Ce contenu n'est pas disponible dans la langue sélectionnée.
3.2. LDAP and IdM
Both standard LDAP directories (such as OpenLDAP and Red Hat Directory Server) can be used as LDAP identity providers. Additionally, older IdM versions and FreeIPA can be configured as identity providers by configuring them as LDAP providers with a related Kerberos server.
Either the openldap-clients package or the sssd package is used to configure an LDAP server for the user database. Both packages are installed by default.
3.2.1. Configuring LDAP Authentication from the UI
Copier lienLien copié sur presse-papiers!
- Open the
authconfigUI, as in Section 2.2.3, “Launching the authconfig UI”. - Select in the User Account Database drop-down menu.
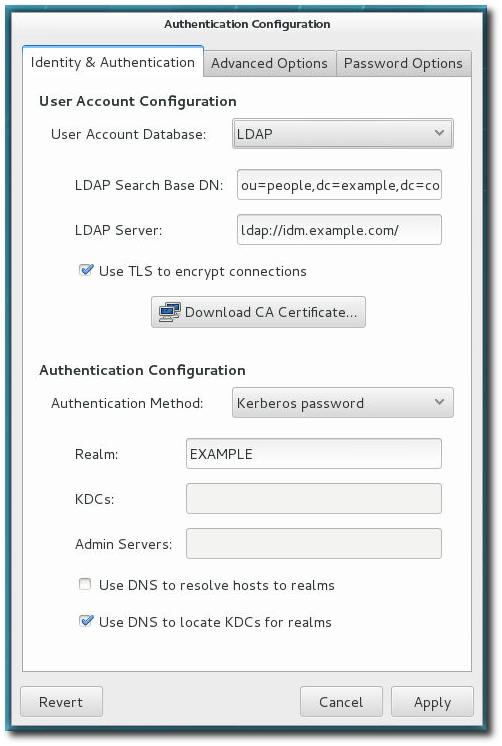
- Set the information that is required to connect to the LDAP server.
- LDAP Search Base DN gives the root suffix or distinguished name (DN) for the user directory. All of the user entries used for identity or authentication exist below this parent entry. For example,
ou=people,dc=example,dc=com.This field is optional. If it is not specified, the System Security Services Daemon (SSSD) attempts to detect the search base using thenamingContextsanddefaultNamingContextattributes in the LDAP server's configuration entry. - LDAP Server gives the URL of the LDAP server. This usually requires both the host name and port number of the LDAP server, such as
ldap://ldap.example.com:389.Entering the secure protocol by using a URL starting withldaps://enables the button, which retrieves the issuing CA certificate for the LDAP server from whatever certificate authority issued it. The CA certificate must be in the privacy enhanced mail (PEM) format. - If you use a insecure standard port connection (URL starting with
ldap://), you can use the Use TLS to encrypt connections check box to encrypt communication with the LDAP server usingSTARTTLS. Selecting this check box also enables the button.Note
You do not need to select the Use TLS to encrypt connections check box if the server URL uses the LDAPS (LDAP over SSL) secure protocol as the communication is already encrypted.
- Select the authentication method. LDAP allows simple password authentication or Kerberos authentication.Using Kerberos is described in Section 4.3.1, “Configuring Kerberos Authentication from the UI”.The LDAP password option uses PAM applications to use LDAP authentication. This option requires a secure connection to be set either by using LDAPS or TLS to connect to the LDAP server.
3.2.2. Configuring LDAP User Stores from the Command Line
Copier lienLien copié sur presse-papiers!
To use an LDAP identity store, use the
--enableldap. To use LDAP as the authentication source, use --enableldapauth and then the requisite connection information, like the LDAP server name, base DN for the user suffix, and (optionally) whether to use TLS. The authconfig command also has options to enable or disable RFC 2307bis schema for user entries, which is not possible through the authconfig UI.
Be sure to use the full LDAP URL, including the protocol (
ldap or ldaps) and the port number. Do not use a secure LDAP URL (ldaps) with the --enableldaptls option.
authconfig --enableldap --enableldapauth --ldapserver=ldap://ldap.example.com:389,ldap://ldap2.example.com:389 --ldapbasedn="ou=people,dc=example,dc=com" --enableldaptls --ldaploadcacert=https://ca.server.example.com/caCert.crt --update
authconfig --enableldap --enableldapauth --ldapserver=ldap://ldap.example.com:389,ldap://ldap2.example.com:389 --ldapbasedn="ou=people,dc=example,dc=com" --enableldaptls --ldaploadcacert=https://ca.server.example.com/caCert.crt --update
Instead of using
--ldapauth for LDAP password authentication, it is possible to use Kerberos with the LDAP user store. These options are described in Section 4.3.2, “Configuring Kerberos Authentication from the Command Line”.