22.3. Defining Host-Based Access Control Rules
Access controls, at a high level, define who has access to what. The who is an IdM user, and the what can be either a host (target host), service, or service group, or a combination of the three.
22.3.1. Setting Host-Based Access Control Rules in the Web UI
Copy linkLink copied to clipboard!
- Click the Policy tab.
- Click the Host-Based Access Control subtab, and then select the HBAC Rules link.
- Click the Add link at the top of the list of host-based access control rules.
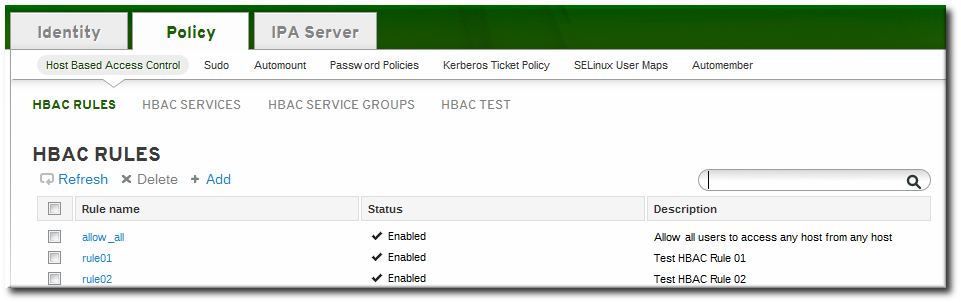
- Enter the name for the rule.

- Click the Add and Edit button to go immediately to set the configuration for the rule.There are a number of configuration areas for the rule. The three basic elements are who the rule applies to, what hosts allow access (the target), and, optionally, what services can be accessed.
- In the Who area, select the users or user groups to which the access control rule is applied.To apply the rule to all IdM users, select the Anyone radio button.To apply the rule to a specific set of users or user groups:
- Select the Specified Users and Groups radio button.
- Click the + Add link at the right of the users list.
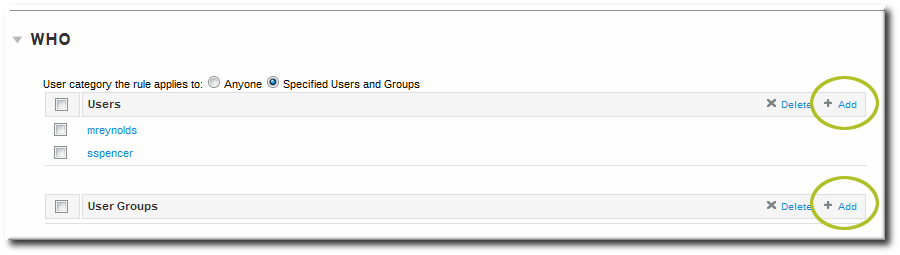
- Click the checkbox by the users to add to the rule, and click the right arrows button, , to move the users to the selection box.

- Click .
- In the Accessing area, select the target hosts which can be accessed through this access control rule.To apply the rule to all IdM hosts, select the Any Host radio button.To apply the rule to a specific set of hosts or host groups:
- Select the Specified Hosts and Groups radio button.
- Click the + Add link at the right of the hosts list.

- Click the checkbox by the hosts to include with the rule, and click the right arrows button, , to move the hosts to the selection box.

- Click .
- In the Via Service area, select specific services on the target hosts which the users are allowed to use to access target machines.To apply the rule to all IdM hosts, select the Any Service radio button.To apply the rule to a specific set of hosts or host groups:
- Select the Specified Services and Groups radio button.
- Click the + Add link at the right of the commands list.

- Click the checkbox by the services or groups to include with the rule, and click the right arrows button, , to move the services to the selection box.
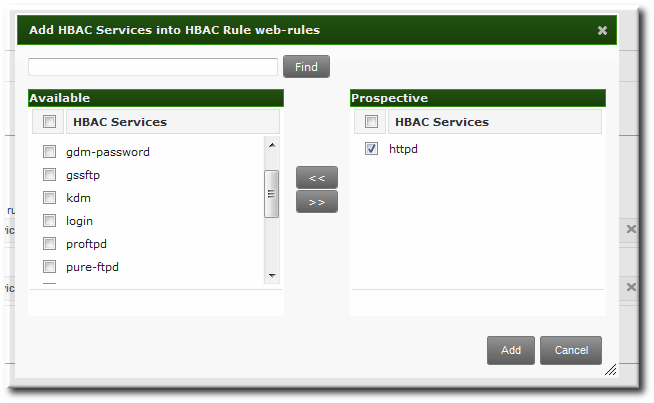
- Click .
22.3.2. Setting Host-Based Access Control Rules in the Command Line
Copy linkLink copied to clipboard!
Access control rules are created using the
hbacrule-* commands (listed in Table 22.1, “Host-Based Access Control Command and Options”). The first step is to create a container entry; from there, users, hosts, and services can be added to the access control entry.
The basic outline of all the access control commands is:
ipa hbacrule-add* options ruleName
$ ipa hbacrule-add* options ruleNameNote
To set every user or every host as a target, use the category options, such as
--usercat=all.
Example 22.1. Granting All Access to One Host
One simple rule is to grant every user access to a single server. The first command creates the entry and uses the category options to apply every user.
The second rule adds the target host, using the
hbacrule-add-host command:
Example 22.2. Adding Control for a Single User to a Service
Another access control method is to specify which services users are allowed to use to access the target hosts.
First, for the user to have access to every machine, every host must be added as both a host and target. This can be done using the category options:
ipa hbacrule-add --hostcat=all sshd-jsmith
$ ipa hbacrule-add --hostcat=all sshd-jsmith
Since the access control rule applies to a specific user, the user is added to the rule using the
hbacrule-add-user command:
ipa hbacrule-add-user --users=jsmith sshd-jsmith
$ ipa hbacrule-add-user --users=jsmith sshd-jsmith
Then, the service is added to the access control rule. (The service should have already been added to the access control system using the
hbacsvc-add command.) This is the service that the user can use to connect to the machine.
ipa hbacrule-add-service --hbacsvcs=sshd sshd-jsmith
$ ipa hbacrule-add-service --hbacsvcs=sshd sshd-jsmithExample 22.3. Adding a Service Group to the Rule
While a single service can be added to a rule, it is also possible to add an entire service group. Like a single service, this uses the
hbacrule-add-service command, only with the --hbacsvcgroups option that specifies the group name.
ipa hbacrule-add-service --hbacsvcgroups=login loginRule
$ ipa hbacrule-add-service --hbacsvcgroups=login loginRule| Command | Description | Arguments | Source or Target Entry |
|---|---|---|---|
| hbacrule-add | Adds a new host-based access control rule. |
| |
| hbacrule-add-host | Adds a target host to the access control rule. A target host can be accessed by other servers and users in the domain. |
| Target |
| hbacrule-add-service | Adds a service type to the rule. |
| Target |
| hbacrule-add-user | Adds a user to the access control rule. The user is then able to access any allowed target host or service within the domain. |
| Source |
| hbacrule-disable | hbacrule-enable | Disables or enables a host-based access control rule. Rules can be disabled if their behavior needs to be evaluated (for troubleshooting or to test a new rule). | ruleName, which is the rule to disable or enable |