6.5. Managing Server Roles
Based on the services installed on an IdM server, it can perform various server roles. For example: CA server, DNS server, or key recovery authority (KRA) server.
6.5.1. Viewing Server Roles
Web UI: Viewing Server Roles
For a complete list of the supported server roles, see
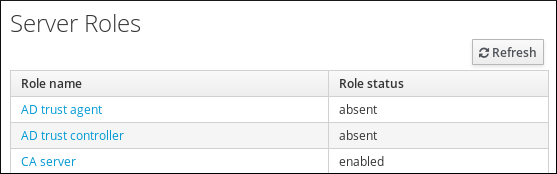
- Role status absent means that no server in the topology is performing the role.
- Role status enabled means that one or more servers in the topology are performing the role.
Figure 6.14. Server Roles in the Web UI
Command Line: Viewing Server Roles
The ipa config-show command displays all CA servers, NTP servers, and the current CA renewal master:
$ ipa config-show ... IPA masters: server1.example.com, server2.example.com, server3.example.com IPA CA servers: server1.example.com, server2.example.com IPA NTP servers: server1.example.com, server2.example.com, server3.example.com IPA CA renewal master: server1.example.com
The ipa server-show command displays a list of roles enabled on a particular server. For example, for a list of roles enabled on server.example.com:
$ ipa server-show
Server name: server.example.com
...
Enabled server roles: CA server, DNS server, NTP server, KRA server
The ipa server-find --servrole searches for all servers with a particular server role enabled. For example, to search for all CA servers:
$ ipa server-find --servrole "CA server" --------------------- 2 IPA servers matched --------------------- Server name: server1.example.com ... Server name: server2.example.com ... ---------------------------- Number of entries returned 2 ----------------------------
6.5.2. Promoting a Replica to a Master CA Server
Note
This section describes changing the CA renewal master at domain level 1 (see Chapter 7, Displaying and Raising the Domain Level). For documentation on changing the CA renewal master at domain level 0, see Section D.4, “Promoting a Replica to a Master CA Server”.
If your IdM deployment uses an embedded certificate authority (CA), one of the IdM CA servers acts as the master CA: it manages the renewal of CA subsystem certificates and generates certificate revocation lists (CRLs). By default, the master CA is the first server on which the system administrator installed the CA role using the ipa-server-install or ipa-ca-install command.
If you plan to take the master CA server offline or decommission it, promote another CA server to take the its place as the new CA renewal master:
- Configure the replica to handle CA subsystem certificate renewal.
- See Section 6.5.2.1, “Changing the Current CA Renewal Master” for domain level 1.
- See Section D.4.1, “Changing Which Server Handles Certificate Renewal” for domain level 0.
- Configure the replica to generate CRLs. See Section 6.5.2.2, “Changing Which Server Generates CRLs”.
- Before decommissioning the previous master CA server, make sure the new master works properly. See Section 6.5.2.3, “Verifying That the New Master CA Server Is Configured Correctly”.
6.5.2.1. Changing the Current CA Renewal Master
Web UI: Changing the Current CA Renewal Master
- Select
. - In the IPA CA renewal master field, select the new CA renewal master.
Command Line: Changing the Current CA Renewal Master
Use the ipa config-mod --ca-renewal-master-server command:
$ ipa config-mod --ca-renewal-master-server new_ca_renewal_master.example.com
...
IPA masters: old_ca_renewal_master.example.com, new_ca_renewal_master.example.com
IPA CA servers: old_ca_renewal_master.example.com, new_ca_renewal_master.example.com
IPA NTP servers: old_ca_renewal_master.example.com, new_ca_renewal_master.example.com
IPA CA renewal master: new_ca_renewal_master.example.com
The output confirms that the update was successful.
6.5.2.2. Changing Which Server Generates CRLs
To change which server generates certificate revocation lists (CRL):
- If you do not know the current CRL generation master, use the ipa-crlgen-manage status command on each IdM certificate authority (CA) to determine whether CRL generation is enabled:
# ipa-crlgen-manage status CRL generation: enabled - On the current CRL generation master, disable the feature:
# ipa-crlgen-manage disable
- On the other CA host that you want to configure as the new CRL generation master, enable the feature:
# ipa-crlgen-manage enable
6.5.2.3. Verifying That the New Master CA Server Is Configured Correctly
Make sure the
/var/lib/ipa/pki-ca/publish/MasterCRL.bin file exists on the new master CA server.
The file is generated based on the time interval defined in the
/etc/pki/pki-tomcat/ca/CS.cfg file using the ca.crl.MasterCRL.autoUpdateInterval parameter. The default value is 240 minutes (4 hours).
Note
If you update the
ca.crl.MasterCRL.autoUpdateInterval parameter, the change will become effective after the next already scheduled CRL update.
If the file exists, the new master CA server is configured correctly, and you can safely dismiss the previous CA master system.
6.5.3. Uninstalling the IdM CA service from an IdM server
Red Hat recommends that you have maximun four Identity Management (IdM) replicas with the CA Role in your topology. Therefore, if you have more than four such replicas and performance issues occur due to redundant certificate replication, remove redundant CA service instances from IdM replicas. To do this, you must first decommission the affected IdM replicas completely before re-installing IdM on them, this time without the CA service.
Important
While you can add the CA role to an IdM replica, IdM does not provide a method to remove only the CA role from an IdM replica: the ipa-ca-install command does not have an
--uninstall option.
- Identify the redundant CA service and follow the procedure in Section 2.4, “Uninstalling an IdM Server” on the IdM replica that hosts this service.
- On the same host, follow the procedure in Section 2.3.5, “Installing a Server with an External CA as the Root CA” or Section 2.3.6, “Installing Without a CA”, depending on your use case.