9.4. Changing Passwords
Password policies (Chapter 19, Policy: Defining Password Policies) and minimal access restrictions can be applied to a password change operation:
- Regular, non-administrative users can change only their personal passwords, and all passwords are constrained by the IdM password policies.This allows administrators to create intro passwords or to reset passwords easily, while still keeping the final password confidential. Since any password sent by an administrator to the user is temporary, there is little security risk.
- Changing a password as the IdM admin user overrides any IdM password policies, but the password expires immediately. This requires the user to change the password at the next login. Similarly, any user who has password change rights can change a password and no password policies are applied, but the other user must reset the password at the next login.
- Changing a password as the LDAP Directory Manager user, using LDAP tools, overrides any IdM password policies.
9.4.1. From the Web UI
Copy linkLink copied to clipboard!
- Open the Identity tab, and select the Users subtab.
- Click the name of the user for whom to reset the password. All users can change their own password; only administrators or users with delegated permissions can change other user's passwords.
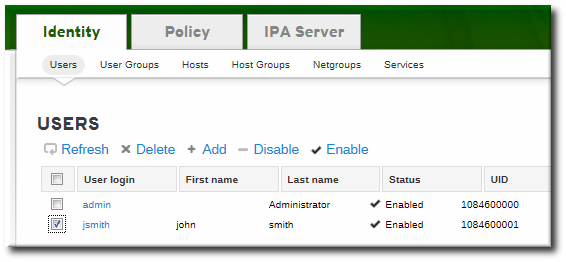
- Scroll to the Account Settings area.
- Click the Reset Password link.
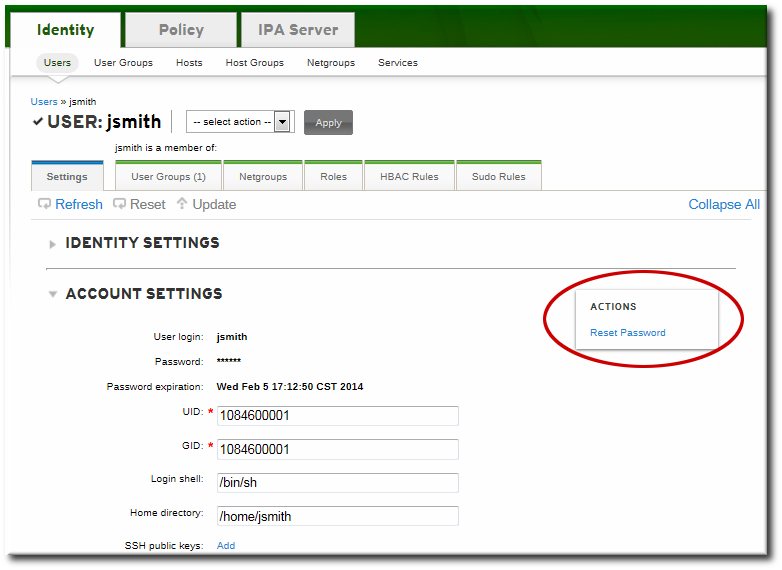
- In the pop-up box, enter and confirm the new password.

9.4.2. From the Command Line
Copy linkLink copied to clipboard!
Changing a password — your own or another user's — is done using the
user-mod command, as with other user account changes.
kinit admin ipa user-mod jsmith --password
[bjensen@ipaserver ~]$ kinit admin
[bjensen@ipaserver ~]$ ipa user-mod jsmith --password