此内容没有您所选择的语言版本。
48.8.2. Basic Firewall Configuration
Just as a firewall in a building attempts to prevent a fire from spreading, a computer firewall attempts to prevent malicious software from spreading to your computer. It also helps to prevent unauthorized users from accessing your computer.
In a default Red Hat Enterprise Linux installation, a firewall exists between your computer or network and any untrusted networks, for example the Internet. It determines which services on your computer remote users can access. A properly configured firewall can greatly increase the security of your system. It is recommended that you configure a firewall for any Red Hat Enterprise Linux system with an Internet connection.
48.8.2.1. Security Level Configuration Tool
复制链接链接已复制到粘贴板!
During the Firewall Configuration screen of the Red Hat Enterprise Linux installation, you were given the option to enable a basic firewall as well as to allow specific devices, incoming services, and ports.
After installation, you can change this preference by using the Security Level Configuration Tool.
To start this application, use the following command:
system-config-securitylevel
system-config-securitylevel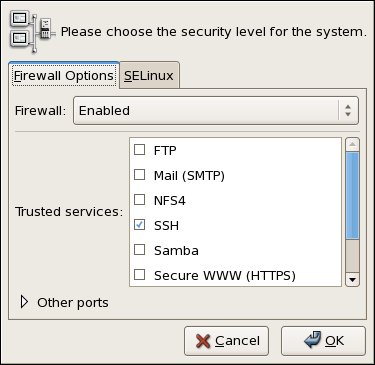
Figure 48.15. Security Level Configuration Tool
Note
The Security Level Configuration Tool only configures a basic firewall. If the system needs more complex rules, refer to Section 48.9, “IPTables” for details on configuring specific
iptables rules.