22.2. Creating Host-Based Access Control Entries for Services and Service Groups
Any PAM service can be identified as to the host-based access control (HBAC) system in IdM. The service entries used in host-based access control are separate from adding a service to the IdM domain. Adding a service to the domain makes it a recognized resource which is available to other resources. Adding a domain resource to the host-based access control configuration allows administrators to exert defined control over what domain users and what domain clients can access that service.
Some common services are already configured as HBAC services, so they can be used in host-based access control rules. Additional services can be added, and services can be added into service groups for simpler management.
22.2.1. Adding HBAC Services
Copy linkLink copied to clipboard!
22.2.1.1. Adding HBAC Services in the Web UI
Copy linkLink copied to clipboard!
- Click the Policy tab.
- Click the Host-Based Access Control subtab, and then select the HBAC Services link.
- Click the Add link at the top of the list of services.

- Enter the service name and a description.
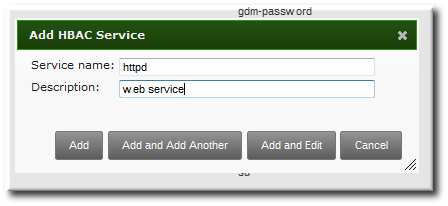
- Click the Add button to save the new service.
- If a service group already exists, then add the service to the desired group, as described in Section 22.2.2.1, “Adding Service Groups in the Web UI”.
22.2.1.2. Adding Services in the Command Line
Copy linkLink copied to clipboard!
The service is added to the access control system using the
hbacsvc-add command, specifying the service by the name that PAM uses to evaluate the service.
For example, this adds the
tftp service:
If a service group already exists, then the service can be added to the group using the
hbacsvcgroup-add-member command, as in Section 22.2.2.2, “Adding Service Groups in the Command Line”.
22.2.2. Adding Service Groups
Copy linkLink copied to clipboard!
Once the individual service is added, it can be added to the access control rule. However, if there is a large number of services, then it can require frequent updates to the access control rules as services change. Identity Management also allows groups of services to be added to access control rules. This makes it much easier to manage access control, because the members of the service group can be changed without having to edit the rule itself.
22.2.2.1. Adding Service Groups in the Web UI
Copy linkLink copied to clipboard!
- Click the Policy tab.
- Click the Host-Based Access Control subtab, and then select the HBAC Service Groups link.
- Click the Add link at the top of the list of service groups.

- Enter the service group name and a description.
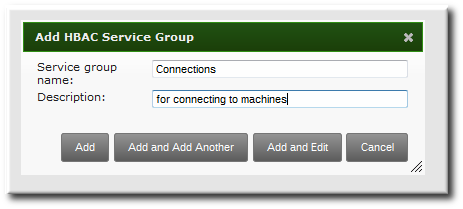
- Click the Add and Edit button to go immediately to the service group configuration page.
- At the top of the HBAC Services tab, click the Add link.
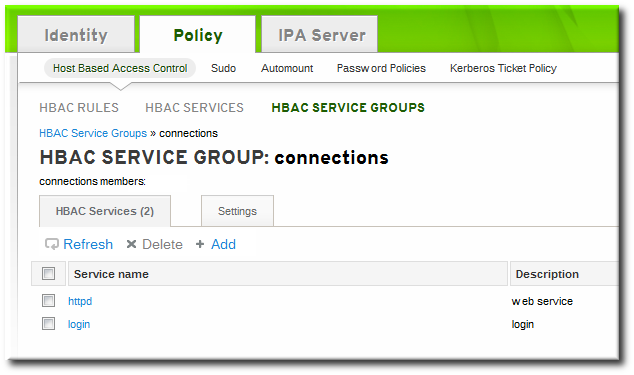
- Click the checkbox by the names of the services to add, and click the right arrows button, , to move the command to the selection box.

- Click the button to save the group membership.
22.2.2.2. Adding Service Groups in the Command Line
Copy linkLink copied to clipboard!
First create the service group entry, then create the service, and then add that service to the service group as a member. For example:
Note
IdM defines two default service groups:
SUDO for sudo services and FTP for services which provide FTP access.