This documentation is for a release that is no longer maintained
See documentation for the latest supported version 3 or the latest supported version 4.9.2. 使用 RBAC 定义和应用权限
理解并应用基于角色的访问控制。
9.2.1. RBAC 概述
基于角色的访问控制 (RBAC) 对象决定是否允许用户在项目内执行给定的操作。
集群管理员可以使用集群角色和绑定来控制谁对 OpenShift Container Platform 平台本身和所有项目具有各种访问权限等级。
开发人员可以使用本地角色和绑定来控制谁有权访问他们的项目。请注意,授权是与身份验证分开的一个步骤,身份验证更在于确定执行操作的人的身份。
授权通过使用以下几项来管理:
| 授权对象 | 描述 |
|---|---|
| 规则 |
一组对象上允许的操作集合。例如,用户或服务帐户能否 |
| 角色 | 规则的集合。可以将用户和组关联或绑定到多个角色。 |
| 绑定 | 用户和/组与角色之间的关联。 |
控制授权的 RBAC 角色和绑定有两个级别:
| RBAC 级别 | 描述 |
|---|---|
| 集群 RBAC | 对所有项目均适用的角色和绑定。集群角色存在于集群范围,集群角色绑定只能引用集群角色。 |
| 本地 RBAC | 作用于特定项目的角色和绑定。虽然本地角色只存在于单个项目中,但本地角色绑定可以同时引用集群和本地角色。 |
集群角色绑定是存在于集群级别的绑定。角色绑定存在于项目级别。集群角色 view 必须使用本地角色绑定来绑定到用户,以便该用户能够查看项目。只有集群角色不提供特定情形所需的权限集合时才应创建本地角色。
这种双级分级结构允许通过集群角色在多个项目间重复使用,同时允许通过本地角色在个别项目中自定义。
在评估过程中,同时使用集群角色绑定和本地角色绑定。例如:
- 选中集群范围的“allow”规则。
- 选中本地绑定的“allow”规则。
- 默认为拒绝。
9.2.1.1. 默认集群角色
OpenShift Container Platform 包括了一组默认的集群角色,您可以在集群范围或本地将它们绑定到用户和组。
不建议手动修改默认集群角色。对这些系统角色的修改可能会阻止集群正常工作。
| 默认集群角色 | 描述 |
|---|---|
|
|
项目管理者。如果在本地绑定中使用,则 |
|
| 此用户可以获取有关项目和用户的基本信息。 |
|
| 此超级用户可以在任意项目中执行任何操作。当使用本地绑定来绑定一个用户时,这些用户可以完全控制项目中每一资源的配额和所有操作。 |
|
| 此用户可以获取基本的集群状态信息。 |
|
| 用户可以获取或查看大多数对象,但不能修改它们。 |
|
| 此用户可以修改项目中大多数对象,但无权查看或修改角色或绑定。 |
|
| 此用户可以创建自己的项目。 |
|
| 此用户无法进行任何修改,但可以查看项目中的大多数对象。不能查看或修改角色或绑定。 |
请注意本地和集群绑定之间的区别。例如,如果使用本地角色绑定将 cluster-admin 角色绑定到一个用户,这可能看似该用户具有了集群管理员的特权。事实并非如此。将 cluster-admin 绑定到项目里的某一用户,仅会将该项目的超级管理员特权授予这一用户。该用户具有集群角色 admin 的权限,以及该项目的一些额外权限,例如能够编辑项目的速率限制。通过 web 控制台 UI 操作时此绑定可能会令人混淆,因为它不会列出绑定到真正集群管理员的集群角色绑定。然而,它会列出可用来本地绑定 cluster-admin 的本地角色绑定。
下方展示了集群角色、本地角色、集群角色绑定、本地角色绑定、用户、组和服务帐户之间的关系。
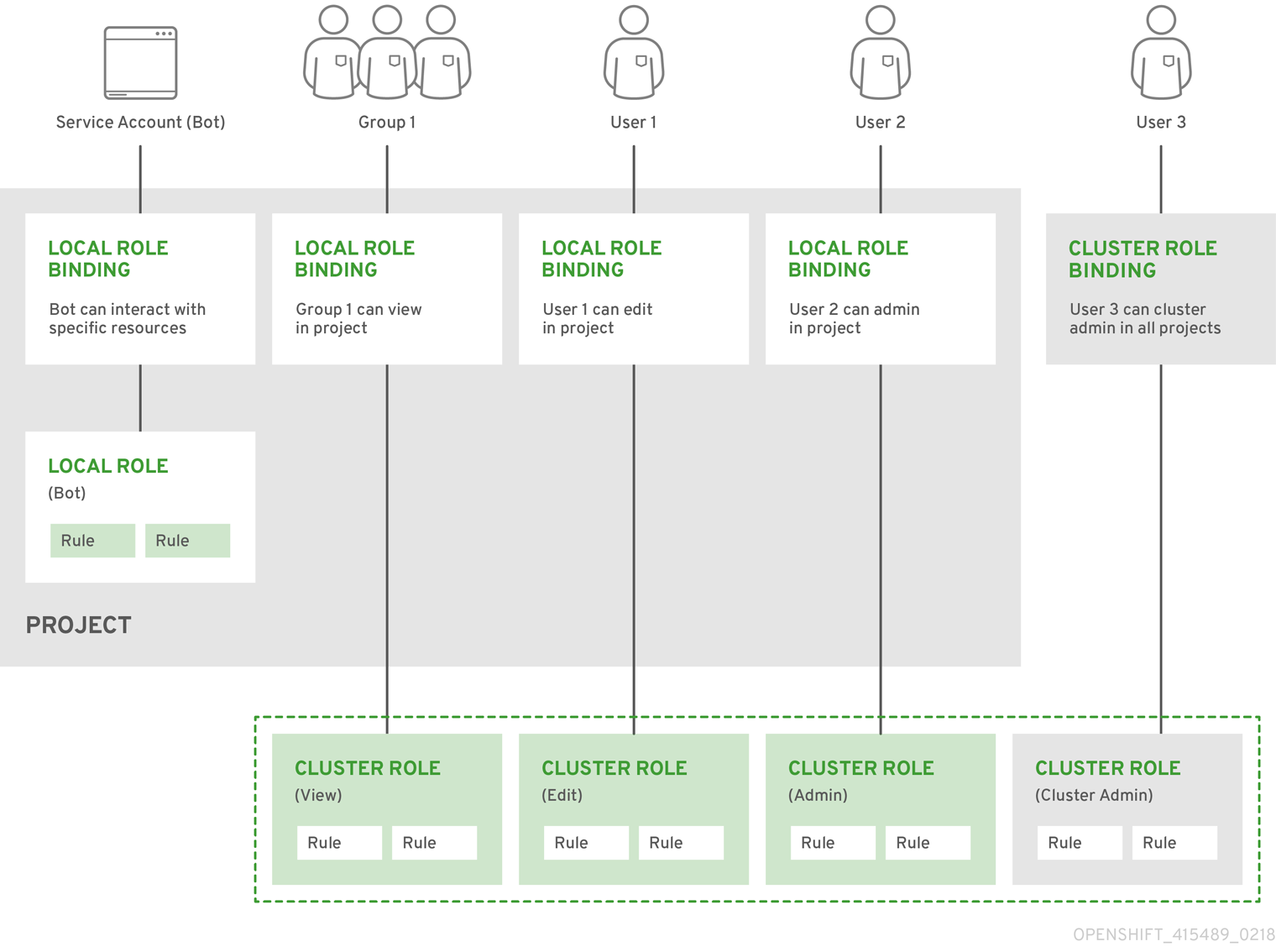
当它们被应用到一个角色时,get pods/exec, get pods/*, 和 get * 规则会授予执行权限。应用最小特权的原则,仅分配用户和代理所需的最小 RBAC 权限。如需更多信息,请参阅 RBAC 规则允许执行权限。
9.2.1.2. 评估授权
OpenShift Container Platform 使用以下几项来评估授权:
- 身份
- 用户名以及用户所属组的列表。
- 操作
您执行的操作。在大多数情况下,这由以下几项组成:
- 项目:您访问的项目。项目是一种附带额外注解的 Kubernetes 命名空间,使一个社区的用户可以在与其他社区隔离的前提下组织和管理其内容。
-
操作动词:操作本身:
get、list、create、update、delete、deletecollection或watch。 - 资源名称:您访问的 API 端点。
- 绑定
- 绑定的完整列表,用户或组与角色之间的关联。
OpenShift Container Platform 通过以下几个步骤评估授权:
- 使用身份和项目范围操作来查找应用到用户或所属组的所有绑定。
- 使用绑定来查找应用的所有角色。
- 使用角色来查找应用的所有规则。
- 针对每一规则检查操作,以查找匹配项。
- 如果未找到匹配的规则,则默认拒绝该操作。
请记住,用户和组可以同时关联或绑定到多个角色。
项目管理员可以使用 CLI 查看本地角色和绑定信息,包括与每个角色关联的操作动词和资源的一览表。
通过本地绑定来绑定到项目管理员的集群角色会限制在一个项目内。不会像授权给 cluster-admin 或 system:admin 的集群角色那样在集群范围绑定。
集群角色是在集群级别定义的角色,但可在集群级别或项目级别进行绑定。
9.2.1.2.1. 集群角色聚合
默认的 admin、edit、view 和 cluster-reader 集群角色支持集群角色聚合,其中每个角色的集群规则可在创建了新规则时动态更新。只有通过创建自定义资源扩展 Kubernetes API 时,此功能才有意义。
9.2.2. 项目和命名空间
Kubernetes 命名空间提供设定集群中资源范围的机制。Kubernetes 文档中提供有关命名空间的更多信息。
命名空间为以下对象提供唯一范围:
- 指定名称的资源,以避免基本命名冲突。
- 委派给可信用户的管理授权。
- 限制社区资源消耗的能力。
系统中的大多数对象都通过命名空间来设定范围,但一些对象不在此列且没有命名空间,如节点和用户。
项目是附带额外注解的 Kubernetes 命名空间,是管理常规用户资源访问权限的集中载体。通过项目,一个社区的用户可以在与其他社区隔离的前提下组织和管理其内容。用户必须由管理员授予对项目的访问权限;或者,如果用户有权创建项目,则自动具有自己创建项目的访问权限。
项目可以有单独的 name、displayName 和 description。
-
其中必备的
name是项目的唯一标识符,在使用 CLI 工具或 API 时最常见。名称长度最多为 63 个字符。 -
可选的
displayName是项目在 web 控制台中的显示形式(默认为name)。 -
可选的
description可以为项目提供更加详细的描述,也可显示在 web 控制台中。
每个项目限制了自己的一组:
| 对象 | 描述 |
|---|---|
|
| Pod、服务和复制控制器等。 |
|
| 用户能否对对象执行操作的规则。 |
|
| 对各种对象进行限制的配额。 |
|
| 服务帐户自动使用项目中对象的指定访问权限进行操作。 |
集群管理员可以创建项目,并可将项目的管理权限委派给用户社区的任何成员。集群管理员也可以允许开发人员创建自己的项目。
开发人员和管理员可以使用 CLI 或 Web 控制台与项目交互。
9.2.3. 默认项目
OpenShift Container Platform 附带若干默认项目,名称以 openshift-- 开头的项目对用户而言最为重要。这些项目托管作为 Pod 运行的主要组件和其他基础架构组件。在这些命名空间中创建的带有关键 (critical) Pod 注解的 Pod 是很重要的,它们可以保证被 kubelet 准入。在这些命名空间中为主要组件创建的 Pod 已标记为“critical”。
您无法将 SCC 分配给在以下某一默认命名空间中创建的 Pod: default、kube-system、kube-public、openshift-node、openshift-infra、openshift。您不能使用这些命名空间用来运行 pod 或服务。
9.2.4. 查看集群角色和绑定
通过 oc describe 命令,可以使用 oc CLI 来查看集群角色和绑定。
先决条件
-
安装
ocCLI。 - 获取查看集群角色和绑定的权限。
在集群范围内绑定了 cluster-admin 默认集群角色的用户可以对任何资源执行任何操作,包括查看集群角色和绑定。
流程
查看集群角色及其关联的规则集:
oc describe clusterrole.rbac
$ oc describe clusterrole.rbacCopy to Clipboard Copied! Toggle word wrap Toggle overflow 输出示例
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 查看当前的集群角色绑定集合,这显示绑定到不同角色的用户和组:
oc describe clusterrolebinding.rbac
$ oc describe clusterrolebinding.rbacCopy to Clipboard Copied! Toggle word wrap Toggle overflow 输出示例
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2.5. 查看本地角色和绑定
使用 oc describe 命令通过 oc CLI 来查看本地角色和绑定。
先决条件
-
安装
ocCLI。 获取查看本地角色和绑定的权限:
-
在集群范围内绑定了
cluster-admin默认集群角色的用户可以对任何资源执行任何操作,包括查看本地角色和绑定。 -
本地绑定了
admin默认集群角色的用户可以查看并管理项目中的角色和绑定。
-
在集群范围内绑定了
流程
查看当前本地角色绑定集合,这显示绑定到当前项目的不同角色的用户和组:
oc describe rolebinding.rbac
$ oc describe rolebinding.rbacCopy to Clipboard Copied! Toggle word wrap Toggle overflow 要查其他项目的本地角色绑定,请向命令中添加
-n标志:oc describe rolebinding.rbac -n joe-project
$ oc describe rolebinding.rbac -n joe-projectCopy to Clipboard Copied! Toggle word wrap Toggle overflow 输出示例
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2.6. 向用户添加角色
可以使用 oc adm 管理员 CLI 管理角色和绑定。
将角色绑定或添加到用户或组可让用户或组具有该角色授予的访问权限。您可以使用 oc adm policy 命令向用户和组添加和移除角色。
您可以将任何默认集群角色绑定到项目中的本地用户或组。
流程
向指定项目中的用户添加角色:
oc adm policy add-role-to-user <role> <user> -n <project>
$ oc adm policy add-role-to-user <role> <user> -n <project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 例如,您可以运行以下命令,将
admin角色添加到joe项目中的alice用户:oc adm policy add-role-to-user admin alice -n joe
$ oc adm policy add-role-to-user admin alice -n joeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 提示您还可以应用以下 YAML 向用户添加角色:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 查看本地角色绑定,并在输出中验证添加情况:
oc describe rolebinding.rbac -n <project>
$ oc describe rolebinding.rbac -n <project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 例如,查看
joe项目的本地角色绑定:oc describe rolebinding.rbac -n joe
$ oc describe rolebinding.rbac -n joeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 输出示例
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
alice用户已添加到adminsRoleBinding。
9.2.7. 创建本地角色
您可以为项目创建本地角色,然后将其绑定到用户。
流程
要为项目创建本地角色,请运行以下命令:
oc create role <name> --verb=<verb> --resource=<resource> -n <project>
$ oc create role <name> --verb=<verb> --resource=<resource> -n <project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 在此命令中,指定:
-
<name>,本地角色的名称 -
<verb>,以逗号分隔的、应用到角色的操作动词列表 -
<resource>,角色应用到的资源 -
<project>,项目名称
例如,要创建一个本地角色来允许用户查看
blue项目中的 Pod,请运行以下命令:oc create role podview --verb=get --resource=pod -n blue
$ oc create role podview --verb=get --resource=pod -n blueCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
要将新角色绑定到用户,运行以下命令:
oc adm policy add-role-to-user podview user2 --role-namespace=blue -n blue
$ oc adm policy add-role-to-user podview user2 --role-namespace=blue -n blueCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2.8. 创建集群角色
您可以创建集群角色。
流程
要创建集群角色,请运行以下命令:
oc create clusterrole <name> --verb=<verb> --resource=<resource>
$ oc create clusterrole <name> --verb=<verb> --resource=<resource>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 在此命令中,指定:
-
<name>,本地角色的名称 -
<verb>,以逗号分隔的、应用到角色的操作动词列表 -
<resource>,角色应用到的资源
例如,要创建一个集群角色来允许用户查看 Pod,请运行以下命令:
oc create clusterrole podviewonly --verb=get --resource=pod
$ oc create clusterrole podviewonly --verb=get --resource=podCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
9.2.9. 本地角色绑定命令
在使用以下操作为本地角色绑定管理用户或组的关联角色时,可以使用 -n 标志来指定项目。如果未指定,则使用当前项目。
您可以使用以下命令进行本地 RBAC 管理。
| 命令 | 描述 |
|---|---|
|
| 指出哪些用户可以对某一资源执行某种操作。 |
|
| 将指定角色绑定到当前项目中的指定用户。 |
|
| 从当前项目中的指定用户移除指定角色。 |
|
| 移除当前项目中的指定用户及其所有角色。 |
|
| 将给定角色绑定到当前项目中的指定组。 |
|
| 从当前项目中的指定组移除给定角色。 |
|
| 移除当前项目中的指定组及其所有角色。 |
9.2.10. 集群角色绑定命令
您也可以使用以下操作管理集群角色绑定。因为集群角色绑定使用没有命名空间的资源,所以这些操作不使用 -n 标志。
| 命令 | 描述 |
|---|---|
|
| 将给定角色绑定到集群中所有项目的指定用户。 |
|
| 从集群中所有项目的指定用户移除给定角色。 |
|
| 将给定角色绑定到集群中所有项目的指定组。 |
|
| 从集群中所有项目的指定组移除给定角色。 |
9.2.11. 创建集群管理员
需要具备 cluster-admin 角色才能在 OpenShift Container Platform 集群上执行管理员级别的任务,例如修改集群资源。
先决条件
- 您必须已创建了要定义为集群管理员的用户。
流程
将用户定义为集群管理员:
oc adm policy add-cluster-role-to-user cluster-admin <user>
$ oc adm policy add-cluster-role-to-user cluster-admin <user>Copy to Clipboard Copied! Toggle word wrap Toggle overflow