このコンテンツは選択した言語では利用できません。
Chapter 17. TCP Wrappers and xinetd
Controlling access to network services is one of the most important security tasks facing a server administrator. Red Hat Enterprise Linux provides several tools which do just that. For instance, an
iptables-based firewall filters out unwelcome network packets within the kernel's network stack. For network services that utilize it, TCP wrappers add an additional layer of protection by defining which hosts are or are not allowed to connect to "wrapped" network services. One such wrapped network service is the xinetd super server. This service is called a super server because it controls connections to a subset of network services and further refines access control.
Figure 17.1, “Access Control to Network Services” is a basic illustration of how these tools work together to protect network services.
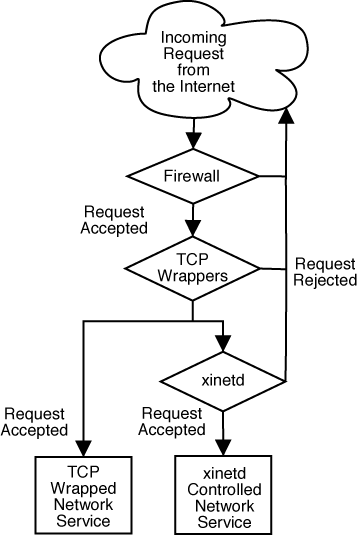
Figure 17.1. Access Control to Network Services
This chapter focuses on the role of TCP wrappers and
xinetd in controlling access to network services and reviews how these tools can be used to enhance both logging and utilization management. For a discussion of using firewalls with iptables, refer to Chapter 18, iptables.
17.1. TCP Wrappers
リンクのコピーリンクがクリップボードにコピーされました!
The TCP wrappers package (
tcp_wrappers) is installed by default and provides host-based access control to network services. The most important component within the package is the /usr/lib/libwrap.a library. In general terms, a TCP wrapped service is one that has been compiled against the libwrap.a library.
When a connection attempt is made to a TCP wrapped service, the service first references the hosts access files (
/etc/hosts.allow and /etc/hosts.deny) to determine whether or not the client host is allowed to connect. In most cases, it then uses the syslog daemon (syslogd) to write the name of the requesting host and the requested service to /var/log/secure or /var/log/messages.
If a client host is allowed to connect, TCP wrappers release control of the connection to the requested service and do not interfere further with communication between the client host and the server.
In addition to access control and logging, TCP wrappers can activate commands to interact with the client before denying or releasing control of the connection to the requested network service.
Because TCP wrappers are a valuable addition to any server administrator's arsenal of security tools, most network services within Red Hat Enterprise Linux are linked against the
libwrap.a library. Some such applications include /usr/sbin/sshd, /usr/sbin/sendmail, and /usr/sbin/xinetd.
Note
To determine if a network service binary is linked against
libwrap.a, type the following command as the root user:
ldd binary-name | grep libwrap
ldd binary-name | grep libwrap
Replace <binary-name> with the name of the network service binary.
If a prompt is returned, then the network service is not linked against
libwrap.a.
17.1.1. Advantages of TCP Wrappers
リンクのコピーリンクがクリップボードにコピーされました!
TCP wrappers provide the following advantages over other network service control techniques:
- Transparency to both the client host and the wrapped network service — Both the connecting client and the wrapped network service are unaware that TCP wrappers are in use. Legitimate users are logged and connected to the requested service while connections from banned clients fail.
- Centralized management of multiple protocols — TCP wrappers operate separately from the network services they protect, allowing many server applications to share a common set of configuration files for simpler management.