Questo contenuto non è disponibile nella lingua selezionata.
50.2.6. Enabling or Disabling Enforcement
You can enable and disable SELinux enforcement at runtime or configure it to start in the correct mode at boot time, using the command line or GUI. SELinux can operate in one of three modes: disabled
, meaning not enabled in the kernel; permissive
, meaning SELinux is running and logging but not controlling permissions; or enforcing
, meaning SELinux is running and enforcing policy.
Use the
setenforce command to change between permissive and enforcing modes at runtime. Use setenforce 0 to enter permissive mode; use setenforce 1 to enter enforcing mode.
The
sestatus command displays the current mode and the mode from the configuration file referenced during boot:
sestatus | grep -i mode Current mode: permissive Mode from config file: permissive
~]# sestatus | grep -i mode
Current mode: permissive
Mode from config file: permissive
Note that changing the runtime enforcement does not affect the boot time configuration:
setenforce 1 sestatus | grep -i mode Current mode: enforcing Mode from config file: permissive
~]# setenforce 1
~]# sestatus | grep -i mode
Current mode: enforcing
Mode from config file: permissive
You can also disable enforcing mode for a single daemon. For example, if you are trying to troubleshoot the
named daemon and SELinux, you can turn off enforcing for just that daemon.
Use the
getsebool command to get the current status of the boolean:
getsebool named_disable_trans named_disable_trans --> off
~]# getsebool named_disable_trans
named_disable_trans --> off
Use the following command to disable enforcing mode for this daemon:
setsebool named_disable_trans 1 getsebool named_disable_trans named_disable_trans --> on
~]# setsebool named_disable_trans 1
~]# getsebool named_disable_trans
named_disable_trans --> onNote
This sets the runtime value only. Use the
-P option to make the change persistent across reboots.
Any *_disable_trans booleans that are set to "on" invoke the conditional that prevents the process from transitioning to the domain on execution.
Use the following command to find which of these booleans are set:
getsebool -a | grep disable.*on httpd_disable_trans=1 mysqld_disable_trans=1 ntpd_disable_trans=1
~]# getsebool -a | grep disable.*on
httpd_disable_trans=1
mysqld_disable_trans=1
ntpd_disable_trans=1
You can set any number of boolean values using the
setsebool command:
setsebool -P httpd_disable_trans=1 mysqld_disable_trans=1 ntpd_disable_trans=1
setsebool -P httpd_disable_trans=1 mysqld_disable_trans=1 ntpd_disable_trans=1
You can also use
togglesebool <boolean_name> to change the value of a specific boolean:
getsebool httpd_disable_trans httpd_disable_trans --> off togglesebool httpd_disable_trans httpd_disable_trans: active
~]# getsebool httpd_disable_trans
httpd_disable_trans --> off
~]# togglesebool httpd_disable_trans
httpd_disable_trans: active
You can configure all of these settings using system-config-selinux. The same configuration files are used, so changes appear bidirectionally.
Changing a Runtime Boolean
Use the following procedure to change a runtime boolean using the GUI.
Note
Administrator privileges are required to perform this procedure.
- On the menu, point to and then click to display the Security Level Configuration dialog box.
- Click the SELinux tab, and then click Modify SELinux Policy.
- In the selection list, click the arrow next to the Name Service entry, and select the Disable SELinux protection for named daemon check box.
- Click to apply the change. Note that it may take a short time for the policy to be reloaded.
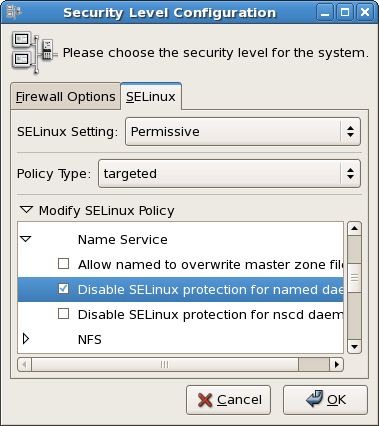
Figure 50.1. Using the Security Level Configuration dialog box to change a runtime boolean.
If you want to control these settings with scripts, you can use the
setenforce(1), getenforce(1), and selinuxenabled(1) commands.