此内容没有您所选择的语言版本。
48.7.7. IPsec Network-to-Network Configuration
IPsec can also be configured to connect an entire network (such as a LAN or WAN) to a remote network using a network-to-network connection. A network-to-network connection requires the setup of IPsec routers on each side of the connecting networks to transparently process and route information from one node on a LAN to a node on a remote LAN. Figure 48.11, “A network-to-network IPsec tunneled connection” shows a network-to-network IPsec tunneled connection.
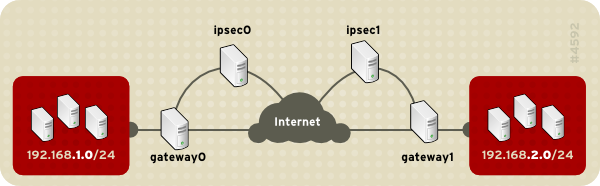
Figure 48.11. A network-to-network IPsec tunneled connection
This diagram shows two separate LANs separated by the Internet. These LANs use IPsec routers to authenticate and initiate a connection using a secure tunnel through the Internet. Packets that are intercepted in transit would require brute-force decryption in order to crack the cipher protecting the packets between these LANs. The process of communicating from one node in the 192.168.1.0/24 IP range to another in the 192.168.2.0/24 range is completely transparent to the nodes as the processing, encryption/decryption, and routing of the IPsec packets are completely handled by the IPsec router.
The information needed for a network-to-network connection include:
- The externally-accessible IP addresses of the dedicated IPsec routers
- The network address ranges of the LAN/WAN served by the IPsec routers (such as 192.168.1.0/24 or 10.0.1.0/24)
- The IP addresses of the gateway devices that route the data from the network nodes to the Internet
- A unique name, for example,
ipsec1. This is used to identify the IPsec connection and to distinguish it from other devices or connections. - A fixed encryption key or one automatically generated by
racoon - A pre-shared authentication key that is used during the initial stage of the connection and to exchange encryption keys during the session.
48.7.7.1. Network-to-Network (VPN) Connection
复制链接链接已复制到粘贴板!
A network-to-network IPsec connection uses two IPsec routers, one for each network, through which the network traffic for the private subnets is routed.
For example, as shown in Figure 48.12, “Network-to-Network IPsec”, if the 192.168.1.0/24 private network sends network traffic to the 192.168.2.0/24 private network, the packets go through gateway0, to ipsec0, through the Internet, to ipsec1, to gateway1, and to the 192.168.2.0/24 subnet.
IPsec routers require publicly addressable IP addresses and a second Ethernet device connected to their respective private networks. Traffic only travels through an IPsec router if it is intended for another IPsec router with which it has an encrypted connection.

Figure 48.12. Network-to-Network IPsec
Alternate network configuration options include a firewall between each IP router and the Internet, and an intranet firewall between each IPsec router and subnet gateway. The IPsec router and the gateway for the subnet can be one system with two Ethernet devices: one with a public IP address that acts as the IPsec router; and one with a private IP address that acts as the gateway for the private subnet. Each IPsec router can use the gateway for its private network or a public gateway to send the packets to the other IPsec router.
Use the following procedure to configure a network-to-network IPsec connection:
- In a command shell, type
system-config-networkto start the Network Administration Tool. - On the IPsec tab, click to start the IPsec configuration wizard.
- Click to start configuring a network-to-network IPsec connection.
- Enter a unique nickname for the connection, for example,
ipsec0. If required, select the check box to automatically activate the connection when the computer starts. Click to continue. - Select Network to Network encryption (VPN) as the connection type, and then click .
- Select the type of encryption to use: manual or automatic.If you select manual encryption, an encryption key must be provided later in the process. If you select automatic encryption, the
racoondaemon manages the encryption key. Theipsec-toolspackage must be installed if you want to use automatic encryption.Click to continue. - On the Local Network page, enter the following information:
- Local Network Address — The IP address of the device on the IPsec router connected to the private network.
- Local Subnet Mask — The subnet mask of the local network IP address.
- Local Network Gateway — The gateway for the private subnet.
Click to continue.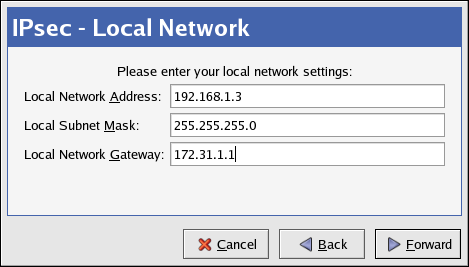
Figure 48.13. Local Network Information
- On the Remote Network page, enter the following information:
- Remote IP Address — The publicly addressable IP address of the IPsec router for the other private network. In our example, for ipsec0, enter the publicly addressable IP address of ipsec1, and vice versa.
- Remote Network Address — The network address of the private subnet behind the other IPsec router. In our example, enter
192.168.1.0if configuring ipsec1, and enter192.168.2.0if configuring ipsec0. - Remote Subnet Mask — The subnet mask of the remote IP address.
- Remote Network Gateway — The IP address of the gateway for the remote network address.
- If manual encryption was selected in step 6, specify the encryption key to use or click to create one.Specify an authentication key or click to generate one. This key can be any combination of numbers and letters.
Click to continue.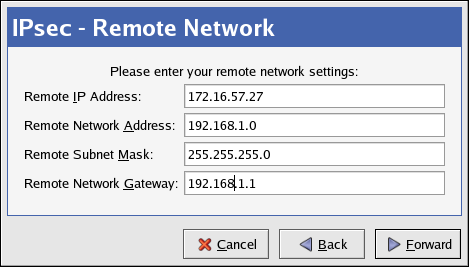
Figure 48.14. Remote Network Information
- Verify the information on the IPsec — Summary page, and then click .
- Select > to save the configuration.
- Select the IPsec connection from the list, and then click to activate the connection.
- Enable IP forwarding:
- Edit
/etc/sysctl.confand setnet.ipv4.ip_forwardto1. - Use the following command to enable the change:
sysctl -p /etc/sysctl.conf
sysctl -p /etc/sysctl.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The network script to activate the IPsec connection automatically creates network routes to send packets through the IPsec router if necessary.