此内容没有您所选择的语言版本。
25.4.2.2. SSL Support
The
mod_ssl enables encryption of the HTTP protocol over SSL. SSL (Secure Sockets Layer) protocol is used for communication and encryption over TCP/IP networks. The SSL tab enables you to configure SSL for your server. To configure SSL you need to provide the path to your:
- Certificate file - equivalent to using the
SSLCertificateFiledirective which points the path to the PEM (Privacy Enhanced Mail)-encoded server certificate file. - Key file - equivalent to using the
SSLCertificateKeyFiledirective which points the path to the PEM-encoded server private key file. - Certificate chain file - equivalent to using the
SSLCertificateChainFiledirective which points the path to the certificate file containing all the server's chain of certificates. - Certificate authority file - is an encrypted file used to confirm the authenticity or identity of parties communicating with the server.
You can find out more about configuration directives for SSL on http://httpd.apache.org/docs/2.2/mod/directives.html#S. You also need to determine which SSL options to enable. These are equivalent to using the
SSLOptions with the following options:
- FakeBasicAuth - enables standard authentication methods used by Apache. This means that the Client X509 certificate's Subject Distinguished Name (DN) is translated into a basic HTTP username.
- ExportCertData - creates CGI environment variables in
SSL_SERVER_CERT,SSL_CLIENT_CERTandSSL_CLIENT_CERT_CHAIN_nwhere n is a number 0,1,2,3,4... These files are used for more certificate checks by CGI scripts. - CompatEnvVars - enables backward compatibility for Apache SSL by adding CGI environment variables.
- StrictRequire - enables strict access which forces denial of access whenever the
SSLRequireSSLandSSLRequiredirectives indicate access is forbidden. - OptRenegotiate - enables avoidance of unnecessary handshakes by
mod_sslwhich also performs safe parameter checks. It is recommended to enable OptRenegotiate on a per directory basis.
More information on the above SSL options can be found on http://httpd.apache.org/docs/2.2/mod/mod_ssl.html#ssloptions. The figure below illustrates the SSL tab and the options discussed above.
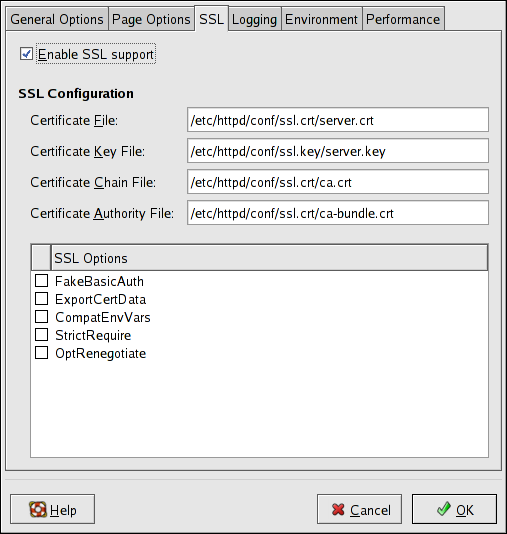
Figure 25.6. SSL
Important
Due to the vulnerability described in POODLE: SSLv3 vulnerability (CVE-2014-3566), Red Hat recommends disabling
SSL and using only TLSv1.1 or TLSv1.2. Backwards compatibility can be achieved using TLSv1.0. Many products Red Hat supports have the ability to use SSLv2 or SSLv3 protocols, or enable them by default. However, the use of SSLv2 or SSLv3 is now strongly recommended against.