This documentation is for a release that is no longer maintained
See documentation for the latest supported version 3 or the latest supported version 4.4.4. Advanced installation configuration options
This guide provides information for cluster administrators about advanced installation configuration options for OpenShift Serverless components.
This guide provides information for cluster administrators about advanced installation configuration options for Knative Serving.
Do not modify any YAML contained inside the config field. Some of the configuration values in this field are injected by the OpenShift Serverless Operator, and modifying them will cause your deployment to become unsupported.
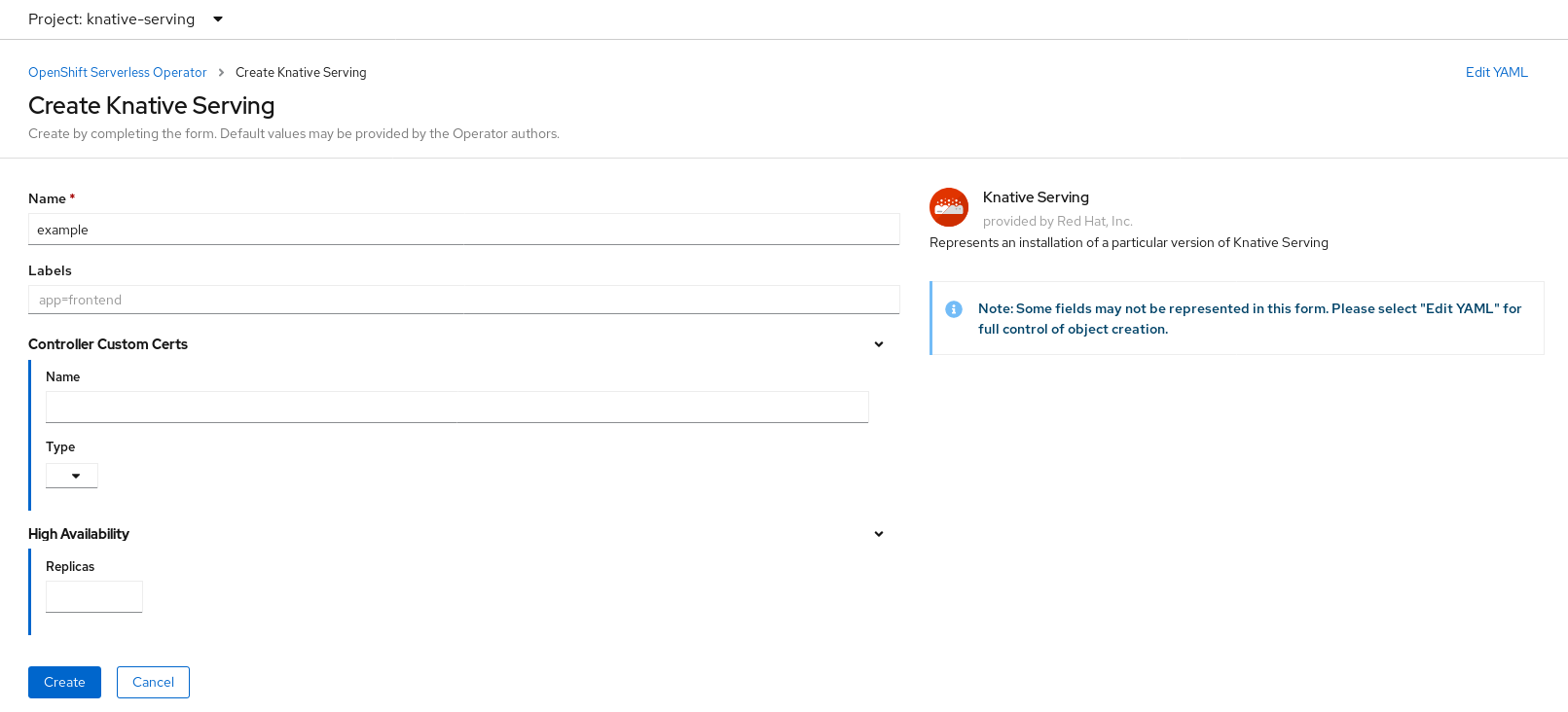
4.4.1.1. Controller custom certificates
If your registry uses a self-signed certificate, you must enable tag-to-digest resolution by creating a config map or secret. The OpenShift Serverless Operator then automatically configures Knative Serving controller access to the registry.
To enable tag-to-digest resolution, the Knative Serving controller requires access to the container registry.
The config map or secret must reside in the same namespace as the Knative Serving custom resource definition (CRD).
The following example triggers the OpenShift Serverless Operator to:
- Create and mount a volume containing the certificate in the controller.
- Set the required environment variable properly.
Example YAML
The following example uses a certificate in a config map named certs in the knative-serving namespace.
The supported types are ConfigMap and Secret.
If no controller custom certificate is specified, this defaults to the config-service-ca config map.
Example default YAML
4.4.1.2. High availability
High availability (HA) defaults to 2 replicas per controller if no number of replicas is specified.
You can set this to 1 to disable HA, or add more replicas by setting a higher integer.
Example YAML
4.4.2. Additional resources
- For more information about configuring high availability, see High availability on OpenShift Serverless.