:
| Log level | Description |
|---|---|
|
| Supplies all logging information for all logging levels. |
|
|
Information that is diagnostically helpful to people. Set to |
|
| Provides information that always should be logged but under normal circumstances does not require user intervention. This is the default logging level. |
|
|
Anything that can potentially cause inconsistent |
|
|
Any error that is fatal to the functioning of |
|
| Turn off all logging. |
27.9.2. Troubleshooting BGP issues
To diagnose and resolve BGP configuration issues, execute commands directly within the FRR container. By accessing the container, you can verify routing states and identify connectivity errors.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole. -
You have installed the OpenShift CLI (
oc).
Procedure
Display the names of the
speakerpods:oc get -n metallb-system pods -l component=speaker
$ oc get -n metallb-system pods -l component=speakerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME READY STATUS RESTARTS AGE speaker-66bth 4/4 Running 0 56m speaker-gvfnf 4/4 Running 0 56m ...
NAME READY STATUS RESTARTS AGE speaker-66bth 4/4 Running 0 56m speaker-gvfnf 4/4 Running 0 56m ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the running configuration for FRR:
oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show running-config"
$ oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show running-config"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
router bgp 64500-
Specifies the
router bgpthat indicates the ASN for MetalLB. neighbor 10.0.2.3 remote-as 64500-
Specifies that a
neighbor <ip-address> remote-as <peer-ASN>line exists for each BGP peer custom resource that you added. bfd profile doc-example-bfd-profile-full- Specifies that the BFD profile is associated with the correct BGP peer and that the BFD profile shows in the command output.
network 203.0.113.200/30-
Specifies that the
network <ip-address-range>lines match the IP address ranges that you specified in address pool custom resources
Display the BGP summary:
oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show bgp summary"
$ oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show bgp summary"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
10.0.2.3- Specifies that the output includes a line for each BGP peer custom resource that you added.
10.0.2.4-
Specifies that the output shows
0messages received and0messages sent, which indicates a BGP peer that does not have a BGP session. Check network connectivity and the BGP configuration of the BGP peer.
Display the BGP peers that received an address pool:
oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show bgp ipv4 unicast 203.0.113.200/30"
$ oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show bgp ipv4 unicast 203.0.113.200/30"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
ipv4withipv6to display the BGP peers that received an IPv6 address pool. Replace203.0.113.200/30with an IPv4 or IPv6 IP address range from an address pool.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
10.0.2.3- Specifies that the output includes an IP address for a BGP peer.
27.9.3. Troubleshooting BFD issues
To diagnose and resolve Bidirectional Forwarding Detection (BFD) issues, execute commands directly within the FRRouting (FRR) container. By accessing the container, you can verify that BFD peers are correctly configured with established BGP sessions.
The BFD implementation that Red Hat supports uses FRRouting (FRR) in a container that exists in a speaker pod.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole. -
You have installed the OpenShift CLI (
oc).
Procedure
Display the names of the
speakerpods:oc get -n metallb-system pods -l component=speaker
$ oc get -n metallb-system pods -l component=speakerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME READY STATUS RESTARTS AGE speaker-66bth 4/4 Running 0 26m speaker-gvfnf 4/4 Running 0 26m ...
NAME READY STATUS RESTARTS AGE speaker-66bth 4/4 Running 0 26m speaker-gvfnf 4/4 Running 0 26m ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display the BFD peers:
oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show bfd peers brief"
$ oc exec -n metallb-system speaker-66bth -c frr -- vtysh -c "show bfd peers brief"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Session count: 2 SessionId LocalAddress PeerAddress Status ========= ============ =========== ====== 3909139637 10.0.1.2 10.0.2.3 up
Session count: 2 SessionId LocalAddress PeerAddress Status ========= ============ =========== ====== 3909139637 10.0.1.2 10.0.2.3 upCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
up-
Specifies that the
PeerAddresscolumn includes each BFD peer. If the output does not list a BFD peer IP address that you expected the output to include, troubleshoot BGP connectivity with the peer. If the status field indicatesdown, check for connectivity on the links and equipment between the node and the peer. You can determine the node name for the speaker pod with a command likeoc get pods -n metallb-system speaker-66bth -o jsonpath='{.spec.nodeName}'.
27.9.4. MetalLB metrics for BGP and BFD
To monitor network connectivity and diagnose routing states, refer to the Prometheus metrics for MetalLB. These metrics provide visibility into the status of BGP peers and BFD profiles so that you can ensure stable external communication.
| Name | Description |
|---|---|
|
| Counts the number of BFD control packets received from each BFD peer. |
|
| Counts the number of BFD control packets sent to each BFD peer. |
|
| Counts the number of BFD echo packets received from each BFD peer. |
|
| Counts the number of BFD echo packets sent to each BFD. |
|
|
Counts the number of times the BFD session with a peer entered the |
|
|
Indicates the connection state with a BFD peer. |
|
|
Counts the number of times the BFD session with a peer entered the |
|
| Counts the number of BFD Zebra notifications for each BFD peer. |
| Name | Description |
|---|---|
|
| Counts the number of load balancer IP address prefixes that are advertised to BGP peers. The terms prefix and aggregated route have the same meaning. |
|
|
Indicates the connection state with a BGP peer. |
|
| Counts the number of BGP update messages sent to each BGP peer. |
|
| Counts the number of BGP open messages sent to each BGP peer. |
|
| Counts the number of BGP open messages received from each BGP peer. |
|
| Counts the number of BGP notification messages sent to each BGP peer. |
|
| Counts the number of BGP update messages received from each BGP peer. |
|
| Counts the number of BGP keepalive messages sent to each BGP peer. |
|
| Counts the number of BGP keepalive messages received from each BGP peer. |
|
| Counts the number of BGP route refresh messages sent to each BGP peer. |
|
| Counts the number of total BGP messages sent to each BGP peer. |
|
| Counts the number of total BGP messages received from each BGP peer. |
Additional resources
27.9.5. About collecting MetalLB data
To collect diagnostic data for debugging or support analysis, execute the oc adm must-gather CLI command. This utility captures essential information regarding the cluster, the MetalLB configuration, and the MetalLB Operator state.
The following list details features and objects related to MetalLB and the MetalLB Operator:
- The namespace and child objects where you deploy the MetalLB Operator
- All MetalLB Operator custom resource definitions (CRDs)
The command collects the following information from FRRouting (FRR), which Red Hat uses to implement BGP and BFD:
-
/etc/frr/frr.conf -
/etc/frr/frr.log -
/etc/frr/daemonsconfiguration file -
/etc/frr/vtysh.conf
The command collects log and configuration files from the frr container that exists in each speaker pod. Additionally, the command collects the output from the following vtysh commands:
-
show running-config -
show bgp ipv4 -
show bgp ipv6 -
show bgp neighbor -
show bfd peer
No additional configuration is required when you run the command.
Additional resources