Chapter 17. Multiple networks
17.1. Understanding multiple networks
OpenShift Container Platform administrators and users can use user-defined networks (UDNs) or NetworkAttachmentDefinition (NADs) to define the networks that handle all of the ordinary network traffic of the cluster.
17.1.1. About using multiple networks with the OVN-K CNI
You can define more than one additional network for your cluster. This gives you flexibility when you configure pods that deliver network functionality, such as switching or routing.
By default, OVN-Kubernetes serves as the Container Network Interface (CNI) of an OpenShift Container Platform cluster. This network interface is what administrators use to create default networks. During cluster installation, you configure your default pod network. The default network handles all ordinary network traffic for the cluster.
OpenShift Container Platform uses the Multus CNI plugin to allow chaining of CNI plugins. You can define an additional network based on the available CNI plugins and attach one or more of these networks to your pods.
17.1.2. Usage scenarios for an additional network
You can use an additional network in situations where you require network isolation, including for data plane and control plane separation.
Isolating network traffic is useful for the following performance and security reasons:
- Performance
- You can send traffic on two different planes to manage how much traffic is along each plane.
- Security
- You can send sensitive traffic onto a network plane that is managed specifically for security considerations, and you can separate private data that must not be shared between tenants or customers.
All of the pods in the cluster still use the cluster-wide default network to maintain connectivity across the cluster. Every pod has an eth0 interface that is attached to the cluster-wide pod network. You can view the interfaces for a pod by using the oc exec -it <pod_name> -- ip a command. If you add additional network interfaces that use Multus CNI, they are named net1, net2, …, netN.
To attach additional network interfaces to a pod, you must create configurations that define how the interfaces are attached. You specify each interface by using a NetworkAttachmentDefinition custom resource (CR). A CNI configuration inside each of these CRs defines how that interface is created.
17.2. Additional networks in OpenShift Container Platform
You can use the following Container Network Interface (CNI) plugins for creating additional networks in your OpenShift Container Platform cluster.
- bridge: Configure a bridge-based additional network to allow pods on the same host to communicate with each other and the host.
- bond-cni: Configure a Bond CNI secondary network to provide a method for aggregating multiple network interfaces into a single logical bonded interface.
- host-device: Configure a host-device additional network to allow pods access to a physical Ethernet network device on the host system.
- ipvlan: Configure an ipvlan-based additional network to allow pods on a host to communicate with other hosts and pods on those hosts, similar to a macvlan-based additional network. Unlike a macvlan-based additional network, each pod shares the same MAC address as the parent physical network interface.
- vlan: Configure a vlan-based additional network to allow VLAN-based network isolation and connectivity for pods.
- macvlan: Configure a macvlan-based additional network to allow pods on a host to communicate with other hosts and pods on those hosts by using a physical network interface. Each pod that is attached to a macvlan-based additional network is provided a unique MAC address.
- TAP: Configure a tap-based additional network to create a tap device inside the container namespace. A tap device enables user space programs to send and receive network packets.
- SR-IOV: Configure an SR-IOV based additional network to allow pods to attach to a virtual function (VF) interface on SR-IOV capable hardware on the host system.
-
route-override: Configure a
route-overridebased additional network to allow pods to override and set routes.
17.3. Configuring an additional network
Cluster administrators can configure an additional network based upon their infrastructure doing so provides more granular control of your network deployment.
The following network types are supported:
- Bridge
- Host device
- Bond CNI
- VLAN
- IPVLAN
- MACVLAN
- TAP
- OVN-Kubernetes
- Route-override
17.3.1. Configuration for a bridge additional network
The bridge CNI plugin JSON configuration object describes the configuration parameters for the Bridge CNI plugin. The following table details these parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The CNI specification version. The |
|
|
|
The value for the |
|
|
|
The name of the CNI plugin to configure: |
|
|
| The configuration object for the IPAM CNI plugin. The plugin manages IP address assignment for the attachment definition. |
|
|
|
Optional: Specify the name of the virtual bridge to use. If the bridge interface does not exist on the host, the bridge interface gets created. The default value is |
|
|
|
Optional: Set to |
|
|
|
Optional: Set to |
|
|
|
Optional: Set to |
|
|
|
Optional: Set to |
|
|
|
Optional: Set to |
|
|
|
Optional: Set to |
|
|
| Optional: Specify a virtual LAN (VLAN) tag as an integer value. By default, no VLAN tag is assigned. |
|
|
|
Optional: Indicates whether the default vlan must be preserved on the |
|
|
|
Optional: Assign a VLAN trunk tag. The default value is |
|
|
| Optional: Set the maximum transmission unit (MTU) to the specified value. The default value is automatically set by the kernel. |
|
|
|
Optional: Enables duplicate address detection for the container side |
|
|
|
Optional: Enables mac spoof check, limiting the traffic originating from the container to the mac address of the interface. The default value is |
The VLAN parameter configures the VLAN tag on the host end of the veth and also enables the vlan_filtering feature on the bridge interface.
To configure an uplink for an L2 network, you must allow the VLAN on the uplink interface by using the following command:
bridge vlan add vid VLAN_ID dev DEV
$ bridge vlan add vid VLAN_ID dev DEV17.3.1.1. Bridge CNI plugin configuration example
The following example configures an additional network named bridge-net:
17.3.2. Configuration for a host device additional network
The host device CNI plugin JSON configuration object describes the configuration parameters for the host-device CNI plugin.
Specify your network device by setting only one of the following parameters: device,hwaddr, kernelpath, or pciBusID.
The following table details the configuration parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The CNI specification version. The |
|
|
|
The value for the |
|
|
|
The name of the CNI plugin to configure: |
|
|
|
Optional: The name of the device, such as |
|
|
| Optional: The device hardware MAC address. |
|
|
|
Optional: The Linux kernel device path, such as |
|
|
|
Optional: The PCI address of the network device, such as |
17.3.2.1. host-device configuration example
The following example configures an additional network named hostdev-net:
17.3.3. Configuration for a Bond CNI secondary network
The Bond Container Network Interface (Bond CNI) enables the aggregation of multiple network interfaces into a single logical bonded interface within a container, which enhanches network redundancy and fault tolerance. Only SR-IOV Virtual Functions (VFs) are supported for bonding with this plugin.
The following table describes the configuration parameters for the Bond CNI plugin:
| Field | Type | Description |
|---|---|---|
|
|
| Specifies the name given to this CNI network attachment definition. This name is used to identify and reference the interface within the container. |
|
|
| The CNI specification version. |
|
|
|
Specifies the name of the CNI plugin to configure: |
|
|
| Specifies the address resolution protocol (ARP) link monitoring frequency in milliseconds. This parameter defines how often the bond interface sends ARP requests to check the availability of its aggregated interfaces. |
|
|
|
Optional: Specifies the maximum transmission unit (MTU) of the bond. The default is |
|
|
|
Optional: Specifies the |
|
|
| Specifies the bonding policy. |
|
|
|
Optional: Specifies whether the network interfaces intended for bonding are expected to be created and available directly within the network namespace of the container when the bond starts. If |
|
|
| Specifies the interfaces to be bonded. |
|
|
| The configuration object for the IPAM CNI plugin. The plugin manages IP address assignment for the attachment definition. |
17.3.3.1. Bond CNI plugin configuration example
The following example configures a secondary network named bond-net1:
17.3.3.2. Configuration for a VLAN additional network
The VLAN CNI plugin JSON configuration object describes the configuration parameters for the VLAN, vlan, CNI plugin. The following table details these parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The CNI specification version. The |
|
|
|
The value for the |
|
|
|
The name of the CNI plugin to configure: |
|
|
|
The Ethernet interface to associate with the network attachment. If a |
|
|
|
Set the ID of the |
|
|
| The configuration object for the IPAM CNI plugin. The plugin manages IP address assignment for the attachment definition. |
|
|
| Optional: Set the maximum transmission unit (MTU) to the specified value. The default value is automatically set by the kernel. |
|
|
| Optional: DNS information to return. For example, a priority-ordered list of DNS nameservers. |
|
|
|
Optional: Specifies whether the |
A NetworkAttachmentDefinition custom resource definition (CRD) with a vlan configuration can be used only on a single pod in a node because the CNI plugin cannot create multiple vlan subinterfaces with the same vlanId on the same master interface.
17.3.3.2.1. VLAN configuration example
The following example demonstrates a vlan configuration with an additional network that is named vlan-net:
-
ipam.type.host-local: Allocates IPv4 and IPv6 IP addresses from a specified set of address ranges. IPAM plugin stores the IP addresses locally on the host filesystem so that the addresses remain unique to the host.
17.3.3.3. Configuration for an IPVLAN additional network
The IPVLAN CNI plugin JSON configuration object describes the configuration parameters for the IPVLAN, ipvlan, CNI plugin. The following table details these parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The CNI specification version. The |
|
|
|
The value for the |
|
|
|
The name of the CNI plugin to configure: |
|
|
| The configuration object for the IPAM CNI plugin. The plugin manages IP address assignment for the attachment definition. This is required unless the plugin is chained. |
|
|
|
Optional: The operating mode for the virtual network. The value must be |
|
|
|
Optional: The Ethernet interface to associate with the network attachment. If a |
|
|
| Optional: Set the maximum transmission unit (MTU) to the specified value. The default value is automatically set by the kernel. |
|
|
|
Optional: Specifies whether the |
-
The
ipvlanobject does not allow virtual interfaces to communicate with themasterinterface. Therefore the container is not able to reach the host by using theipvlaninterface. Be sure that the container joins a network that provides connectivity to the host, such as a network supporting the Precision Time Protocol (PTP). -
A single
masterinterface cannot simultaneously be configured to use bothmacvlanandipvlan. -
For IP allocation schemes that cannot be interface agnostic, the
ipvlanplugin can be chained with an earlier plugin that handles this logic. If themasteris omitted, then the previous result must contain a single interface name for theipvlanplugin to enslave. Ifipamis omitted, then the previous result is used to configure theipvlaninterface.
17.3.3.3.1. IPVLAN CNI plugin configuration example
The following example configures an additional network named ipvlan-net:
17.3.3.4. Configuration for a MACVLAN additional network
The MACVLAN CNI plugin JSON configuration object describes the configuration parameters for the MAC Virtual LAN (MACVLAN) Container Network Interface (CNI) plugin. The following table describes these parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The CNI specification version. The |
|
|
|
The value for the |
|
|
|
The name of the CNI plugin to configure: |
|
|
| The configuration object for the IPAM CNI plugin. The plugin manages IP address assignment for the attachment definition. |
|
|
|
Optional: Configures traffic visibility on the virtual network. Must be either |
|
|
| Optional: The host network interface to associate with the newly created macvlan interface. If a value is not specified, then the default route interface is used. |
|
|
| Optional: The maximum transmission unit (MTU) to the specified value. The default value is automatically set by the kernel. |
|
|
|
Optional: Specifies whether the |
If you specify the master key for the plugin configuration, use a different physical network interface than the one that is associated with your primary network plugin to avoid possible conflicts.
17.3.3.4.1. MACVLAN CNI plugin configuration example
The following example configures an additional network named macvlan-net:
17.3.3.5. Configuration for a TAP additional network
The TAP CNI plugin JSON configuration object describes the configuration parameters for the TAP CNI plugin. The following table describes these parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The CNI specification version. The |
|
|
|
The value for the |
|
|
|
The name of the CNI plugin to configure: |
|
|
| Optional: Request the specified MAC address for the interface. |
|
|
| Optional: Set the maximum transmission unit (MTU) to the specified value. The default value is automatically set by the kernel. |
|
|
| Optional: The SELinux context to associate with the tap device. Note
The value |
|
|
|
Optional: Set to |
|
|
| Optional: The user owning the tap device. |
|
|
| Optional: The group owning the tap device. |
|
|
| Optional: Set the tap device as a port of an already existing bridge. |
17.3.3.5.1. Tap configuration example
The following example configures an additional network named mynet:
17.3.3.6. Configuring routes using the route-override plugin on an additional network
The Route override CNI plugin JSON configuration object describes the configuration parameters for the route-override CNI plugin. The following table details these parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNI plugin to configure: |
|
|
|
Optional: Set to |
|
|
|
Optional: Set to |
|
|
| Optional: Specify the list of routes to delete from the container namespace. |
|
|
|
Optional: Specify the list of routes to add to the container namespace. Each route is a dictionary with |
|
|
|
Optional: Set this to |
17.3.3.6.1. Route-override plugin configuration example
The route-override CNI is a type of CNI that is designed to be used when chained with a parent CNI. The CNI type does not operate independently, but relies on the parent CNI to first create the network interface and assign IP addresses before the CNI type can modify the routing rules.
The following example configures a secondary network named mymacvlan. The parent CNI creates a network interface attached to eth1 and assigns an IP address in the 192.168.1.0/24 range by using host-local IPAM. The route-override CNI is then chained to the parent CNI and modifies the routing rules by flushing existing routes, deleting the route to 192.168.0.0/24, and adding a new route for 192.168.0.0/24 with a custom gateway.
where:
"type": "macvlan"-
The parent CNI creates a network interface attached to
eth1. "type": "route-override"-
The chained
route-overrideCNI modifies the routing rules.
17.3.3.7. Configuration for a layer 2 switched topology
The switched (layer 2) topology networks interconnect the workloads through a cluster-wide logical switch. This configuration can be used for IPv6 and dual-stack deployments.
Layer 2 switched topology networks only allow for the transfer of data packets between pods within a cluster.
The following JSON example configures a switched secondary network:
17.3.4. Configuration of IP address assignment for a network attachment
For secondary networks, you can assign IP addresses by using an IP Address Management (IPAM) CNI plugin, which supports various assignment methods, including Dynamic Host Configuration Protocol (DHCP) and static assignment.
You can use the following IP address assignment types:
- Static assignment.
- Dynamic assignment through a DHCP server. The DHCP server you specify must be reachable from the additional network.
- Dynamic assignment through the Whereabouts IPAM CNI plugin.
17.3.4.1. Static IP address assignment configuration
The following table describes the configuration for static IP address assignment:
| Field | Type | Description |
|---|---|---|
|
|
|
The IPAM address type. The value |
|
|
| An array of objects specifying IP addresses to assign to the virtual interface. Both IPv4 and IPv6 IP addresses are supported. |
|
|
| An array of objects specifying routes to configure inside the pod. |
|
|
| Optional: An array of objects specifying the DNS configuration. |
The addresses array requires objects with the following fields:
| Field | Type | Description |
|---|---|---|
|
|
|
An IP address and network prefix that you specify. For example, if you specify |
|
|
| The default gateway to route egress network traffic to. |
| Field | Type | Description |
|---|---|---|
|
|
|
The IP address range in CIDR format, such as |
|
|
| The gateway that routes network traffic. |
| Field | Type | Description |
|---|---|---|
|
|
| An array of one or more IP addresses where DNS queries get sent. |
|
|
|
The default domain to append to a hostname. For example, if the domain is set to |
|
|
|
An array of domain names to append to an unqualified hostname, such as |
Static IP address assignment configuration example
17.3.4.2. Dynamic IP address (DHCP) assignment configuration
A pod obtains its original DHCP lease when the pod gets created. The lease must be periodically renewed by a minimal DHCP server deployment running on the cluster.
For an Ethernet network attachment, the SR-IOV Network Operator does not create a DHCP server deployment; the Cluster Network Operator is responsible for creating the minimal DHCP server deployment.
To trigger the deployment of the DHCP server, you must create a shim network attachment by editing the Cluster Network Operator configuration, as in the following example:
Example shim network attachment definition
where:
type- Specifies dynamic IP address assignment for the cluster.
The following table describes the configuration parameters for dynamic IP address address assignment with DHCP.
| Field | Type | Description |
|---|---|---|
|
|
|
The IPAM address type. The value |
The following JSON example describes the configuration p for dynamic IP address address assignment with DHCP.
Dynamic IP address (DHCP) assignment configuration example
{
"ipam": {
"type": "dhcp"
}
}
{
"ipam": {
"type": "dhcp"
}
}17.3.4.3. Dynamic IP address assignment configuration with Whereabouts
The Whereabouts CNI plugin allows the dynamic assignment of an IP address to an additional network without the use of a DHCP server.
The Whereabouts CNI plugin also supports overlapping IP address ranges and configuration of the same CIDR range multiple times within separate NetworkAttachmentDefinition CRDs. This provides greater flexibility and management capabilities in multi-tenant environments.
17.3.4.3.1. Dynamic IP address configuration objects
The following table describes the configuration objects for dynamic IP address assignment with Whereabouts:
| Field | Type | Description |
|---|---|---|
|
|
|
The IPAM address type. The value |
|
|
| An IP address and range in CIDR notation. IP addresses are assigned from within this range of addresses. |
|
|
| Optional: A list of zero or more IP addresses and ranges in CIDR notation. IP addresses within an excluded address range are not assigned. |
|
|
| Optional: Helps ensure that each group or domain of pods gets its own set of IP addresses, even if they share the same range of IP addresses. Setting this field is important for keeping networks separate and organized, notably in multi-tenant environments. |
17.3.4.3.2. Dynamic IP address assignment configuration that uses Whereabouts
The following example shows a dynamic address assignment configuration that uses Whereabouts:
Whereabouts dynamic IP address assignment
17.3.4.3.3. Dynamic IP address assignment that uses Whereabouts with overlapping IP address ranges
The following example shows a dynamic IP address assignment that uses overlapping IP address ranges for multi-tenant networks.
NetworkAttachmentDefinition 1
- 1
- Optional. If set, must match the
network_nameofNetworkAttachmentDefinition 2.
NetworkAttachmentDefinition 2
- 1
- Optional. If set, must match the
network_nameofNetworkAttachmentDefinition 1.
17.3.4.4. Creating a whereabouts-reconciler daemon set
The Whereabouts reconciler is responsible for managing dynamic IP address assignments for the pods within a cluster by using the Whereabouts IP Address Management (IPAM) solution. The Whereabouts reconciler ensures that each pod gets a unique IP address from the specified IP address range. The Whereabouts reconciler also handles IP address releases when pods are deleted or scaled down.
You can also use a NetworkAttachmentDefinition custom resource definition (CRD) for dynamic IP address assignment.
The whereabouts-reconciler daemon set is automatically created when you configure a secondary network through the Cluster Network Operator. The whereabouts-reconciler DaemonSet does not get automatically created when you configure a secondary network from a YAML manifest.
To trigger the deployment of the whereabouts-reconciler daemon set, you must manually create a whereabouts-shim network attachment by editing the Cluster Network Operator custom resource (CR) file.
Procedure
Edit the
Network.operator.openshift.ioCR by running the following command:oc edit network.operator.openshift.io cluster
$ oc edit network.operator.openshift.io clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Include the
additionalNetworkssection shown in this example YAML extract within thespecdefinition of the CR:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the file and exit the text editor.
Verify that the
whereabouts-reconcilerdaemon set deployed successfully by running the following command:oc get all -n openshift-multus | grep whereabouts-reconciler
$ oc get all -n openshift-multus | grep whereabouts-reconcilerCopy to Clipboard Copied! Toggle word wrap Toggle overflow pod/whereabouts-reconciler-jnp6g 1/1 Running 0 6s pod/whereabouts-reconciler-k76gg 1/1 Running 0 6s daemonset.apps/whereabouts-reconciler 6 6 6 6 6 kubernetes.io/os=linux 6s
pod/whereabouts-reconciler-jnp6g 1/1 Running 0 6s pod/whereabouts-reconciler-k76gg 1/1 Running 0 6s daemonset.apps/whereabouts-reconciler 6 6 6 6 6 kubernetes.io/os=linux 6sCopy to Clipboard Copied! Toggle word wrap Toggle overflow
17.3.4.5. Configuring the Whereabouts IP reconciler schedule
The Whereabouts IPAM CNI plugin runs the IP address reconciler daily. This process cleans up any stranded IP address allocations that might result in exhausting IP addresses and therefore prevent new pods from getting a stranded IP address allocated to them.
Use this procedure to change the frequency at which the IP reconciler runs.
Prerequisites
-
You installed the OpenShift CLI (
oc). -
You have access to the cluster as a user with the
cluster-adminrole. -
You have deployed the
whereabouts-reconcilerdaemon set, and thewhereabouts-reconcilerpods are up and running.
Procedure
Run the following command to create a
ConfigMapobject namedwhereabouts-configin theopenshift-multusnamespace with a specific cron expression for the IP reconciler:oc create configmap whereabouts-config -n openshift-multus --from-literal=reconciler_cron_expression="*/15 * * * *"
$ oc create configmap whereabouts-config -n openshift-multus --from-literal=reconciler_cron_expression="*/15 * * * *"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This cron expression indicates the IP reconciler runs every 15 minutes. Adjust the expression based on your specific requirements.
NoteThe
whereabouts-reconcilerdaemon set can only consume a cron expression pattern that includes five asterisks. Red Hat does not support the sixth asterisk, which is used to denote seconds.Retrieve information about resources related to the
whereabouts-reconcilerdaemon set and pods within theopenshift-multusnamespace by running the following command:oc get all -n openshift-multus | grep whereabouts-reconciler
$ oc get all -n openshift-multus | grep whereabouts-reconcilerCopy to Clipboard Copied! Toggle word wrap Toggle overflow pod/whereabouts-reconciler-2p7hw 1/1 Running 0 4m14s pod/whereabouts-reconciler-76jk7 1/1 Running 0 4m14s daemonset.apps/whereabouts-reconciler 6 6 6 6 6 kubernetes.io/os=linux 4m16s
pod/whereabouts-reconciler-2p7hw 1/1 Running 0 4m14s pod/whereabouts-reconciler-76jk7 1/1 Running 0 4m14s daemonset.apps/whereabouts-reconciler 6 6 6 6 6 kubernetes.io/os=linux 4m16sCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to verify that the
whereabouts-reconcilerpod runs the IP reconciler with the configured interval:oc -n openshift-multus logs whereabouts-reconciler-2p7hw
$ oc -n openshift-multus logs whereabouts-reconciler-2p7hwCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.3.4.6. Creating a configuration for assignment of dual-stack IP addresses dynamically
You can dynamically assign dual-stack IP addresses to a secondary network so that pods can communicate over both IPv4 and IPv6 addresses.
You can configure the following IP address assignment types in the ipRanges parameter:
- IPv4 addresses
- IPv6 addresses
- multiple IP address assignment
Procedure
-
Set
typetowhereabouts. Use
ipRangesto allocate IP addresses as shown in the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Attach the secondary network to a pod. For more information, see "Adding a pod to a secondary network".
Verification
Verify that all IP addresses got assigned to the network interfaces within the network namespace of a pod by entering the following command:
$ oc exec -it <pod_name> -- ip a
$ oc exec -it <pod_name> -- ip aCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<podname>- The name of the pod.
17.3.5. About configuring the master interface in the container network namespace
You can create a MAC-VLAN, an IP-VLAN, or a VLAN subinterface that is based on a master interface that exists in a container namespace. You can also create a master interface as part of the pod network configuration in a separate network attachment definition CRD.
To use a container namespace master interface, you must specify true for the linkInContainer parameter that exists in the subinterface configuration of the NetworkAttachmentDefinition CRD.
17.3.5.1. Creating multiple VLANs on SR-IOV VFs
You can create multiple VLANs based on SR-IOV VFs. For this configuration, create an SR-IOV network and then define the network attachments for the VLAN interfaces.
The following diagram shows the setup process for creating multiple VLANs on SR-IOV VFs.
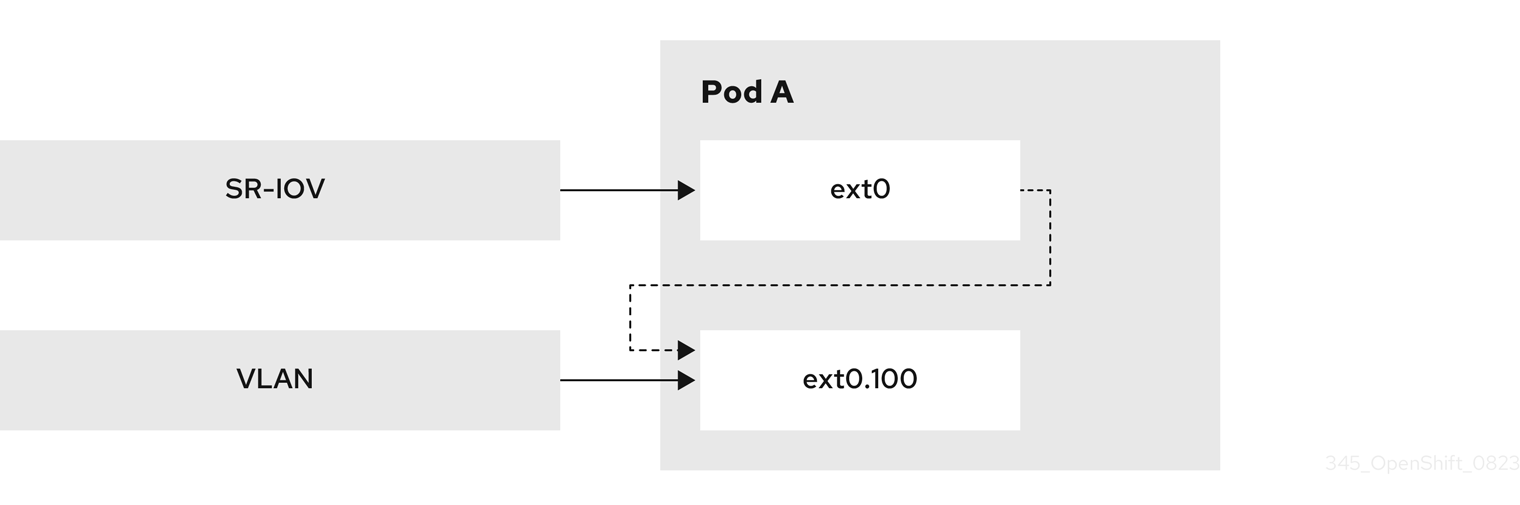
Prerequisites
-
You installed the OpenShift CLI (
oc). -
You have access to the cluster as a user with the
cluster-adminrole. - You have installed the SR-IOV Network Operator.
Procedure
Create a dedicated container namespace where you want to deploy your pod by using the following command:
oc new-project test-namespace
$ oc new-project test-namespaceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create an SR-IOV node policy.
Create an
SriovNetworkNodePolicyobject, and then save the YAML in thesriov-node-network-policy.yamlfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
vendor-
The vendor hexadecimal code of the SR-IOV network device. The value
15b3associates with a Mellanox NIC. deviceIDThe device hexadecimal code of the SR-IOV network device.
NoteThe SR-IOV network node policy configuration example, with the setting
deviceType: netdevice, is tailored specifically for Mellanox Network Interface Cards (NICs).
Apply the YAML configuration by running the following command:
oc apply -f sriov-node-network-policy.yaml
$ oc apply -f sriov-node-network-policy.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteApplying the YAML configuration might take time because of a node reboot operation.
Create an SR-IOV network:
Create the
SriovNetworkcustom resource (CR) for the additional secondary SR-IOV network attachment as demonstrated in the following example CR. Save the YAML as asriov-network-attachment.yamlfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the YAML by running the following command:
oc apply -f sriov-network-attachment.yaml
$ oc apply -f sriov-network-attachment.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create the VLAN secondary network.
Using the following YAML example, create a file named
vlan100-additional-network-configuration.yaml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
master-
The VLAN configuration needs to specify the
mastername. You can specify the name in the networks annotation of a pod. linkInContainer-
The
linkInContainerparameter must be specified.
Apply the YAML file by running the following command:
oc apply -f vlan100-additional-network-configuration.yaml
$ oc apply -f vlan100-additional-network-configuration.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a pod definition by using the earlier specified networks.
Using the following YAML configuration example, create a file named
pod-a.yamlfile:NoteThe manifest example includes the following resources:
- Namespace with security labels
- Pod definition with appropriate network annotation
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
interface-
The name to be used as the
masterinterface for the VLAN interface.
Apply the YAML file by running the following command:
oc apply -f pod-a.yaml
$ oc apply -f pod-a.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Get detailed information about the
nginx-podwithin thetest-namespaceby running the following command:oc describe pods nginx-pod -n test-namespace
$ oc describe pods nginx-pod -n test-namespaceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.3.5.2. Creating a subinterface based on a bridge master interface in a container namespace
You can create a subinterface based on a bridge master interface that exists in a container namespace. Creating a subinterface can be applied to other types of interfaces.
Prerequisites
-
You have installed the OpenShift CLI (
oc). -
You are logged in to the OpenShift Container Platform cluster as a user with
cluster-adminprivileges.
Procedure
Create a dedicated container namespace where you want to deploy your pod by entering the following command:
oc new-project test-namespace
$ oc new-project test-namespaceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Using the following YAML configuration example, create a bridge
NetworkAttachmentDefinitioncustom resource definition (CRD) file namedbridge-nad.yaml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to apply the
NetworkAttachmentDefinitionCRD to your OpenShift Container Platform cluster:oc apply -f bridge-nad.yaml
$ oc apply -f bridge-nad.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that you successfully created a
NetworkAttachmentDefinitionCRD by entering the following command. The expected output shows the name of the NAD CRD and the creation age in minutes.oc get network-attachment-definitions
$ oc get network-attachment-definitionsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Using the following YAML example, create a file named
ipvlan-additional-network-configuration.yamlfor the IPVLAN secondary network configuration:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
master- Specifies the ethernet interface to associate with the network attachment. The ethernet interface is subsequently configured in the pod networks annotation.
linkInContainer-
Specifies that the
masterinterface exists in the container network namespace.
Apply the YAML file by running the following command:
oc apply -f ipvlan-additional-network-configuration.yaml
$ oc apply -f ipvlan-additional-network-configuration.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the
NetworkAttachmentDefinitionCRD has been created successfully by running the following command. The expected output shows the name of the NAD CRD and the creation age in minutes.oc get network-attachment-definitions
$ oc get network-attachment-definitionsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Using the following YAML configuration example, create a file named
pod-a.yamlfor the pod definition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
k8s.v1.cni.cncf.io/networks,interface-
Specifies the name to be used as the
masterfor the IPVLAN interface.
Apply the YAML file by running the following command:
oc apply -f pod-a.yaml
$ oc apply -f pod-a.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Verify that the pod is running by using the following command:
oc get pod -n test-namespace
$ oc get pod -n test-namespaceCopy to Clipboard Copied! Toggle word wrap Toggle overflow NAME READY STATUS RESTARTS AGE pod-a 1/1 Running 0 2m36s
NAME READY STATUS RESTARTS AGE pod-a 1/1 Running 0 2m36sCopy to Clipboard Copied! Toggle word wrap Toggle overflow Show network interface information about the
pod-aresource within thetest-namespaceby running the following command:oc exec -n test-namespace pod-a -- ip a
$ oc exec -n test-namespace pod-a -- ip aCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow This output shows that the network interface
net2associates with the physical interfacenet1.
17.4. Creating additional networks
You can manage additional networks in your OpenShift cluster by creating, editing, viewing, and deleting them as needed. You can extend the networking capabilities of your cluster beyond the default primary network by configuring additional networks.
17.4.1. Configuration for a primary network attachment
You configure a primary network by using the NetworkAttachmentDefinition API in the k8s.cni.cncf.io API group.
The configuration for the API is described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
| The name for the primary network. |
|
|
| The namespace that the object is associated with. |
|
|
| The CNI plugin configuration in JSON format. |
17.4.2. Approaches to managing an additional network
You can manage the life cycle of a primary network created by a NAD CR through the Cluster Network Operator (CNO) or a YAML manifest. Using the CNO provides automated management of the network resource, while applying a YAML manifest allows for direct control over the network configuration.
- Modifying the Cluster Network Operator (CNO) configuration
-
With this method, the CNO automatically creates and manages the
NetworkAttachmentDefinitionobject. In addition to managing the object lifecycle, the CNO ensures that a DHCP is available for a primary network that uses a DHCP assigned IP address. - Applying a YAML manifest
-
With this method, you can manage the primary network directly by creating an
NetworkAttachmentDefinitionobject. This approach allows for the invocation of multiple CNI plugins in order to attach primary network interfaces in a pod.
Each approach is mutually exclusive and you can only use one approach for managing a primary network at a time. For either approach, the primary network is managed by a Container Network Interface (CNI) plugin that you configure.
When deploying OpenShift Container Platform nodes with multiple network interfaces on Red Hat OpenStack Platform (RHOSP) with OVN SDN, DNS configuration of the secondary interface might take precedence over the DNS configuration of the primary interface. In this case, remove the DNS nameservers for the subnet ID that is attached to the secondary interface by running the following command:
openstack subnet set --dns-nameserver 0.0.0.0 <subnet_id>
$ openstack subnet set --dns-nameserver 0.0.0.0 <subnet_id>17.4.3. Creating an additional network attachment with the Cluster Network Operator
When you specify a primary network to create by using the Cluster Network Operator (CNO), the (CNO) creates the NetworkAttachmentDefinition custom resource definition (CRD) automatically and manages it.
The Cluster Network Operator (CNO) manages additional network definitions. When you specify a primary network to create, the CNO creates the NetworkAttachmentDefinition custom resource definition (CRD) automatically.
Do not edit the NetworkAttachmentDefinition CRDs that the Cluster Network Operator manages. Doing so might disrupt network traffic on your additional network.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Optional: Create the namespace for the additional networks:
oc create namespace <namespace_name>
$ oc create namespace <namespace_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To edit the CNO configuration, enter the following command:
oc edit networks.operator.openshift.io cluster
$ oc edit networks.operator.openshift.io clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Modify the CR that you are creating by adding the configuration for the additional network that you are creating, as in the following example CR.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save your changes and quit the text editor to commit your changes.
Verification
Confirm that the CNO created the
NetworkAttachmentDefinitionCRD by running the following command. A delay might exist before the CNO creates the CRD. The expected output shows the name of the NAD CRD and the creation age in minutes.oc get network-attachment-definitions -n <namespace>
$ oc get network-attachment-definitions -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<namespace>- Specifies the namespace for the network attachment that you added to the CNO configuration.
17.4.4. Creating an additional network attachment by applying a YAML manifest
Create a primary network attachment by directly applying a NetworkAttachmentDefinition YAML manifest. This gives you full control over the network configuration without relying on the Cluster Network Operator to manage the resource automatically.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Create a YAML file with your additional network configuration, such as in the following example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To create the additional network, enter the following command:
oc apply -f <file>.yaml
$ oc apply -f <file>.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<file>- Specifies the name of the file contained the YAML manifest.
17.4.5. IP address assignment for additional networks
For additional networks, you can assign IP addresses by using an IP Address Management (IPAM) CNI plugin, which supports various assignment methods, including Dynamic Host Configuration Protocol (DHCP) and static assignment.
The DHCP IPAM CNI plugin responsible for dynamic assignment of IP addresses operates with two distinct components:
- CNI Plugin: Responsible for integrating with the Kubernetes networking stack to request and release IP addresses.
- DHCP IPAM CNI Daemon: A listener for DHCP events that coordinates with existing DHCP servers in the environment to handle IP address assignment requests. This daemon is not a DHCP server itself.
For networks requiring type: dhcp in their IPAM configuration, ensure the following:
- A DHCP server is available and running in the environment. The DHCP server is external to the cluster and is expected to be part of the customer’s existing network infrastructure.
- The DHCP server is appropriately configured to serve IP addresses to the nodes.
In cases where a DHCP server is unavailable in the environment, it is recommended to use the Whereabouts IPAM CNI plugin instead. The Whereabouts CNI provides similar IP address management capabilities without the need for an external DHCP server.
Use the Whereabouts CNI plugin when there is no external DHCP server or where static IP address management is preferred. The Whereabouts plugin includes a reconciler daemon to manage stale IP address allocations.
A DHCP lease must be periodically renewed throughout the container’s lifetime, so a separate daemon, the DHCP IPAM CNI Daemon, is required. To deploy the DHCP IPAM CNI daemon, modify the Cluster Network Operator (CNO) configuration to trigger the deployment of this daemon as part of the additional network setup.
17.4.6. Configuration for an OVN-Kubernetes additional network
The Red Hat OpenShift Networking OVN-Kubernetes network plugin allows the configuration of secondary network interfaces for pods. To configure secondary network interfaces, you must define the configurations in the NetworkAttachmentDefinition custom resource definition (CRD).
Pod and multi-network policy creation might remain in a pending state until the OVN-Kubernetes control plane agent in the nodes processes the associated network-attachment-definition CRD.
You must install the NMState Operator before using the OVN-Kubernetes network plugin to configure secondary network interfaces.
You can configure an OVN-Kubernetes additional network in either layer 2 or localnet topologies.
- A layer 2 topology supports east-west cluster traffic, but does not allow access to the underlying physical network.
- A localnet topology allows connections to the physical network, but requires additional configuration of the underlying Open vSwitch (OVS) bridge on cluster nodes.
The following sections provide example configurations for each of the topologies that OVN-Kubernetes currently allows for secondary networks.
Networks names must be unique. For example, creating multiple NetworkAttachmentDefinition CRDs with different configurations that reference the same network is unsupported.
17.4.6.1. Supported platforms for OVN-Kubernetes additional network
You can use an OVN-Kubernetes additional network with the following supported platforms:
- Bare metal
- IBM Power®
- IBM Z®
- IBM® LinuxONE
- VMware vSphere
- Red Hat OpenStack Platform (RHOSP)
17.4.6.2. OVN-Kubernetes network plugin JSON configuration table
The OVN-Kubernetes network plugin JSON configuration object describes the configuration parameters for the OVN-Kubernetes CNI network plugin. The following table details these parameters:
| Field | Type | Description |
|---|---|---|
|
|
|
The CNI specification version. The required value is |
|
|
|
The name of the network. These networks are not namespaced. For example, a network named |
|
|
|
The name of the CNI plugin to configure. This value must be set to |
|
|
|
The topological configuration for the network. Must be one of |
|
|
| The subnet to use for the network across the cluster.
For When omitted, the logical switch implementing the network only provides layer 2 communication, and users must configure IP addresses for the pods. Port security only prevents MAC spoofing. |
|
|
| The maximum transmission unit (MTU). If you do not set a value, the Cluster Network Operator (CNO) sets a default MTU value by calculating the difference among the underlay MTU of the primary network interface, the overlay MTU of the pod network, such as the Geneve (Generic Network Virtualization Encapsulation), and byte capacity of any enabled features, such as IPsec. |
|
|
|
The metadata |
|
|
| A comma-separated list of CIDRs and IP addresses. IP addresses are removed from the assignable IP address pool and are never passed to the pods. |
|
|
|
If topology is set to |
17.4.6.3. Compatibility with multi-network policy
When defining a network policy, the network policy rules that can be used depend on whether the OVN-Kubernetes secondary network defines the subnets field.
The multi-network policy API, which is provided by the MultiNetworkPolicy custom resource definition (CRD) in the k8s.cni.cncf.io API group, is compatible with an OVN-Kubernetes secondary network.
Refer to the following table that details supported multi-network policy selectors that are based on a subnets CNI configuration:
subnets field specified | Allowed multi-network policy selectors |
|---|---|
| Yes |
|
| No |
|
You can use the k8s.v1.cni.cncf.io/policy-for annotation on a MultiNetworkPolicy object to point to a NetworkAttachmentDefinition (NAD) custom resource (CR). The NAD CR defines the network to which the policy applies. The following example multi-network policy that uses a pod selector is valid only if the subnets field is defined in the secondary network CNI configuration for the secondary network named blue2:
The following example uses the ipBlock network multi-network policy that is always valid for an OVN-Kubernetes secondary network:
Example multi-network policy that uses an IP block selector
17.4.6.4. Configuration for a localnet switched topology
The switched localnet topology interconnects the workloads created as Network Attachment Definitions (NADs) through a cluster-wide logical switch to a physical network.
You must map a secondary network to the OVS bridge to use it as an OVN-Kubernetes secondary network. Bridge mappings allow network traffic to reach the physical network. A bridge mapping associates a physical network name, also known as an interface label, to a bridge created with Open vSwitch (OVS).
You can create an NodeNetworkConfigurationPolicy (NNCP) object, part of the nmstate.io/v1 API group, to declaratively create the mapping. This API is provided by the NMState Operator. By using this API you can apply the bridge mapping to nodes that match your specified nodeSelector expression, such as node-role.kubernetes.io/worker: ''. With this declarative approach, the NMState Operator applies additional network configuration to all nodes specified by the node selector automatically and transparently.
When attaching an additional network, you can either use the existing br-ex bridge or create a new bridge. Which approach to use depends on your specific network infrastructure. Consider the following approaches:
-
If your nodes include only a single network interface, you must use the existing bridge. This network interface is owned and managed by OVN-Kubernetes and you must not remove it from the
br-exbridge or alter the interface configuration. If you remove or alter the network interface, your cluster network stops working correctly. - If your nodes include several network interfaces, you can attach a different network interface to a new bridge, and use that for your secondary network. This approach provides for traffic isolation from your primary cluster network.
You cannot make configuration changes to the br-ex bridge or its underlying interfaces in the NodeNetworkConfigurationPolicy (NNCP) resource as a postinstallation task. As a workaround, use a secondary network interface connected to your host or switch.
The localnet1 network is mapped to the br-ex bridge in the following sharing-a-bridge example:
+ where:
+ metadata.name:: The name for the configuration object. spec.nodeSelector.node-role.kubernetes.io/worker:: A node selector that specifies the nodes to apply the node network configuration policy to. spec.desiredState.ovn.bridge-mappings.localnet:: The name for the secondary network from which traffic is forwarded to the OVS bridge. This secondary network must match the name of the spec.config.name field of the NetworkAttachmentDefinition CRD that defines the OVN-Kubernetes secondary network. spec.desiredState.ovn.bridge-mappings.bridge:: The name of the OVS bridge on the node. This value is required only if you specify state: present. spec.desiredState.ovn.bridge-mappings.state:: The state for the mapping. Must be either present to add the bridge or absent to remove the bridge. The default value is present.
+ The following JSON example configures a localnet secondary network that is named localnet1. Note that the value for the mtu parameter must match the MTU value that was set for the secondary network interface that is mapped to the br-ex bridge interface.
In the following multiple interfaces example, the localnet2 network interface is attached to the ovs-br1 bridge. Through this attachment, the network interface is available to the OVN-Kubernetes network plugin as a secondary network.
+ where:
+ metadata.name:: Specifies the name of the configuration object. node-role.kubernetes.io/worker:: Specifies a node selector that identifies the nodes to which the node network configuration policy applies. desiredState.interfaces.name:: Specifies a new OVS bridge that operates separately from the default bridge used by OVN-Kubernetes for cluster traffic. options.mcast-snooping-enable:: Specifies whether to enable multicast snooping. When enabled, multicast snooping prevents network devices from flooding multicast traffic to all network members. By default, an OVS bridge does not enable multicast snooping. The default value is false. bridge.port.name:: Specifies the network device on the host system to associate with the new OVS bridge. ovn.bridge-mappings.localnet:: Specifies the name of the secondary network that forwards traffic to the OVS bridge. This name must match the value of the spec.config.name field in the NetworkAttachmentDefinition CRD that defines the OVN-Kubernetes secondary network. ovn.bridge-mappings.bridge:: Specifies the name of the OVS bridge on the node. The value is required only when state: present is set. ovn.bridge-mappings.state:: Specifies the state of the mapping. Valid values are present to add the bridge or absent to remove the bridge. The default value is present.
+ The following JSON example configures a localnet secondary network that is named localnet2. Note that the value for the mtu parameter must match the MTU value that was set for the eth1 secondary network interface.
17.4.6.4.1. Configuring pods for additional networks
You must specify the secondary network attachments through the k8s.v1.cni.cncf.io/networks annotation.
The following example provisions a pod with two secondary attachments, one for each of the attachment configurations presented in this guide:
17.4.6.4.2. Configuring pods with a static IP address
You can configure pods with a static IP address. The example in the procedure provisions a pod with a static IP address.
- You can only specify the IP address for a pod’s secondary network attachment for layer 2 attachments.
- Specifying a static IP address for the pod is only possible when the attachment configuration does not feature subnets.
where:
k8s.v1.cni.cncf.io/networks.name-
The name of the network. This value must be unique across all
NetworkAttachmentDefinitionCRDs. k8s.v1.cni.cncf.io/networks.mac- The MAC address to be assigned for the interface.
k8s.v1.cni.cncf.io/networks.interface- The name of the network interface to be created for the pod.
k8s.v1.cni.cncf.io/networks.ips- The IP addresses to be assigned to the network interface.
17.5. About virtual routing and forwarding
17.5.1. About virtual routing and forwarding
You can use virtual routing and forwarding (VRF) to provide multi-tenancy functionality. For example, where each tenant has its own unique routing tables and requires different default gateways.
VRF reduces the number of permissions needed by cloud-native network function (CNF), and provides increased visibility of the network topology of secondary networks. VRF devices combined with IP address rules provide the ability to create virtual routing and forwarding domains.
Processes can bind a socket to the VRF device. Packets through the binded socket use the routing table associated with the VRF device. An important feature of VRF is that it impacts only OSI model layer 3 traffic and above so L2 tools, such as LLDP, are not affected. This allows higher priority IP address rules such as policy based routing to take precedence over the VRF device rules directing specific traffic.
17.5.1.1. Benefits of secondary networks for pods for telecommunications operators
You can connect network functions to different customers' infrastructure by using the same IP address with the Container Network Interface (CNI) virtual routing and forwarding (VRF) plugin. Using the CNI VRF plugin keeps different customers isolated.
In telecommunications use cases, each CNF can potentially be connected to many different networks sharing the same address space. These secondary networks can potentially conflict with the cluster’s main network CIDR.
With the CNI VRF plugin, IP addresses are overlapped with the OpenShift Container Platform IP address space. The CNI VRF plugin also reduces the number of permissions needed by CNF and increases the visibility of the network topologies of secondary networks.
17.6. Configuring multi-network policy
As a cluster administrator, you can configure a multi-network policy for a Single-Root I/O Virtualization (SR-IOV), MAC Virtual Local Area Network (MacVLAN), or OVN-Kubernetes additional networks.
MacVLAN additional networks are fully supported. Other types of additional networks, such as IP Virtual Local Area Network (IPVLAN), are not supported.
Support for configuring multi-network policies for SR-IOV additional networks is only supported with kernel network interface controllers (NICs). SR-IOV is not supported for Data Plane Development Kit (DPDK) applications.
17.6.1. Differences between multi-network policy and network policy
Although the MultiNetworkPolicy API implements the NetworkPolicy API, ensure that you understand the following key differences between the two policies:
You must use the
MultiNetworkPolicyAPI, as demonstrated in the following example configuration:apiVersion: k8s.cni.cncf.io/v1beta1 kind: MultiNetworkPolicy # ...
apiVersion: k8s.cni.cncf.io/v1beta1 kind: MultiNetworkPolicy # ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
You must use the
multi-networkpolicyresource name when using the CLI to interact with multi-network policies. For example, you can view a multi-network policy object with theoc get multi-networkpolicy <name>command where<name>is the name of a multi-network policy. You can use the
k8s.v1.cni.cncf.io/policy-forannotation on aMultiNetworkPolicyobject to point to aNetworkAttachmentDefinition(NAD) custom resource (CR). The NAD CR defines the network to which the policy applies. The following example multi-network policy includes thek8s.v1.cni.cncf.io/policy-forannotation:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<namespace_name>- Specifies the namespace name.
<network_name>- Specifies the name of a network attachment definition.
17.6.2. Enabling multi-network policy for the cluster
As a cluster administrator, you can enable multi-network policy support on your cluster.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in to the cluster with a user with
cluster-adminprivileges.
Procedure
Create the
multinetwork-enable-patch.yamlfile with the following YAML:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the cluster to enable multi-network policy. Successful output lists the name of the policy object and the
patchedstatus.oc patch network.operator.openshift.io cluster --type=merge --patch-file=multinetwork-enable-patch.yaml
$ oc patch network.operator.openshift.io cluster --type=merge --patch-file=multinetwork-enable-patch.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
17.6.3. Supporting multi-network policies in IPv6 networks
The ICMPv6 Neighbor Discovery Protocol (NDP) is a set of messages and processes that enable devices to discover and maintain information about neighboring nodes. NDP plays a crucial role in IPv6 networks, facilitating the interaction between devices on the same link.
The Cluster Network Operator (CNO) deploys the iptables implementation of multi-network policy when the useMultiNetworkPolicy parameter is set to true.
To support multi-network policies in IPv6 networks the Cluster Network Operator deploys the following set of custom rules in every pod affected by a multi-network policy:
where:
icmpv6-type neighbor-solicitation- This rule allows incoming ICMPv6 neighbor solicitation messages, which are part of the neighbor discovery protocol (NDP). These messages help determine the link-layer addresses of neighboring nodes.
icmpv6-type neighbor-advertisement- This rule allows incoming ICMPv6 neighbor advertisement messages, which are part of NDP and provide information about the link-layer address of the sender.
icmpv6-type router-solicitation- This rule permits incoming ICMPv6 router solicitation messages. Hosts use these messages to request router configuration information.
icmpv6-type router-advertisement- This rule allows incoming ICMPv6 router advertisement messages, which give configuration information to hosts.
You cannot edit the predefined rules.
The rules collectively enable essential ICMPv6 traffic for correct network functioning, including address resolution and router communication in an IPv6 environment. With these rules in place and a multi-network policy denying traffic, applications are not expected to experience connectivity issues.
17.6.3.1. Creating a multi-network policy using the CLI
To define granular rules describing ingress or egress network traffic allowed for namespaces in your cluster, you can create a multi-network policy.
Prerequisites
-
Your cluster uses a network plugin that supports
NetworkPolicyobjects, such as the OVN-Kubernetes network plugin or the OpenShift SDN network plugin withmode: NetworkPolicyset. This mode is the default for OpenShift SDN. - You have enabled multi-network policy support for your cluster.
-
You installed the OpenShift CLI (
oc). -
You logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace that the multi-network policy applies to.
Procedure
Create a policy rule.
Create a
<policy_name>.yamlfile:touch <policy_name>.yaml
$ touch <policy_name>.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<policy_name>- Specifies the multi-network policy file name.
Define a multi-network policy in the created file. The following example denies ingress traffic from all pods in all namespaces. This is a fundamental policy, blocking all cross-pod networking other than cross-pod traffic allowed by the configuration of other Network Policies.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<network_name>Specifies the name of a network attachment definition.
The following example configuration allows ingress traffic from all pods in the same namespace:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<network_name>Specifies the name of a network attachment definition.
The following example allows ingress traffic to one pod from a particular namespace. This policy allows traffic to pods that have the
pod-alabel from pods running innamespace-y.Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<network_name>Specifies the name of a network attachment definition.
The following example configuration restricts traffic to a service. This policy when applied ensures every pod with both labels
app=bookstoreandrole=apican only be accessed by pods with labelapp=bookstore. In this example the application could be a REST API server, marked with labelsapp=bookstoreandrole=api.This example configuration addresses the following use cases:
- Restricting the traffic to a service to only the other microservices that need to use it.
Restricting the connections to a database to only permit the application using it.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<network_name>- Specifies the name of a network attachment definition.
To create the multi-network policy object, enter the following command. Successful output lists the name of the policy object and the
createdstatus.oc apply -f <policy_name>.yaml -n <namespace>
$ oc apply -f <policy_name>.yaml -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<policy_name>- Specifies the multi-network policy file name.
<namespace>- Optional parameter. If you defined the object in a different namespace than the current namespace, the parameter specifices the namespace.
Successful output lists the name of the policy object and the
createdstatus.NoteIf you log in to the web console with
cluster-adminprivileges, you have a choice of creating a network policy in any namespace in the cluster directly in YAML or from a form in the web console.
17.6.3.2. Editing a multi-network policy
To modify existing policy configurations, you can edit a multi-network policy in a namespace. Edit policies by modifying the policy file and applying it with oc apply, or by using the oc edit command directly.
If you log in with cluster-admin privileges, you can edit network policies in any namespace in the cluster. In the web console, you can edit policies directly in YAML or by using the Actions menu.
Prerequisites
-
Your cluster uses a network plugin that supports
NetworkPolicyobjects, such as the OVN-Kubernetes network plugin or the OpenShift SDN network plugin withmode: NetworkPolicyset. This mode is the default for OpenShift SDN. -
You installed the OpenShift CLI (
oc). -
You are logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace where the multi-network policy exists.
Procedure
Optional: To list the multi-network policy objects in a namespace, enter the following command:
oc get multi-network policy -n <namespace>
$ oc get multi-network policy -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<namespace>- Optional: Specifies the namespace if the object is defined in a different namespace than the current namespace.
Edit the multi-network policy object.
If you saved the multi-network policy definition in a file, edit the file and make any necessary changes, and then enter the following command.
oc apply -n <namespace> -f <policy_file>.yaml
$ oc apply -n <namespace> -f <policy_file>.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<namespace>- Optional: Specifies the namespace if the object is defined in a different namespace than the current namespace.
<policy_file>- Specifies the name of the file containing the network policy.
If you need to update the multi-network policy object directly, enter the following command:
oc edit multi-network policy <policy_name> -n <namespace>
$ oc edit multi-network policy <policy_name> -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<policy_name>- Specifies the name of the network policy.
<namespace>- Optional: Specifies the namespace if the object is defined in a different namespace than the current namespace.
Confirm that the multi-network policy object is updated.
oc describe multi-networkpolicy <policy_name> -n <namespace>
$ oc describe multi-networkpolicy <policy_name> -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<policy_name>- Specifies the name of the multi-network policy.
<namespace>- Optional: Specifies the namespace if the object is defined in a different namespace than the current namespace.
17.6.3.3. Viewing multi-network policies using the CLI
You can examine the multi-network policies in a namespace.
If you log in with cluster-admin privileges, you can edit network policies in any namespace in the cluster. In the web console, you can edit policies directly in YAML or by using the Actions menu.
Prerequisites
-
You installed the OpenShift CLI (
oc). -
You are logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace where the multi-network policy exists.
Procedure
List multi-network policies in a namespace.
To view multi-network policy objects defined in a namespace enter the following command:
oc get multi-networkpolicy
$ oc get multi-networkpolicyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: To examine a specific multi-network policy enter the following command:
oc describe multi-networkpolicy <policy_name> -n <namespace>
$ oc describe multi-networkpolicy <policy_name> -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<policy_name>- Specifies the name of the multi-network policy to inspect.
<namespace>- Optional: Specifies the namespace if the object is defined in a different namespace than the current namespace.
17.6.3.4. Deleting a multi-network policy using the CLI
You can delete a multi-network policy in a namespace.
If you log in with cluster-admin privileges, you can delete network policies in any namespace in the cluster. In the web console, you can delete policies directly in YAML or by using the Actions menu.
Prerequisites
-
Your cluster uses a network plugin that supports
NetworkPolicyobjects, such as the OVN-Kubernetes network plugin or the OpenShift SDN network plugin withmode: NetworkPolicyset. This mode is the default for OpenShift SDN. -
You installed the OpenShift CLI (
oc). -
You logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace where the multi-network policy exists.
Procedure
To delete a multi-network policy object, enter the following command. Successful output lists the name of the policy object and the
deletedstatus.oc delete multi-networkpolicy <policy_name> -n <namespace>
$ oc delete multi-networkpolicy <policy_name> -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<policy_name>- Specifies the name of the multi-network policy.
<namespace>- Optional parameter. If you defined the object in a different namespace than the current namespace, the parameter specifices the namespace.
17.6.3.5. Creating a default deny all multi-network policy
The default deny all multi-network policy blocks all cross-pod networking other than network traffic allowed by the configuration of other deployed network policies and traffic between host-networked pods. This procedure enforces a strong deny policy by applying a deny-by-default policy in the my-project namespace.
Without configuring a NetworkPolicy custom resource (CR) that allows traffic communication, the following policy might cause communication problems across your cluster.
Prerequisites
-
Your cluster uses a network plugin that supports
NetworkPolicyobjects, such as the OVN-Kubernetes network plugin or the OpenShift SDN network plugin withmode: NetworkPolicyset. This mode is the default for OpenShift SDN. -
You installed the OpenShift CLI (
oc). -
You logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace that the multi-network policy applies to.
Procedure
Create the following YAML that defines a
deny-by-defaultpolicy to deny ingress from all pods in all namespaces. Save the YAML in thedeny-by-default.yamlfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
namespace-
Specifies the namespace in which to deploy the policy. For example, the
my-projectnamespace. annotations- Specifies the name of namespace project followed by the network attachment definition name.
podSelector-
If this field is empty, the configuration matches all the pods. Therefore, the policy applies to all pods in the
my-projectnamespace. policyTypes-
Specifies a list of rule types that the
NetworkPolicyrelates to. - Ingress-
Specifies
IngressonlypolicyTypes. ingress- Specifies ingress rules. If not specified, all incoming traffic is dropped to all pods.
Apply the policy by entering the following command. Successful output lists the name of the policy object and the
createdstatus.oc apply -f deny-by-default.yaml
$ oc apply -f deny-by-default.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
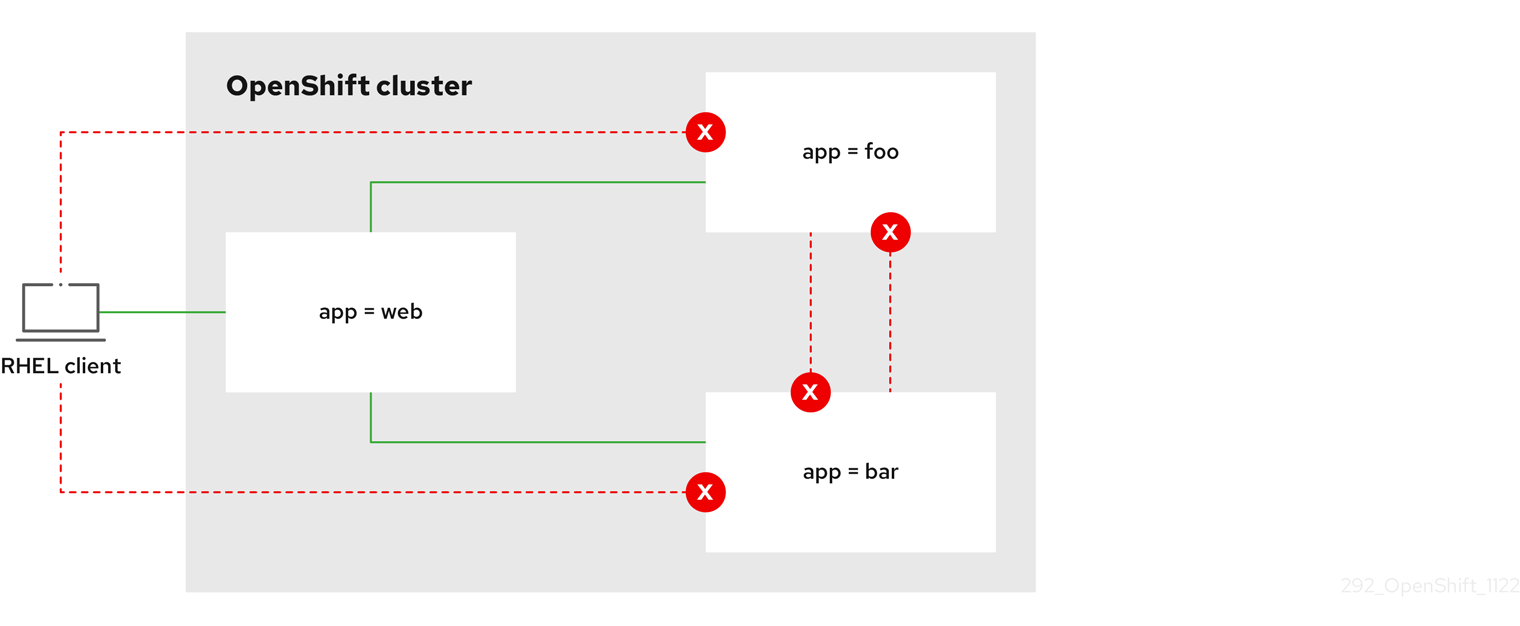
17.6.3.6. Creating a multi-network policy to allow traffic from external clients
With the deny-by-default policy in place you can proceed to configure a policy that allows traffic from external clients to a pod with the label app=web.
If you log in with a user with the cluster-admin role, then you can create a network policy in any namespace in the cluster.
Follow this procedure to configure a policy that allows external service from the public Internet directly or by using a Load Balancer to access the pod. Traffic is only allowed to a pod with the label app=web.
Prerequisites
-
Your cluster uses a network plugin that supports
NetworkPolicyobjects, such as the OVN-Kubernetes network plugin or the OpenShift SDN network plugin withmode: NetworkPolicyset. This mode is the default for OpenShift SDN. -
You installed the OpenShift CLI (
oc). -
You logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace that the multi-network policy applies to.
Procedure
Create a policy that allows traffic from the public Internet directly or by using a load balancer to access the pod. Save the YAML in the
web-allow-external.yamlfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the policy by entering the following command. Successful output lists the name of the policy object and the
createdstatus.oc apply -f web-allow-external.yaml
$ oc apply -f web-allow-external.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow This policy allows traffic from all resources, including external traffic as illustrated in the following diagram:
17.6.3.7. Creating a multi-network policy allowing traffic to an application from all namespaces
You can configure a policy that allows traffic from all pods in all namespaces to a particular application.
If you log in with a user with the cluster-admin role, then you can create a network policy in any namespace in the cluster.
Prerequisites
-
Your cluster uses a network plugin that supports
NetworkPolicyobjects, such as the OVN-Kubernetes network plugin or the OpenShift SDN network plugin withmode: NetworkPolicyset. This mode is the default for OpenShift SDN. -
You installed the OpenShift CLI (
oc). -
You logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace that the multi-network policy applies to.
Procedure
Create a policy that allows traffic from all pods in all namespaces to a particular application. Save the YAML in the
web-allow-all-namespaces.yamlfile:+ where:
+
app-
Applies the policy only to
app:webpods in default namespace. namespaceSelector- Selects all pods in all namespaces.
By default, if you do not specify a namespaceSelector parameter in the policy object, no namespaces get selected. This means the policy allows traffic only from the namespace where the network policy deployes.
Apply the policy by entering the following command. Successful output lists the name of the policy object and the
createdstatus.oc apply -f web-allow-all-namespaces.yaml
$ oc apply -f web-allow-all-namespaces.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Start a web service in the
defaultnamespace by entering the following command:oc run web --namespace=default --image=nginx --labels="app=web" --expose --port=80
$ oc run web --namespace=default --image=nginx --labels="app=web" --expose --port=80Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to deploy an
alpineimage in thesecondarynamespace and to start a shell:oc run test-$RANDOM --namespace=secondary --rm -i -t --image=alpine -- sh
$ oc run test-$RANDOM --namespace=secondary --rm -i -t --image=alpine -- shCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command in the shell and observe that the service allows the request:
wget -qO- --timeout=2 http://web.default
# wget -qO- --timeout=2 http://web.defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.6.3.8. Creating a multi-network policy allowing traffic to an application from a namespace
You can configure a policy that allows traffic to a pod with the label app=web from a particular namespace. This configuration is useful in the following use cases:
- Restrict traffic to a production database only to namespaces that have production workloads deployed.
- Enable monitoring tools deployed to a particular namespace to scrape metrics from the current namespace.
If you log in with a user with the cluster-admin role, then you can create a network policy in any namespace in the cluster.
Prerequisites
-
Your cluster uses a network plugin that supports
NetworkPolicyobjects, such as the OVN-Kubernetes network plugin or the OpenShift SDN network plugin withmode: NetworkPolicyset. This mode is the default for OpenShift SDN. -
You installed the OpenShift CLI (
oc). -
You logged in to the cluster with a user with
cluster-adminprivileges. - You are working in the namespace that the multi-network policy applies to.
Procedure
Create a policy that allows traffic from all pods in a particular namespaces with a label
purpose=production. Save the YAML in theweb-allow-prod.yamlfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
app-
Applies the policy only to
app:webpods in the default namespace. purpose-
Restricts traffic to only pods in namespaces that have the label
purpose=production.
Apply the policy by entering the following command. Successful output lists the name of the policy object and the
createdstatus.oc apply -f web-allow-prod.yaml
$ oc apply -f web-allow-prod.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Start a web service in the
defaultnamespace by entering the following command:oc run web --namespace=default --image=nginx --labels="app=web" --expose --port=80
$ oc run web --namespace=default --image=nginx --labels="app=web" --expose --port=80Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to create the
prodnamespace:oc create namespace prod
$ oc create namespace prodCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to label the
prodnamespace:oc label namespace/prod purpose=production
$ oc label namespace/prod purpose=productionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to create the
devnamespace:oc create namespace dev
$ oc create namespace devCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to label the
devnamespace:oc label namespace/dev purpose=testing
$ oc label namespace/dev purpose=testingCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to deploy an
alpineimage in thedevnamespace and to start a shell:oc run test-$RANDOM --namespace=dev --rm -i -t --image=alpine -- sh
$ oc run test-$RANDOM --namespace=dev --rm -i -t --image=alpine -- shCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command in the shell and observe the reason for the blocked request. For example, expected output states
wget: download timed out.wget -qO- --timeout=2 http://web.default
# wget -qO- --timeout=2 http://web.defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to deploy an
alpineimage in theprodnamespace and start a shell:oc run test-$RANDOM --namespace=prod --rm -i -t --image=alpine -- sh
$ oc run test-$RANDOM --namespace=prod --rm -i -t --image=alpine -- shCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command in the shell and observe that the request is allowed:
wget -qO- --timeout=2 http://web.default
# wget -qO- --timeout=2 http://web.defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.7. Attaching a pod to an additional network
To enable a pod to use additional network interfaces beyond the primary cluster network in OpenShift Container Platform, you can attach the pod to a secondary network. Secondary networks provide additional connectivity options for your workloads.
17.7.1. Adding a pod to an additional network
To enable a pod to use additional network interfaces in OpenShift Container Platform, you can attach the pod to a secondary network. The pod continues to send normal cluster-related network traffic over the default network.
When a pod is created, a secondary network is attached to the pod. However, if a pod already exists, you cannot attach a secondary network to it.
The pod must be in the same namespace as the additional network.
Prerequisites
-
Install the OpenShift CLI (
oc). - Log in to the cluster.
Procedure
Add an annotation to the
Podobject. Only one of the following annotation formats can be used:To attach a secondary network without any customization, add an annotation with the following format:
metadata: annotations: k8s.v1.cni.cncf.io/networks: <network>[,<network>,...]metadata: annotations: k8s.v1.cni.cncf.io/networks: <network>[,<network>,...]Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
k8s.v1.cni.cncf.io/networks- Specifies the name of the secondary network to associate with the pod. To specify more than one secondary network, separate each network with a comma. Do not include whitespace between the comma. If you specify the same secondary network multiple times, that pod will have multiple network interfaces attached to that network.
To attach a secondary network with customizations, add an annotation with the following format:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<network>-
Specifies the name of the secondary network defined by a
NetworkAttachmentDefinitionobject. <namespace>-
Specifies the namespace where the
NetworkAttachmentDefinitionobject is defined. <default-route>-
Optional parameter. Specifies an override for the default route, such as
192.168.17.1.
Create the pod by entering the following command.
oc create -f <name>.yaml
$ oc create -f <name>.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<name>with the name of the pod.Optional: Confirm that the annotation exists in the
podCR by entering the following command. Replace<name>with the name of the pod.oc get pod <name> -o yaml
$ oc get pod <name> -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the following example, the
example-podpod is attached to thenet1additional network:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
k8s.v1.cni.cncf.io/network-status- Specifies a JSON array of objects. Each object describes the status of a secondary network attached to the pod. The annotation value is stored as a plain text value.
17.7.1.1. Specifying pod-specific addressing and routing options
To set static IP addresses, MAC addresses, and default routes for a pod in OpenShift Container Platform, you can configure pod-specific addressing and routing options using JSON-formatted annotations. With these annotations, you can customize network behavior for individual pods on secondary networks.
Prerequisites
- The pod must be in the same namespace as the additional network.
-
Install the OpenShift CLI (
oc). - You must log in to the cluster.
Procedure
Edit the
Podresource definition. If you are editing an existingPodresource, run the following command to edit its definition in the default editor. Replace<name>with the name of thePodresource to edit.oc edit pod <name>
$ oc edit pod <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the
Podresource definition, add thek8s.v1.cni.cncf.io/networksparameter to the podmetadatamapping. Thek8s.v1.cni.cncf.io/networksaccepts a JSON string of a list of objects that reference the name ofNetworkAttachmentDefinitioncustom resource (CR) names in addition to specifying additional properties.metadata: annotations: k8s.v1.cni.cncf.io/networks: '[<network>[,<network>,...]]' # ...metadata: annotations: k8s.v1.cni.cncf.io/networks: '[<network>[,<network>,...]]' # ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<network>- Replace with a JSON object as shown in the following examples. The single quotes are required.
In the following example the annotation specifies which network attachment will have the default route, using the
default-routeparameter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
net1,net2-
Specifies the name of the
NetworkAttachmentDefinitionresource that defines the secondary network to associate with the pod. 192.0.2.1-
Specifies a value of a gateway for traffic to be routed over if no other routing entry is present in the routing table. If more than one
default-routekey is specified, this will cause the pod to fail to become active.
The default route will cause any traffic that is not specified in other routes to be routed to the gateway.
ImportantSetting the default route to an interface other than the default network interface for OpenShift Container Platform may cause traffic that is anticipated for pod-to-pod traffic to be routed over another interface.
To verify the routing properties of a pod, the
occommand may be used to execute theipcommand within a pod.oc exec -it <pod_name> -- ip route
$ oc exec -it <pod_name> -- ip routeCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou may also reference the pod’s
k8s.v1.cni.cncf.io/network-statusto see which additional network has been assigned the default route, by the presence of thedefault-routekey in the JSON-formatted list of objects.To set a static IP address or MAC address for a pod you can use the JSON formatted annotations. This requires you create networks that specifically allow for this functionality. This can be specified in a rawCNIConfig for the CNO.
Edit the CNO CR by running the following command:
oc edit networks.operator.openshift.io cluster
$ oc edit networks.operator.openshift.io clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow The following YAML describes the configuration parameters for the CNO:
Cluster Network Operator YAML configuration
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
name-
Specifies a name for the secondary network attachment that you are creating. The name must be unique within the specified
namespace. namespace-
Specifies the namespace to create the network attachment in. If you do not specify a value, then the
defaultnamespace is used. rawCNIConfig- Specifies the CNI plugin configuration in JSON format, which is based on the following template.
The following object describes the configuration parameters for utilizing static MAC address and IP address using the macvlan CNI plugin:
macvlan CNI plugin JSON configuration object using static IP and MAC address
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
name-
Specifies the name for the secondary network attachment to create. The name must be unique within the specified
namespace. plugins- Specifies an array of CNI plugin configurations. The first object specifies a macvlan plugin configuration and the second object specifies a tuning plugin configuration.
ips- Specifies that a request is made to enable the static IP address functionality of the CNI plugin runtime configuration capabilities.
master- Specifies the interface that the macvlan plugin uses.
mac- Specifies that a request is made to enable the static MAC address functionality of a CNI plugin.
The above network attachment can be referenced in a JSON formatted annotation, along with keys to specify which static IP and MAC address will be assigned to a given pod.
Edit the pod by entering the following command:
oc edit pod <name>
$ oc edit pod <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow macvlan CNI plugin JSON configuration object using static IP and MAC address
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
metadata.name-
Specifies the name for the secondary network attachment to create. The name must be unique within the specified
namespace. metadata.annotations.k8s.v1.cni.cncf.io/ips- Specifies an IP address including the subnet mask.
metadata.annotations.k8s.v1.cni.cncf.io/mac- Specifies the MAC address.
NoteStatic IP addresses and MAC addresses do not have to be used at the same time. You can use them individually, or together.
17.8. Removing a pod from an additional network
To disconnect a pod from specific network configurations in OpenShift Container Platform, you can remove the pod from a secondary network. Delete the pod to remove its connection to the secondary network.
17.8.1. Removing a pod from an additional network
To disconnect a pod from specific network configurations in OpenShift Container Platform, you can remove the pod from a secondary network. Delete the pod using the oc delete pod command to remove its connection to the secondary network.
Prerequisites
- An additional network is attached to the pod.
-
Install the OpenShift CLI (
oc). - Log in to the cluster.
Procedure
Delete the pod by entering the following command:
oc delete pod <name> -n <namespace>
$ oc delete pod <name> -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<name>- Specifies the name of the pod.
<namespace>- Specifies the namespace that contains the pod.
17.9. Editing an additional network
To update network settings or change network parameters for a secondary network in OpenShift Container Platform, you can modify the configuration for an existing secondary network. Edit the NetworkAttachmentDefinition custom resource to apply your changes.
17.9.1. Modifying a NetworkAttachmentDefinition custom resource
To update network settings or change network parameters for a secondary network in OpenShift Container Platform, you can modify the NetworkAttachmentDefinition custom resource. Edit the Cluster Network Operator CR to apply your changes.
Prerequisites
- You have configured an additional network for your cluster.
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Edit the Cluster Network Operator (CNO) CR in your default text editor by running the following command:
oc edit networks.operator.openshift.io cluster
$ oc edit networks.operator.openshift.io clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
In the
additionalNetworkscollection, update the secondary network with your changes. - Save your changes and quit the text editor to commit your changes.
Optional: Confirm that the CNO updated the
NetworkAttachmentDefinitionobject by running the following command. Replace<network_name>with the name of the secondary network to display. There might be a delay before the CNO updates theNetworkAttachmentDefinitionobject to reflect your changes.oc get network-attachment-definitions <network_name> -o yaml
$ oc get network-attachment-definitions <network_name> -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example, the following console output displays a
NetworkAttachmentDefinitionobject that is namednet1:oc get network-attachment-definitions net1 -o go-template='{{printf "%s\n" .spec.config}}' { "cniVersion": "0.3.1", "type": "macvlan", "master": "ens5", "mode": "bridge", "ipam": {"type":"static","routes":[{"dst":"0.0.0.0/0","gw":"10.128.2.1"}],"addresses":[{"address":"10.128.2.100/23","gateway":"10.128.2.1"}],"dns":{"nameservers":["172.30.0.10"],"domain":"us-west-2.compute.internal","search":["us-west-2.compute.internal"]}} }$ oc get network-attachment-definitions net1 -o go-template='{{printf "%s\n" .spec.config}}' { "cniVersion": "0.3.1", "type": "macvlan", "master": "ens5", "mode": "bridge", "ipam": {"type":"static","routes":[{"dst":"0.0.0.0/0","gw":"10.128.2.1"}],"addresses":[{"address":"10.128.2.100/23","gateway":"10.128.2.1"}],"dns":{"nameservers":["172.30.0.10"],"domain":"us-west-2.compute.internal","search":["us-west-2.compute.internal"]}} }Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.9.2. Using an OVN-Kubernetes localnet topology to map VLANs to a secondary interface
You can use OVN-Kubernetes localnet topology in a NetworkAttachmentDefinition (NAD) to map a specific VLAN ID from the physical network to the secondary interface of a pod.
To provide multiple VLANs for cluster workloads in OpenShift Container Platform, define additional VLANs in the NetworkAttachmentDefinition custom resource (CR). Configuring trunk ports ensures that the physical network associates correctly with your virtual infrastructure for reliable traffic management.
The example in the procedure demonstrates the following configurations:
- Physical switch ports connect to OpenShift Container Platform nodes by using VLAN trunking. The trunk carries tagged traffic for the VLANs you define in NADs.
-
The
br-exacts as the OVS bridge that connects virtual workloads to the physical workloads. -
Multiple NADs with specific VLAN tags get created by using the
localnettopology. This configuration defines specific VLAN IDs for traffic isolation. - Pods or virtual machines (VMs) attach to the NAD CRs for the purposes of improved network connectivity.
Prerequisites
-
You installed the OpenShift CLI (
oc). -
You logged in as a user with
cluster-adminprivileges. - You installed the NMState Operator.
-
You configured the
br-exbridge interface during cluster installation.
Procedure
Create an
NetworkAttachmentDefinitionCR for each VLAN, such asnad-cvlan100.yaml. OVN-Kubernetes uses the NAD files to tag and untag Ethernet frames for pods or VMs.Example configuration
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Attach pods or VMs to the VLANs by referencing the NAD in the configuration for the pod or VM:
Example pod configuration
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example VM configuration
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
17.10. Removing an additional network
To clean up unused network configurations or free up network resources in OpenShift Container Platform, you can remove an additional network attachment. Delete the NetworkAttachmentDefinition custom resource to remove the secondary network from your cluster.
17.10.1. Removing a secondary NetworkAttachmentDefinition custom resource
To clean up unused network configurations or free up network resources in OpenShift Container Platform, you can remove a secondary NetworkAttachmentDefinition CR. Edit the Cluster Network Operator CR and delete the NetworkAttachmentDefinition CR to remove the secondary network from your cluster.
When a secondary network is removed from the cluster, it is not removed from any pods that it is attached to.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in as a user with
cluster-adminprivileges.
Procedure
Edit the Cluster Network Operator (CNO) in your default text editor by running the following command:
oc edit networks.operator.openshift.io cluster
$ oc edit networks.operator.openshift.io clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Modify the custom resource (CR) by removing the configuration that the CNO created from the
additionalNetworkscollection for the secondary network that you want to remove.Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
spec.additionalNetworks-
Specifies the secondary network attachment definition that you want to remove from the
additionalNetworkscollection. If you are removing the configuration mapping for the only secondary network attachment definition in theadditionalNetworkscollection, you must specify an empty collection.
Remove the
NetworkAttachmentDefinitionCR from the network of your cluster by entering the following command:oc delete net-attach-def <name_of_network_attachment_definition>
$ oc delete net-attach-def <name_of_network_attachment_definition>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<name_of_network_attachment_definition>with the name of theNetworkAttachmentDefinitionCR that you want to remove.- Save your changes and quit the text editor to commit your changes.
Optional: Confirm that the additional network CR was deleted by running the following command:
oc get network-attachment-definition --all-namespaces
$ oc get network-attachment-definition --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
17.11. Assigning a secondary network to a VRF
As a cluster administrator, you can configure a secondary network for a virtual routing and forwarding (VRF) domain by using the CNI VRF plugin. The virtual network that this plugin creates is associated with the physical interface that you specify.
Using a secondary network with a VRF instance has the following advantages:
- Workload isolation
- Isolate workload traffic by configuring a VRF instance for the additional network.
- Improved security
- Enable improved security through isolated network paths in the VRF domain.
- Multi-tenancy support
- Support multi-tenancy through network segmentation with a unique routing table in the VRF domain for each tenant.
Applications that use VRFs must bind to a specific device. The common usage is to use the SO_BINDTODEVICE option for a socket. The SO_BINDTODEVICE option binds the socket to the device that is specified in the passed interface name, for example, eth1. To use the SO_BINDTODEVICE option, the application must have CAP_NET_RAW capabilities.
Using a VRF through the ip vrf exec command is not supported in OpenShift Container Platform pods. To use VRF, bind applications directly to the VRF interface.
17.11.1. Creating an additional network attachment with the CNI VRF plugin
The Cluster Network Operator (CNO) manages secondary network definitions. When you specify a secondary network in the cluster-scoped Network custom resource (CR), the CNO automatically creates the NetworkAttachmentDefinition CR.
Do not edit the NetworkAttachmentDefinition CRs that the Cluster Network Operator manages. Doing so might disrupt network traffic on your additional network.
To create an additional network attachment with the CNI VRF plugin, perform the following procedure.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Log in to the cluster as a user with
cluster-adminprivileges.
Procedure
Create the
NetworkCR for the additional network attachment and insert therawCNIConfigconfiguration for the secondary network. Save as theadditional-network-attachment.yamlfile.Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
plugins- You must specify a list. The first item in the list must be the secondary network underpinning the VRF network. The second item in the list is the VRF plugin configuration.
type-
You must set this parameter to
vrf. vrfname- The name of the VRF that the interface is assigned to. If the VRF does not exist in the pod, the CNI creates the VRF.
tableOptional parameter. Specify the routing table ID. By default, the
tableidparameter is used. If you do not specify a table ID, the CNI assigns a free routing table ID to the VRF.NoteVRF functions correctly only when the resource is of type
netdevice.
Create the
Networkresource:oc create -f additional-network-attachment.yaml
$ oc create -f additional-network-attachment.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the CNO created the
NetworkAttachmentDefinitionCR by running the following command. Replace<namespace>with the namespace that you specified when configuring the network attachment, for example,additional-network-1. The expected output shows the name of the NAD CR and the creation age in minutes.oc get network-attachment-definitions -n <namespace>
$ oc get network-attachment-definitions -n <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteA delay might exist before the CNO creates the CR.
Verification
Create a pod and assign the pod to the secondary network that includes the VRF plugin configuration.
Create a YAML file that defines the
Podresource, as demonstrated in the followingpod-additional-net.yamlfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
name- Specify the name of the secondary network that includes the VRF plugin configuration.
Create the
Podresource by running the following command. The expected output shows the name of thePodresource and the creation age in minutes.oc create -f pod-additional-net.yaml
$ oc create -f pod-additional-net.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verify that the pod network attachment connects to the VRF secondary network. Start a remote session with the pod and run the following command. The expected output shows the name of the VRF interface and its unique ID in the routing table.
ip vrf show
$ ip vrf showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the VRF interface is the controller for the secondary interface by entering the following command:
ip link
$ ip linkCopy to Clipboard Copied! Toggle word wrap Toggle overflow 5: net1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master red state UP mode
5: net1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master red state UP modeCopy to Clipboard Copied! Toggle word wrap Toggle overflow