2.13.
2.13.1.
2.13.1.1.
2.13.1.1.1.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc create -n <namespace> -f <policy.yaml>
$ oc create -n <namespace> -f <policy.yaml>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.1.1.2.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc create -n <namespace> -f <destination-rule.yaml>
$ oc create -n <namespace> -f <destination-rule.yaml>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.1.1.3.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.1.2.
그림 2.5.

[D]
그림 2.6.

[D]
그림 2.7.
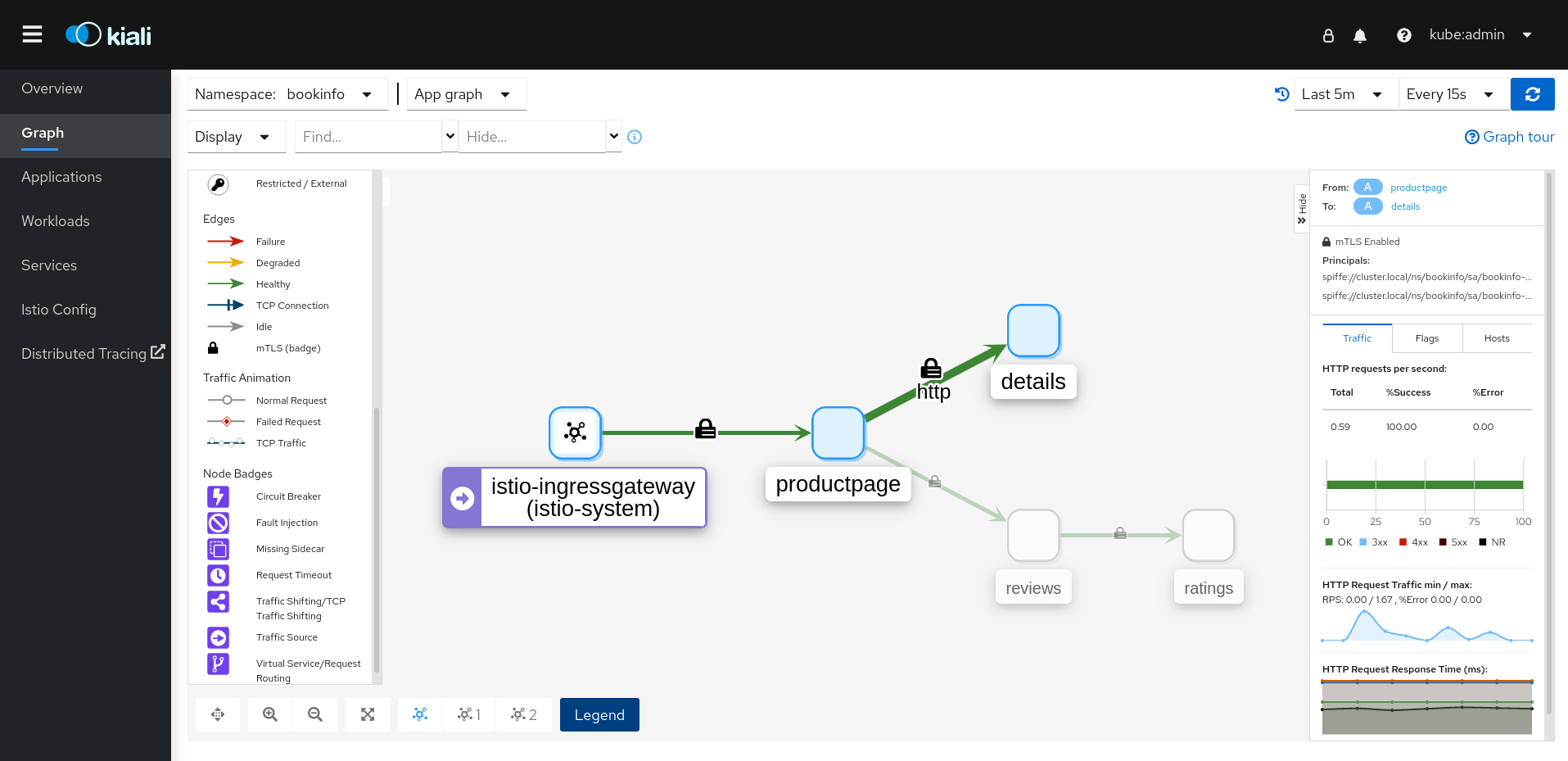
[D]
2.13.2.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc create -n istio-system -f <filename>
$ oc create -n istio-system -f <filename>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.2.1.
2.13.2.1.1.
2.13.2.1.2.
2.13.2.2.
2.13.2.3.
2.13.3.
2.13.4.
$ oc edit smcp <smcp-name>
$ oc edit smcp <smcp-name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.5.
2.13.5.1.
oc create secret generic cacerts -n istio-system --from-file=<path>/ca-cert.pem \ --from-file=<path>/ca-key.pem --from-file=<path>/root-cert.pem \ --from-file=<path>/cert-chain.pem$ oc create secret generic cacerts -n istio-system --from-file=<path>/ca-cert.pem \ --from-file=<path>/ca-key.pem --from-file=<path>/root-cert.pem \ --from-file=<path>/cert-chain.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc -n istio-system delete pods -l 'app in (istiod,istio-ingressgateway, istio-egressgateway)'
$ oc -n istio-system delete pods -l 'app in (istiod,istio-ingressgateway, istio-egressgateway)'Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc -n info delete pods --all
$ oc -n info delete pods --allCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc get pods -n info
$ oc get pods -n infoCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.5.2.
sleep 60 oc -n info exec "$(oc -n bookinfo get pod -l app=productpage -o jsonpath={.items..metadata.name})" -c istio-proxy -- openssl s_client -showcerts -connect details:9080 > bookinfo-proxy-cert.txt sed -n '/-----BEGIN CERTIFICATE-----/{:start /-----END CERTIFICATE-----/!{N;b start};/.*/p}' info-proxy-cert.txt > certs.pem awk 'BEGIN {counter=0;} /BEGIN CERT/{counter++} { print > "proxy-cert-" counter ".pem"}' < certs.pem$ sleep 60 $ oc -n info exec "$(oc -n bookinfo get pod -l app=productpage -o jsonpath={.items..metadata.name})" -c istio-proxy -- openssl s_client -showcerts -connect details:9080 > bookinfo-proxy-cert.txt $ sed -n '/-----BEGIN CERTIFICATE-----/{:start /-----END CERTIFICATE-----/!{N;b start};/.*/p}' info-proxy-cert.txt > certs.pem $ awk 'BEGIN {counter=0;} /BEGIN CERT/{counter++} { print > "proxy-cert-" counter ".pem"}' < certs.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow openssl x509 -in <path>/root-cert.pem -text -noout > /tmp/root-cert.crt.txt
$ openssl x509 -in <path>/root-cert.pem -text -noout > /tmp/root-cert.crt.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow openssl x509 -in ./proxy-cert-3.pem -text -noout > /tmp/pod-root-cert.crt.txt
$ openssl x509 -in ./proxy-cert-3.pem -text -noout > /tmp/pod-root-cert.crt.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow diff -s /tmp/root-cert.crt.txt /tmp/pod-root-cert.crt.txt
$ diff -s /tmp/root-cert.crt.txt /tmp/pod-root-cert.crt.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow openssl x509 -in <path>/ca-cert.pem -text -noout > /tmp/ca-cert.crt.txt
$ openssl x509 -in <path>/ca-cert.pem -text -noout > /tmp/ca-cert.crt.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow openssl x509 -in ./proxy-cert-2.pem -text -noout > /tmp/pod-cert-chain-ca.crt.txt
$ openssl x509 -in ./proxy-cert-2.pem -text -noout > /tmp/pod-cert-chain-ca.crt.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow diff -s /tmp/ca-cert.crt.txt /tmp/pod-cert-chain-ca.crt.txt
$ diff -s /tmp/ca-cert.crt.txt /tmp/pod-cert-chain-ca.crt.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow openssl verify -CAfile <(cat <path>/ca-cert.pem <path>/root-cert.pem) ./proxy-cert-1.pem
$ openssl verify -CAfile <(cat <path>/ca-cert.pem <path>/root-cert.pem) ./proxy-cert-1.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.5.3.
oc delete secret cacerts -n istio-system
$ oc delete secret cacerts -n istio-systemCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.13.6.
2.13.6.1.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고oc apply -f cluster-issuer.yaml
$ oc apply -f cluster-issuer.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc apply -n istio-system -f istio-ca.yaml
$ oc apply -n istio-system -f istio-ca.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
helm install istio-csr jetstack/cert-manager-istio-csr \ -n istio-system \ -f deploy/examples/cert-manager/istio-csr/istio-csr.yaml$ helm install istio-csr jetstack/cert-manager-istio-csr \ -n istio-system \ -f deploy/examples/cert-manager/istio-csr/istio-csr.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc apply -f mesh.yaml -n istio-system
$ oc apply -f mesh.yaml -n istio-systemCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
oc new-project <namespace>
$ oc new-project <namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc apply -f https://raw.githubusercontent.com/maistra/istio/maistra-2.4/samples/httpbin/httpbin.yaml
$ oc apply -f https://raw.githubusercontent.com/maistra/istio/maistra-2.4/samples/httpbin/httpbin.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow oc apply -f https://raw.githubusercontent.com/maistra/istio/maistra-2.4/samples/sleep/sleep.yaml
$ oc apply -f https://raw.githubusercontent.com/maistra/istio/maistra-2.4/samples/sleep/sleep.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow oc exec "$(oc get pod -l app=sleep -n <namespace> \ -o jsonpath={.items..metadata.name})" -c sleep -n <namespace> -- \ curl http://httpbin.<namespace>:8000/ip -s -o /dev/null \ -w "%{http_code}\n"$ oc exec "$(oc get pod -l app=sleep -n <namespace> \ -o jsonpath={.items..metadata.name})" -c sleep -n <namespace> -- \ curl http://httpbin.<namespace>:8000/ip -s -o /dev/null \ -w "%{http_code}\n"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 200
200Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc apply -n <namespace> -f https://raw.githubusercontent.com/maistra/istio/maistra-2.4/samples/httpbin/httpbin-gateway.yaml
$ oc apply -n <namespace> -f https://raw.githubusercontent.com/maistra/istio/maistra-2.4/samples/httpbin/httpbin-gateway.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow INGRESS_HOST=$(oc -n istio-system get routes istio-ingressgateway -o jsonpath='{.spec.host}')INGRESS_HOST=$(oc -n istio-system get routes istio-ingressgateway -o jsonpath='{.spec.host}')Copy to Clipboard Copied! Toggle word wrap Toggle overflow curl -s -I http://$INGRESS_HOST/headers -o /dev/null -w "%{http_code}" -s$ curl -s -I http://$INGRESS_HOST/headers -o /dev/null -w "%{http_code}" -sCopy to Clipboard Copied! Toggle word wrap Toggle overflow