This documentation is for a release that is no longer maintained
See documentation for the latest supported version 3 or the latest supported version 4.이 콘텐츠는 선택한 언어로 제공되지 않습니다.
Chapter 7. Scanning pods for vulnerabilities
Using the Container Security Operator (CSO), you can access vulnerability scan results from the OpenShift Container Platform web console for container images used in active pods on the cluster. The CSO:
- Watches containers associated with pods on all or specified namespaces
- Queries the container registry where the containers came from for vulnerability information, provided an image’s registry is running image scanning (such as Quay.io or a Red Hat Quay registry with Clair scanning)
-
Exposes vulnerabilities via the
ImageManifestVulnobject in the Kubernetes API
Using the instructions here, the CSO is installed in the openshift-operators namespace, so it is available to all namespaces on your OpenShift cluster.
7.1. Running the Container Security Operator
You can start the Container Security Operator from the OpenShift Container Platform web console by selecting and installing that Operator from the Operator Hub, as described here.
Prerequisites
- Have administrator privileges to the OpenShift Container Platform cluster
- Have containers that come from a Red Hat Quay or Quay.io registry running on your cluster
Procedure
-
Navigate to Operators
OperatorHub and select Security. - Select the Container Security Operator, then select Install to go to the Create Operator Subscription page.
- Check the settings. All namespaces and automatic approval strategy are selected, by default.
- Select Install. The Container Security Operator appears after a few moments on the Installed Operators screen.
Optionally, you can add custom certificates to the CSO. In this example, create a certificate named
quay.crtin the current directory. Then run the following command to add the cert to the CSO:oc create secret generic container-security-operator-extra-certs --from-file=quay.crt -n openshift-operators
$ oc create secret generic container-security-operator-extra-certs --from-file=quay.crt -n openshift-operatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - If you added a custom certificate, restart the Operator pod for the new certs to take effect.
Open the OpenShift Dashboard (
HomeOverview). A link to Quay Image Security appears under the status section, with a listing of the number of vulnerabilities found so far. Select the link to see a Quay Image Security breakdown, as shown in the following figure: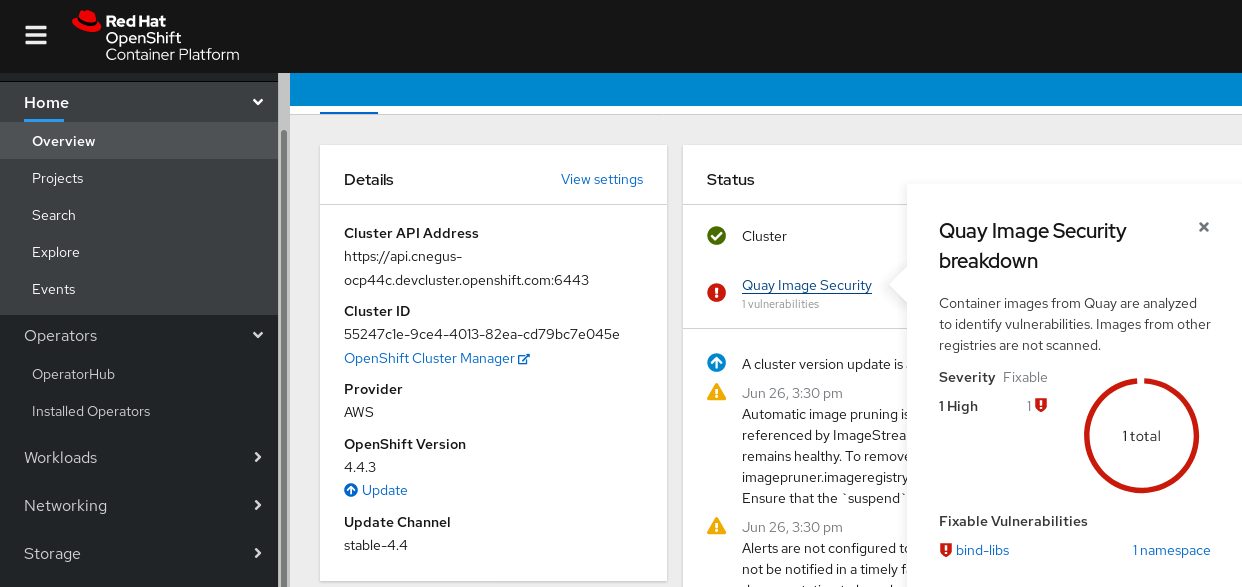
You can do one of two things at this point to follow up on any detected vulnerabilities:
Select the link to the vulnerability. You are taken to the container registry that the container came from, where you can see information about the vulnerability. The following figure shows an example of detected vulnerabilities from a Quay.io registry:
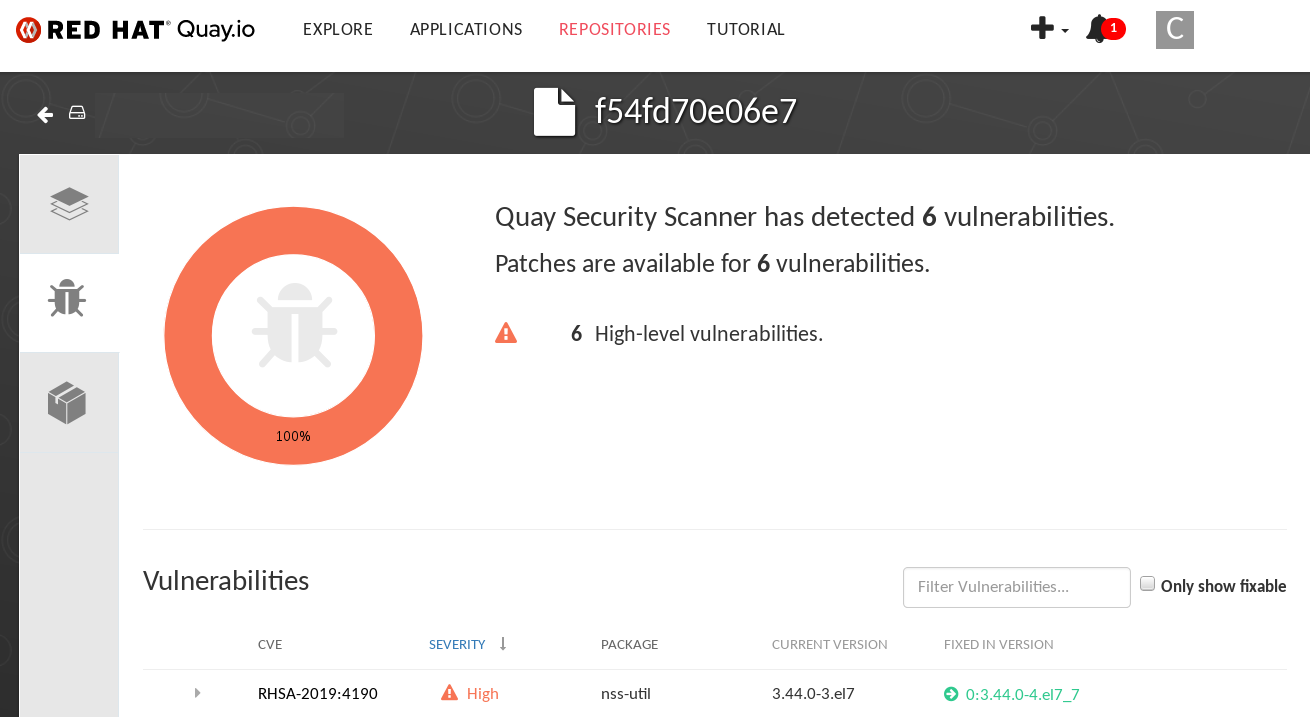
Select the namespaces link to go to the ImageManifestVuln screen, where you can see the name of the selected image and all namespaces where that image is running. The following figure indicates that a particular vulnerable image is running in the
quay-enterprisenamespace: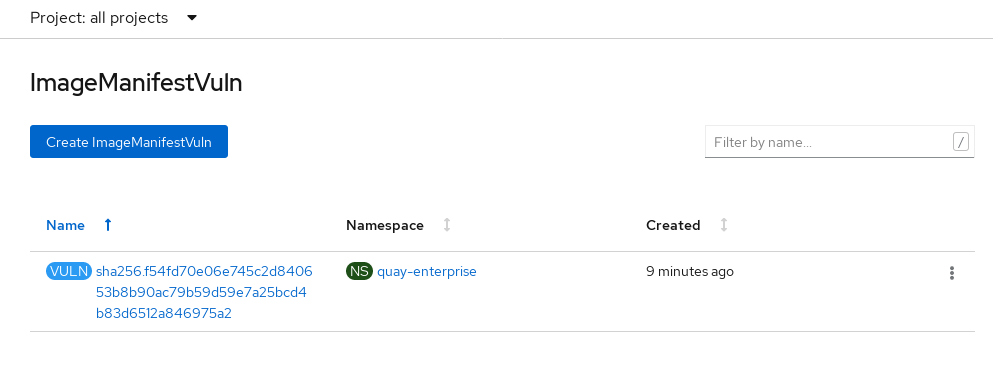
At this point, you know what images are vulnerable, what you need to do to fix those vulnerabilities, and every namespace that the image was run in. So you can:
- Alert anyone running the image that they need to correct the vulnerability
- Stop the images from running by deleting the deployment or other object that started the pod that the image is in
Note that if you do delete the pod, it may take several minutes for the vulnerability to reset on the dashboard.
7.2. Querying image vulnerabilities from the CLI
Using the oc command, you can display information about vulnerabilities detected by the Container Security Operator.
Prerequisites
- Be running the Container Security Operator on your OpenShift Container Platform instance
Procedure
To query for detected container image vulnerabilities, type:
oc get vuln --all-namespaces
$ oc get vuln --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAMESPACE NAME AGE default sha256.ca90... 6m56s skynet sha256.ca90... 9m37s
NAMESPACE NAME AGE default sha256.ca90... 6m56s skynet sha256.ca90... 9m37sCopy to Clipboard Copied! Toggle word wrap Toggle overflow To display details for a particular vulnerability, provide the vulnerability name and its namespace to the
oc describecommand. This example shows an active container whose image includes an RPM package with a vulnerability:oc describe vuln --namespace mynamespace sha256.ac50e3752...
$ oc describe vuln --namespace mynamespace sha256.ac50e3752...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow