Chapter 94. Managing DNS locations in IdM
To learn more about managing Identity Management (IdM) DNS locations by using the IdM Web UI and IdM command-line interface (CLI), see the following topics and procedures:
- DNS-based service discovery
- Deployment considerations for DNS locations
- DNS time to live (TTL)
- Creating DNS locations using the IdM Web UI
- Creating DNS locations using the IdM CLI
- Assigning an IdM server to a DNS location using the IdM Web UI
- Assigning an IdM server to a DNS location using the IdM Web UI
- Configuring an IdM client to use IdM servers in the same location
94.1. DNS-based service discovery
DNS-based service discovery is a process in which a client uses the DNS protocol to locate servers in a network that offer a specific service, such as LDAP or Kerberos. One typical type of operation is to allow clients to locate authentication servers within the closest network infrastructure, because they provide a higher throughput and lower network latency, lowering overall costs.
The major advantages of service discovery are:
- No need for clients to be explicitly configured with names of nearby servers.
- DNS servers are used as central providers of policy. Clients using the same DNS server have access to the same policy about service providers and their preferred order.
In an Identity Management (IdM) domain, DNS service records (SRV records) exist for LDAP, Kerberos, and other services. For example, the following command queries the DNS server for hosts providing a TCP-based Kerberos service in an IdM DNS domain:
Example 94.1. DNS location independent results
$ dig -t SRV +short _kerberos._tcp.idm.example.com
0 100 88 idmserver-01.idm.example.com.
0 100 88 idmserver-02.idm.example.com.The output contains the following information:
-
0(priority): Priority of the target host. A lower value is preferred. -
100(weight). Specifies a relative weight for entries with the same priority. For further information, see RFC 2782, section 3. -
88(port number): Port number of the service. - Canonical name of the host providing the service.
In the example, the two host names returned have the same priority and weight. In this case, the client uses a random entry from the result list.
When the client is, instead, configured to query a DNS server that is configured in a DNS location, the output differs. For IdM servers that are assigned to a location, tailored values are returned. In the example below, the client is configured to query a DNS server in the location germany:
Example 94.2. DNS location-based results
$ dig -t SRV +short _kerberos._tcp.idm.example.com
_kerberos._tcp.germany._locations.idm.example.com.
0 100 88 idmserver-01.idm.example.com.
50 100 88 idmserver-02.idm.example.com.The IdM DNS server automatically returns a DNS alias (CNAME) pointing to a DNS location specific SRV record which prefers local servers. This CNAME record is shown in the first line of the output. In the example, the host idmserver-01.idm.example.com has the lowest priority value and is therefore preferred. The idmserver-02.idm.example.com has a higher priority and thus is used only as backup for cases when the preferred host is unavailable.
94.2. Deployment considerations for DNS locations
Identity Management (IdM) can generate location-specific service (SRV) records when using the integrated DNS. Because each IdM DNS server generates location-specific SRV records, you have to install at least one IdM DNS server in each DNS location.
The client’s affinity to a DNS location is only defined by the DNS records received by the client. For this reason, you can combine IdM DNS servers with non-IdM DNS consumer servers and recursors if the clients doing DNS service discovery resolve location-specific records from IdM DNS servers.
In the majority of deployments with mixed IdM and non-IdM DNS services, DNS recursors select the closest IdM DNS server automatically by using round-trip time metrics. Typically, this ensures that clients using non-IdM DNS servers are getting records for the nearest DNS location and thus use the optimal set of IdM servers.
94.3. DNS time to live (TTL)
Clients can cache DNS resource records for an amount of time that is set in the zone’s configuration. Because of this caching, a client might not be able to receive the changes until the time to live (TTL) value expires. The default TTL value in Identity Management (IdM) is 1 day.
If your client computers roam between sites, you should adapt the TTL value for your IdM DNS zone. Set the value to a lower value than the time clients need to roam between sites. This ensures that cached DNS entries on the client expire before they reconnect to another site and thus query the DNS server to refresh location-specific SRV records.
Additional resources
94.4. Creating DNS locations using the IdM Web UI
You can use DNS locations to increase the speed of communication between Identity Management (IdM) clients and servers. Follow this procedure to create a DNS location using the IdM Web UI.
Prerequisites
- Your IdM deployment has integrated DNS.
- You have a permission to create DNS locations in IdM. For example, you are logged in as IdM admin.
Procedure
-
Open the
IPA Servertab. -
Select
Topologysubtab. -
Click
IPA Locationsin the navigation bar. - Click at the top of the locations list.
- Fill in the location name.
- Click the button to save the location.
- Optional: Repeat the steps to add further locations.
Additional resources
94.5. Creating DNS locations using the IdM CLI
You can use DNS locations to increase the speed of communication between Identity Management (IdM) clients and servers. Follow this procedure to create DNS locations using the ipa location-add command in the IdM command-line interface (CLI).
Prerequisites
- Your IdM deployment has integrated DNS.
- You have a permission to create DNS locations in IdM. For example, you are logged in as IdM admin.
Procedure
For example, to create a new location
germany, enter:$ ipa location-add germany ---------------------------- Added IPA location "germany" ---------------------------- Location name: germany- Optional: Repeat the step to add further locations.
Additional resources
94.6. Assigning an IdM server to a DNS location using the IdM Web UI
You can use Identity Management (IdM) DNS locations to increase the speed of communication between IdM clients and servers. Follow this procedure to assign IdM servers to DNS locations using the IdM Web UI.
Prerequisites
- Your IdM deployment has integrated DNS.
- You are logged in as a user with a permission to assign a server to a DNS location, for example the IdM admin user.
-
You have
rootaccess to the host that you want to assign a DNS location to. - You have created the IdM DNS locations to which you want to assign servers.
Procedure
-
Open the
IPA Servertab. -
Select the
Topologysubtab. -
Click
IPA Serversin the navigation. - Click on the IdM server name.
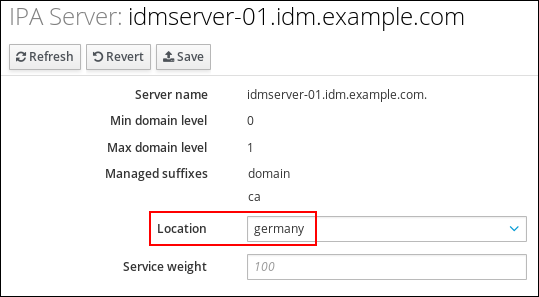
Select a DNS location, and optionally set a service weight:
Figure 94.1. Assigning a server to a DNS location
- Click .
In the command-line interface (CLI) of the host you assigned in the previous steps the DNS location to, restart the
named-pkcs11service:[root@idmserver-01 ~]# systemctl restart named-pkcs11- Optional: Repeat the steps to assign DNS locations to further IdM servers.
Additional resources
94.7. Assigning an IdM server to a DNS location using the IdM CLI
You can use Identity Management (IdM) DNS locations to increase the speed of communication between IdM clients and servers. Follow this procedure to assign IdM servers to DNS locations using the IdM command-line interface (CLI).
Prerequisites
- Your IdM deployment has integrated DNS.
- You are logged in as a user with a permission to assign a server to a DNS location, for example the IdM admin user.
-
You have
rootaccess to the host that you want to assign a DNS location to. - You have created the IdM DNS locations to which you want to assign servers.
Procedure
Optional: List all configured DNS locations:
[root@server ~]# ipa location-find ----------------------- 2 IPA locations matched ----------------------- Location name: australia Location name: germany ----------------------------- Number of entries returned: 2 -----------------------------Assign the server to the DNS location. For example, to assign the location
germanyto the server idmserver-01.idm.example.com, run:# ipa server-mod idmserver-01.idm.example.com --location=germany ipa: WARNING: Service named-pkcs11.service requires restart on IPA server idmserver-01.idm.example.com to apply configuration changes. -------------------------------------------------- Modified IPA server "idmserver-01.idm.example.com" -------------------------------------------------- Servername: idmserver-01.idm.example.com Min domain level: 0 Max domain level: 1 Location: germany Enabled server roles: DNS server, NTP serverRestart the
named-pkcs11service on the host you assigned in the previous steps the DNS location to:# systemctl restart named-pkcs11- Optional: Repeat the steps to assign DNS locations to further IdM servers.
Additional resources
94.8. Configuring an IdM client to use IdM servers in the same location
Identity Management (IdM) servers are assigned to DNS locations as described in Assigning an IdM server to a DNS location using the IdM Web UI. Now you can configure the clients to use a DNS server that is in the same location as the IdM servers:
-
If a
DHCPserver assigns the DNS server IP addresses to the clients, configure theDHCPservice. For further details about assigning a DNS server in yourDHCPservice, see theDHCPservice documentation. -
If your clients do not receive the DNS server IP addresses from a
DHCPserver, manually set the IPs in the client’s network configuration. For further details about configuring the network on Red Hat Enterprise Linux, see the Configuring Network Connection Settings section in the Red Hat Enterprise Linux Networking Guide.
If you configure the client to use a DNS server that is assigned to a different location, the client contacts IdM servers in both locations.
Example 94.3. Different name server entries depending on the location of the client
The following example shows different name server entries in the /etc/resolv.conf file for clients in different locations:
Clients in Prague:
nameserver 10.10.0.1 nameserver 10.10.0.2
Clients in Paris:
nameserver 10.50.0.1 nameserver 10.50.0.3
Clients in Oslo:
nameserver 10.30.0.1
Clients in Berlin:
nameserver 10.30.0.1
If each of the DNS servers is assigned to a location in IdM, the clients use the IdM servers in their location.