此内容没有您所选择的语言版本。
9.10. Managing User and Group Schema
When a user entry is created, it is automatically assigned certain LDAP object classes which, in turn, make available certain attributes. LDAP attributes are the way that information is stored in the directory. (This is discussed in detail in the Directory Server Deployment Guide and the Directory Server Schema Reference.)
| Description | Object Classes | |||||
|---|---|---|---|---|---|---|
| IdM object classes |
| |||||
| Person object classes |
| |||||
| Kerberos object classes |
| |||||
| Managed entries (template) object classes | mepOriginEntry |
A number of attributes are available to user entries. Some are set manually and some are set based on defaults if a specific value is not set. There is also an option to add any attributes available in the object classes in Table 9.1, “Default Identity Management User Object Classes”, even if there is not a UI or command-line argument for that attribute. Additionally, the values generated or used by the default attributes can be configured, as in Section 9.10.4, “Specifying Default User and Group Attributes”.
| UI Field | Command-Line Option | Required, Optional, or Default[a] |
|---|---|---|
| User login | username | Required |
| First name | --first | Required |
| Last name | --last | Required |
| Full name | --cn | Optional |
| Display name | --displayname | Optional |
| Initials | --initials | Default |
| Home directory | --homedir | Default |
| GECOS field | --gecos | Default |
| Shell | --shell | Default |
| Kerberos principal | --principal | Default |
| Email address | Optional | |
| Password | --password [b] | Optional |
| User ID number[c] | --uid | Default |
| Group ID number[c] | --gidnumber | Default |
| Street address | --street | Optional |
| City | --city | Optional |
| State/Province | --state | Optional |
| Zip code | --postalcode | Optional |
| Telephone number | --phone | Optional |
| Mobile telephone number | --mobile | Optional |
| Pager number | --pager | Optional |
| Fax number | --fax | Optional |
| Organizational unit | --orgunit | Optional |
| Job title | --title | Optional |
| Manager | --manager | Optional |
| Car license | --carlicense | Optional |
| --noprivate | Optional | |
| SSH Keys | --sshpubkey | Optional |
| Additional attributes | --addattr | Optional |
[a]
Required attributes must be set for every entry. Optional attributes may be set, while default attributes are automatically added with a pre-defined value unless a specific value is given.
[b]
The script prompts for the new password, rather than accepting a value with the argument.
[c]
When a user is created without specifying a UID number, then the user account is automatically assigned an ID number that is next available in the server or replica range. (Number ranges are described more in Section 9.9, “Managing Unique UID and GID Number Assignments”.) This means that a user always has a unique number for its UID number and, if configured, for its private group.
If a number is manually assigned to a user entry, the server does not validate that the uidNumber is unique. It will allow duplicate IDs; this is expected (though discouraged) behavior for POSIX entries.
If two entries are assigned the same ID number, only the first entry is returned in a search for that ID number. However, both entries will be returned in searches for other attributes or with ipa user-find --all.
| ||
9.10.1. About Changing the Default User and Group Schema
复制链接链接已复制到粘贴板!
It is possible to add or change the object classes and attributes used for user and group entries (Section 9.10, “Managing User and Group Schema”).
The IdM configuration provides some validation when object classes are changed:
- All of the object classes and their specified attributes must be known to the LDAP server.
- All default attributes that are configured for the entry must be supported by the configured object classes.
There are limits to the IdM schema validation, however. Most important, the IdM server does not check that the defined user or group object classes contain all of the required object classes for IdM entries. For example, all IdM entries require the
ipaobject object class. However, when the user or group schema is changed, the server does not check to make sure that this object class is included; if the object class is accidentally deleted, then future entry add operations will fail.
Also, all object class changes are atomic, not incremental. The entire list of default object classes has to be defined every time there is a change. For example, a company may create a custom object class to store employee information like birthdays and employment start dates. The administrator cannot simply add the custom object class to the list; he must set the entire list of current default object classes plus the new object class. The existing default object classes must always be included when the configuration is updated. Otherwise, the current settings will be overwritten, which causes serious performance problems.
User and group accounts are created with a pre-defined set of LDAP object classes applied to the entry. Any attributes which belong to the object class can be added to the user entry.
While the standard and IdM-specific LDAP object classes will cover most deployment scenarios, administrators may have custom object classes with custom attributes which should be applied to user entries.
9.10.2.1. From the Web UI
复制链接链接已复制到粘贴板!
- Add all of the custom schema elements to the 389 Directory Server instance used by Identity Management. Adding schema elements is described in the schema chapter of the Directory Server Administrator's Guide.
- Open the IPA Server tab.
- Select the Configuration subtab.
- Scroll to the User Options area.
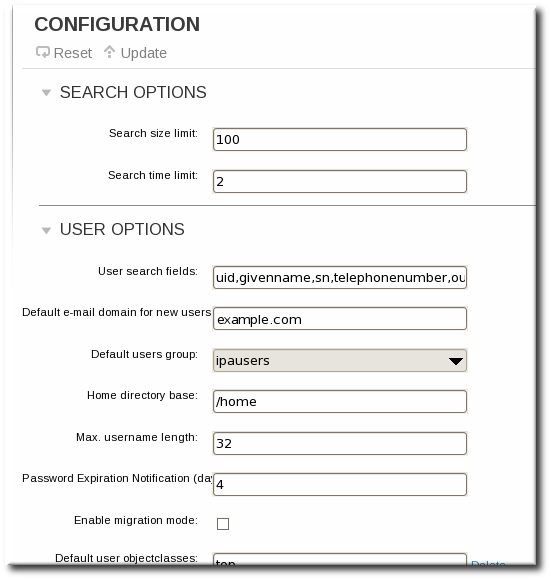
- At the bottom of the users area, click the Add link to add a new field for another object class.
Important
Always include the existing default object classes when the configuration is updated. Otherwise, the current settings will be overwritten. If any object classes required by Identity Management are not included, then subsequent attempts to add an entry will fail with object class violations.
- When the changes are complete, click the Update link at the top of the Configuration page.
9.10.2.2. From the Command Line
复制链接链接已复制到粘贴板!
- Add all of the custom schema elements to the 389 Directory Server instance used by Identity Management. Adding schema elements is described in the schema chapter of the Directory Server Administrator's Guide.
- Add the new object class to the list of object classes added to entries. The option for user object classes is
--userobjectclasses.Important
Always include the existing default object classes when the configuration is updated. Otherwise, the current settings will be overwritten. If any object classes required by Identity Management are not included, then subsequent attempts to add an entry will fail with object class violations.For example:ipa config-mod --userobjectclasses=top,person,organizationalperson,inetorgperson,inetuser,posixaccount, krbprincipalaux,krbticketpolicyaux,ipaobject,ipasshuser,employeeinfo
[bjensen@server ~]$ ipa config-mod --userobjectclasses=top,person,organizationalperson,inetorgperson,inetuser,posixaccount, krbprincipalaux,krbticketpolicyaux,ipaobject,ipasshuser,employeeinfoCopy to Clipboard Copied! Toggle word wrap Toggle overflow
As with user entries, administrators may have custom object classes with custom attributes which should be applied to group entries. These can be added automatically by adding the object classes to the IdM server configuration.
9.10.3.1. From the Web UI
复制链接链接已复制到粘贴板!
- Add all of the custom schema elements to the 389 Directory Server instance used by Identity Management. Adding schema elements is described in the schema chapter of the Directory Server Administrator's Guide.
- Open the IPA Server tab.
- Select the Configuration subtab.
- Scroll to the Group Options area.
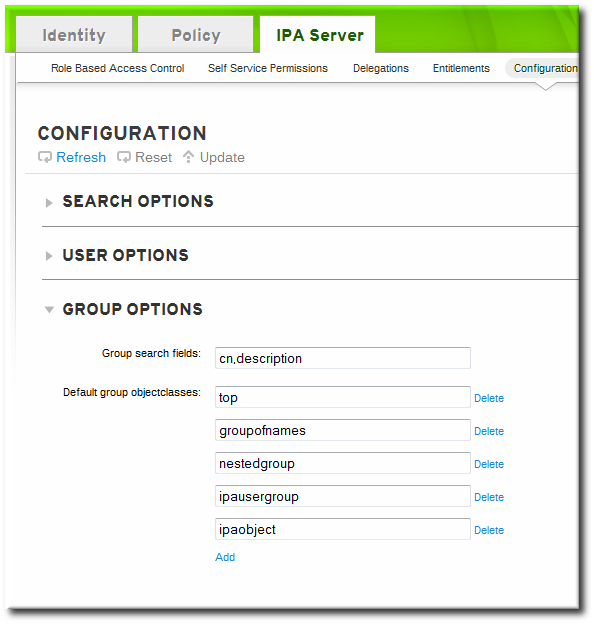
- Click the Add link to add a new field for another object class.
Important
Always include the existing default object classes when the configuration is updated. Otherwise, the current settings will be overwritten. If any object classes required by Identity Management are not included, then subsequent attempts to add an entry will fail with object class violations. - When the changes are complete, click the Update link at the top of the Configuration page.
9.10.3.2. From the Command Line
复制链接链接已复制到粘贴板!
- Add all of the custom schema elements to the 389 Directory Server instance used by Identity Management. Adding schema elements is described in the schema chapter of the Directory Server Administrator's Guide.
- Add the new object class to the list of object classes added to entries. The option for group object classes is
--groupobjectclasses.Important
Always include the existing default object classes when the configuration is updated. Otherwise, the current settings will be overwritten. If any object classes required by Identity Management are not included, then subsequent attempts to add an entry will fail with object class violations.For example:ipa config-mod --groupobjectclasses=top,groupofnames,nestedgroup,ipausergroup,ipaobject,ipasshuser,employeegroup
[bjensen@server ~]$ ipa config-mod --groupobjectclasses=top,groupofnames,nestedgroup,ipausergroup,ipaobject,ipasshuser,employeegroupCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.10.4. Specifying Default User and Group Attributes
复制链接链接已复制到粘贴板!
Identity Management uses a template when it creates new entries.
For users, the template is very specific. Identity Management uses default values for several core attributes for IdM user accounts. These defaults can define actual values for user account attributes (such as the home directory location) or it can define the format of attribute values, such as the username length. These settings also define the object classes assigned to users.
For groups, the template only defines the assigned object classes.
These default definitions are all contained in a single configuration entry for the IdM server,
cn=ipaconfig,cn=etc,dc=example,dc=com.
The configuration can be changed using the
ipa config-mod command.
| Field | Command-Line Option | Descriptions |
|---|---|---|
| Maximum username length | --maxusername | Sets the maximum number of characters for usernames. The default value is eight. |
| Root for home directories | --homedirectory | Sets the default directory to use for user home directories. The default value is /home. |
| Default shell | --defaultshell | Sets the default shell to use for users. The default value is /bin/sh. |
| Default user group | --defaultgroup | Sets the default group to which all newly created accounts are added. The default value is ipausers, which is automatically created during the IdM server installation process. |
| Default e-mail domain | --emaildomain | Sets the email domain to use to create email addresses based on the new accounts. The default is the IdM server domain. |
| Search time limit | --searchtimelimit | Sets the maximum amount of time, in seconds, to spend on a search before the server returns results. |
| Search size limit | --searchrecordslimit | Sets the maximum number of records to return in a search. |
| User search fields | --usersearch | Sets the fields in a user entry that can be used as a search string. Any attribute listed has an index kept for that attribute, so setting too many attributes could affect server performance. |
| Group search fields | --groupsearch | Sets the fields in a group entry that can be used as a search string. |
| Certificate subject base | Sets the base DN to use when creating subject DNs for client certificates. This is configured when the server is set up. | |
| Default user object classes | --userobjectclasses | Sets a list of object classes that are used to create IdM user accounts. |
| Default group object classes | --groupobjectclasses | Sets a list of object classes that are used to create IdM group accounts. |
| Password expiration notification | --pwdexpnotify | Sets how long, in days, before a password expires for the server to send a notification. |
| Password plug-in features | Sets the format of passwords that are allowed for users. |
9.10.4.1. Viewing Attributes from the Web UI
复制链接链接已复制到粘贴板!
- Open the IPA Server tab.
- Select the Configuration subtab.
- The complete configuration entry is shown in three sections, one for all search limits, one for user templates, and one for group templates.

9.10.4.2. Viewing Attributes from the Command Line
复制链接链接已复制到粘贴板!
The
config-show command shows the current configuration which applies to all new user accounts. By default, only the most common attributes are displayed; use the --all option to show the complete configuration.