This documentation is for a release that is no longer maintained
See documentation for the latest supported version 3 or the latest supported version 4.Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 7. Preparing to update a cluster with manually maintained credentials
The Cloud Credential Operator (CCO) Upgradable status for a cluster with manually maintained credentials is False by default.
-
For minor releases, for example, from 4.10 to 4.11, this status prevents you from updating until you have addressed any updated permissions and annotated the
CloudCredentialresource to indicate that the permissions are updated as needed for the next version. This annotation changes theUpgradablestatus toTrue. - For z-stream releases, for example, from 4.10.0 to 4.10.1, no permissions are added or changed, so the update is not blocked.
Before updating a cluster with manually maintained credentials, you must accommodate any new or changed credentials in the release image for the version of OpenShift Container Platform you are updating to.
7.1. Update requirements for clusters with manually maintained credentials
Before you update a cluster that uses manually maintained credentials with the Cloud Credential Operator (CCO), you must update the cloud provider resources for the new release.
If the cloud credential management for your cluster was configured using the CCO utility (ccoctl), use the ccoctl utility to update the resources. Clusters that were configured to use manual mode without the ccoctl utility require manual updates for the resources.
After updating the cloud provider resources, you must update the upgradeable-to annotation for the cluster to indicate that it is ready to update.
The process to update the cloud provider resources and the upgradeable-to annotation can only be completed by using command line tools.
7.1.1. Cloud credential configuration options and update requirements by platform type
Some platforms only support using the CCO in one mode. For clusters that are installed on those platforms, the platform type determines the credentials update requirements.
For platforms that support using the CCO in multiple modes, you must determine which mode the cluster is configured to use and take the required actions for that configuration.
Figure 7.1. Credentials update requirements by platform type
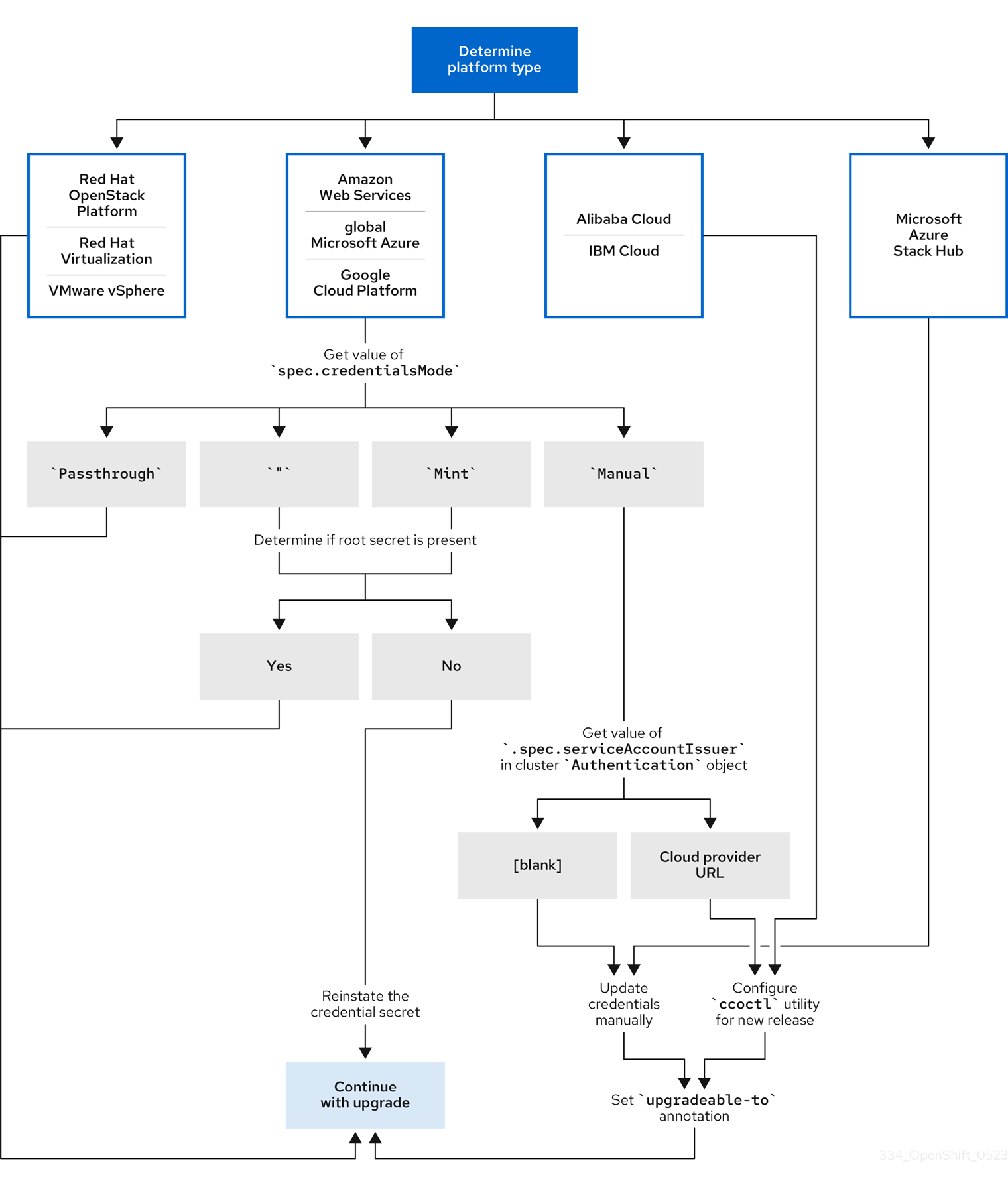
- Red Hat OpenStack Platform (RHOSP), Red Hat Virtualization (RHV), and VMware vSphere
These platforms do not support using the CCO in manual mode. Clusters on these platforms handle changes in cloud provider resources automatically and do not require an update to the
upgradeable-toannotation.Administrators of clusters on these platforms should skip the manually maintained credentials section of the update process.
- Alibaba Cloud and IBM Cloud
Clusters installed on these platforms are configured using the
ccoctlutility.Administrators of clusters on these platforms must take the following actions:
-
Configure the
ccoctlutility for the new release. -
Use the
ccoctlutility to update the cloud provider resources. -
Indicate that the cluster is ready to update with the
upgradeable-toannotation.
-
Configure the
- Microsoft Azure Stack Hub
These clusters use manual mode with long-lived credentials and do not use the
ccoctlutility.Administrators of clusters on these platforms must take the following actions:
- Manually update the cloud provider resources for the new release.
-
Indicate that the cluster is ready to update with the
upgradeable-toannotation.
- Amazon Web Services (AWS), global Microsoft Azure, and Google Cloud Platform (GCP)
Clusters installed on these platforms support multiple CCO modes.
The required update process depends on the mode that the cluster is configured to use. If you are not sure what mode the CCO is configured to use on your cluster, you can use the web console or the CLI to determine this information.
7.1.2. Determining the Cloud Credential Operator mode by using the web console
You can determine what mode the Cloud Credential Operator (CCO) is configured to use by using the web console.
Only Amazon Web Services (AWS), global Microsoft Azure, and Google Cloud Platform (GCP) clusters support multiple CCO modes.
Prerequisites
- You have access to an OpenShift Container Platform account with cluster administrator permissions.
Procedure
-
Log in to the OpenShift Container Platform web console as a user with the
cluster-adminrole. -
Navigate to Administration
Cluster Settings. - On the Cluster Settings page, select the Configuration tab.
- Under Configuration resource, select CloudCredential.
- On the CloudCredential details page, select the YAML tab.
In the YAML block, check the value of
spec.credentialsMode. The following values are possible, though not all are supported on all platforms:-
'': The CCO is operating in the default mode. In this configuration, the CCO operates in mint or passthrough mode, depending on the credentials provided during installation. -
Mint: The CCO is operating in mint mode. -
Passthrough: The CCO is operating in passthrough mode. -
Manual: The CCO is operating in manual mode.
ImportantTo determine the specific configuration of an AWS or GCP cluster that has a
spec.credentialsModeof'',Mint, orManual, you must investigate further.AWS and GCP clusters support using mint mode with the root secret deleted. If the cluster is specifically configured to use mint mode or uses mint mode by default, you must determine if the root secret is present on the cluster before updating.
An AWS or GCP cluster that uses manual mode might be configured to create and manage cloud credentials from outside of the cluster using the AWS Security Token Service (STS) or GCP Workload Identity. You can determine whether your cluster uses this strategy by examining the cluster
Authenticationobject.-
AWS or GCP clusters that use mint mode only: To determine whether the cluster is operating without the root secret, navigate to Workloads
Secrets and look for the root secret for your cloud provider. NoteEnsure that the Project dropdown is set to All Projects.
Expand Platform Secret name AWS
aws-credsGCP
gcp-credentials- If you see one of these values, your cluster is using mint or passthrough mode with the root secret present.
- If you do not see these values, your cluster is using the CCO in mint mode with the root secret removed.
AWS or GCP clusters that use manual mode only: To determine whether the cluster is configured to create and manage cloud credentials from outside of the cluster, you must check the cluster
Authenticationobject YAML values.-
Navigate to Administration
Cluster Settings. - On the Cluster Settings page, select the Configuration tab.
- Under Configuration resource, select Authentication.
- On the Authentication details page, select the YAML tab.
In the YAML block, check the value of the
.spec.serviceAccountIssuerparameter.-
A value that contains a URL that is associated with your cloud provider indicates that the CCO is using manual mode with AWS STS or GCP Workload Identity to create and manage cloud credentials from outside of the cluster. These clusters are configured using the
ccoctlutility. -
An empty value (
'') indicates that the cluster is using the CCO in manual mode but was not configured using theccoctlutility.
-
A value that contains a URL that is associated with your cloud provider indicates that the CCO is using manual mode with AWS STS or GCP Workload Identity to create and manage cloud credentials from outside of the cluster. These clusters are configured using the
-
Navigate to Administration
Next steps
- If you are updating a cluster that has the CCO operating in mint or passthrough mode and the root secret is present, you do not need to update any cloud provider resources and can continue to the next part of the update process.
- If your cluster is using the CCO in mint mode with the root secret removed, you must reinstate the credential secret with the administrator-level credential before continuing to the next part of the update process.
If your cluster was configured using the CCO utility (
ccoctl), you must take the following actions:-
Configure the
ccoctlutility for the new release and use it to update the cloud provider resources. -
Update the
upgradeable-toannotation to indicate that the cluster is ready to update.
-
Configure the
If your cluster is using the CCO in manual mode but was not configured using the
ccoctlutility, you must take the following actions:- Manually update the cloud provider resources for the new release.
-
Update the
upgradeable-toannotation to indicate that the cluster is ready to update.
7.1.3. Determining the Cloud Credential Operator mode by using the CLI
You can determine what mode the Cloud Credential Operator (CCO) is configured to use by using the CLI.
Only Amazon Web Services (AWS), global Microsoft Azure, and Google Cloud Platform (GCP) clusters support multiple CCO modes.
Prerequisites
- You have access to an OpenShift Container Platform account with cluster administrator permissions.
-
You have installed the OpenShift CLI (
oc).
Procedure
-
Log in to
ocon the cluster as a user with thecluster-adminrole. To determine the mode that the CCO is configured to use, enter the following command:
oc get cloudcredentials cluster \ -o=jsonpath={.spec.credentialsMode}$ oc get cloudcredentials cluster \ -o=jsonpath={.spec.credentialsMode}Copy to Clipboard Copied! Toggle word wrap Toggle overflow The following output values are possible, though not all are supported on all platforms:
-
'': The CCO is operating in the default mode. In this configuration, the CCO operates in mint or passthrough mode, depending on the credentials provided during installation. -
Mint: The CCO is operating in mint mode. -
Passthrough: The CCO is operating in passthrough mode. -
Manual: The CCO is operating in manual mode.
ImportantTo determine the specific configuration of an AWS or GCP cluster that has a
spec.credentialsModeof'',Mint, orManual, you must investigate further.AWS and GCP clusters support using mint mode with the root secret deleted. If the cluster is specifically configured to use mint mode or uses mint mode by default, you must determine if the root secret is present on the cluster before updating.
An AWS or GCP cluster that uses manual mode might be configured to create and manage cloud credentials from outside of the cluster using the AWS Security Token Service (STS) or GCP Workload Identity. You can determine whether your cluster uses this strategy by examining the cluster
Authenticationobject.-
AWS or GCP clusters that use mint mode only: To determine whether the cluster is operating without the root secret, run the following command:
oc get secret <secret_name> \ -n=kube-system
$ oc get secret <secret_name> \ -n=kube-systemCopy to Clipboard Copied! Toggle word wrap Toggle overflow where
<secret_name>isaws-credsfor AWS orgcp-credentialsfor GCP.If the root secret is present, the output of this command returns information about the secret. An error indicates that the root secret is not present on the cluster.
AWS or GCP clusters that use manual mode only: To determine whether the cluster is configured to create and manage cloud credentials from outside of the cluster, run the following command:
oc get authentication cluster \ -o jsonpath \ --template='{ .spec.serviceAccountIssuer }'$ oc get authentication cluster \ -o jsonpath \ --template='{ .spec.serviceAccountIssuer }'Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command displays the value of the
.spec.serviceAccountIssuerparameter in the clusterAuthenticationobject.-
An output of a URL that is associated with your cloud provider indicates that the CCO is using manual mode with AWS STS or GCP Workload Identity to create and manage cloud credentials from outside of the cluster. These clusters are configured using the
ccoctlutility. -
An empty output indicates that the cluster is using the CCO in manual mode but was not configured using the
ccoctlutility.
-
An output of a URL that is associated with your cloud provider indicates that the CCO is using manual mode with AWS STS or GCP Workload Identity to create and manage cloud credentials from outside of the cluster. These clusters are configured using the
Next steps
- If you are updating a cluster that has the CCO operating in mint or passthrough mode and the root secret is present, you do not need to update any cloud provider resources and can continue to the next part of the update process.
- If your cluster is using the CCO in mint mode with the root secret removed, you must reinstate the credential secret with the administrator-level credential before continuing to the next part of the update process.
If your cluster was configured using the CCO utility (
ccoctl), you must take the following actions:-
Configure the
ccoctlutility for the new release and use it to update the cloud provider resources. -
Update the
upgradeable-toannotation to indicate that the cluster is ready to update.
-
Configure the
If your cluster is using the CCO in manual mode but was not configured using the
ccoctlutility, you must take the following actions:- Manually update the cloud provider resources for the new release.
-
Update the
upgradeable-toannotation to indicate that the cluster is ready to update.
7.2. Configuring the Cloud Credential Operator utility for a cluster update
To upgrade a cluster that uses the Cloud Credential Operator (CCO) in manual mode to create and manage cloud credentials from outside of the cluster, extract and prepare the CCO utility (ccoctl) binary.
The ccoctl utility is a Linux binary that must run in a Linux environment.
Prerequisites
- You have access to an OpenShift Container Platform account with cluster administrator access.
-
You have installed the OpenShift CLI (
oc).
-
Your cluster was configured using the
ccoctlutility to create and manage cloud credentials from outside of the cluster.
Procedure
Obtain the OpenShift Container Platform release image:
RELEASE_IMAGE=$(./openshift-install version | awk '/release image/ {print $3}')$ RELEASE_IMAGE=$(./openshift-install version | awk '/release image/ {print $3}')Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the CCO container image from the OpenShift Container Platform release image:
CCO_IMAGE=$(oc adm release info --image-for='cloud-credential-operator' $RELEASE_IMAGE)
$ CCO_IMAGE=$(oc adm release info --image-for='cloud-credential-operator' $RELEASE_IMAGE)Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteEnsure that the architecture of the
$RELEASE_IMAGEmatches the architecture of the environment in which you will use theccoctltool.Extract the
ccoctlbinary from the CCO container image within the OpenShift Container Platform release image:oc image extract $CCO_IMAGE --file="/usr/bin/ccoctl" -a ~/.pull-secret
$ oc image extract $CCO_IMAGE --file="/usr/bin/ccoctl" -a ~/.pull-secretCopy to Clipboard Copied! Toggle word wrap Toggle overflow Change the permissions to make
ccoctlexecutable:chmod 775 ccoctl
$ chmod 775 ccoctlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
To verify that
ccoctlis ready to use, display the help file:ccoctl --help
$ ccoctl --helpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Output of
ccoctl --helpCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.3. Updating cloud provider resources with the Cloud Credential Operator utility
The process for upgrading an OpenShift Container Platform cluster that was configured using the CCO utility (ccoctl) is similar to creating the cloud provider resources during installation.
By default, ccoctl creates objects in the directory in which the commands are run. To create the objects in a different directory, use the --output-dir flag. This procedure uses <path_to_ccoctl_output_dir> to refer to this directory.
On AWS clusters, some ccoctl commands make AWS API calls to create or modify AWS resources. You can use the --dry-run flag to avoid making API calls. Using this flag creates JSON files on the local file system instead. You can review and modify the JSON files and then apply them with the AWS CLI tool using the --cli-input-json parameters.
Prerequisites
- Obtain the OpenShift Container Platform release image for the version that you are upgrading to.
-
Extract and prepare the
ccoctlbinary from the release image.
Procedure
Extract the list of
CredentialsRequestcustom resources (CRs) from the OpenShift Container Platform release image by running the following command:oc adm release extract --credentials-requests \ --cloud=<provider_type> \ --to=<path_to_directory_with_list_of_credentials_requests>/credrequests \ quay.io/<path_to>/ocp-release:<version>
$ oc adm release extract --credentials-requests \ --cloud=<provider_type> \ --to=<path_to_directory_with_list_of_credentials_requests>/credrequests \ quay.io/<path_to>/ocp-release:<version>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
-
<provider_type>is the value for your cloud provider. Valid values arealibabacloud,aws,gcp, andibmcloud. -
credrequestsis the directory where the list ofCredentialsRequestobjects is stored. This command creates the directory if it does not exist.
-
For each
CredentialsRequestCR in the release image, ensure that a namespace that matches the text in thespec.secretRef.namespacefield exists in the cluster. This field is where the generated secrets that hold the credentials configuration are stored.Sample AWS
CredentialsRequestobjectCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- This field indicates the namespace which needs to exist to hold the generated secret.
The
CredentialsRequestCRs for other platforms have a similar format with different platform-specific values.For any
CredentialsRequestCR for which the cluster does not already have a namespace with the name specified inspec.secretRef.namespace, create the namespace:oc create namespace <component_namespace>
$ oc create namespace <component_namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
ccoctltool to process allCredentialsRequestobjects in thecredrequestsdirectory by running the command for your cloud provider. The following commands processCredentialsRequestobjects:-
Alibaba Cloud:
ccoctl alibabacloud create-ram-users -
Amazon Web Services (AWS):
ccoctl aws create-iam-roles -
Google Cloud Platform (GCP):
ccoctl gcp create-all -
IBM Cloud:
ccoctl ibmcloud create-service-id
ImportantRefer to the
ccoctlutility instructions in the installation content for your cloud provider for important platform-specific details about the required arguments and special considerations.For each
CredentialsRequestobject,ccoctlcreates the required provider resources and a permissions policy as defined in eachCredentialsRequestobject from the OpenShift Container Platform release image.-
Alibaba Cloud:
Apply the secrets to your cluster:
ls <path_to_ccoctl_output_dir>/manifests/*-credentials.yaml | xargs -I{} oc apply -f {}$ ls <path_to_ccoctl_output_dir>/manifests/*-credentials.yaml | xargs -I{} oc apply -f {}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
You can verify that the required provider resources and permissions policies are created by querying the cloud provider. For more information, refer to your cloud provider documentation on listing roles or service accounts.
Next steps
-
Update the
upgradeable-toannotation to indicate that the cluster is ready to upgrade.
7.4. Updating cloud provider resources with manually maintained credentials
Before upgrading a cluster with manually maintained credentials, you must create any new credentials for the release image that you are upgrading to. You must also review the required permissions for existing credentials and accommodate any new permissions requirements in the new release for those components.
Procedure
Extract and examine the
CredentialsRequestcustom resource for the new release.The "Manually creating IAM" section of the installation content for your cloud provider explains how to obtain and use the credentials required for your cloud.
Update the manually maintained credentials on your cluster:
-
Create new secrets for any
CredentialsRequestcustom resources that are added by the new release image. -
If the
CredentialsRequestcustom resources for any existing credentials that are stored in secrets have changed permissions requirements, update the permissions as required.
-
Create new secrets for any
Next steps
-
Update the
upgradeable-toannotation to indicate that the cluster is ready to upgrade.
7.5. Indicating that the cluster is ready to upgrade
The Cloud Credential Operator (CCO) Upgradable status for a cluster with manually maintained credentials is False by default.
Prerequisites
-
For the release image that you are upgrading to, you have processed any new credentials manually or by using the Cloud Credential Operator utility (
ccoctl). -
You have installed the OpenShift CLI (
oc).
Procedure
-
Log in to
ocon the cluster as a user with thecluster-adminrole. Edit the
CloudCredentialresource to add anupgradeable-toannotation within themetadatafield by running the following command:oc edit cloudcredential cluster
$ oc edit cloudcredential clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Text to add
... metadata: annotations: cloudcredential.openshift.io/upgradeable-to: <version_number> ...... metadata: annotations: cloudcredential.openshift.io/upgradeable-to: <version_number> ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Where
<version_number>is the version that you are upgrading to, in the formatx.y.z. For example, use4.10.2for OpenShift Container Platform 4.10.2.It may take several minutes after adding the annotation for the upgradeable status to change.
Verification
-
In the Administrator perspective of the web console, navigate to Administration
Cluster Settings. To view the CCO status details, click cloud-credential in the Cluster Operators list.
-
If the Upgradeable status in the Conditions section is False, verify that the
upgradeable-toannotation is free of typographical errors.
-
If the Upgradeable status in the Conditions section is False, verify that the
- When the Upgradeable status in the Conditions section is True, begin the OpenShift Container Platform upgrade.