Chapter 11. Identity: Managing Services
Some services that run on a host can also belong to the IdM domain. Any service that can store a Kerberos principal or an SSL certificate (or both) can be configured as an IdM service. Adding a service to the IdM domain allows the service to request an SSL certificate or keytab from the domain. (Only the public key for the certificate is stored in the service record. The private key is local to the service.)
An IdM domain establishes a commonality between machines, with common identity information, common policies, and shared services. Any machine which belongs to a domain functions as a client of the domain, which means it uses the services that the domain provides. An IdM domain (as described in Section 1.2, “Bringing Linux Services Together”) provides three main services specifically for machines:
- DNS
- Kerberos
- Certificate management
11.1. Adding and Editing Service Entries and Keytabs
Copy linkLink copied to clipboard!
As with host entries, service entries for the host (and any other services on that host which will belong to the domain) must be added manually to the IdM domain. This is a two step process. First, the service entry must be created, and then a keytab must be created for that service which it will use to access the domain.
By default, Identity Management saves its HTTP keytab to
/etc/httpd/conf/ipa.keytab.
Note
This keytab is used for the web UI. If a key were stored in
ipa.keytab and that keytab file is deleted, the IdM web UI will stop working, because the original key would also be deleted.
Similar locations can be specified for each service that needs to be made Kerberos aware. There is no specific location that must be used, but, when using
ipa-getkeytab, you should avoid using /etc/krb5.keytab. This file should not contain service-specific keytabs; each service should have its keytab saved in a specific location and the access privileges (and possibly SELinux rules) should be configured so that only this service has access to the keytab.
11.1.1. Adding Services and Keytabs from the Web UI
Copy linkLink copied to clipboard!
- Open the Identity tab, and select the Services subtab.
- Click the Add link at the top of the services list.

- Select the service type from the drop-down menu, and give it a name.
- Select the hostname of the IdM host on which the service is running. The hostname is used to construct the full service principal name.
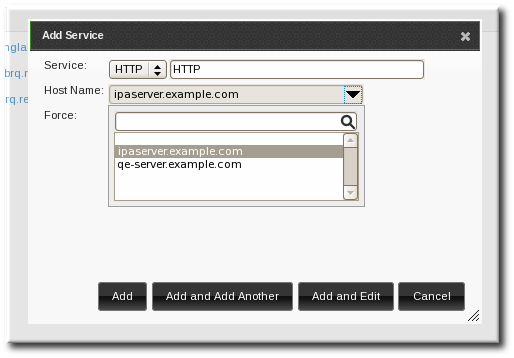
- Click the Add button to save the new service principal.
- Use the
ipa-getkeytabcommand to generate and assign the new keytab for the service principal.# ipa-getkeytab -s ipaserver.example.com -p HTTP/server.example.com -k /etc/httpd/conf/krb5.keytab -e aes256-cts
[root@ipaserver ~]# # ipa-getkeytab -s ipaserver.example.com -p HTTP/server.example.com -k /etc/httpd/conf/krb5.keytab -e aes256-ctsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The realm name is optional. The IdM server automatically appends the Kerberos realm for which it is configured. You cannot specify a different realm.
- The hostname must resolve to a DNS A record for it to work with Kerberos. You can use the
--forceflag to force the creation of a principal should this prove necessary. - The
-eargument can include a comma-separated list of encryption types to include in the keytab. This supersedes any default encryption type.
Warning
Creating a new key resets the secret for the specified principal. This means that all other keytabs for that principal are rendered invalid.
11.1.2. Adding Services and Keytabs from the Command Line
Copy linkLink copied to clipboard!
- Create the service principal. The service is recognized through a name like service/FQDN:
ipa service-add serviceName/hostname
# ipa service-add serviceName/hostnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create the service keytab file using the
ipa-getkeytabcommand. This command is run on the client in the IdM domain. (Actually, it can be run on any IdM server or client, and then the keys copied to the appropriate machine. However, it is simplest to run the command on the machine with the service being created.)The command requires the Kerberos service principal (-p), the IdM server name (-s), the file to write (-k), and the encryption method (-e). Be sure to copy the keytab to the appropriate directory for the service.For example:ipa-getkeytab -s server.example.com -p HTTP/server.example.com -k /etc/httpd/conf/krb5.keytab -e aes256-cts
# ipa-getkeytab -s server.example.com -p HTTP/server.example.com -k /etc/httpd/conf/krb5.keytab -e aes256-ctsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The realm name is optional. The IdM server automatically appends the Kerberos realm for which it is configured. You cannot specify a different realm.
- The hostname must resolve to a DNS A record for it to work with Kerberos. You can use the
--forceflag to force the creation of a principal should this prove necessary. - The
-eargument can include a comma-separated list of encryption types to include in the keytab. This supersedes any default encryption type.
Warning
Theipa-getkeytabcommand resets the secret for the specified principal. This means that all other keytabs for that principal are rendered invalid.