このコンテンツは選択した言語では利用できません。
16.6. PAM and Administrative Credential Caching
A variety of graphical administrative tools under Red Hat Enterprise Linux give users elevated privileges for up to five minutes via the
pam_timestamp.so module. It is important to understand how this mechanism works because a user who walks away from a terminal while pam_timestamp.so is in effect leaves the machine open to manipulation by anyone with physical access to the console.
Under the PAM timestamp scheme, the graphical administrative application prompts the user for the root password when it is launched. Once authenticated, the
pam_timestamp.so module creates a timestamp file within the /var/run/sudo/ directory by default. If the timestamp file already exists, other graphical administrative programs do not prompt for a password. Instead, the pam_timestamp.so module freshens the timestamp file — reserving an extra five minutes of unchallenged administrative access for the user.
The existence of the timestamp file is denoted by an authentication icon in the notification area of the panel. Below is an illustration of the authentication icon:
Figure 16.1. The Authentication Icon
16.6.1. Removing the Timestamp File
リンクのコピーリンクがクリップボードにコピーされました!
It is recommended that before walking away from a console where a PAM timestamp is active, the timestamp file be destroyed. To do this from within a graphical environment, click on the authentication icon on the panel. When a dialog box appears, click on the button.
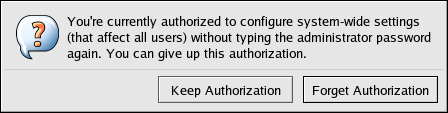
Figure 16.2. Authentication Icon Dialog
If logged into a system remotely using
ssh, use the /sbin/pam_timestamp_check -k root command to destroy the timestamp file.
Note
You must be logged in as the user who originally invoked the
pam_timestamp.so module in order to use the /sbin/pam_timestamp_check command. Do not log in as root to issue this command.
For information about destroying the timestamp file using
pam_timestamp_check, refer to the pam_timestamp_check man page.