Ce contenu n'est pas disponible dans la langue sélectionnée.
2.2. Using authconfig
The
authconfig tool can help configure what kind of data store to use for user credentials, such as LDAP. On Red Hat Enterprise Linux, authconfig has both GUI and command-line options to configure any user data stores. The authconfig tool can configure the system to use specific services — SSSD, LDAP, NIS, or Winbind — for its user database, along with using different forms of authentication mechanisms.
Important
To configure Identity Management systems, Red Hat recommends using the
ipa-client-install utility or the realmd system instead of authconfig. The authconfig utilities are limited and substantially less flexible. For more information, see Section 2.1, “Identity Management Tools for System Authentication”.
The following three
authconfig utilities are available for configuring authentication settings:
authconfig-gtkprovides a full graphical interface.authconfigprovides a command-line interface for manual configuration.authconfig-tuiprovides a text-based UI. Note that this utility has been deprecated.
All of these configuration utilities must be run as
root.
2.2.1. Tips for Using the authconfig CLI
Copier lienLien copié sur presse-papiers!
The
authconfig command-line tool updates all of the configuration files and services required for system authentication, according to the settings passed to the script. Along with providing even more identity and authentication configuration options than can be set through the UI, the authconfig tool can also be used to create backup and kickstart files.
For a complete list of
authconfig options, check the help output and the man page.
There are some things to remember when running
authconfig:
- With every command, use either the
--updateor--testoption. One of those options is required for the command to run successfully. Using--updatewrites the configuration changes. The--testoption displays the changes but does not apply the changes to the configuration.If the--updateoption is not used, then the changes are not written to the system configuration files. - The command line can be used to update existing configuration as well as to set new configuration. Because of this, the command line does not enforce that required attributes are used with a given invocation (because the command may be updating otherwise complete settings).When editing the authentication configuration, be very careful that the configuration is complete and accurate. Changing the authentication settings to incomplete or wrong values can lock users out of the system. Use the --test option to confirm that the settings are proper before using the --update option to write them.
- Each enable option has a corresponding disable option.
2.2.2. Installing the authconfig UI
Copier lienLien copié sur presse-papiers!
The
authconfig UI is not installed by default, but it can be useful for administrators to make quick changes to the authentication configuration.
To install the UI, install the
authconfig-gtk package. This has dependencies on some common system packages, such as the authconfig command-line tool, Bash, and Python. Most of those are installed by default.
2.2.3. Launching the authconfig UI
Copier lienLien copié sur presse-papiers!
- Open the terminal and log in as root.
- Run the
system-config-authenticationcommand.
Important
Any changes take effect immediately when the
authconfig UI is closed.
There are three configuration tabs in the Authentication dialog box:
- Identity & Authentication, which configures the resource used as the identity store (the data repository where the user IDs and corresponding credentials are stored).
- Advanced Options, which configures authentication methods other than passwords or certificates, like smart cards and fingerprint.
- Password Options, which configures password authentication methods.
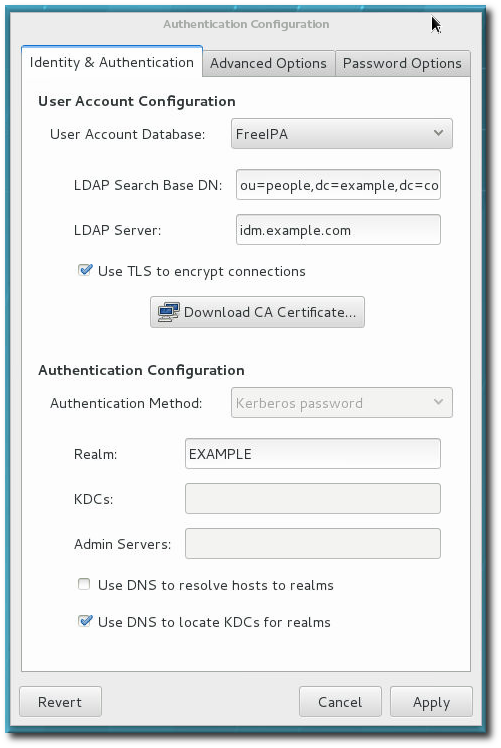
Figure 2.1. authconfig Window
2.2.4. Testing Authentication Settings
Copier lienLien copié sur presse-papiers!
It is critical that authentication is fully and properly configured. Otherwise all users (even root) could be locked out of the system, or some users blocked.
The
--test option prints all of the authentication configuration for the system, for every possible identity and authentication mechanism. This shows both the settings for what is enabled and what areas are disabled.
The
test option can be run by itself to show the full, current configuration or it can be used with an authconfig command to show how the configuration will be changed (without actually changing it). This can be very useful in verifying that the proposed authentication settings are complete and correct.
2.2.5. Saving and Restoring Configuration Using authconfig
Copier lienLien copié sur presse-papiers!
Changing authentication settings can be problematic. Improperly changing the configuration can wrongly exclude users who should have access, can cause connections to the identity store to fail, or can even lock all access to a system.
Before editing the authentication configuration, it is strongly recommended that administrators take a backup of all configuration files. This is done with the
--savebackup option.
authconfig --savebackup=/backups/authconfigbackup20200701
[root@server ~]# authconfig --savebackup=/backups/authconfigbackup20200701
The authentication configuration can be restored to any previous saved version using the
--restorebackup option, with the name of the backup to use.
authconfig --restorebackup=/backups/authconfigbackup20200701
[root@server ~]# authconfig --restorebackup=/backups/authconfigbackup20200701
The
authconfig command saves an automatic backup every time the configuration is altered. It is possible to restore the last backup using the --restorelastbackup option.
authconfig --restorelastbackup
[root@server ~]# authconfig --restorelastbackup