Chapter 31. Configuring Host-Based Access Control
This chapter describes host-based access control (HBAC) in Identity Management (IdM) and explains how you can use HBAC to manage access control in your IdM domain.
31.1. How Host-Based Access Control Works in IdM
Copy linkLink copied to clipboard!
Host-based access control defines which users (or user groups) can access specified hosts (or host groups) by using specified services (or services in a service group). For example, you can:
- Limit access to a specified system in your domain to members of a specific user group.
- Allow only a specific service to be used to access the systems in your domain.
The administrator configures host-based access control by using a set of allowing rules named HBAC rules. By default, IdM is configured with a default HBAC rule named
allow_all, which allows universal access in the whole IdM domain.
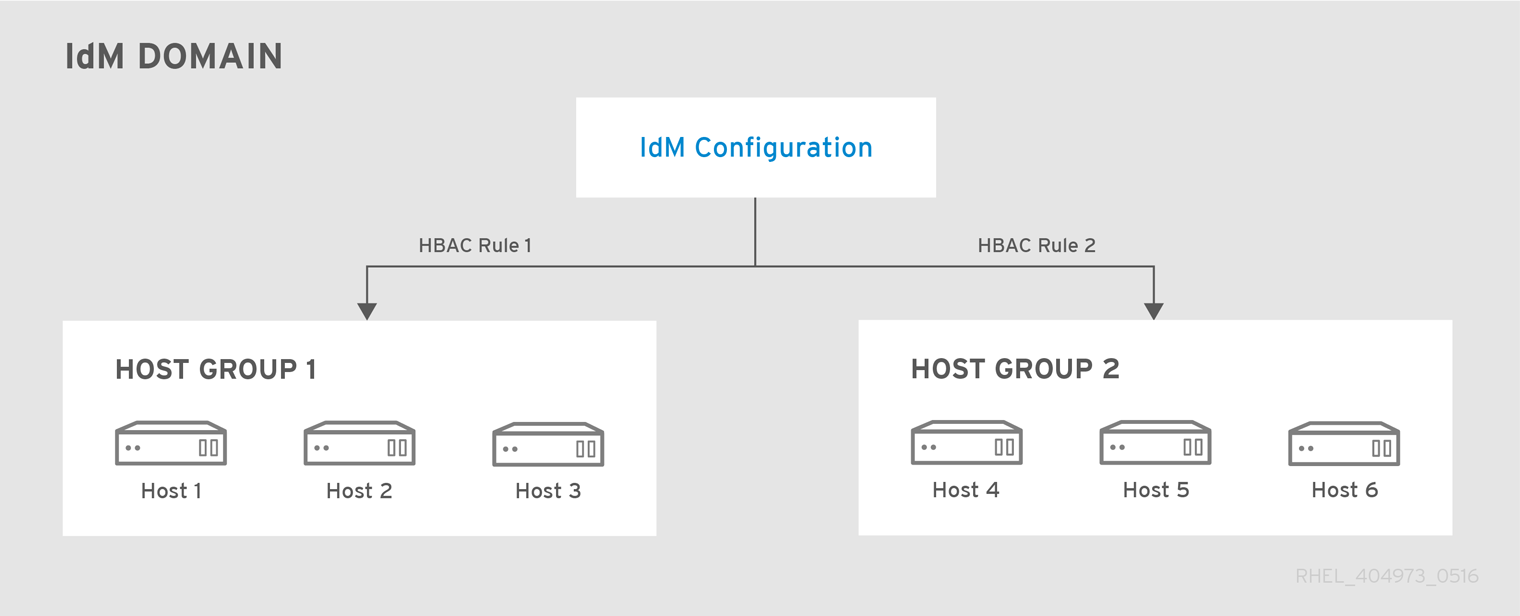
Applying HBAC Rules to Groups
For centralized and simplified access control management, you can apply HBAC rules to whole user, host, or service groups instead of individual users, hosts, or services.
Figure 31.1. Host Groups and Host-Based Access Control
When applying HBAC rules to groups, consider using automember rules. See Section 13.6, “Defining Automatic Group Membership for Users and Hosts”.