26.2. Authentication
The Authentication tab allows for the configuration of network authentication methods. To enable an option, click the empty checkbox beside it. To disable an option, click the checkbox beside it to clear the checkbox.
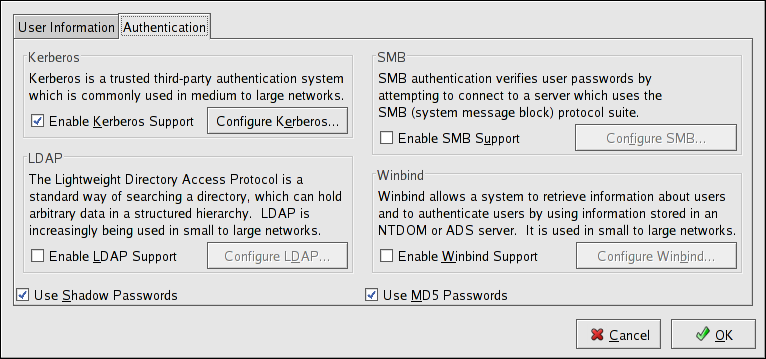
Figure 26.2. Authentication
The following explains what each option configures:
- Enable Kerberos Support — Select this option to enable Kerberos authentication. Click the button to configure:
- Realm — Configure the realm for the Kerberos server. The realm is the network that uses Kerberos, composed of one or more KDCs and a potentially large number of clients.
- KDC — Define the Key Distribution Center (KDC), which is the server that issues Kerberos tickets.
- Admin Servers — Specify the administration server(s) running
kadmind.
Thekrb5-libsandkrb5-workstationpackages must be installed for this option to work. Refer to the Reference Guide for more information on Kerberos. - Enable LDAP Support — Select this option to have standard PAM-enabled applications use LDAP for authentication. Click the button to specify the following:
- Use TLS to encrypt connections — Use Transport Layer Security to encrypt passwords sent to the LDAP server.
- LDAP Search Base DN — Retrieve user information by its Distinguished Name (DN).
- LDAP Server — Specify the IP address of the LDAP server.
Theopenldap-clientspackage must be installed for this option to work. Refer to the Reference Guide for more information about LDAP. - Use Shadow Passwords — Select this option to store passwords in shadow password format in the
/etc/shadowfile instead of/etc/passwd. Shadow passwords are enabled by default during installation and are highly recommended to increase the security of the system.Theshadow-utilspackage must be installed for this option to work. For more information about shadow passwords, refer to the Users and Groups chapter in the Reference Guide. - Enable SMB Support — This option configures PAM to use an SMB server to authenticate users. Click the button to specify:
- Workgroup — Specify the SMB workgroup to use.
- Domain Controllers — Specify the SMB domain controllers to use.
- Winbind — Select this option to configure the system to connect to a Windows Active Directory or a Windows domain controller. User information can be accessed, as well as server authentication options can be configured.
- Use MD5 Passwords — Select this option to enable MD5 passwords, which allows passwords to be up to 256 characters instead of eight characters or less. It is selected by default during installation and is highly recommended for increased security.