29.3. Options
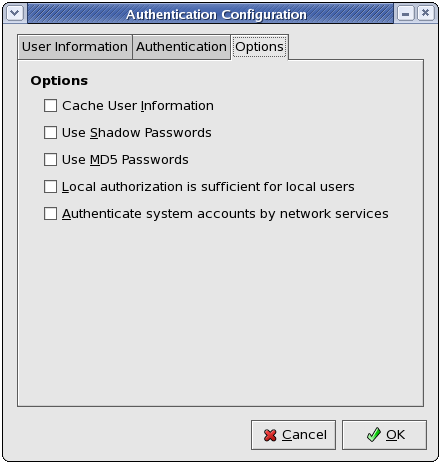
Figure 29.3. Options
Select this option to enable the name service cache daemon (nscd) and configure it to start at boot time.
nscd package must be installed for this option to work. For more information about nscd, refer to its man page using the command man nscd.
Select this option to store passwords in shadow password format in the /etc/shadow file instead of /etc/passwd. Shadow passwords are enabled by default during installation and are highly recommended to increase the security of the system.
shadow-utils package must be installed for this option to work. For more information about shadow passwords, refer to Section 37.6, “Shadow Passwords”.
Select this option to enable MD5 passwords, which allows passwords to be up to 256 characters instead of eight characters or less. It is selected by default during installation and is highly recommended for increased security.