32.3. Mapping SELinux Users and IdM Users
An SELinux map associates an SELinux user context on a local system with an IdM user, or users, within the domain. An SELinux map has three parts: the SELinux user context and an IdM user-host pairing. The IdM user-host pair can be defined in one of two ways: it can be set for explicit users, or user groups, on explicit hosts, or host groups; or it can be defined using a host-based access control rule.
32.3.1. In the Web UI
Copy linkLink copied to clipboard!
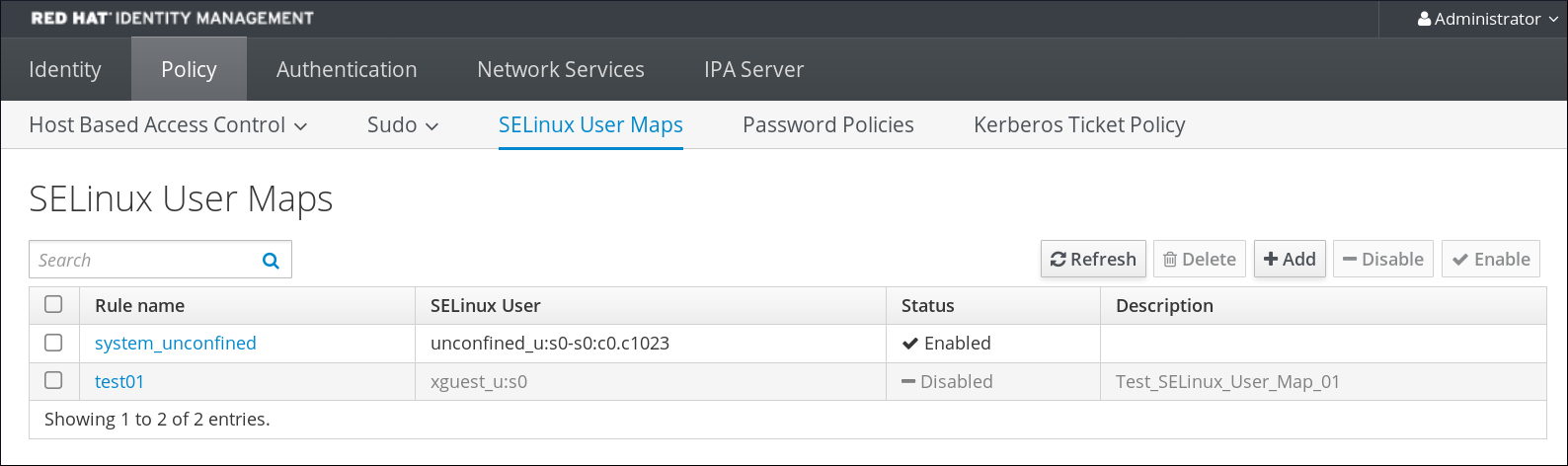
- In the top menu, click the Policy main tab and the SELinux User Mappings subtab.
- In the list of mappings, click the button to create a new map.
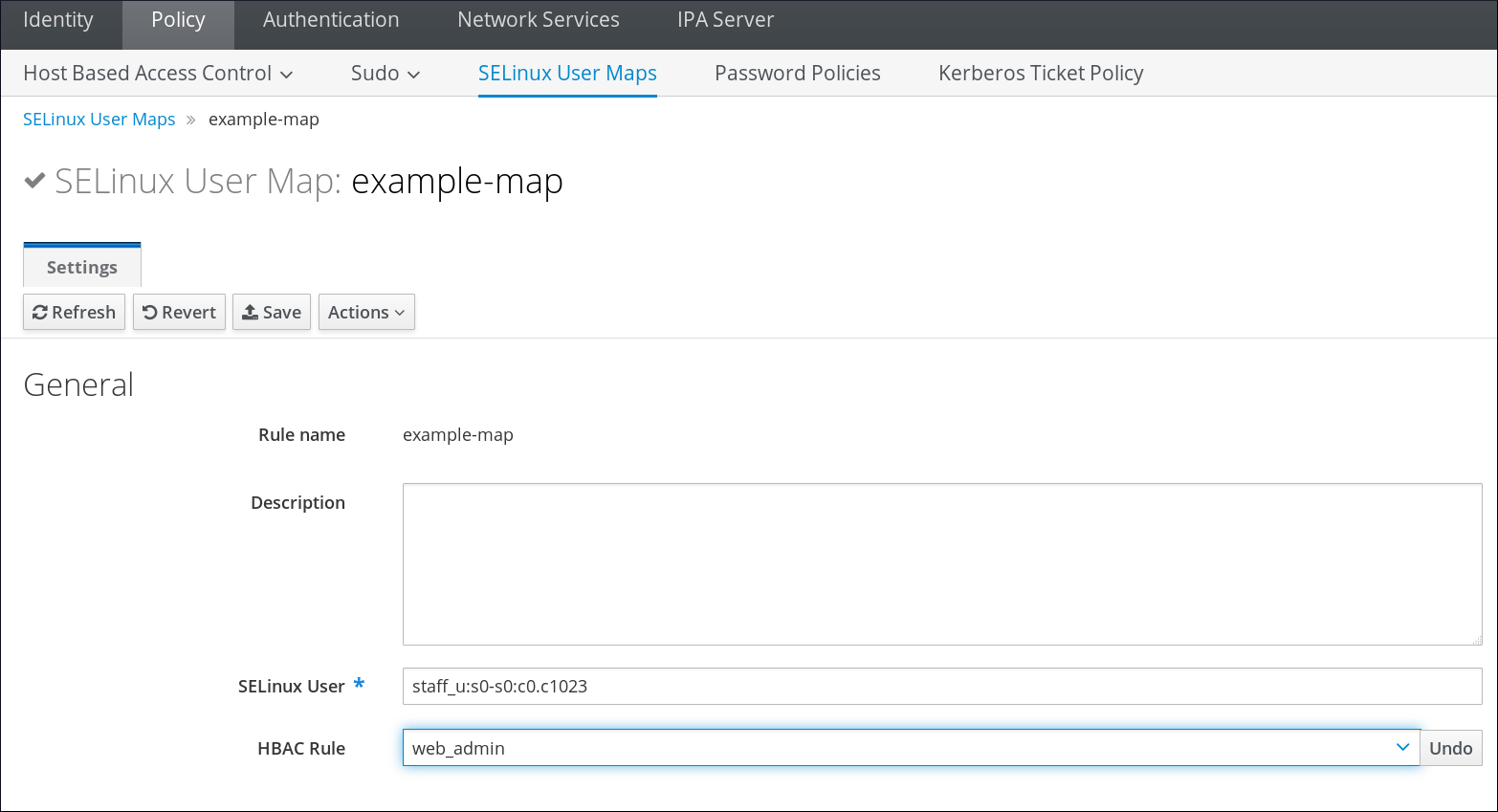
- Enter the name for the map and the SELinux user. The format of the SELinux user has to be identical with how it appears in the IdM server configuration. SELinux users have the format SELinux_user:MLS[:MCS].
- Click to add the IdM user information.
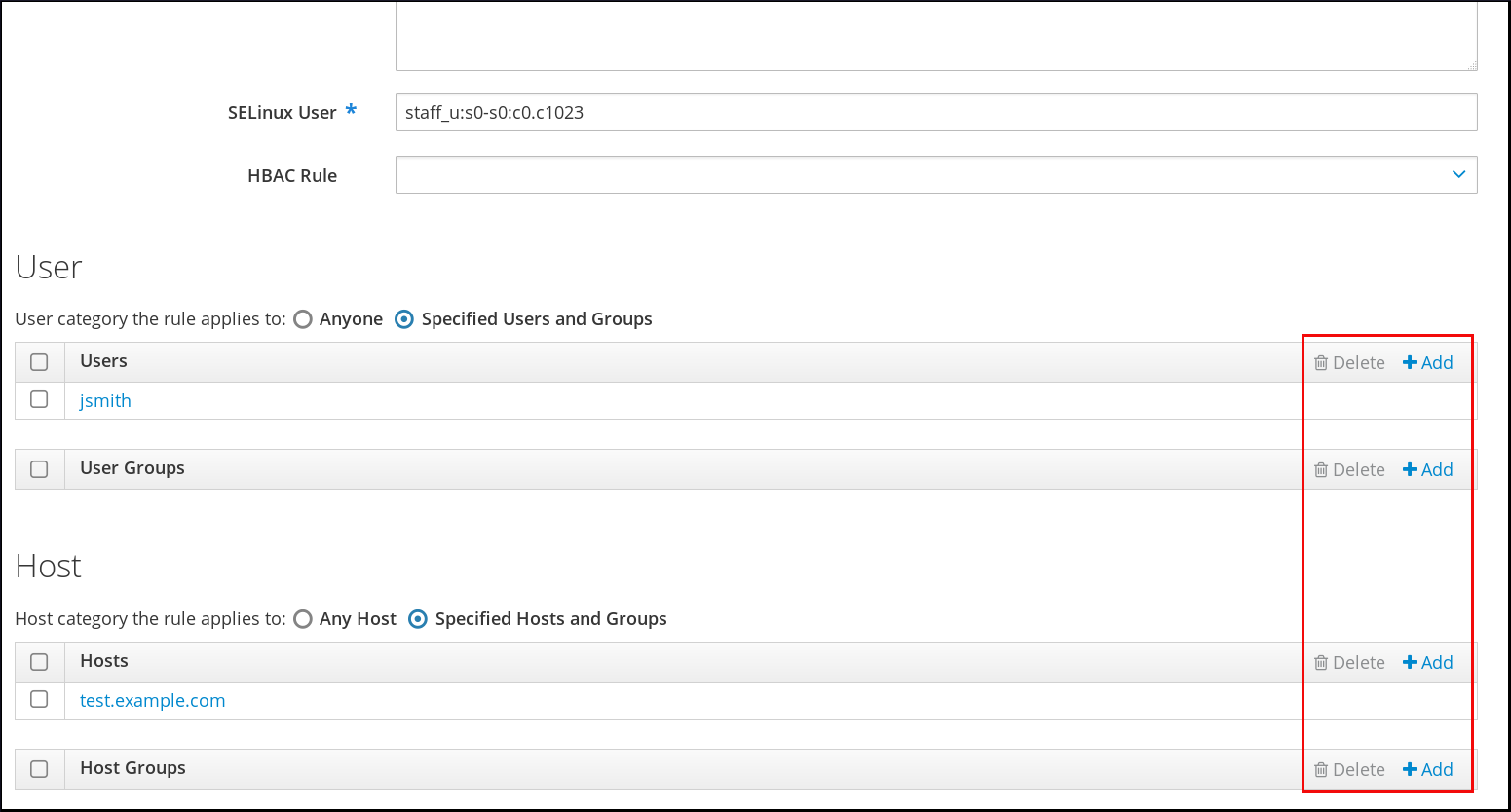
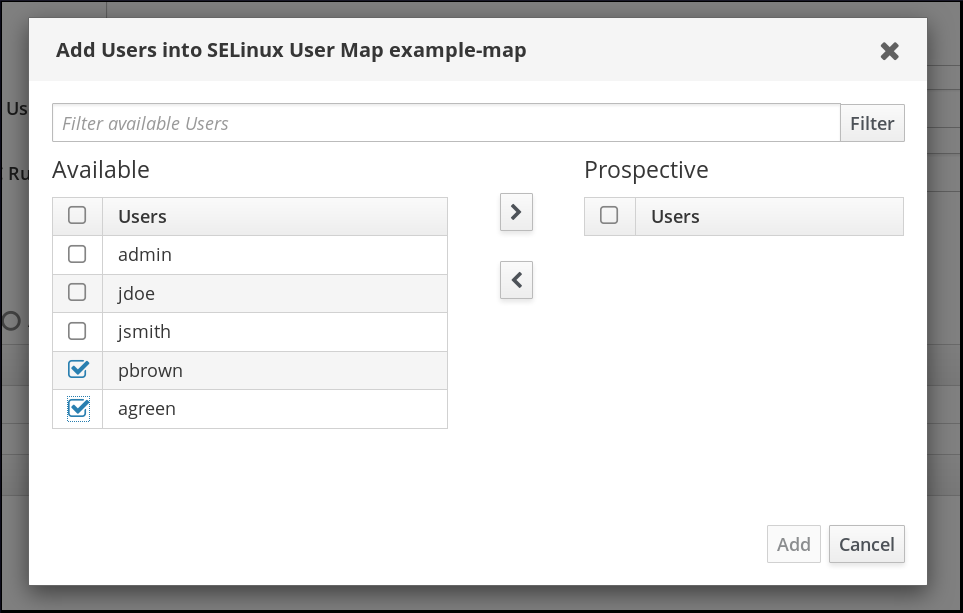
- To set a host-based access control rule, select the rule from the drop-down menu in the General area of the configuration. Using a host-based access control rule also introduces access controls on what hosts a remote user can use to access a target machine. Only one host-based access control rule can be assigned.NoteThe host-based access control rule must contain users and hosts, not just services.Alternatively, scroll down the Users and Hosts areas, and click the Add link to assign users, user groups, hosts, or host groups to the SELinux map.Select the users (or hosts or groups) on the left, click the right arrows button () to move them to the Prospective column, and click the button to add them to the rule.NoteOnly one option can be used: either a host-based access control rule can be given or the users and hosts can be set manually. Both options cannot be used at the same time.
- Click the Update link at the top to save the changes to the SELinux user map.
32.3.2. In the CLI
Copy linkLink copied to clipboard!
An SELinux map rule has three fundamental parts:
- The SELinux user:
--selinuxuser - The user or user groups which are associated with the SELinux user:
--usersor--groups - The host or host groups which are associated with the SELinux user:
--hostsor--hostgroups - Alternatively, a host-based access control rule which specifies both hosts and users in it:
--hbacrule
A rule can be created with all information at once using the selinuxusermap-add command. Users and hosts can be added to a rule after it is created by using the selinuxusermap-add-user and selinuxusermap-add-host commands, respectively.
Example 32.3. Creating a New SELinux Map
The
--selinuxuser value must be the SELinux user name exactly as it appears in the IdM server configuration. SELinux users have the format SELinux_user:MLS[:MCS].
The user, or user group; and the host, or host group must be specified for the SELinux mapping to be valid. The user, host, and group options can be used multiple times or can be used once with a comma-separated listed inside curly braces, for example --option={val1,val2,val3}.
ipa selinuxusermap-add --selinuxuser="xguest_u:s0" selinux1 ipa selinuxusermap-add-user --users=user1 --users=user2 --users=user3 selinux1 ipa selinuxusermap-add-host --hosts=server.example.com --hosts=test.example.com selinux1
[user1@server ~]$ ipa selinuxusermap-add --selinuxuser="xguest_u:s0" selinux1
[user1@server ~]$ ipa selinuxusermap-add-user --users=user1 --users=user2 --users=user3 selinux1
[user1@server ~]$ ipa selinuxusermap-add-host --hosts=server.example.com --hosts=test.example.com selinux1Example 32.4. Creating an SELinux Map with a Host-Based Access Control Rule
The
--hbacrule value identifies the host-based access control rule to use for mapping. Using a host-based access control rule introduces access controls on what hosts a remote user can use to access a target machine, along with applying SELinux contexts after the remote user has logged into the target machine.
The access control rule must specify both users and hosts appropriately so that the SELinux map can construct the SELinux user, IdM user, and host triple.
Only one host-based access control rule can be specified.
ipa selinuxusermap-add --hbacrule=webserver --selinuxuser="xguest_u:s0" selinux1
[user1@server ~]$ ipa selinuxusermap-add --hbacrule=webserver --selinuxuser="xguest_u:s0" selinux1
Host-based access control rules are described in Chapter 31, Configuring Host-Based Access Control.
Example 32.5. Adding a User to an SELinux Map
Users and hosts can be added to an already existing map. This is done using a specific command, either selinuxusermap-add-user or selinuxusermap-add-host.
ipa selinuxusermap-add-user --users=user1 selinux1
[user1@server ~]$ ipa selinuxusermap-add-user --users=user1 selinux1
If the selinuxusermap-mod command is used with the
--hbacrule option to modify an already existing SELinux map, the new SELinux map overwrites the previous SELinux map.
Example 32.6. Removing a User from an SELinux Map
A specific user or host can be removed from an SELinux map by using either the selinuxusermap-remove-host or selinuxusermap-remove-user command. For example:
ipa selinuxusermap-remove-user --users=user2 selinux1
[user1@server ~]$ ipa selinuxusermap-remove-user --users=user2 selinux1