이 콘텐츠는 선택한 언어로 제공되지 않습니다.
Chapter 5. Build Process
5.1. Build Once, Deploy Everywhere
In a container environment, the software build process is the stage in the life cycle where application code is integrated with the required runtime libraries. Managing this build process is key to securing the software stack.
Using OpenShift Container Platform as the standard platform for container builds enables you to guarantee the security of the build environment. Adhering to a "build once, deploy everywhere" philosophy ensures that the product of the build process is exactly what is deployed in production.
It is also important to maintain the immutability of your containers. You should not patch running containers, but rebuild and redeploy them.
5.2. Build Management and Security
You can use source-to-Image (S2I) to combine source code and base images. Builder images make use of S2I to enable your development and operations teams to collaborate on a reproducible build environment.
When developers commit code with Git for an application using build images, OpenShift Container Platform can perform the following functions:
- Trigger, either via webhooks on the code repository or other automated continuous integration (CI) process, to automatically assemble a new image from available artifacts, the S2I builder image, and the newly committed code.
- Automatically deploy the newly-built image for testing.
- Promote the tested image to production where it can be automatically deployed using CI process.
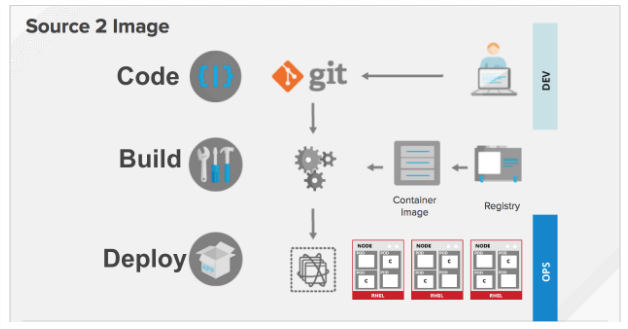
You can use OpenShift Container Registry to manage access to final images. Both S2I and native build images are automatically pushed to the OpenShift Container Registry.
In addition to the included Jenkins for CI, you can also integrate your own build / CI environment with OpenShift Container Platform using RESTful APIs, as well as use any API-compliant image registry.
Further Reading
OpenShift Container Platform Developer Guide
- OpenShift Container Platform Architecture: Source-to-Image (S2I) Build
-
OpenShift Container Platform Using Images: Other Images
Jenkins
5.3. Securing Inputs During Builds
In some scenarios, build operations require credentials to access dependent resources, but it is undesirable for those credentials to be available in the final application image produced by the build. You can define input secrets for this purpose.
For example, when building a Node.js application, you can set up your private mirror for Node.js modules. In order to download modules from that private mirror, you have to supply a custom .npmrc file for the build that contains a URL, user name, and password. For security reasons, you do not want to expose your credentials in the application image.
Using this example scenario, you can add an input secret to a new BuildConfig:
Create the secret, if it does not exist:
oc create secret generic secret-npmrc --from-file=.npmrc=~/.npmrc
$ oc create secret generic secret-npmrc --from-file=.npmrc=~/.npmrcCopy to Clipboard Copied! Toggle word wrap Toggle overflow This creates a new secret named secret-npmrc, which contains the base64 encoded content of the ~/.npmrc file.
Add the secret to the
sourcesection in the existingBuildConfig:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To include the secret in a new
BuildConfig, run the following command:oc new-build \ openshift/nodejs-010-centos7~https://github.com/sclorg/nodejs-ex.git \ --build-secret secret-npmrc$ oc new-build \ openshift/nodejs-010-centos7~https://github.com/sclorg/nodejs-ex.git \ --build-secret secret-npmrcCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Further Reading
- OpenShift Container Platform Developer Guide: Input Secrets
5.4. Designing Your Build Process
You can design your container image management and build process to use container layers so that you can separate control.
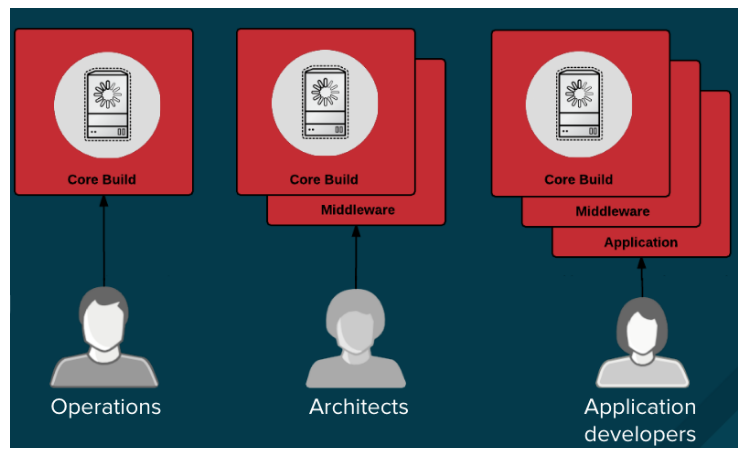
For example, an operations team manages base images, while architects manage middleware, runtimes, databases, and other solutions. Developers can then focus on application layers and just write code.
Because new vulnerabilities are identified daily, you need to proactively check container content over time. To do this, you should integrate automated security testing into your build or CI process. For example:
- SAST / DAST – Static and Dynamic security testing tools.
- Scanners for real-time checking against known vulnerabilities. Tools like these catalog the open source packages in your container, notify you of any known vulnerabilities, and update you when new vulnerabilities are discovered in previously scanned packages.
Your CI process should include policies that flag builds with issues discovered by security scans so that your team can take appropriate action to address those issues. You should sign your custom built containers to ensure that nothing is tampered with between build and deployment.
Further Reading
- Red Hat Enterprise Linux Atomic Host Managing Containers: Signing Container Images