18.3. Defining a Different Attribute Value for a User Account on Different Hosts
An administrator can create multiple ID views that override an attribute value used by a user account and apply these ID views to different client hosts. Example: A service account is configured to use different SSH public keys when authenticating on different hosts.
This section includes the following procedures:
The procedures show how to create an ID view for a client host named
host1.example.com. To override the attribute values on the other hosts as well, use the procedures to create multiple ID views, one for each host.
In the following procedures:
useris the user account whose attribute needs to be overriddenhost1.example.comis the host on which the ID view will be applied
Important
After you create a new ID view, restart SSSD on all clients where the ID view is applied.
If the new ID view changes a UID or GID, clear the SSSD cache on these clients as well.
18.3.1. Web UI: Overriding an Attribute Value for a Specific Host
To manage ID views, first log in to the IdM web UI as an IdM administrator.
Creating a New ID View
- Under the Identity tab, select the ID Views subtab.
- Click and provide a name for the ID view.
Figure 18.1. Adding an ID View
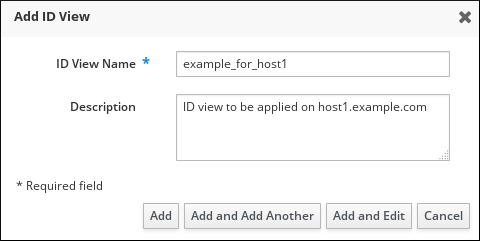
- Click to confirm.
The new ID view is now displayed in the list of ID views.
Figure 18.2. List of ID Views

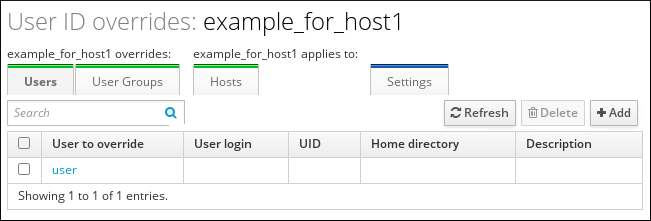
Adding a User Override to the ID View
- In the list of ID views, click the name of the ID view.
Figure 18.3. Editing an ID View
- Under the Users tab, click to add the user override.
- Select the user account whose attribute value to override, and click .
The user override is now displayed on the
example_for_host1 ID view page.
Figure 18.4. List of Overrides
Specifying the Attribute to Override
- Click the override that you want to use to change the attribute value.
Figure 18.5. Editing an Override
- Define the new value for the attribute.For example, to override the SSH public key used by the user account:
- Click .
Figure 18.6. Adding an SSH Public Key
- Paste in the public key.
NoteFor details on adding SSH keys to IdM, see Section 22.5, “Managing Public SSH Keys for Users”. - Click to update the override.
Applying the ID View to a Specific Host
- In the list of ID views, click the name of the ID view.
Figure 18.7. Editing an ID View

- Under the Hosts tab, click .
- Select the
host1.example.comhost, and move it to the Prospective column. - Click .
The host is now displayed in the list of hosts to which the ID view applies.
Figure 18.8. Listing Hosts to Which an ID View Applies
18.3.2. Command Line: Overriding an Attribute Value for a Specific Host
Before managing ID views, request a ticket as an IdM administrator. For example:
$ kinit admin
- Create a new ID view. For example, the create an ID view named
example_for_host1:$ ipa idview-add example_for_host1 --------------------------- Added ID View "example_for_host1" --------------------------- ID View Name: example_for_host1
- Add a user override to the
example_for_host1ID view. The ipa idoverrideuser-add command requires the name of the ID view and the user to override.- To specify the new attribute value, add the corresponding command-line option as well. For a list of the available options, run ipa idoverrideuser-add --help. For example, use the
--sshpubkeyoption to override the SSH public key value:$ ipa idoverrideuser-add example_for_host1 user --sshpubkey="ssh-rsa AAAAB3NzaC1yrRqFE...gWRL71/miPIZ user@example.com" ----------------------------- Added User ID override "user" ----------------------------- Anchor to override: user SSH public key: ssh-rsa AAAB3NzaC1yrRqFE...gWRL71/miPIZ user@example.comNoteFor details on adding SSH keys to IdM, see Section 22.5, “Managing Public SSH Keys for Users”. - The ipa idoverrideuser-add --certificate command replaces all existing certificates for the account in the specified ID view. To append an additional certificate, use the ipa idoverrideuser-add-cert command instead:
$ ipa idoverrideuser-add-cert example_for_host1 user --certificate="MIIEATCC..."
- Using the ipa idoverrideuser-mod command, you can also specify new attribute values for an existing user override.
- Use the ipa idoverrideuser-del command to delete a user override.NoteIf you use this command to delete SSH keys overrides, it does not delete the SSH keys from the cache immediately. With the default cache timeout value (
entry_cache_timeout = 5400), the keys remain in cache for one and a half hours.
- Apply
example_for_host1to thehost1.example.comhost:$ ipa idview-apply example_for_host1 --hosts=host1.example.com ----------------------------- Applied ID View "example_for_host1" ----------------------------- hosts: host1.example.com --------------------------------------------- Number of hosts the ID View was applied to: 1 ---------------------------------------------
NoteThe ipa idview-apply command also accepts the--hostgroupsoption. The option applies the ID view to hosts that belong to the specified host group, but does not associate the ID view with the host group itself. Instead, the--hostgroupsoption expands the members of the specified host group and applies the--hostsoption individually to every one of them.