このコンテンツは選択した言語では利用できません。
10.3. Roles and LDAP User Groups
10.3.1. About Group Authorization
リンクのコピーリンクがクリップボードにコピーされました!
Many LDAP directories already contain organizational groups with users who will need to access resources in JBoss ON. Configuring JBoss ON to connect to these directories allows JBoss ON to assign LDAP groups to roles and then pull in those member lists dynamically, so the roles are populated with pre-existing member lists. All of the LDAP users automatically inherit the permissions of that role.
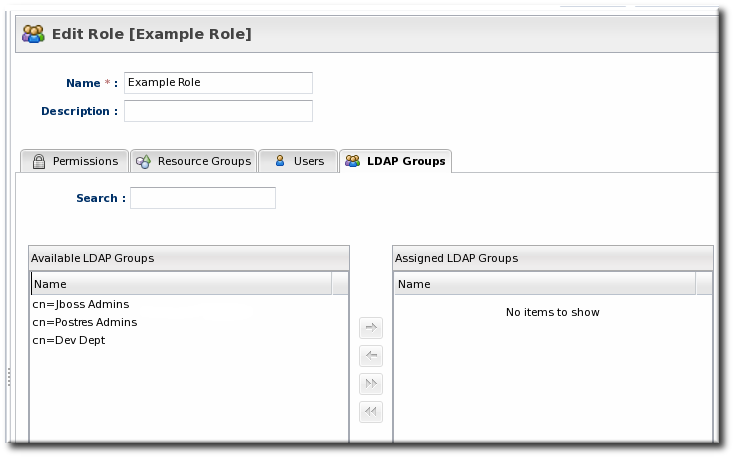
In the role details page, these LDAP user groups are separated from the resource groups, so it's easy to distinguish which types of group are being added to the role.
Figure 10.2. Groups Assigned to a Role
JBoss ON determines what LDAP groups a user belongs to with a simple search. Whenever a user logs into JBoss ON and an LDAP connection is configured, JBoss ON maps that JBoss ON username to a user entry in the LDAP directory server. The specific LDAP distinguished name (DN) for the user is used as part of a search to find matching member attributes in LDAP group entries. That is, the LDAP server can check the member lists in group entries to see what groups the person with that DN belongs to.
For LDAP groups to be added to roles, three things are required:
- An LDAP directory server connection has to be configured.
- There has to be an LDAP attribute given to search for group entries.For Active Directory, this is generally the
groupobject class. For Red Hat Directory Server, this is generallygroupOfUniqueNames. Other standard object classes are available, and it is also possible to use a custom, even JBoss ON-specific, object class. - There has to be an LDAP attribute given to identify members in the group.Common member attributes are
memberanduniqueMember.
JBoss ON constructs an LDAP search based on the group object class and member attribute in the server configuration, plus the DN of the user given when the user logs in.
(&(group_filter)(member_attribute=user_DN))
(&(group_filter)(member_attribute=user_DN))
For example, this looks for the
member attribute on an Active Directory group:
ldapsearch -h server.example.com -x -D "cn=Administrator,cn=Users,dc=example,dc=com" -W -b "dc=example,dc=com" -x '(&(objectclass=group)(member=CN=John Smith,CN=Users,DC=example,DC=com))'
ldapsearch -h server.example.com -x -D "cn=Administrator,cn=Users,dc=example,dc=com" -W -b "dc=example,dc=com" -x '(&(objectclass=group)(member=CN=John Smith,CN=Users,DC=example,DC=com))'
Red Hat Directory Server uses the
uniqueMember attribute on groupOfUniqueNames groups more commonly than member and group. For example:
/usr/lib64/mozldap6/ldapsearch -D "cn=directory manager" -w secret -p 389 -h server.example.com -b "ou=People,dc=example,dc=com" -s sub "(&(objectclass=groupOfUniqueNames)(uniqueMember=uid=jsmith,ou=People,dc=example,dc=com))"
/usr/lib64/mozldap6/ldapsearch -D "cn=directory manager" -w secret -p 389 -h server.example.com -b "ou=People,dc=example,dc=com" -s sub "(&(objectclass=groupOfUniqueNames)(uniqueMember=uid=jsmith,ou=People,dc=example,dc=com))"
This search returns a list of all groups to which the user is a member. If any of these LDAP groups is assigned to a JBoss ON role, then that user is also automatically a member of that JBoss ON role.
Note
Using custom LDAP group object classes can allow you to be very specific about which groups to use for JBoss ON roles.
10.3.2. Associating LDAP User Groups to Roles
リンクのコピーリンクがクリップボードにコピーされました!
Section 10.2.3, “Configuring LDAP User Authentication” describes how an LDAP directory server can be used to authenticate users to JBoss ON. Any time a user attempts to log in, that request — with the username and password — is simply forwarded to the specified LDAP directory server to see if the credentials are correct.
Members of LDAP groups can be pulled in, automatically, as members of JBoss ON roles. The LDAP group is associated with a JBoss ON role and then the group members are authorized to do whatever the JBoss ON role is configured to allow. Any changes made in the LDAP group members are automatically reflected in JBoss ON, without having to edit the JBoss ON role.
- In the top menu, click the Administration tab.
- In the menu table on the left, select the item.
- Jump to the LDAP Configuration Properties area.
- Set up the LDAP connections, as described in Section 10.2.3, “Configuring LDAP User Authentication”. It is not required that the LDAP directory be used as the identity store in order to configure LDAP authorization, but it is recommended.
- Set the parameters to use for the server to use to search for LDAP groups and their members.The search filter that JBoss ON constructs looks like this:
(&(group_filter)(member_attribute=user_DN))
(&(group_filter)(member_attribute=user_DN))Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The Group Search Filter field sets how to search for the group entry. This is usually done by specifying the type of group to search for through its object class:
(objectclass=groupOfUniqueNames)
(objectclass=groupOfUniqueNames)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The Group Member Filter field gives the attribute that the specified group type uses to store member distinguished names. For example:
uniqueMember
uniqueMemberCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The user_DN is dynamically supplied by JBoss ON when a user logs into the UI. - Save the LDAP settings.