34.3. Create User
Create a user account for yourself with this screen. Always use this account to log in to your Red Hat Enterprise Linux system, rather than using the
root account.
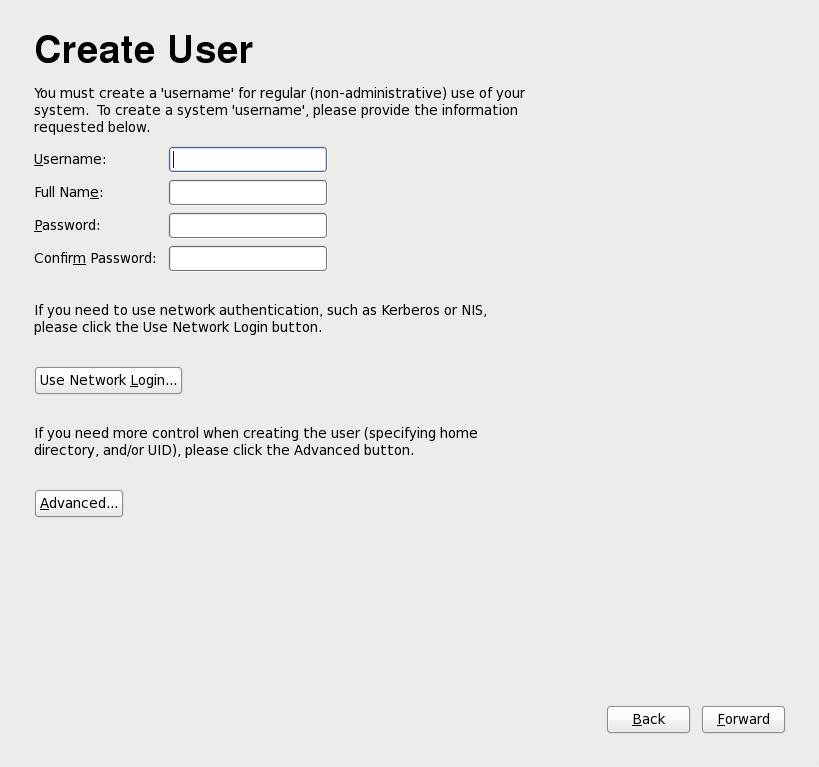
Figure 34.12. Firstboot create user screen
Enter a user name and your full name, and then enter your chosen password. Type your password once more in the Confirm Password box to ensure that it is correct.
To configure Red Hat Enterprise Linux to use network services for authentication of user information, click . Refer to Section 34.3.1, “Authentication Configuration” for further details.
Important
If you do not create at least one user account in this step, you will not be able to log in to the Red Hat Enterprise Linux graphical environment. If you skipped this step during installation, refer to Section 10.4.2, “Booting into a Graphical Environment”.
Note
To add additional user accounts to your system after the installation is complete, choose
34.3.1. Authentication Configuration
Copy linkLink copied to clipboard!
If you clicked on the Create User screen, you must now specify how users are to be authenticated on the system. Use the drop-down menu to select from the following types of user database:
- (for use when the user database on the network is not accessible)
- (Lightweight Directory Access Protocol)
- (Network Information Service)
- (for use with Microsoft Active Directory)
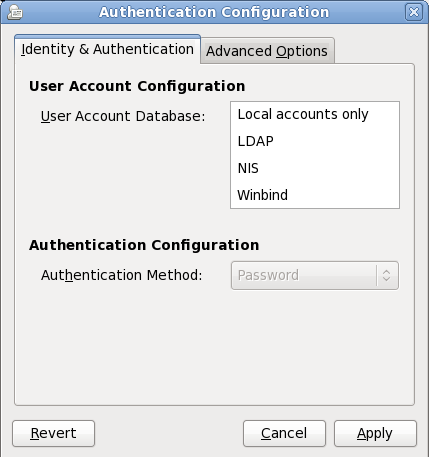
Figure 34.13. Firstboot Authentication Configuration screen
When you select the type of user database appropriate for your network, you must provide additional details relevant to that database type. For example, if you select
LDAP, you must specify the base distinguished name for LDAP searches, and the address of the LDAP server. You must also select an Authentication Method relevant to the type of user database that you chose, for example, a Kerberos password, LDAP password, or NIS password.
The Advanced Options tab lets you enable other authentication mechanisms, including fingerprint readers, smart cards, and local access control in
/etc/security/access.conf.
For more information, refer to Authentication Configuration in the Red Hat Enterprise Linux Deployment Guide.
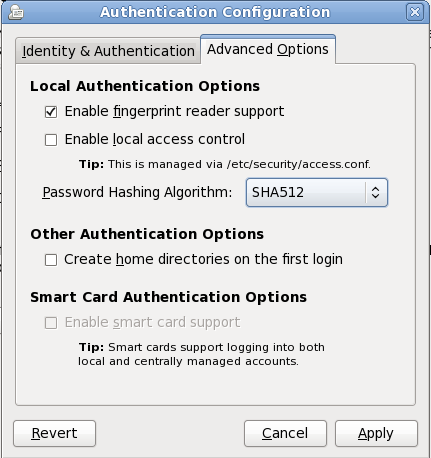
Figure 34.14. Firstboot authentication Advanced Options screen