Este contenido no está disponible en el idioma seleccionado.
10.3.6. Establishing a Bond Connection
You can use NetworkManager to create a Bond from two or more Wired or Infiniband connections. It is not necessary to create the connections to be bonded first. They can be configured as part of the process to configure the bond. You must have the MAC addresses of the interfaces available in order to complete the configuration process.
Note
NetworkManager support for bonding must be enabled by means of the
NM_BOND_VLAN_ENABLED directive and then NetworkManager must be restarted. See Section 11.2.1, “Ethernet Interfaces” for an explanation of NM_CONTROLLED and the NM_BOND_VLAN_ENABLED directive. See Section 12.3.4, “Restarting a Service” for an explanation of restarting a service such as NetworkManager from the command line. Alternatively, for a graphical tool see Section 12.2.1, “Using the Service Configuration Utility”.
Procedure 10.9. Adding a New Bond Connection
You can configure a Bond connection by opening the Network Connections window, clicking , and selecting Bond from the list.
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Click the button to open the selection list. Select Bond and then click . The Editing Bond connection 1 window appears.
- On the Bond tab, click and select the type of interface you want to use with the bond connection. Click the button. Note that the dialog to select the slave type only comes up when you create the first slave; after that, it will automatically use that same type for all further slaves.
- The Editing bond0 slave 1 window appears. Fill in the MAC address of the first interface to be bonded. The first slave's MAC address will be used as the MAC address for the bond interface. If required, enter a clone MAC address to be used as the bond's MAC address. Click the button.
- The Authenticate window appears. Enter the
rootpassword to continue. Click the button. - The name of the bonded slave appears in the Bonded Connections window. Click the button to add further slave connections.
- Review and confirm the settings and then click the Apply button.
- Edit the bond-specific settings by referring to the section called “Configuring the Bond Tab” below.
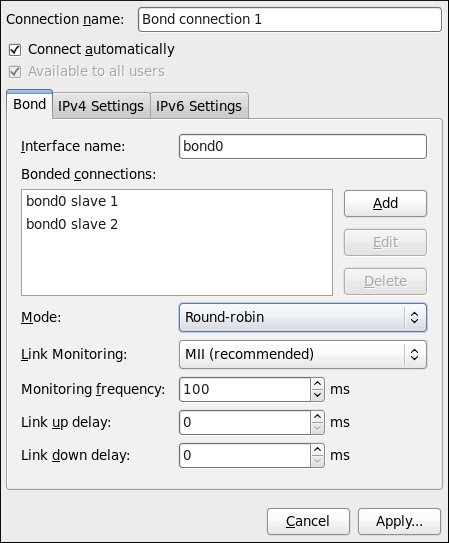
Figure 10.14. Editing the newly created Bond connection 1
Procedure 10.10. Editing an Existing Bond Connection
Follow these steps to edit an existing bond connection.
- Right-click on the NetworkManager applet icon in the Notification Area and click Edit Connections. The Network Connections window appears.
- Select the connection you want to edit and click the Edit button.
- Select the Bond tab.
- Configure the connection name, auto-connect behavior, and availability settings.Three settings in the Editing dialog are common to all connection types:
- Connection name — Enter a descriptive name for your network connection. This name will be used to list this connection in the Bond section of the Network Connections window.
- Connect automatically — Select this box if you want NetworkManager to auto-connect to this connection when it is available. See Section 10.2.3, “Connecting to a Network Automatically” for more information.
- Available to all users — Select this box to create a connection available to all users on the system. Changing this setting may require
rootprivileges. See Section 10.2.4, “User and System Connections” for details.
- Edit the bond-specific settings by referring to the section called “Configuring the Bond Tab” below.
Saving Your New (or Modified) Connection and Making Further Configurations
Once you have finished editing your bond connection, click the button to save your customized configuration. Given a correct configuration, you can connect to your new or customized connection by selecting it from the NetworkManager Notification Area applet. See Section 10.2.1, “Connecting to a Network” for information on using your new or altered connection.
You can further configure an existing connection by selecting it in the Network Connections window and clicking Edit to return to the Editing dialog.
Then, to configure:
- IPv4 settings for the connection, click the IPv4 Settings tab and proceed to Section 10.3.9.4, “Configuring IPv4 Settings”; or,
- IPv6 settings for the connection, click the IPv6 Settings tab and proceed to Section 10.3.9.5, “Configuring IPv6 Settings”.
Configuring the Bond Tab
If you have already added a new bond connection (see Procedure 10.9, “Adding a New Bond Connection” for instructions), you can edit the Bond tab to set the load sharing mode and the type of link monitoring to use to detect failures of a slave connection.
- Mode
- The mode that is used to share traffic over the slave connections which make up the bond. The default is Round-robin. Other load sharing modes, such as
802.3ad, can be selected by means of the drop-down list. - Link Monitoring
- The method of monitoring the slaves ability to carry network traffic.
The following modes of load sharing are selectable from the Mode drop-down list:
- Round-robin
- Sets a round-robin policy for fault tolerance and load balancing. Transmissions are received and sent out sequentially on each bonded slave interface beginning with the first one available. This mode might not work behind a bridge with virtual machines without additional switch configuration.
- Active backup
- Sets an active-backup policy for fault tolerance. Transmissions are received and sent out via the first available bonded slave interface. Another bonded slave interface is only used if the active bonded slave interface fails. Note that this is the only mode available for bonds of InfiniBand devices.
- XOR
- Sets an XOR (exclusive-or) policy. Transmissions are based on the selected hash policy. The default is to derive a hash by XOR of the source and destination MAC addresses multiplied by the modulo of the number of slave interfaces. In this mode traffic destined for specific peers will always be sent over the same interface. As the destination is determined by the MAC addresses this method works best for traffic to peers on the same link or local network. If traffic has to pass through a single router then this mode of traffic balancing will be suboptimal.
- Broadcast
- Sets a broadcast policy for fault tolerance. All transmissions are sent on all slave interfaces. This mode might not work behind a bridge with virtual machines without additional switch configuration.
- 802.3ad
- Sets an IEEE
802.3addynamic link aggregation policy. Creates aggregation groups that share the same speed and duplex settings. Transmits and receives on all slaves in the active aggregator. Requires a network switch that is802.3adcompliant. - Adaptive transmit load balancing
- Sets an adaptive Transmit Load Balancing (TLB) policy for fault tolerance and load balancing. The outgoing traffic is distributed according to the current load on each slave interface. Incoming traffic is received by the current slave. If the receiving slave fails, another slave takes over the MAC address of the failed slave. This mode is only suitable for local addresses known to the kernel bonding module and therefore cannot be used behind a bridge with virtual machines.
- Adaptive load balancing
- Sets an Adaptive Load Balancing (ALB) policy for fault tolerance and load balancing. Includes transmit and receive load balancing for
IPv4traffic. Receive load balancing is achieved throughARPnegotiation. This mode is only suitable for local addresses known to the kernel bonding module and therefore cannot be used behind a bridge with virtual machines.
The following types of link monitoring can be selected from the Link Monitoring drop-down list. It is a good idea to test which channel bonding module parameters work best for your bonded interfaces.
- MII (Media Independent Interface)
- The state of the carrier wave of the interface is monitored. This can be done by querying the driver, by querying MII registers directly, or by using ethtool to query the device. Three options are available:
- Monitoring Frequency
- The time interval, in milliseconds, between querying the driver or MII registers.
- Link up delay
- The time in milliseconds to wait before attempting to use a link that has been reported as up. This delay can be used if some gratuitous
ARPrequests are lost in the period immediately following the link being reported as “up”. This can happen during switch initialization for example. - Link down delay
- The time in milliseconds to wait before changing to another link when a previously active link has been reported as “down”. This delay can be used if an attached switch takes a relatively long time to change to backup mode.
- ARP
- The address resolution protocol (
ARP) is used to probe one or more peers to determine how well the link-layer connections are working. It is dependent on the device driver providing the transmit start time and the last receive time.Two options are available:- Monitoring Frequency
- The time interval, in milliseconds, between sending
ARPrequests. - ARP targets
- A comma separated list of
IPaddresses to sendARPrequests to.