22.5. Managing Public SSH Keys for Users
Identity Management allows you to upload a public SSH key to a user entry. The user who has access to the corresponding private SSH key can use
ssh to log into an IdM machine without using Kerberos credentials. If pam_krb5 is configured properly or if SSSD is used as the IdM server's identity provider, the user also receives a Kerberos ticket-granting ticket (TGT) after login; see the section called “Obtaining Kerberos Tickets Automatically” for more details.
Note that users can still authenticate by providing their Kerberos credentials if they are logging in from a machine where their private SSH key file is not available.
Caching and Retrieving SSH Keys Automatically
During an IdM server or client installation, SSSD is automatically configured on the machine to cache and retrieve user and host SSH keys. This allows IdM to serve as a universal and centralized repository of SSH keys.
If the server or client was not configured during installation, you can configure SSSD on the machine manually. For information on how to do this, see Section 22.6, “Configuring SSSD to Provide a Cache for the OpenSSH Services”. Note that caching SSH keys by SSSD requires administrative privileges on the local machines.
SSH Key Format Requirements
IdM accepts the following two SSH key formats:
A key file, such as
id_rsa.pub, consists of three parts: the key type, the key itself, and an additional comment or identifier. In the following example, the key type is RSA and the comment associates the key with the client.example.com host name:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDMM4xPu54Kf2dx7C4Ta2F7vnIzuL1i6P21TTKniSkjFuA+r qW06588e7v14Im4VejwnNk352gp49A62qSVOzp8IKA9xdtyRmHYCTUvmkcyspZvFRI713zfRKQVFyJOqHmW/m dCmak7QBxYou2ELSPhH3pe8MYTQIulKDSu5Zbsrqedg1VGkSJxf7mDnCSPNWWzAY9AFB9Lmd2m2xZmNgVAQEQ nZXNMaIlroLD/51rmMSkJGHGb1O68kEq9Z client.example.com
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDMM4xPu54Kf2dx7C4Ta2F7vnIzuL1i6P21TTKniSkjFuA+r
qW06588e7v14Im4VejwnNk352gp49A62qSVOzp8IKA9xdtyRmHYCTUvmkcyspZvFRI713zfRKQVFyJOqHmW/m
dCmak7QBxYou2ELSPhH3pe8MYTQIulKDSu5Zbsrqedg1VGkSJxf7mDnCSPNWWzAY9AFB9Lmd2m2xZmNgVAQEQ
nZXNMaIlroLD/51rmMSkJGHGb1O68kEq9Z client.example.com
When uploading a key to IdM, you can either upload all three key parts, or only the key itself. If you only upload the key itself, IdM automatically identifies the key type, such as RSA or DSA, from the uploaded key.
22.5.1. Generating an SSH Key
Copy linkLink copied to clipboard!
You can generate an SSH key using the OpenSSH
ssh-keygen utility. The utility displays information about the location of the public key. For example:
To upload an SSH key for a user, use the public key string stored in the displayed file.
22.5.2. Uploading User SSH Keys
Copy linkLink copied to clipboard!
22.5.2.1. Web UI: Uploading User SSH Keys
Copy linkLink copied to clipboard!
- Select
. - Click the name of the user to edit.
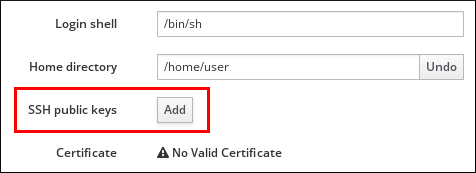
- Under the Settings tab in the Account Settings area, click SSH public keys: Add.
Figure 22.9. SSH public keys in the Account Settings
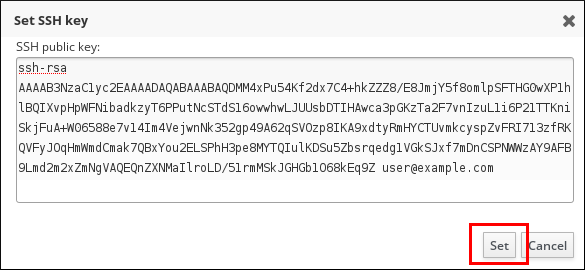
- Paste in the Base 64-encoded public key string, and click .
Figure 22.10. Pasting in the Public Key
- Click Save at the top of the page.
22.5.2.2. Command Line: Uploading User SSH Keys
Copy linkLink copied to clipboard!
Use the ipa user-mod command and pass the Base 64-encoded public key string using the
--sshpubkey option.
For example, to upload the key type, the key itself, and the host name identifier:
ipa user-mod user --sshpubkey="ssh-rsa AAAAB3Nza...SNc5dv== client.example.com"
$ ipa user-mod user --sshpubkey="ssh-rsa AAAAB3Nza...SNc5dv== client.example.com"
To upload multiple keys, use
--sshpubkey multiple times. For example, to upload two SSH keys:
--sshpubkey="AAAAB3Nza...SNc5dv==" --sshpubkey="RjlzYQo...ZEt0TAo="
--sshpubkey="AAAAB3Nza...SNc5dv==" --sshpubkey="RjlzYQo...ZEt0TAo="Note
Instead of pasting the key string manually into the command line, you can use command redirection and point to the file containing the key. For example:
ipa user-mod user --sshpubkey="$(cat ~/.ssh/id_rsa.pub)" --sshpubkey="$(cat ~/.ssh/id_rsa2.pub)"
$ ipa user-mod user --sshpubkey="$(cat ~/.ssh/id_rsa.pub)" --sshpubkey="$(cat ~/.ssh/id_rsa2.pub)"
22.5.3. Deleting User Keys
Copy linkLink copied to clipboard!
To delete an SSH key:
- using the web UI, see Section 22.5.3.1, “Web UI: Deleting User SSH Keys”
- using the command line, see Section 22.5.3.2, “Command Line: Deleting User SSH Keys”
22.5.3.1. Web UI: Deleting User SSH Keys
Copy linkLink copied to clipboard!
- Select
. - Click the name of the user to edit.
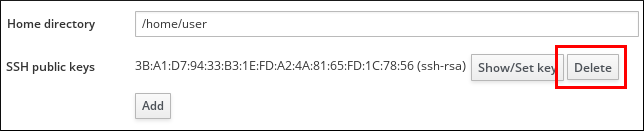
- Under the Settings tab in the Account Settings area, click Delete next to the key you want to remove.
Figure 22.11. Deleting User SSH Public Key
- Click Save at the top of the page.
22.5.3.2. Command Line: Deleting User SSH Keys
Copy linkLink copied to clipboard!
To delete all SSH keys assigned to a user account, add the
--sshpubkey option to the ipa user-mod command without specifying any key:
ipa user-mod user --sshpubkey=
$ ipa user-mod user --sshpubkey=
If you only want to delete a specific SSH key or keys, use the
--sshpubkey option to specify the key or keys you want to keep.
Note
This command does not delete the SSH keys from the cache immediately. With the default cache timeout value (
entry_cache_timeout = 5400), the keys remain in cache for one and a half hours.