이 콘텐츠는 선택한 언어로 제공되지 않습니다.
14.2.4. Using Key-Based Authentication
To improve the system security even further, you can enforce key-based authentication by disabling the standard password authentication. To do so, open the
/etc/ssh/sshd_config configuration file in a text editor such as vi or nano, and change the PasswordAuthentication option as follows:
PasswordAuthentication no
PasswordAuthentication no
To be able to use
ssh, scp, or sftp to connect to the server from a client machine, generate an authorization key pair by following the steps below. Note that keys must be generated for each user separately.
Red Hat Enterprise Linux 6 uses SSH Protocol 2 and RSA keys by default (see Section 14.1.3, “Protocol Versions” for more information).
Important
Do not generate key pairs as
root, as only root would be able to use those keys.
Note
Before reinstalling your system, back up the
~/.ssh/ directory to keep the generated key pair. Copy the backed-up data to the home directory in the new system for any user you require, including root.
14.2.4.1. Generating Key Pairs
링크 복사링크가 클립보드에 복사되었습니다!
To generate an RSA key pair for version 2 of the SSH protocol, follow these steps:
- Generate an RSA key pair by typing the following at a shell prompt:
ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/john/.ssh/id_rsa):
~]$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/john/.ssh/id_rsa):Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Enter to confirm the default location (that is,
~/.ssh/id_rsa) for the newly created key. - Enter a passphrase, and confirm it by entering it again when prompted to do so. For security reasons, avoid using the same password as you use to log in to your account.After this, you will be presented with a message similar to this:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the permissions of the
~/.ssh/directory:chmod 700 ~/.ssh
~]$ chmod 700 ~/.sshCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the content of
~/.ssh/id_rsa.pubinto the~/.ssh/authorized_keyson the machine to which you want to connect, appending it to its end if the file already exists. - Change the permissions of the
~/.ssh/authorized_keysfile using the following command:chmod 600 ~/.ssh/authorized_keys
~]$ chmod 600 ~/.ssh/authorized_keysCopy to Clipboard Copied! Toggle word wrap Toggle overflow
To generate a DSA key pair for version 2 of the SSH protocol, follow these steps:
- Generate a DSA key pair by typing the following at a shell prompt:
ssh-keygen -t dsa Generating public/private dsa key pair. Enter file in which to save the key (/home/john/.ssh/id_dsa):
~]$ ssh-keygen -t dsa Generating public/private dsa key pair. Enter file in which to save the key (/home/john/.ssh/id_dsa):Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Enter to confirm the default location (that is,
~/.ssh/id_dsa) for the newly created key. - Enter a passphrase, and confirm it by entering it again when prompted to do so. For security reasons, avoid using the same password as you use to log in to your account.After this, you will be presented with a message similar to this:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the permissions of the
~/.ssh/directory:chmod 700 ~/.ssh
~]$ chmod 700 ~/.sshCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the content of
~/.ssh/id_dsa.pubinto the~/.ssh/authorized_keyson the machine to which you want to connect, appending it to its end if the file already exists. - Change the permissions of the
~/.ssh/authorized_keysfile using the following command:chmod 600 ~/.ssh/authorized_keys
~]$ chmod 600 ~/.ssh/authorized_keysCopy to Clipboard Copied! Toggle word wrap Toggle overflow
To generate an RSA key pair for version 1 of the SSH protocol, follow these steps:
- Generate an RSA key pair by typing the following at a shell prompt:
ssh-keygen -t rsa1 Generating public/private rsa1 key pair. Enter file in which to save the key (/home/john/.ssh/identity):
~]$ ssh-keygen -t rsa1 Generating public/private rsa1 key pair. Enter file in which to save the key (/home/john/.ssh/identity):Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Enter to confirm the default location (that is,
~/.ssh/identity) for the newly created key. - Enter a passphrase, and confirm it by entering it again when prompted to do so. For security reasons, avoid using the same password as you use to log into your account.After this, you will be presented with a message similar to this:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Change the permissions of the
~/.ssh/directory:chmod 700 ~/.ssh
~]$ chmod 700 ~/.sshCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the content of
~/.ssh/identity.pubinto the~/.ssh/authorized_keyson the machine to which you want to connect, appending it to its end if the file already exists. - Change the permissions of the
~/.ssh/authorized_keysfile using the following command:chmod 600 ~/.ssh/authorized_keys
~]$ chmod 600 ~/.ssh/authorized_keysCopy to Clipboard Copied! Toggle word wrap Toggle overflow
See Section 14.2.4.2, “Configuring ssh-agent” for information on how to set up your system to remember the passphrase.
Important
Never share your private key with anybody; it is for your personal use only.
14.2.4.2. Configuring ssh-agent
링크 복사링크가 클립보드에 복사되었습니다!
To store your passphrase so that you do not have to enter it each time you initiate a connection with a remote machine, you can use the
ssh-agent authentication agent. If you are running GNOME, you can configure it to prompt you for your passphrase whenever you log in and remember it during the whole session. Otherwise you can store the passphrase for a certain shell prompt.
To save your passphrase during your GNOME session, follow these steps:
- Make sure you have the openssh-askpass package installed. If not, see Section 8.2.4, “Installing Packages” for more information on how to install new packages in Red Hat Enterprise Linux.
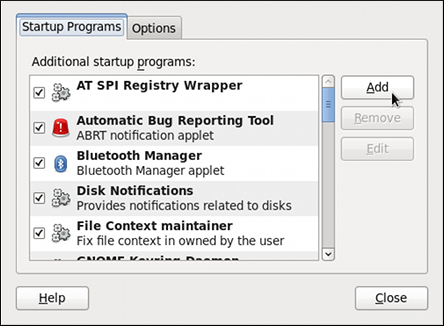
- Select
from the panel. The Startup Applications Preferences will be started, and the tab containing a list of available startup programs will be shown by default. Figure 14.1. Startup Applications Preferences
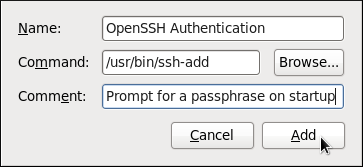
- Click the button on the right, and enter
/usr/bin/ssh-addin the Command field.Figure 14.2. Adding new application
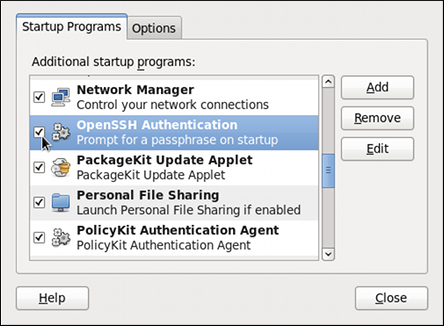
- Click and make sure the check box next to the newly added item is selected.
Figure 14.3. Enabling the application
- Log out and then log back in. A dialog box will appear prompting you for your passphrase. From this point on, you should not be prompted for a password by
ssh,scp, orsftp.Figure 14.4. Entering a passphrase
To save your passphrase for a certain shell prompt, use the following command:
ssh-add Enter passphrase for /home/john/.ssh/id_rsa:
~]$ ssh-add
Enter passphrase for /home/john/.ssh/id_rsa:
Note that when you log out, your passphrase will be forgotten. You must execute the command each time you log in to a virtual console or a terminal window.
14.2.4.3. Multiple required methods of authentication for sshd
링크 복사링크가 클립보드에 복사되었습니다!
For higher security, SSH can require multiple methods of authentication to log in successfully, for example both a passphrase and a public key. Set the
RequiredAuthentications2 option in the /etc/ssh/sshd_config file as desired, for example by running:
echo "RequiredAuthentications2 publickey,password" >> /etc/ssh/sshd_config
~]# echo "RequiredAuthentications2 publickey,password" >> /etc/ssh/sshd_config
For more information on the available options, see the
sshd_config(5) manual page.